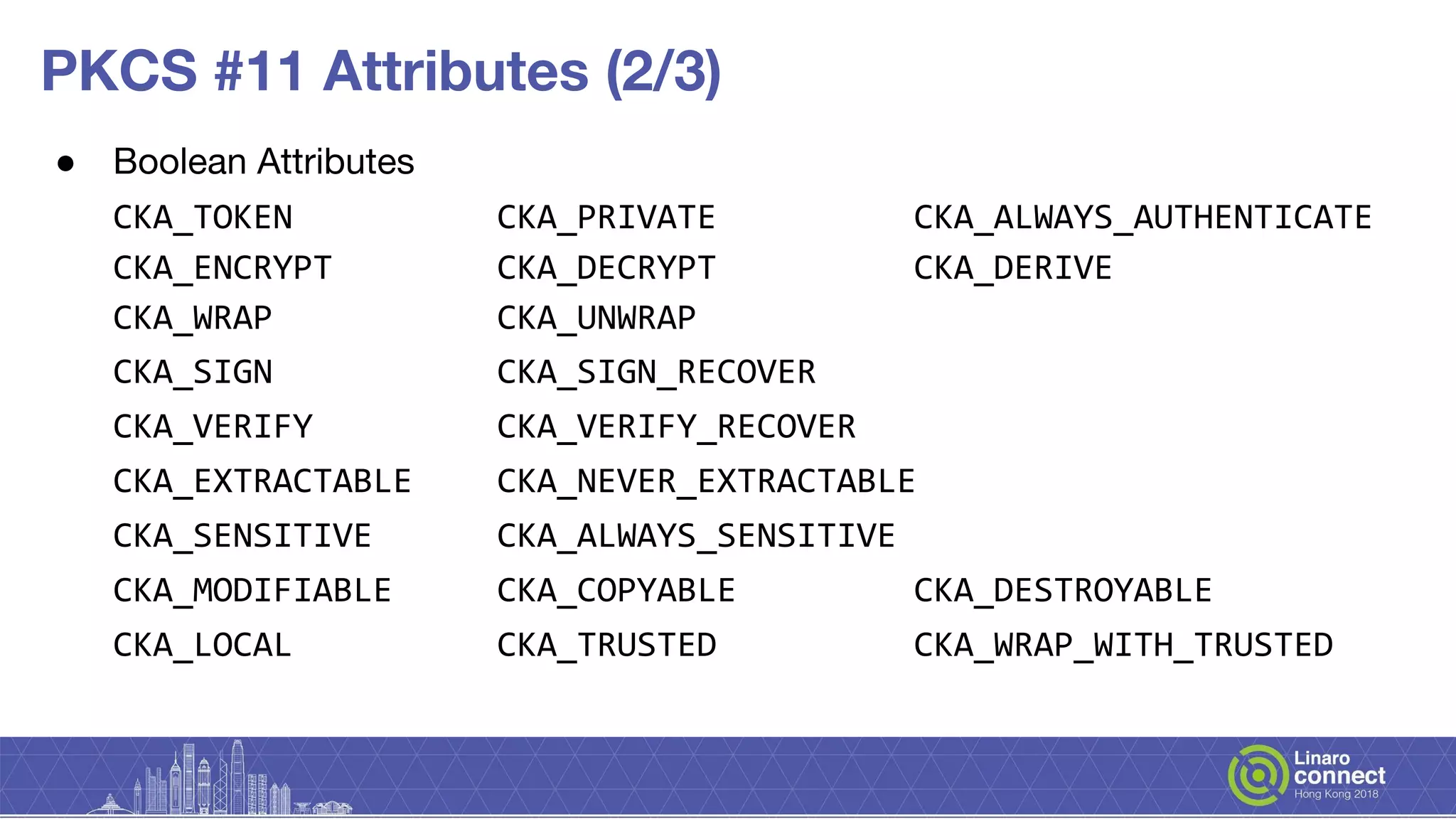
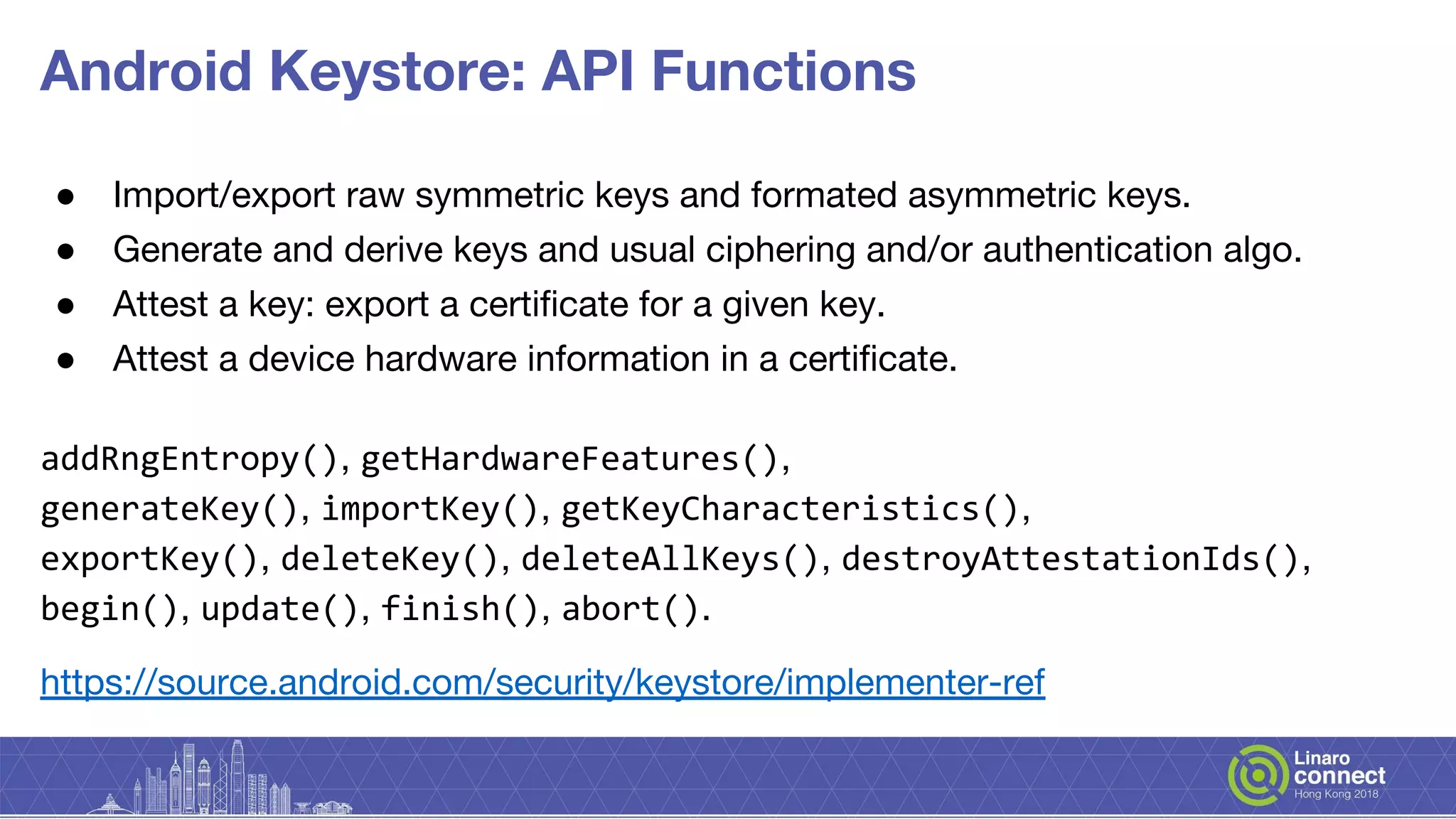
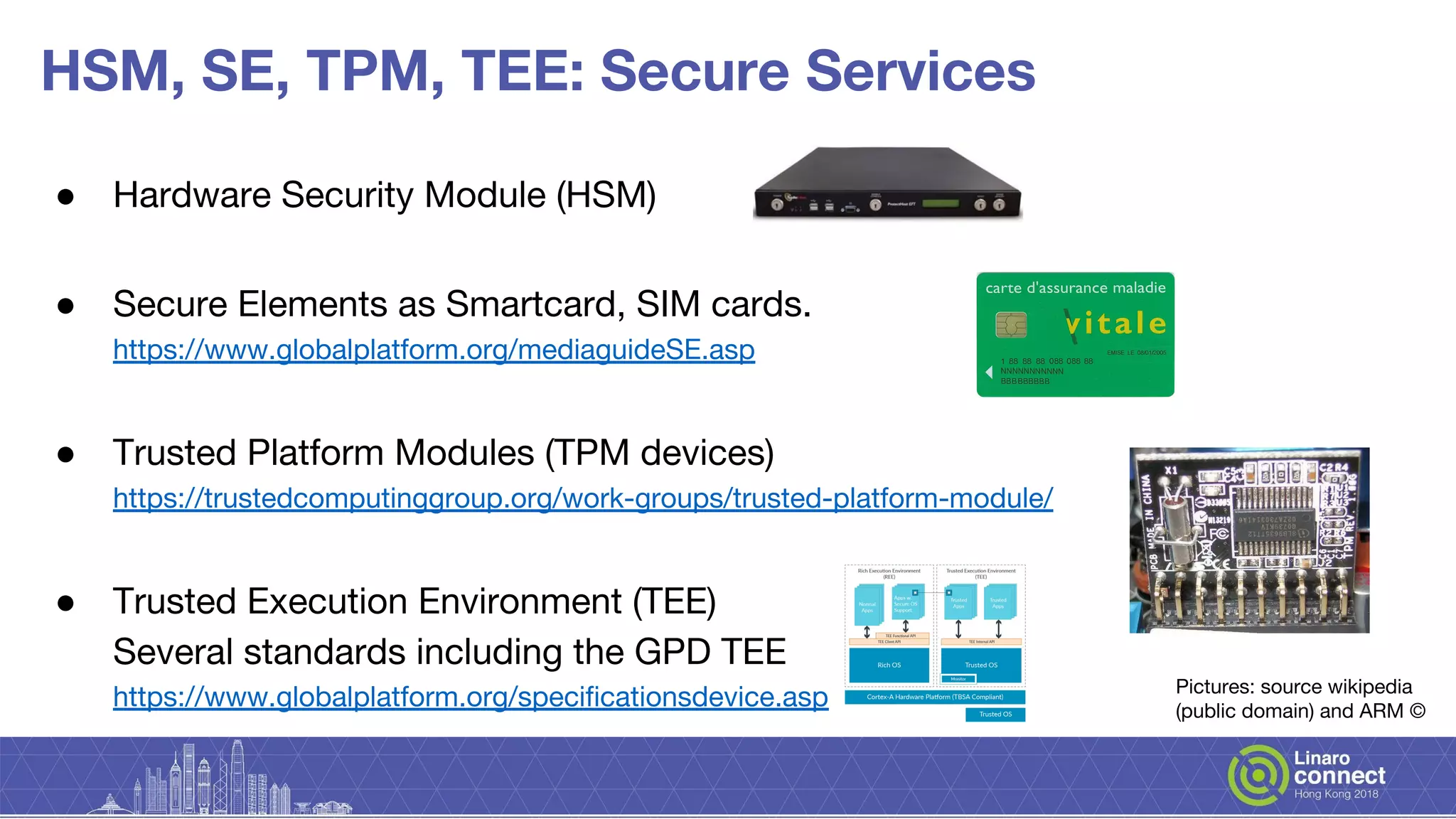
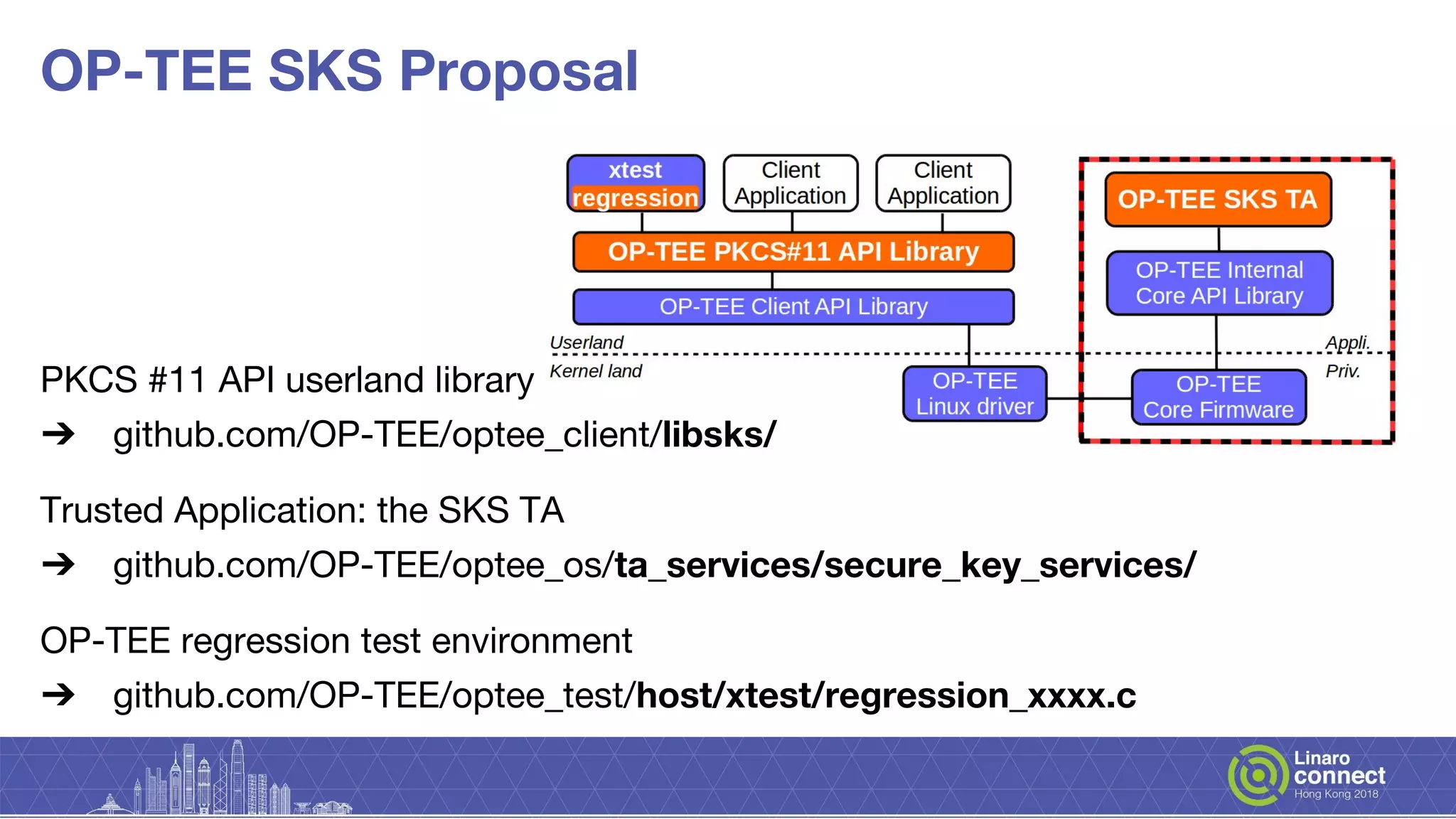
The document discusses secure key services implemented within OP-TEE, detailing its architecture, client interfaces, cryptographic operations, and integration with hardware security modules and secure elements. It highlights the lack of a uniform interface for secure key management and outlines the OP-TEE's reliance on various APIs for cryptographic functions. Additionally, it presents plans for the development of the secure key services and ongoing enhancements needed for broader functionality and security features.
























![Thank You
etienne.carriere@linaro.org [github: @etienne-lms]
#HKG18
HKG18 keynotes and videos on: connect.linaro.org
For further information: www.linaro.org](https://image.slidesharecdn.com/hkg18-402-180328091217/75/HKG18-402-Build-secure-key-management-services-in-OP-TEE-30-2048.jpg)