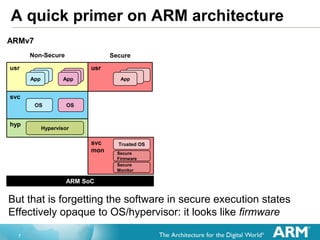
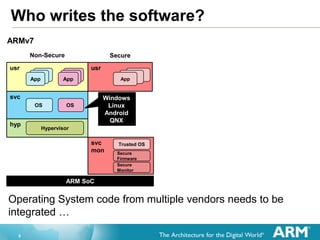
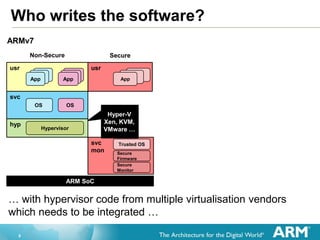
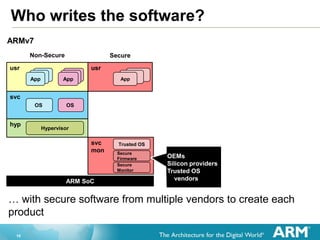
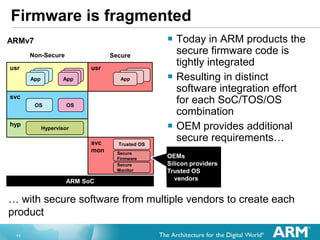
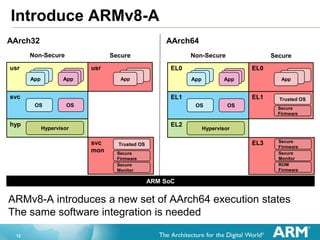
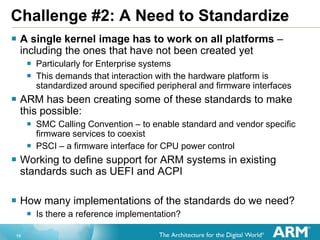
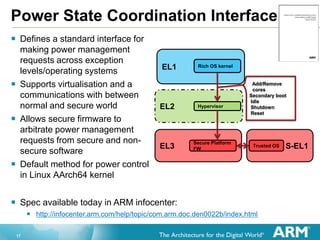
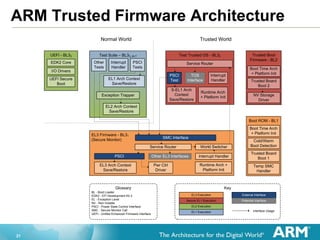
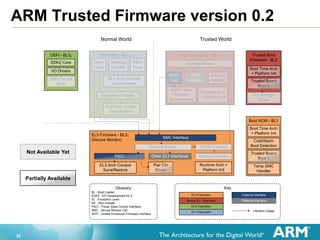
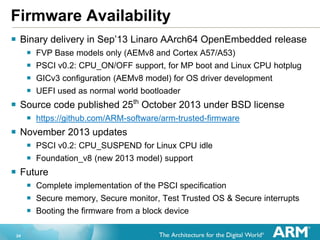
The document provides an overview of the Arm Trusted Firmware for Armv8-A, detailing its role as a reference implementation of secure software and emphasizing the need for standardization across various platforms. It discusses challenges such as rewriting firmware, integrating multiple software components, and the importance of a standardized interface for power management and system operations. The document also highlights the collaborative nature of the project, which is intended to facilitate easier integration and foster community development through an open-source model.