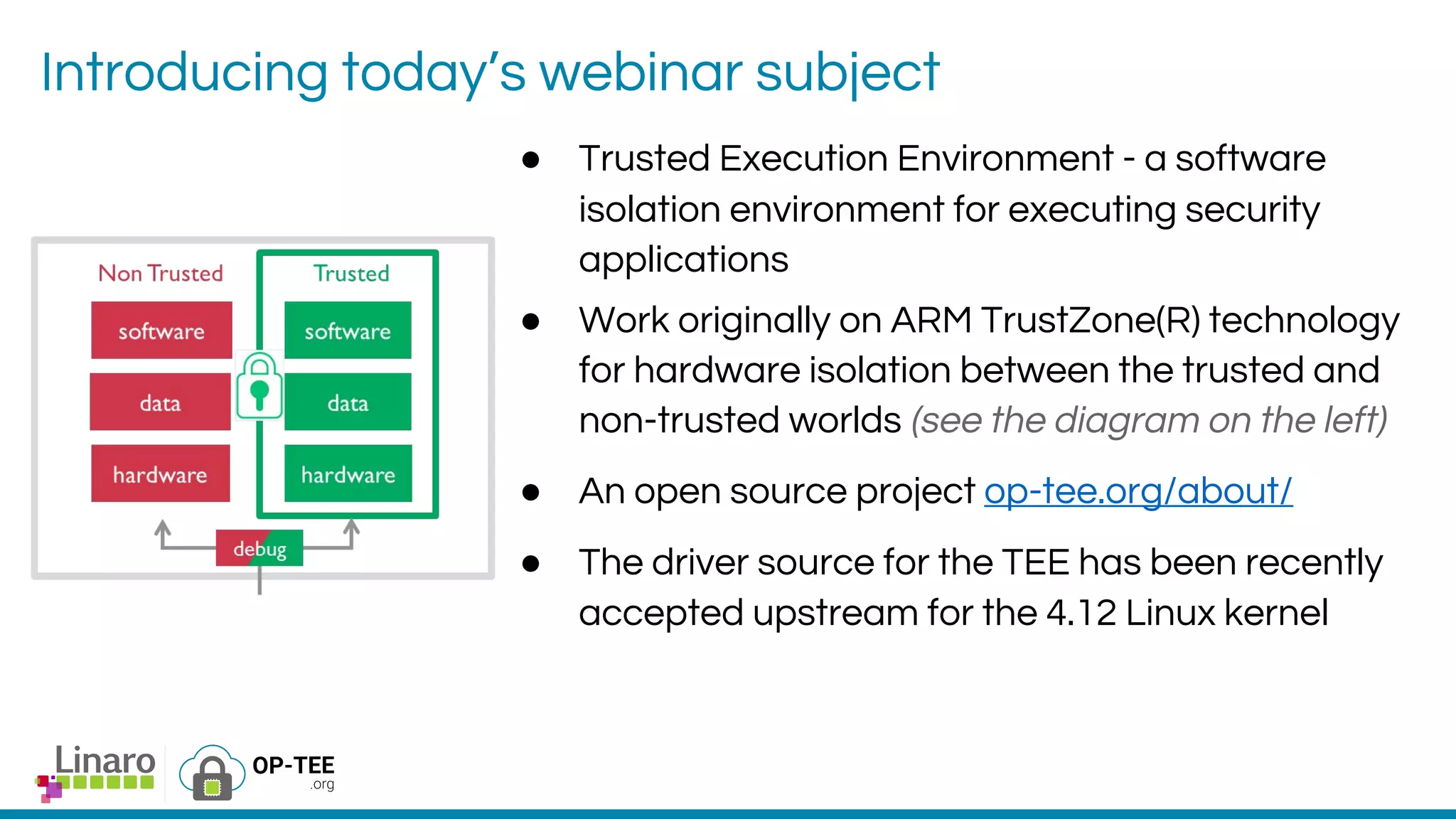
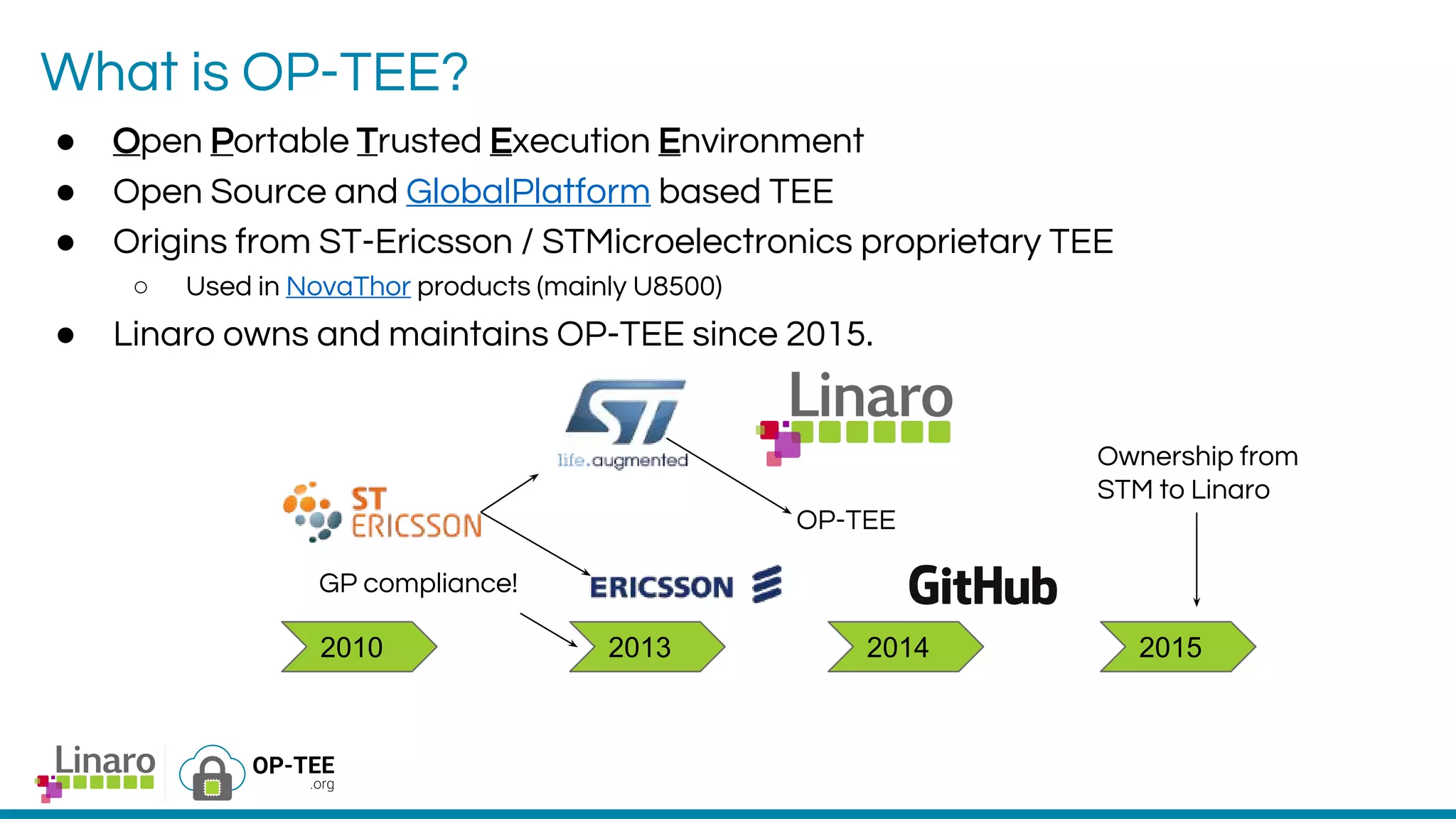
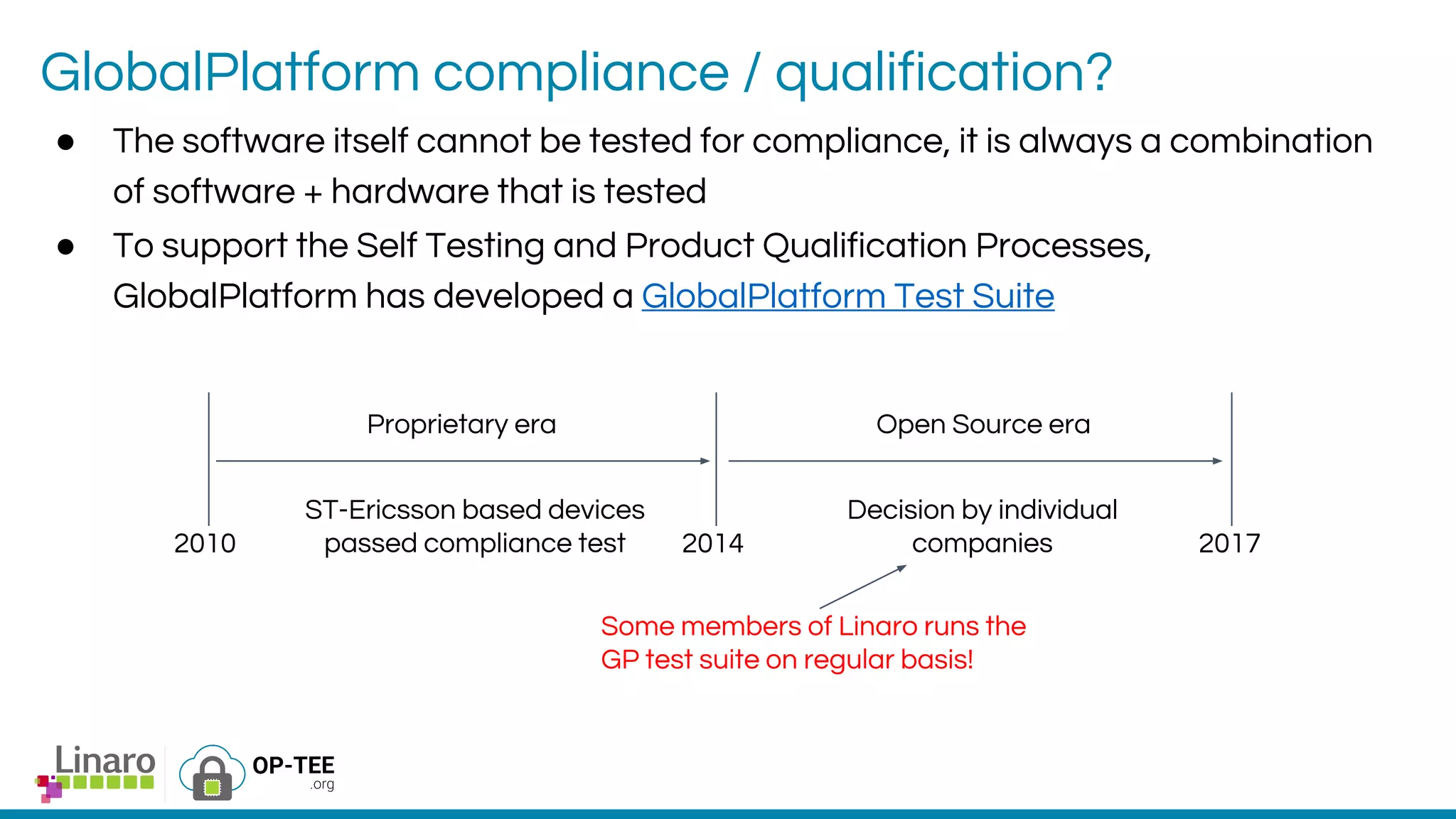
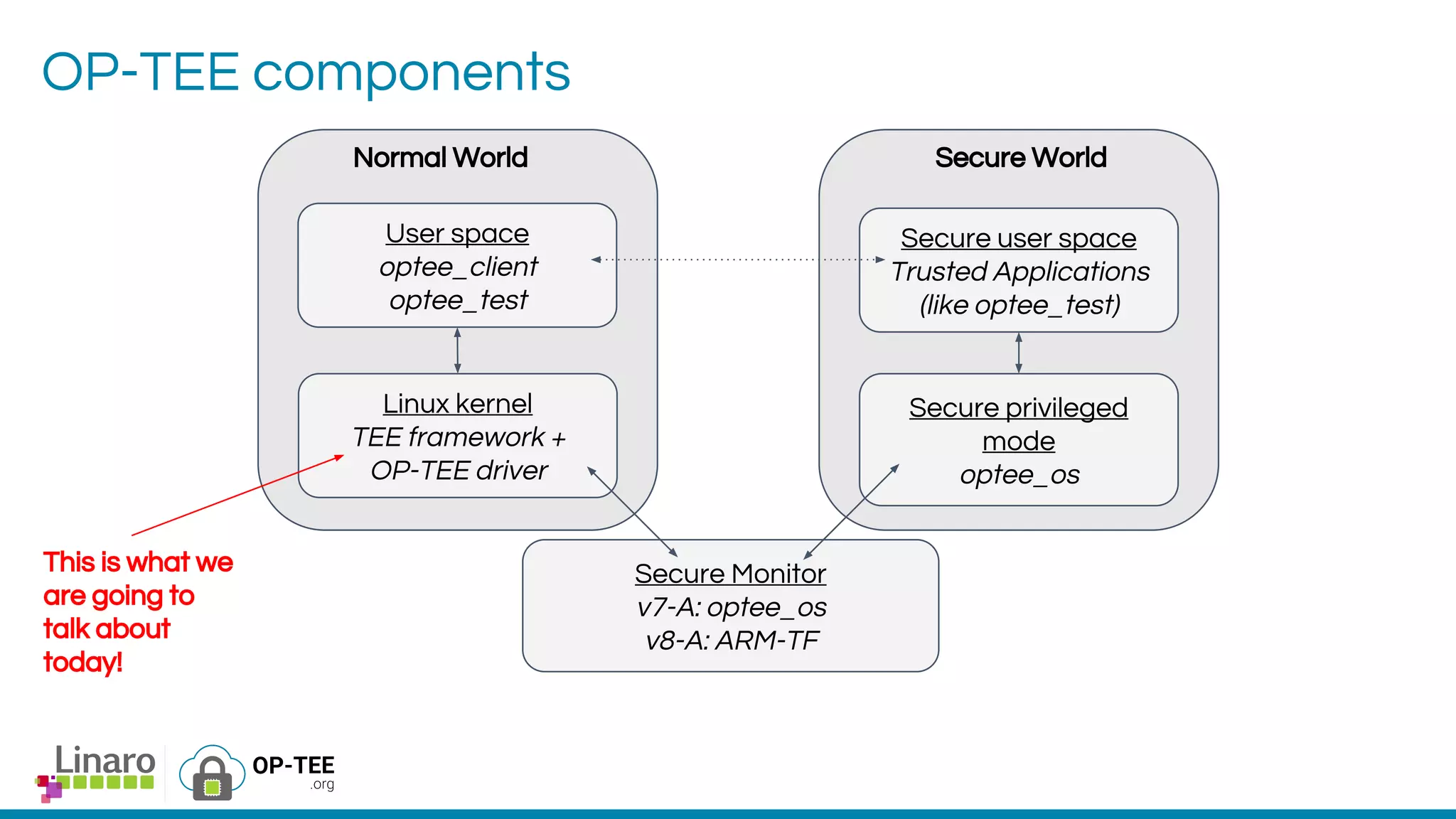
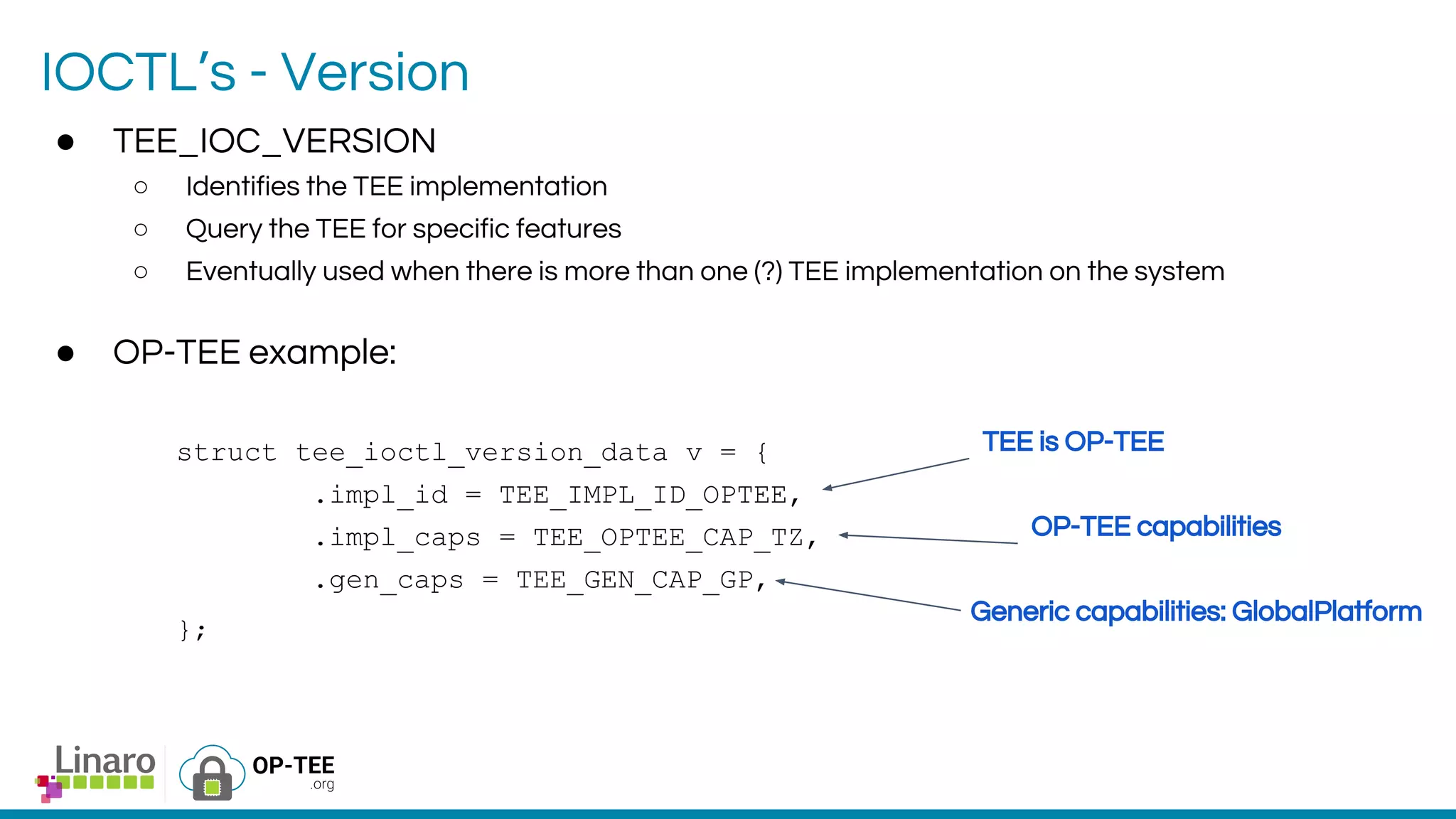
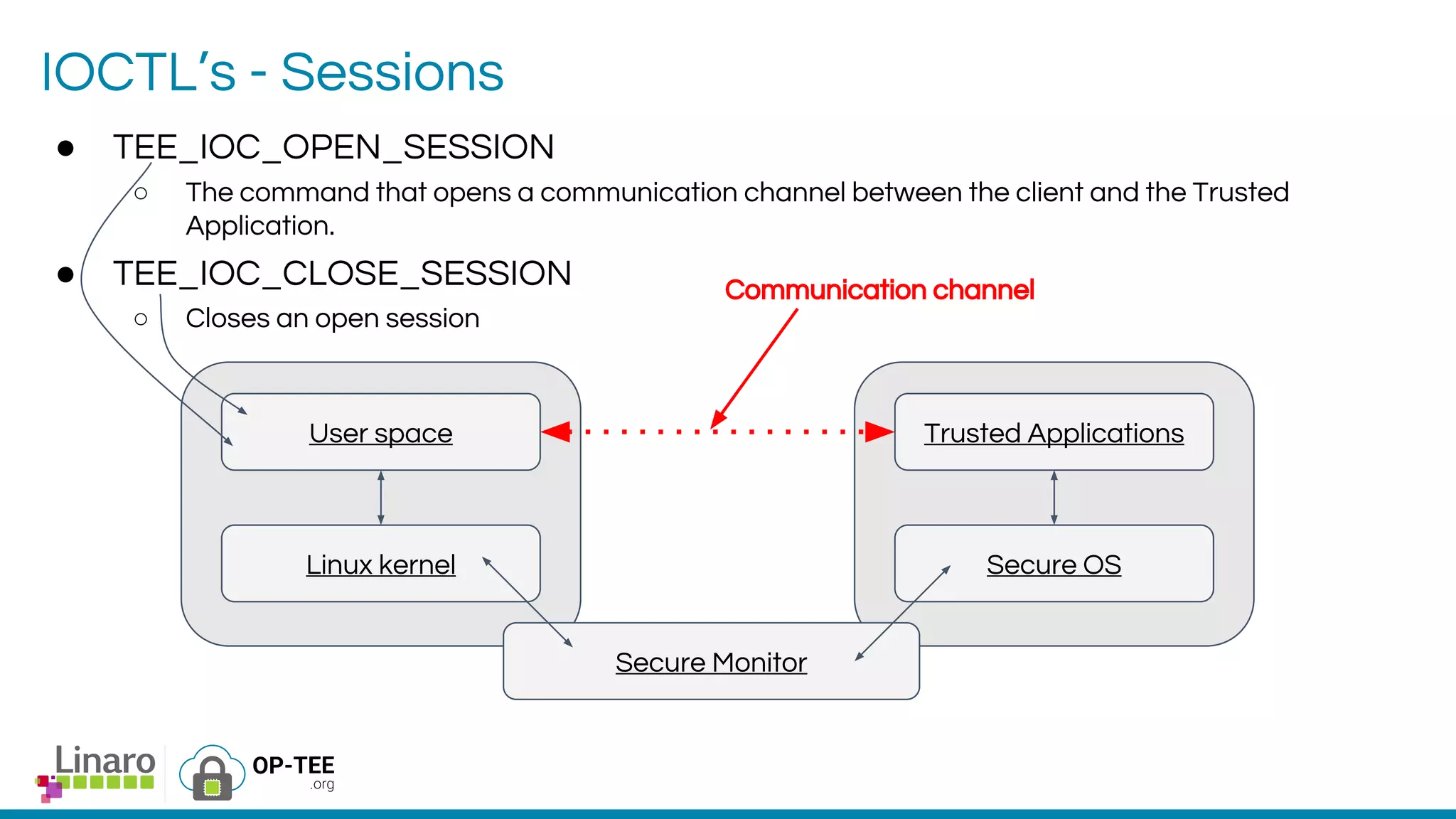
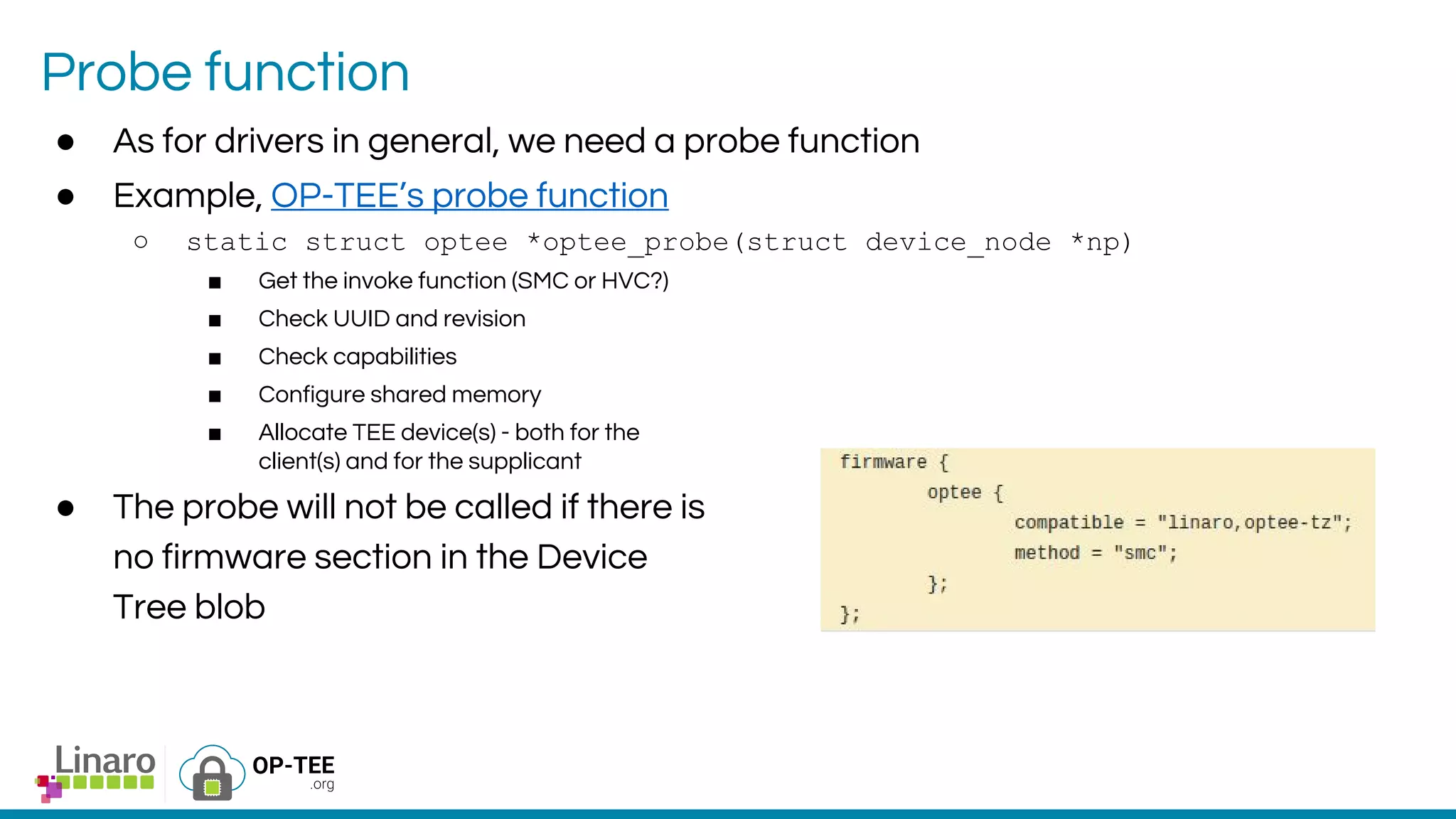
The webinar introduces the concept of Trusted Execution Environment (TEE) focused on open-source project OP-TEE, which utilizes ARM TrustZone technology for secure application execution. It provides insights into the TEE framework's design principles, kernel support, and the significance of unifying TEE protocols for open-source security. The session welcomes participation from the development community and includes a Q&A segment for further engagement.