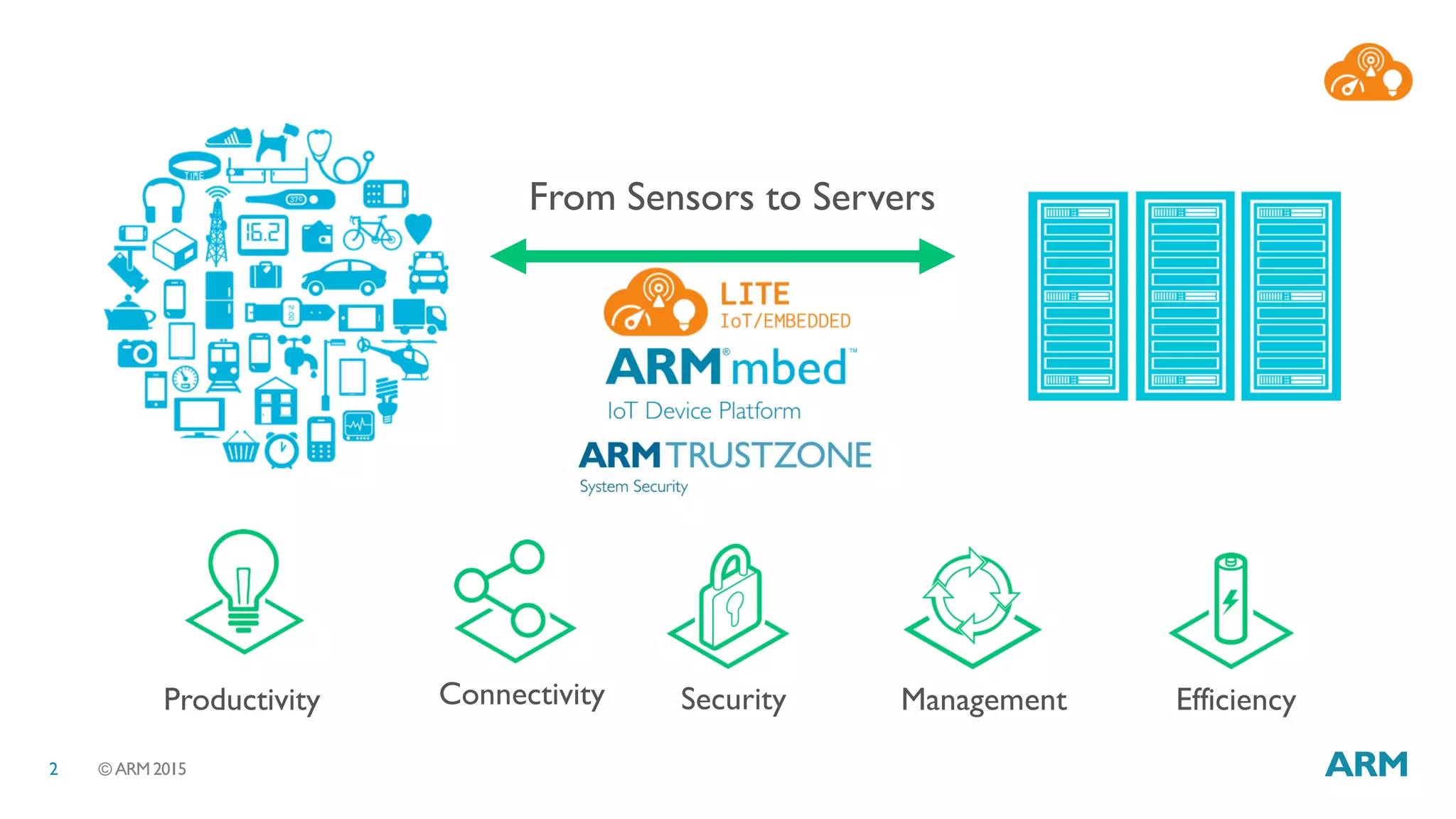
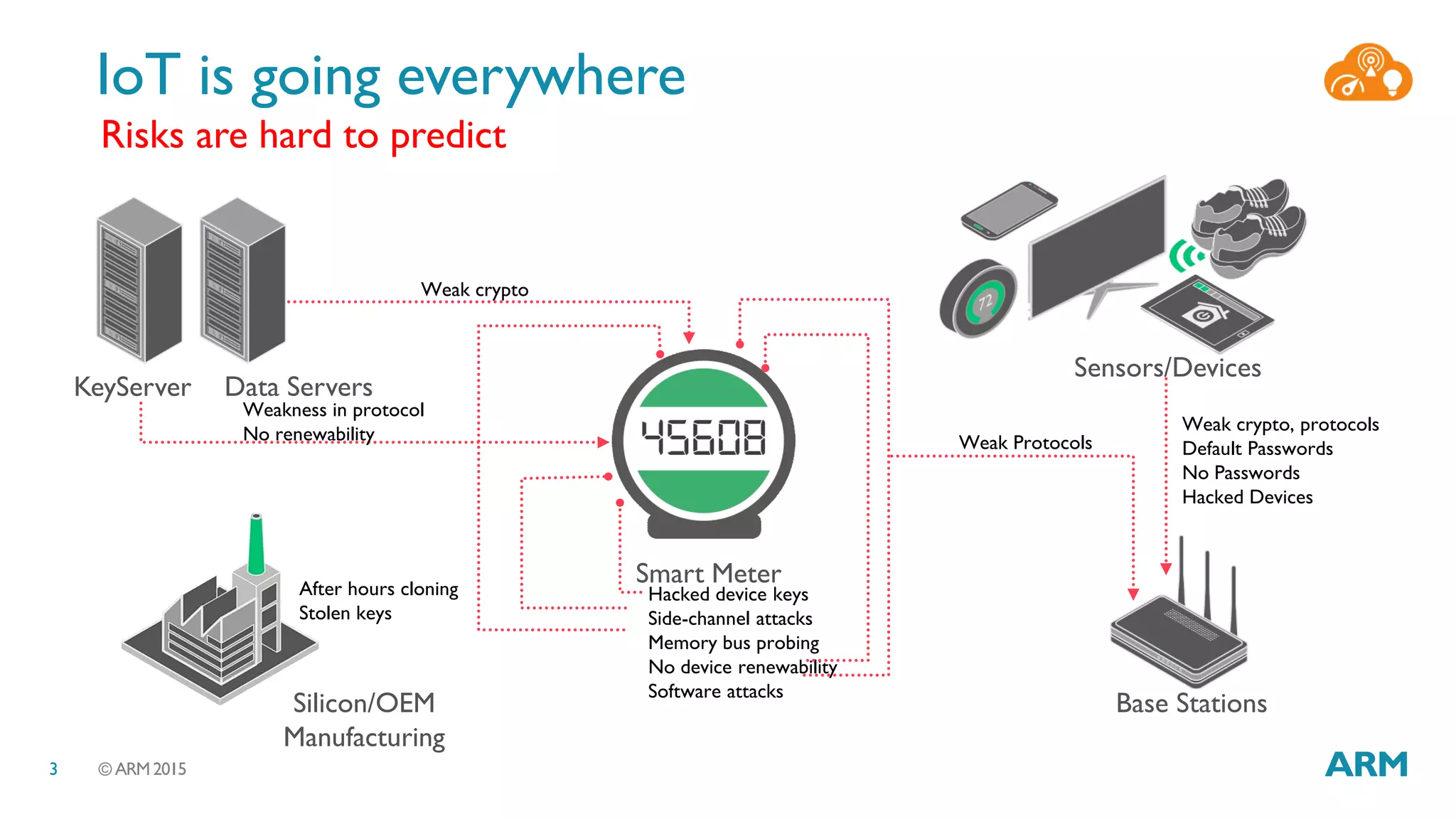
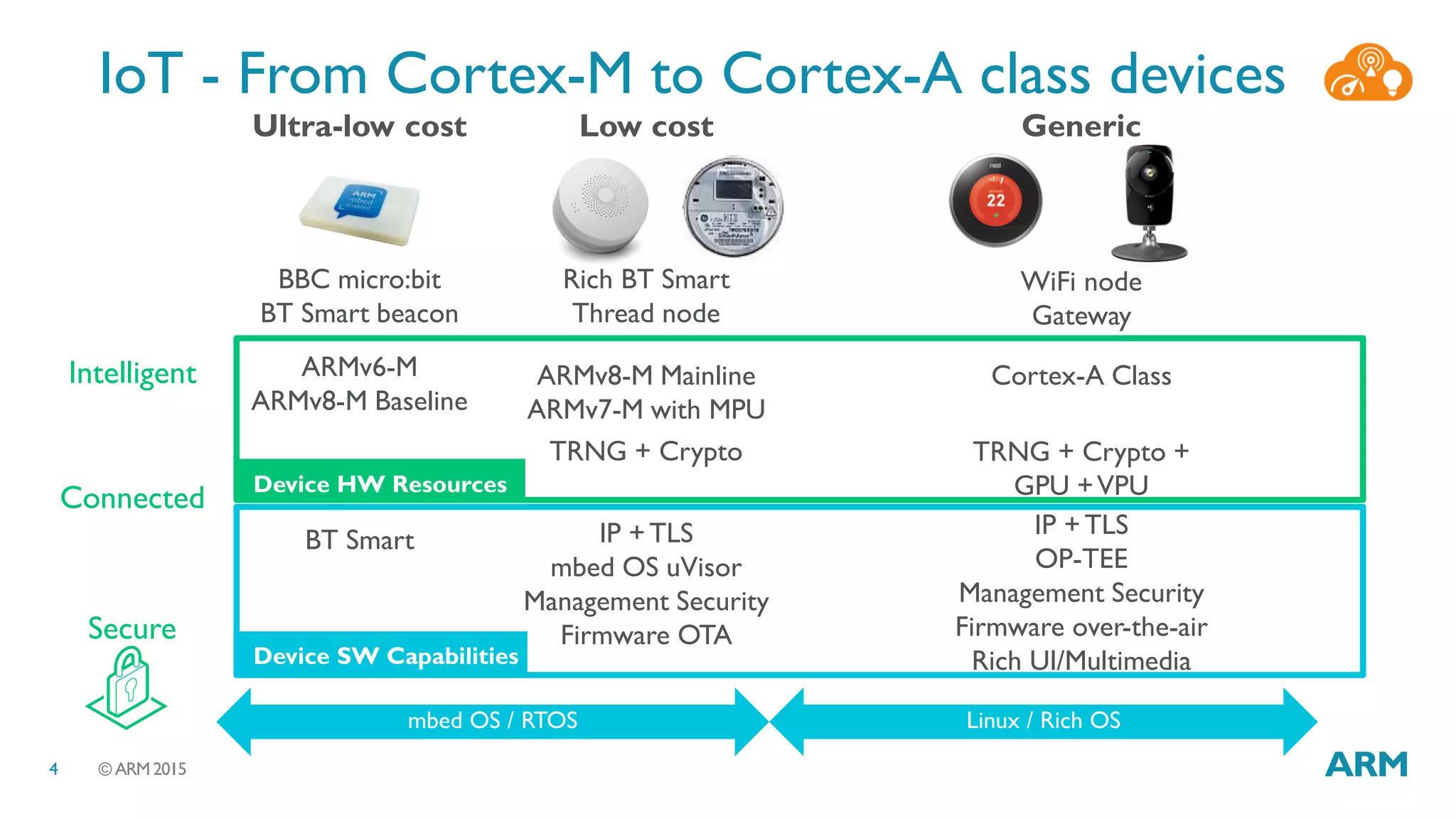
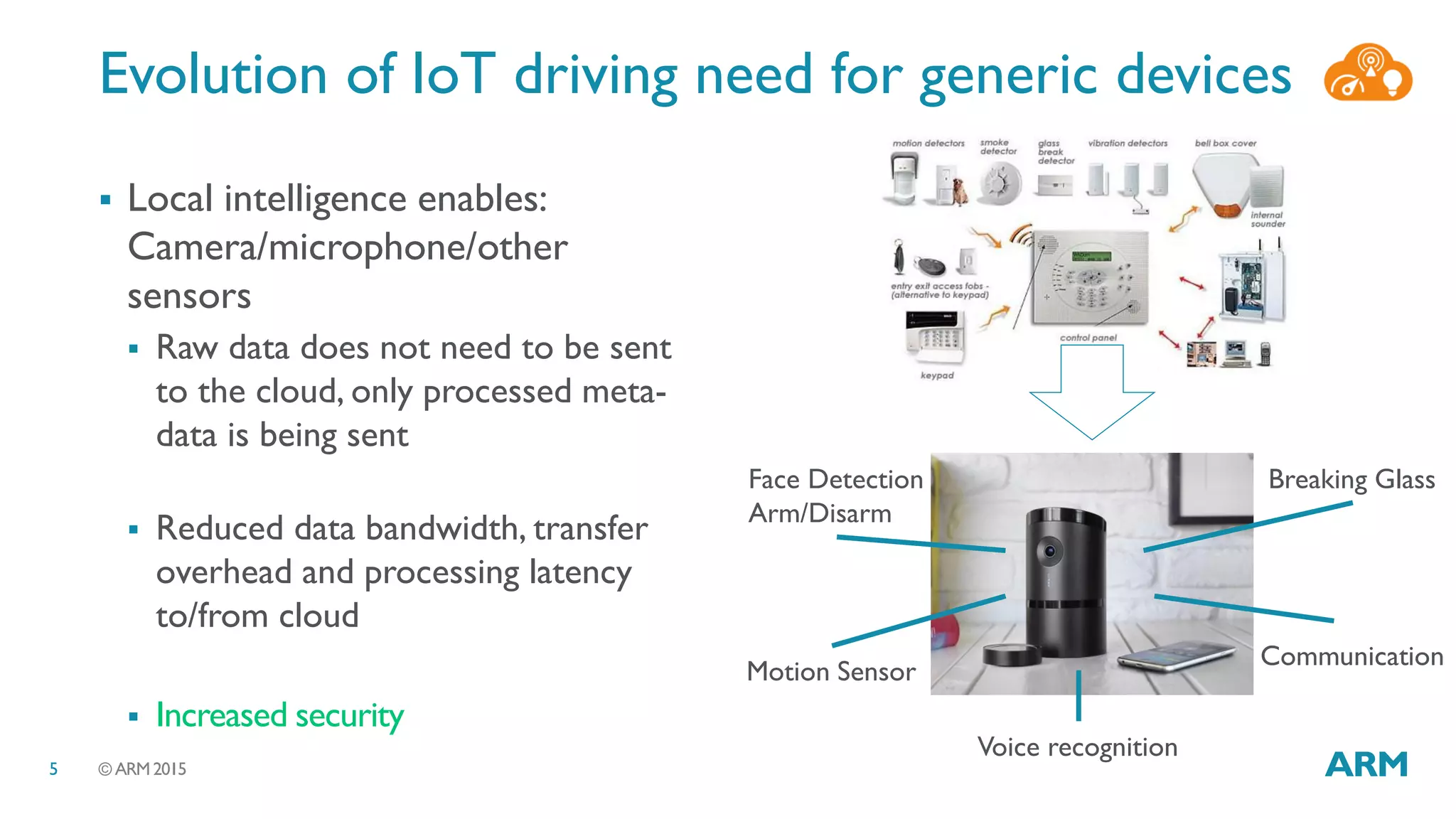
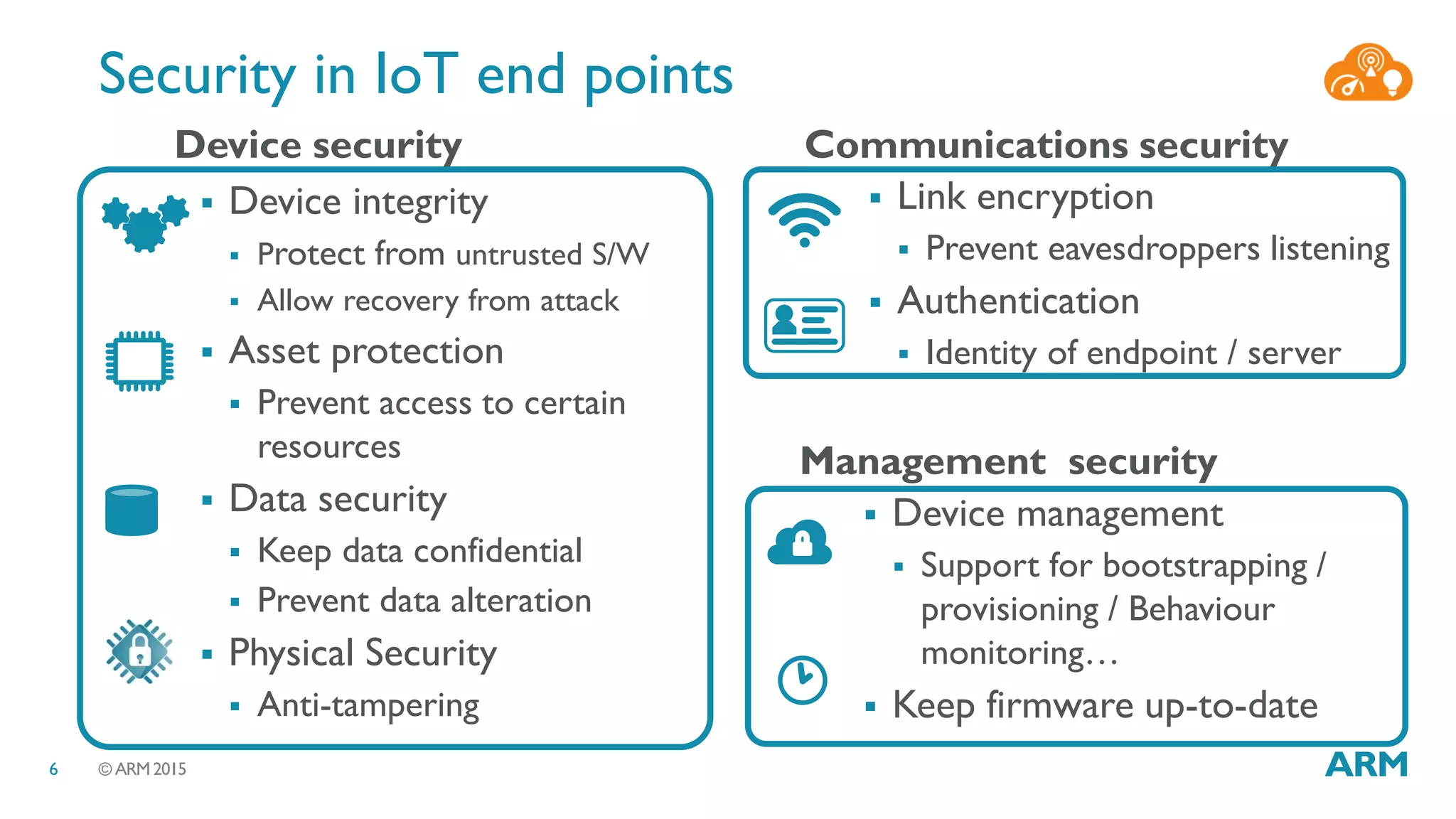
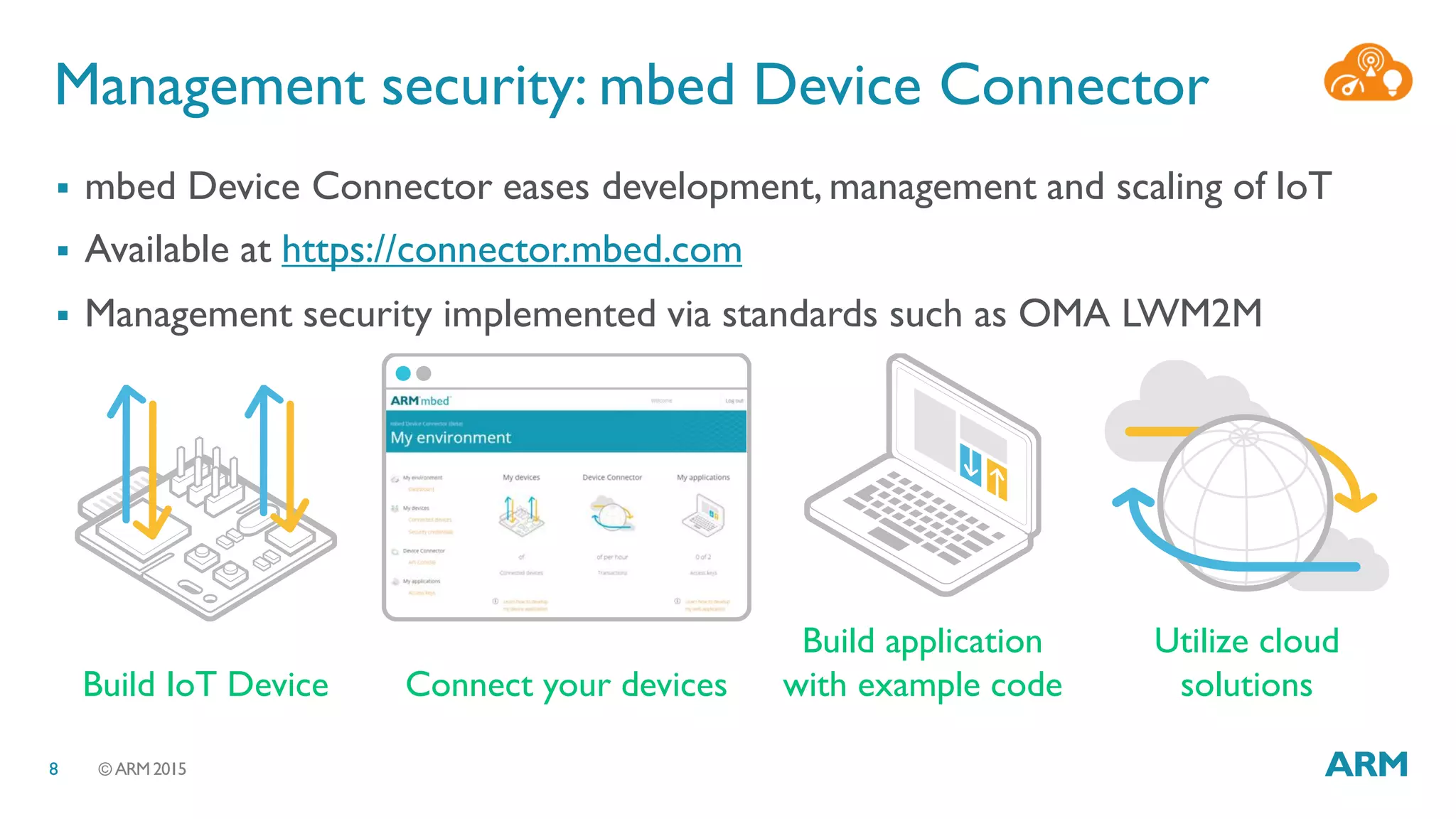
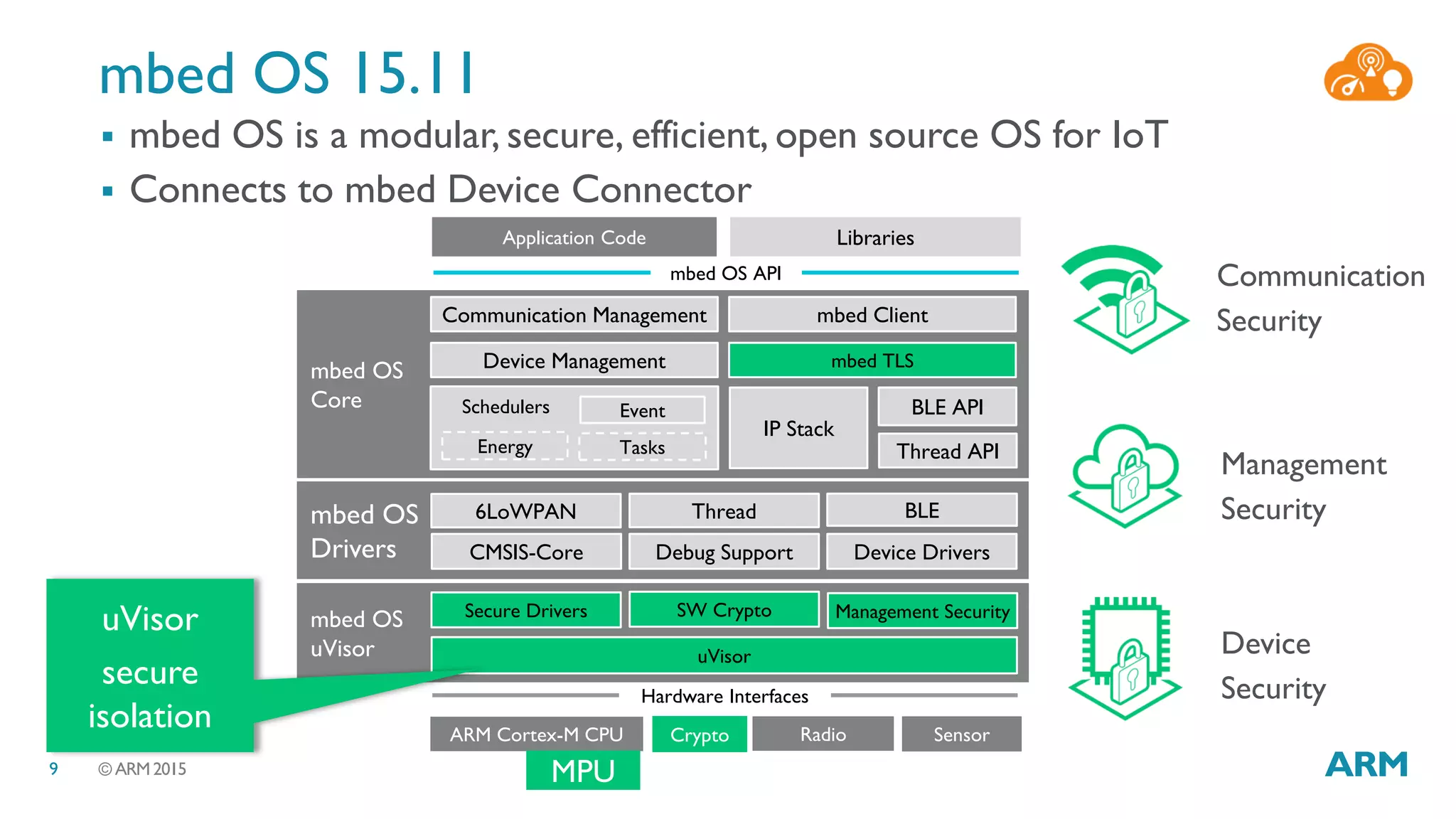
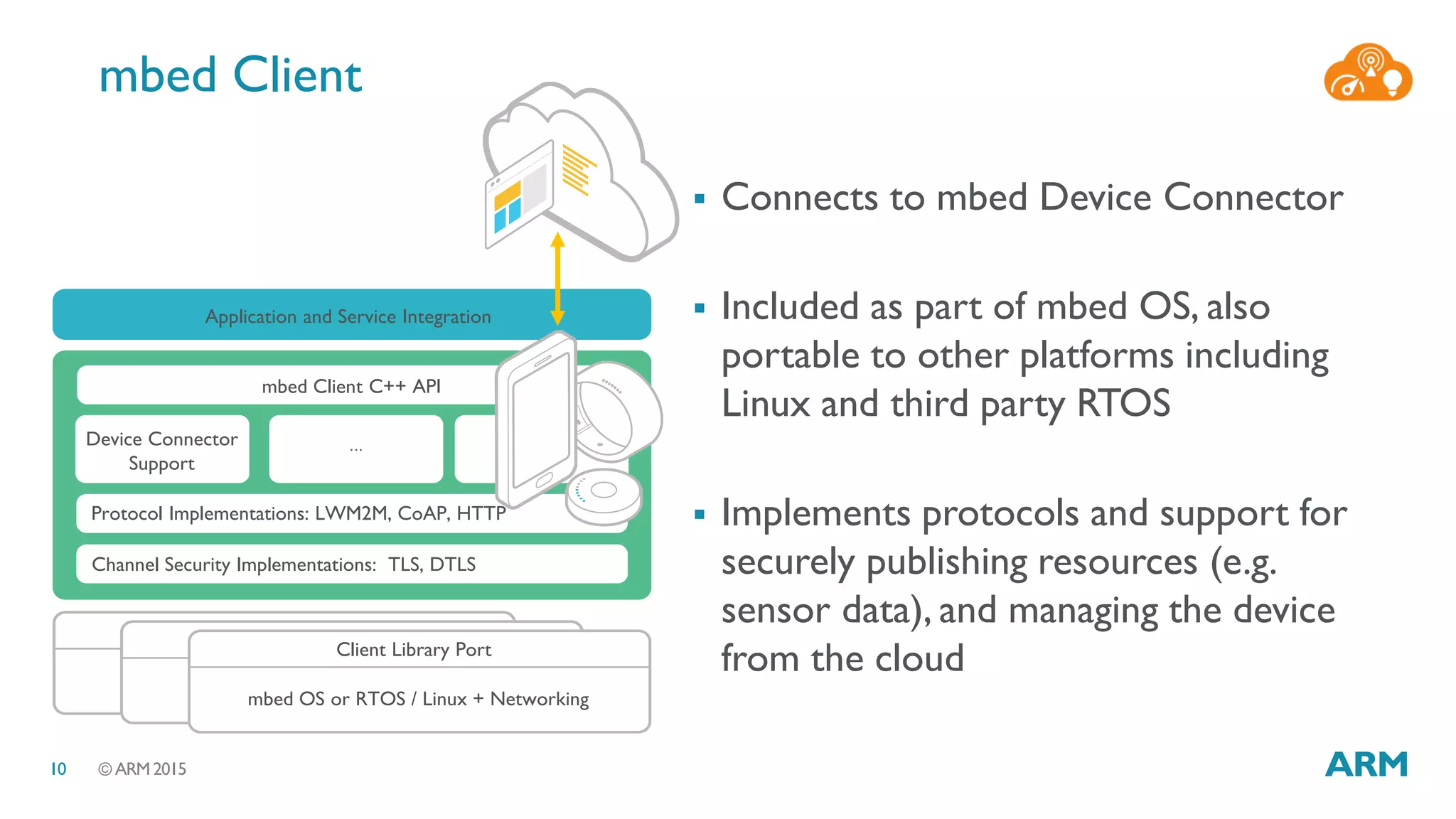
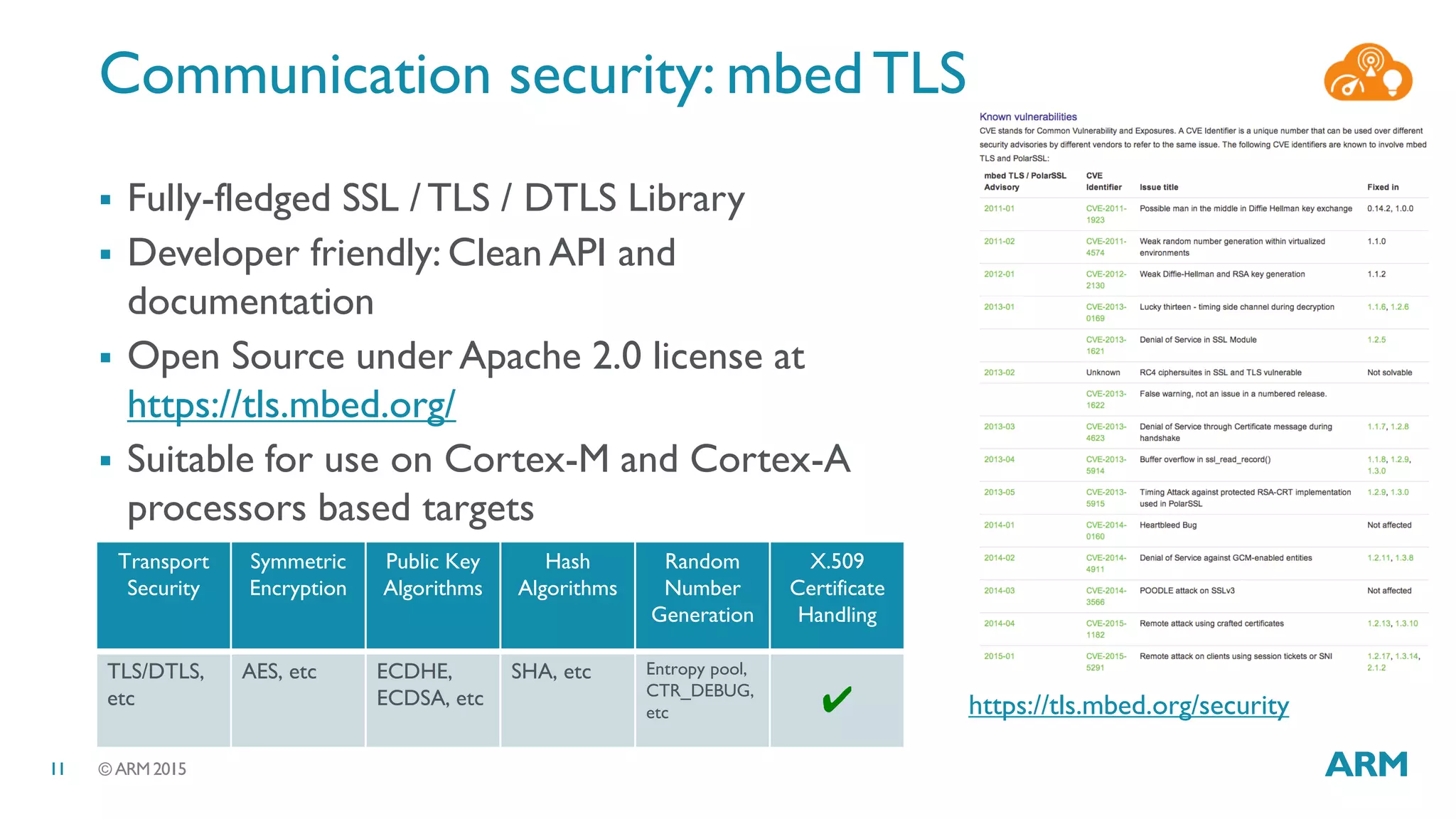
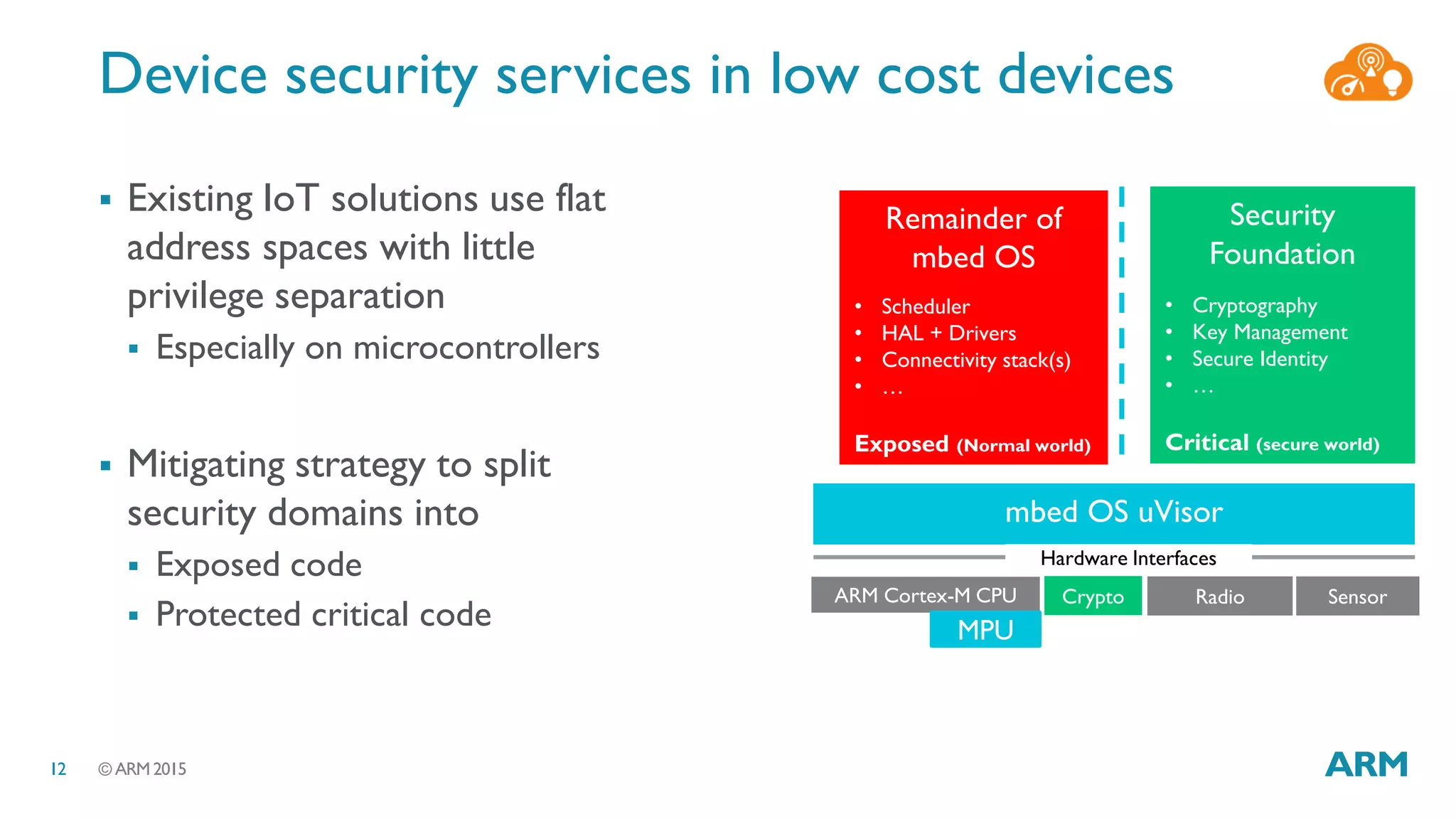
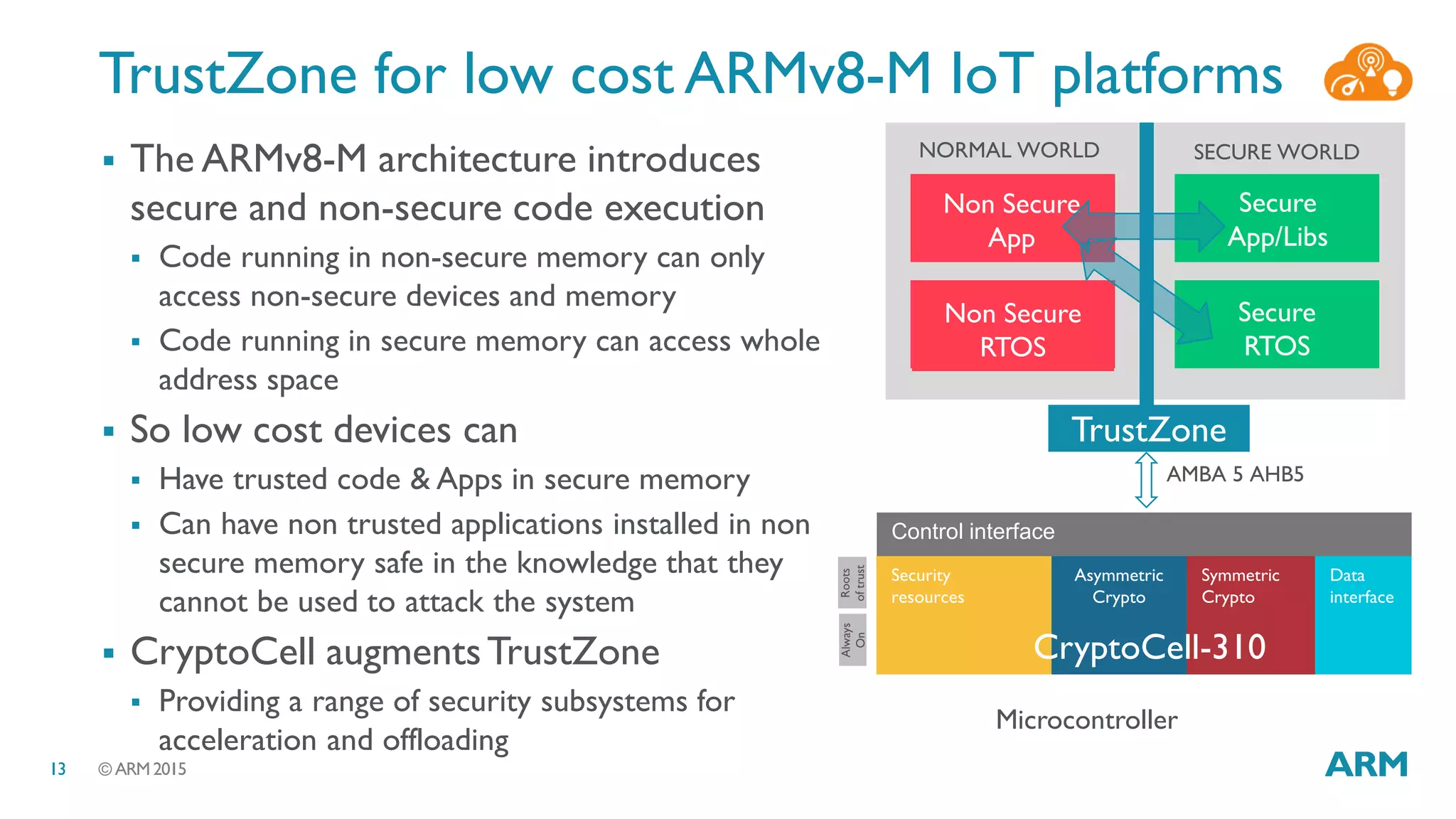
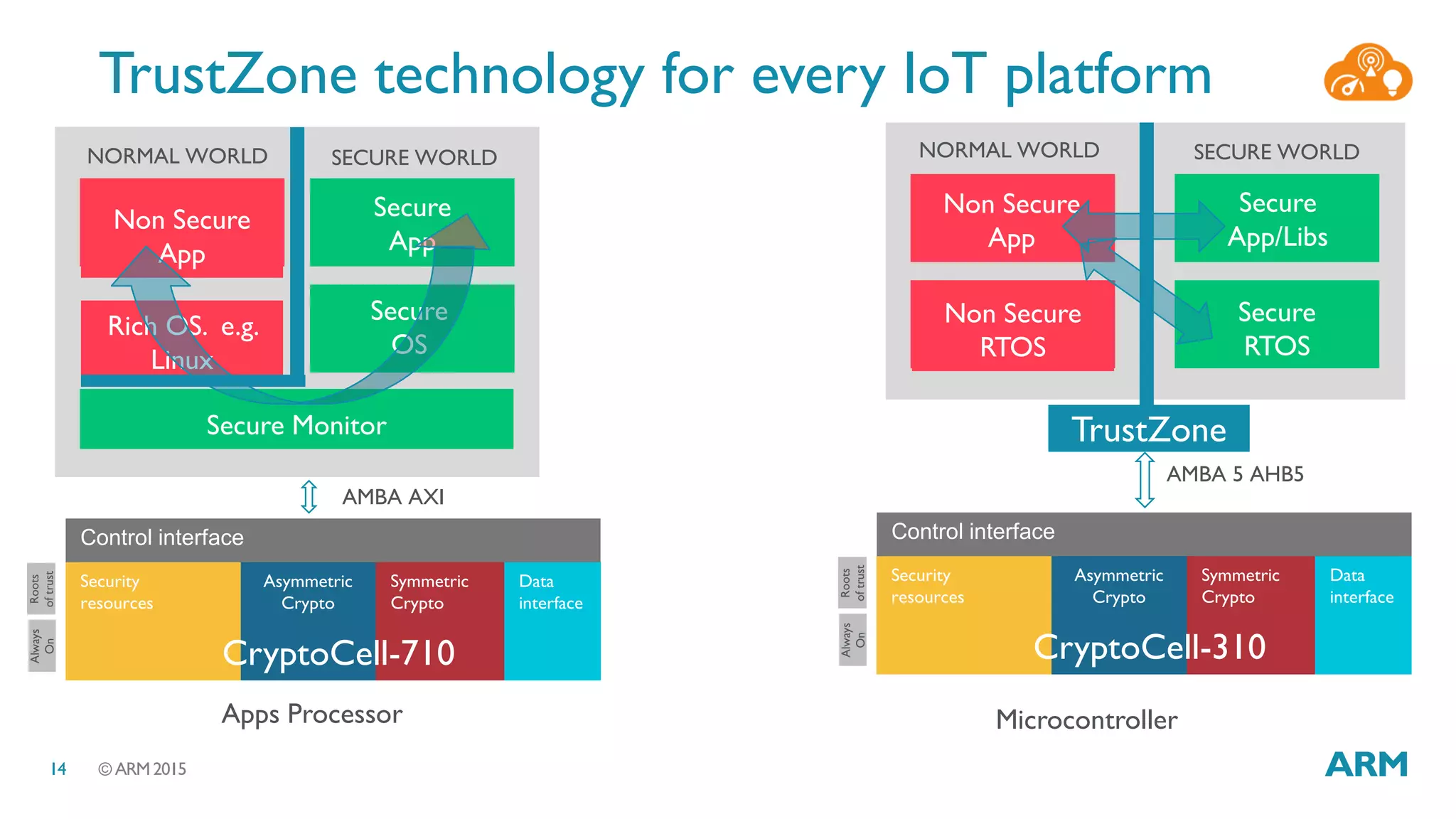
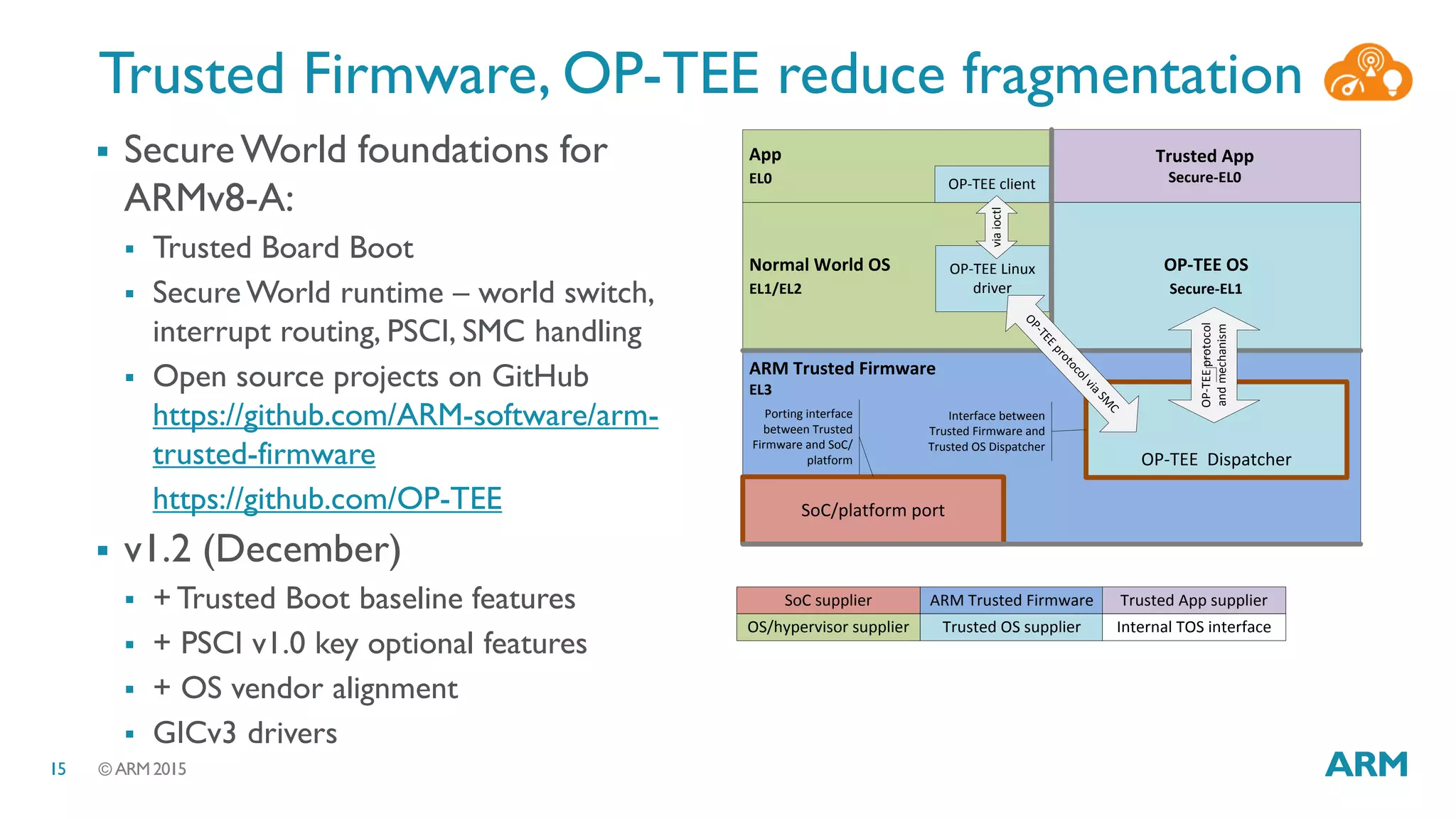
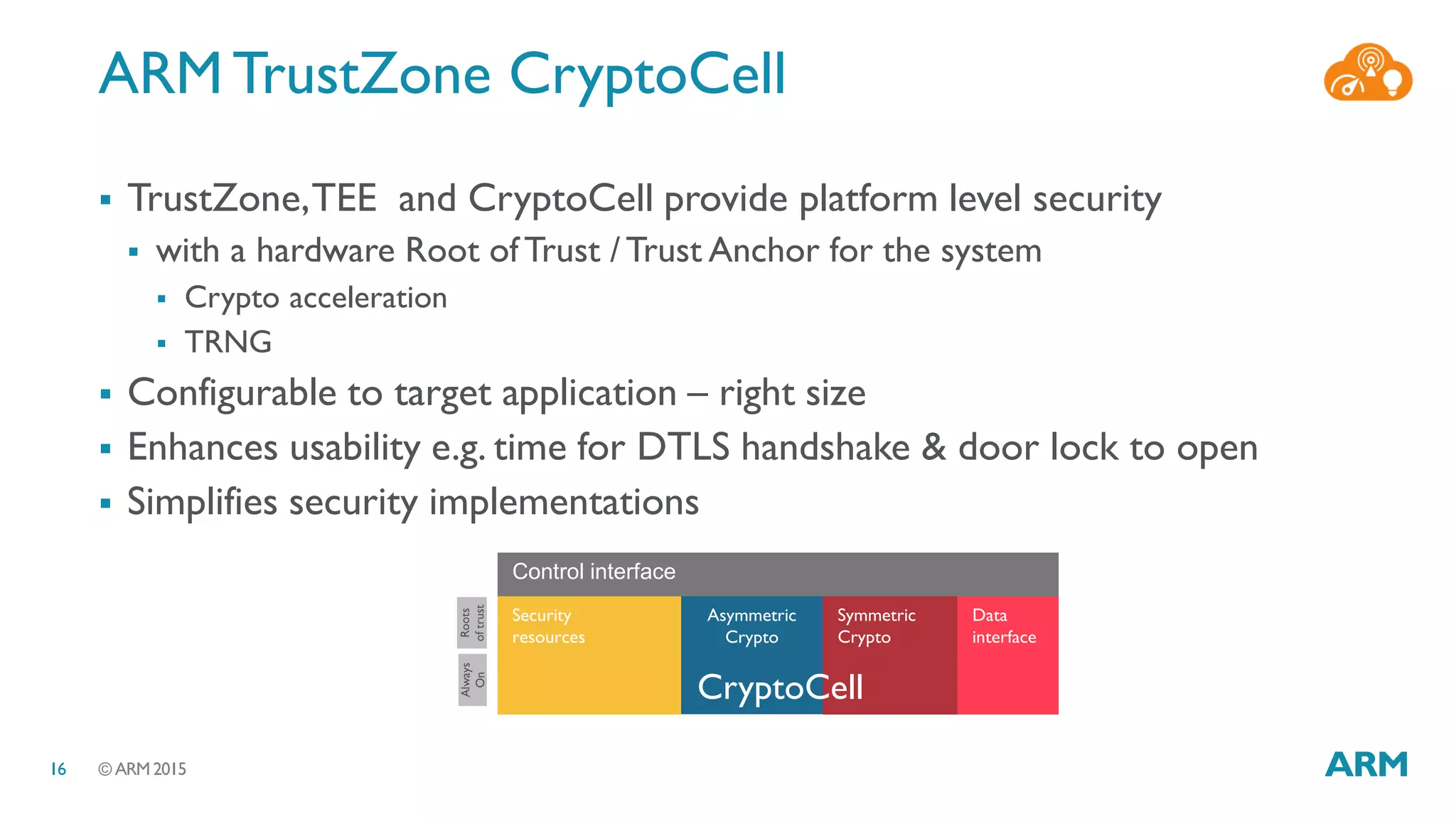
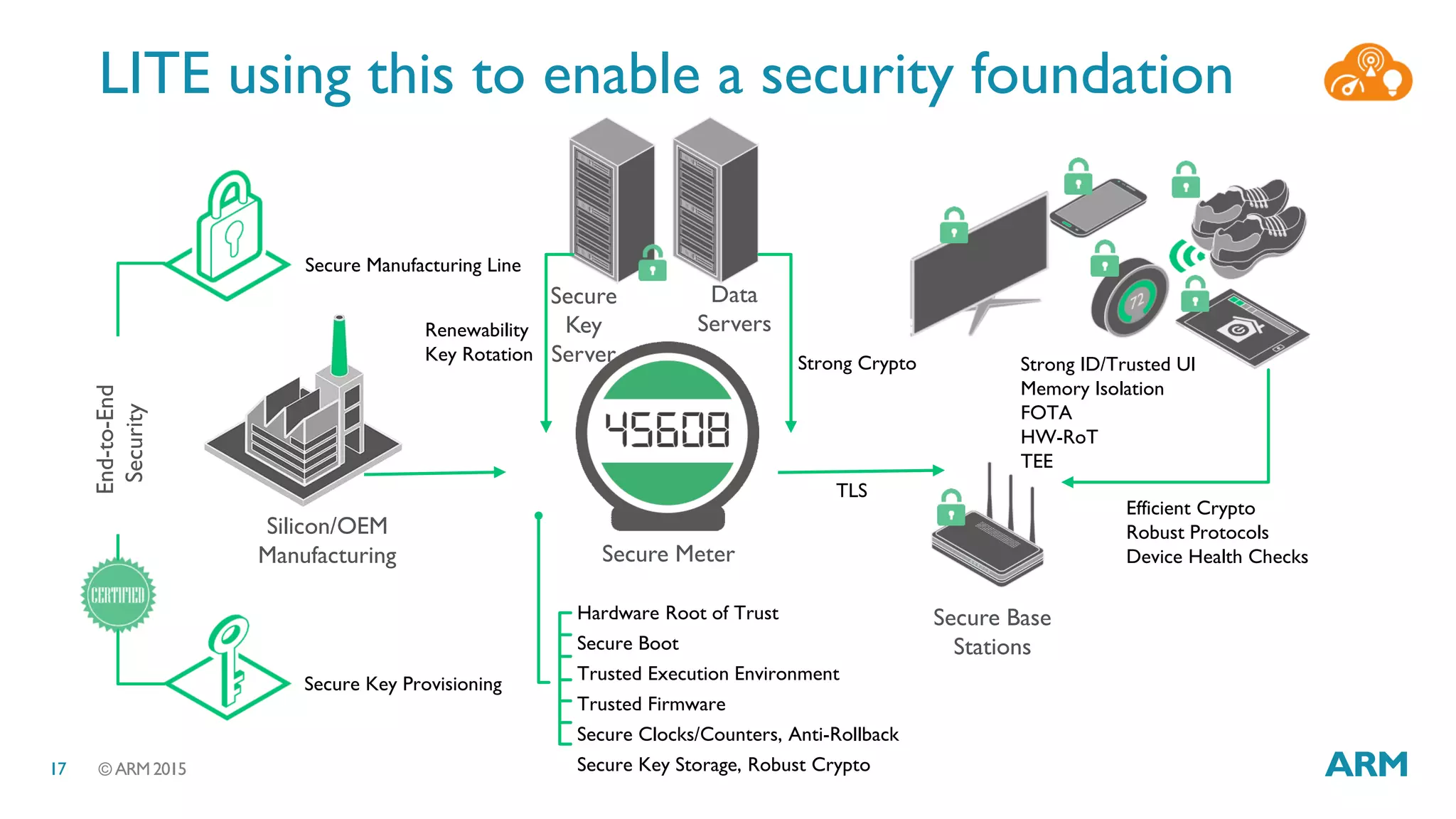
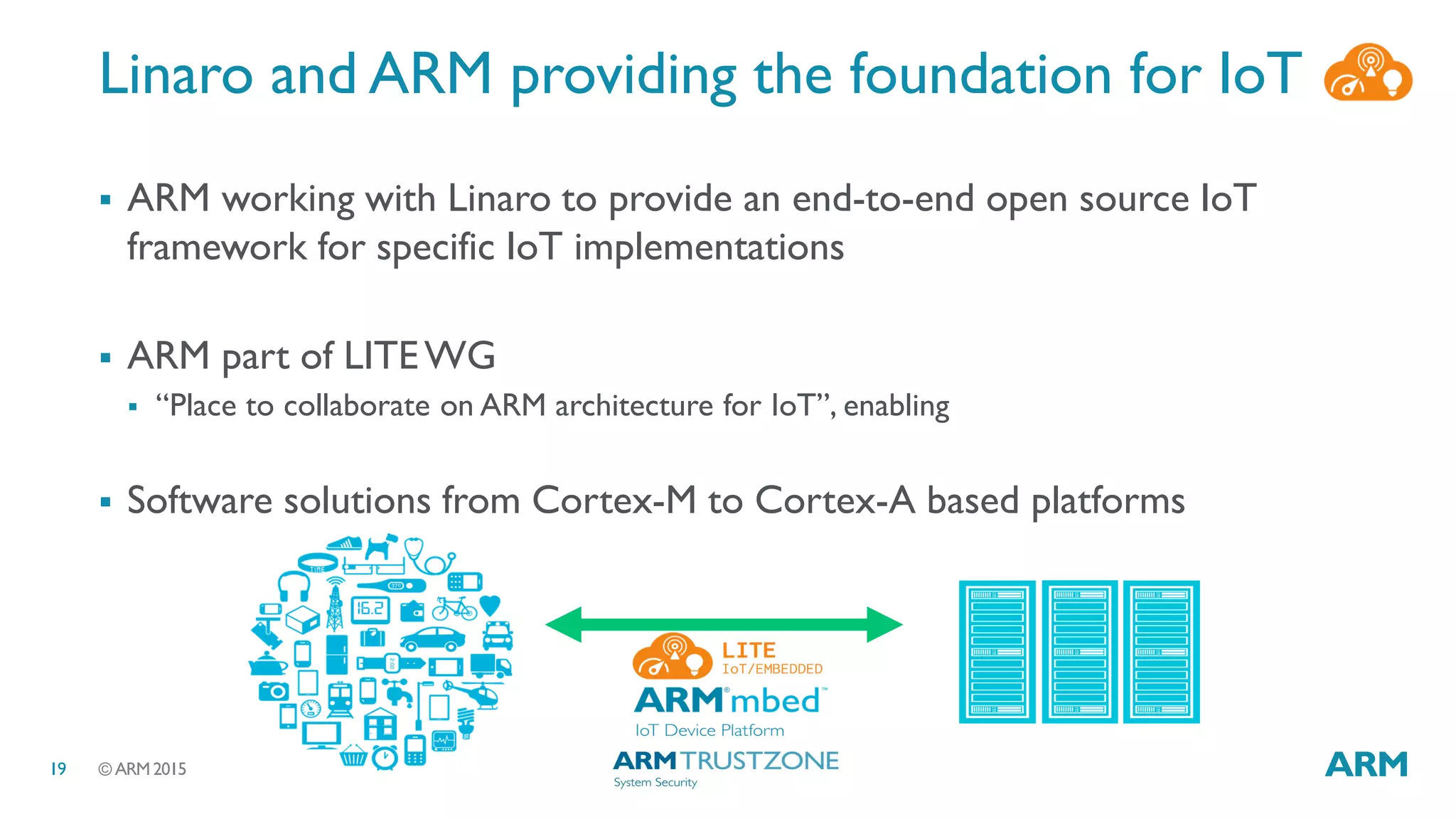
This document discusses security considerations for Internet of Things (IoT) systems. It outlines various security risks for IoT devices like weak cryptography, default passwords, and lack of device renewability. It then describes how security can be built into IoT systems at different levels, including device hardware with features like ARM TrustZone, software like mbed OS and mbedTLS, and cloud management platforms. The document advocates for an end-to-end secure IoT framework provided through collaboration between ARM and Linaro.