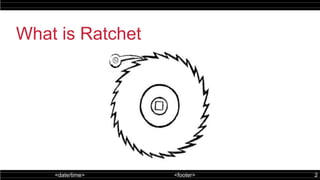
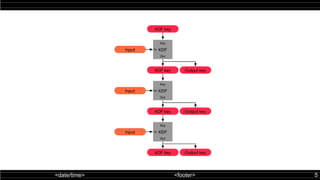
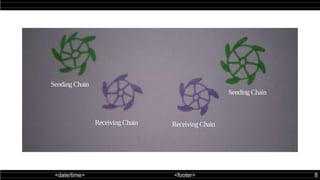
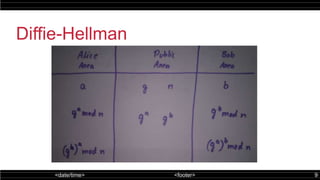
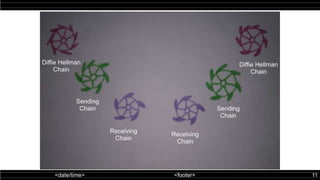
The double ratchet algorithm enables secure communication between two parties using a shared secret key, typically agreed upon via a key agreement protocol. This algorithm combines symmetric-key and Diffie-Hellman ratchets, allowing parties to derive new keys with each message while enhancing security against potential key compromises. The document outlines key properties and mechanisms involved in the operation of the double ratchet, including resilience and forward security.