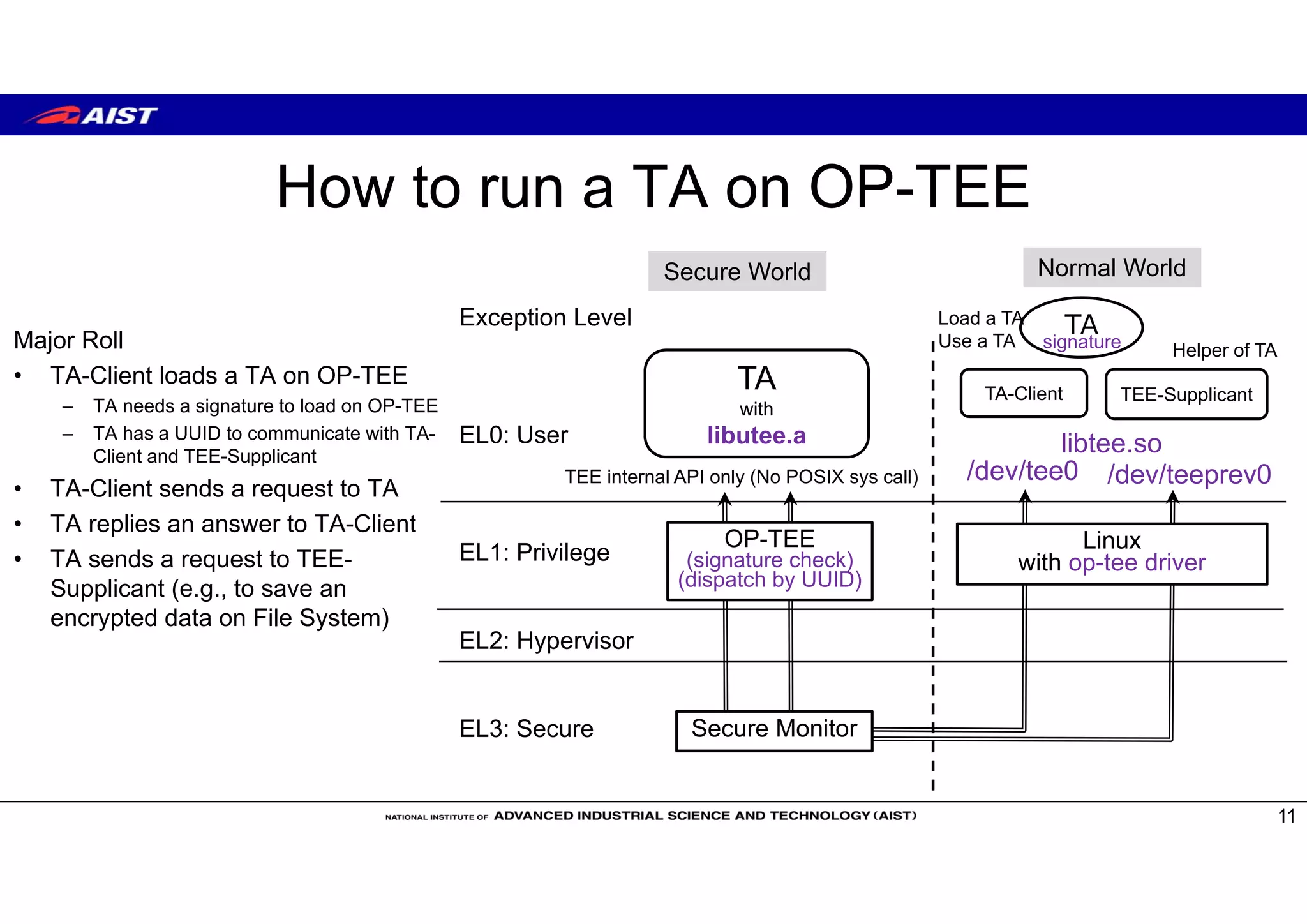
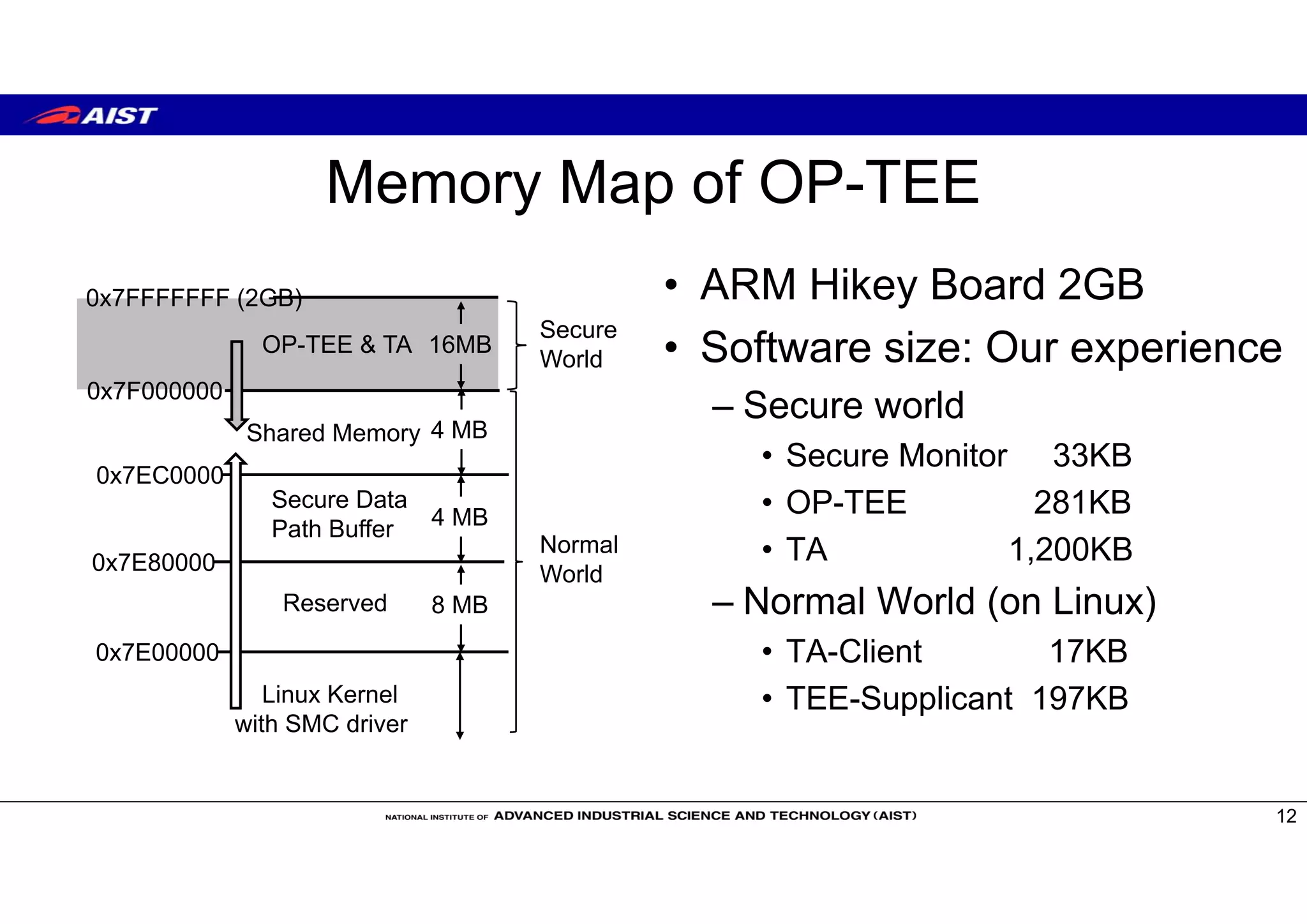
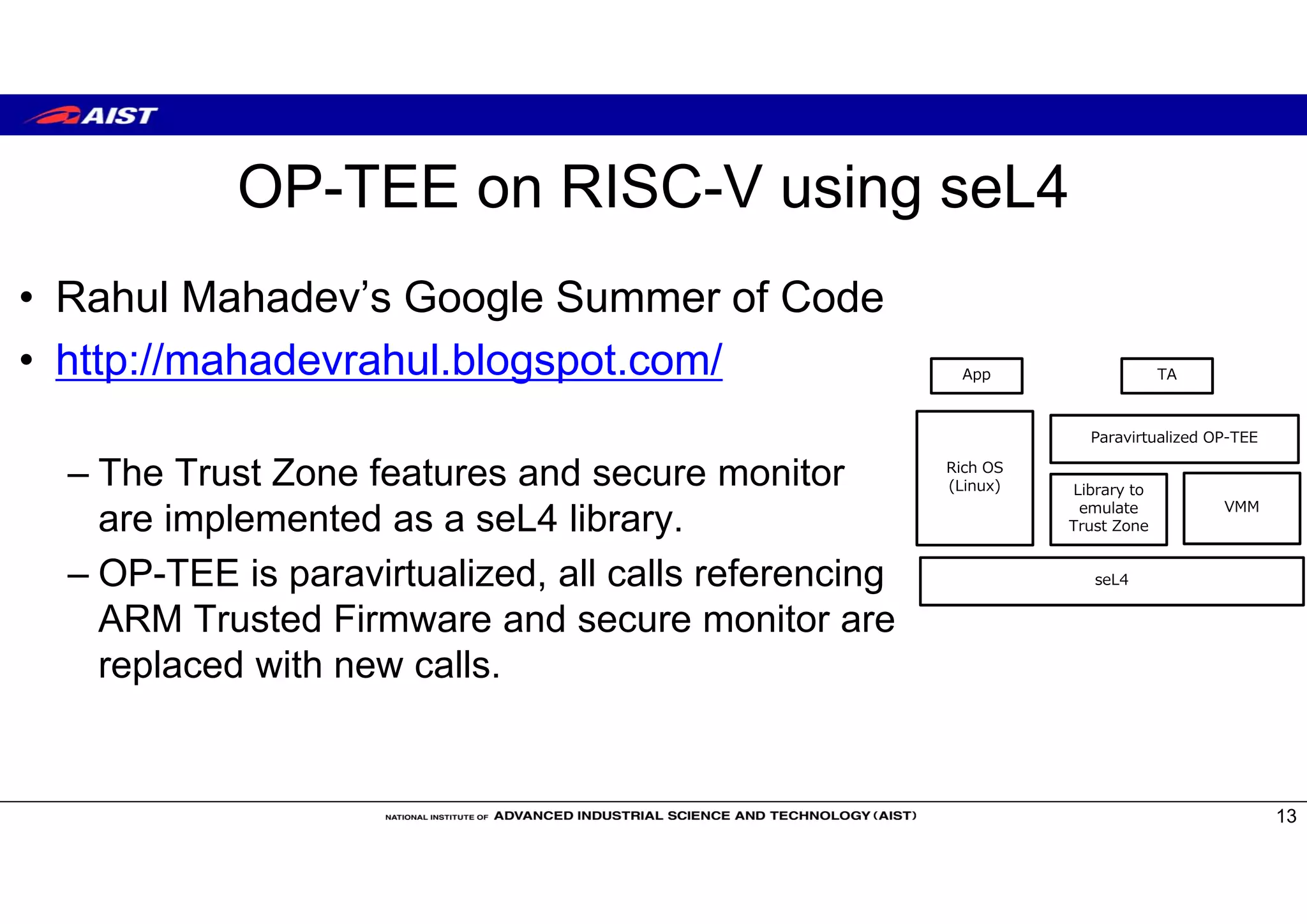
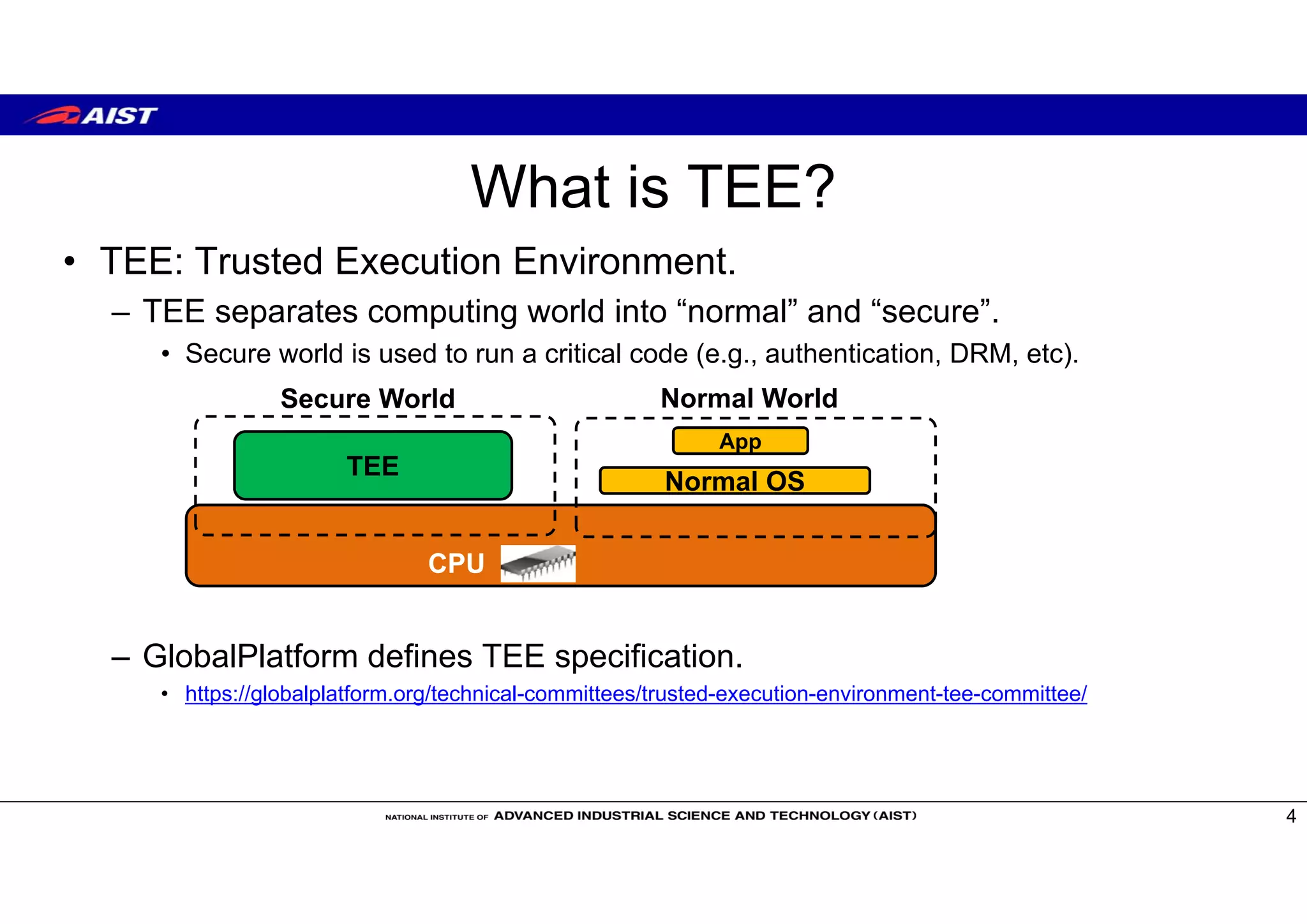
The document discusses Trusted Execution Environments (TEEs) and running the Open Portable Trusted Execution Environment (OP-TEE) trusted operating system on RISC-V. It provides an overview of TEEs, describes OP-TEE and the requirements to implement it on RISC-V, including developing a boot sequence, kernel driver, and libraries. The document also compares TEE implementations on ARM TrustZone and Intel SGX and covers memory mapping when running OP-TEE on ARM-based boards.


![HIEE: Hardware-assisted Isolated Execution Environments*
• HIEE is used for important process which is independent of OS.
• Current CPU has HIEE.
– X86 SMM: System Management Mode
• Used by BIOS/UEFI.
– Intel’s ME: Management Engine.
• Run MINIX. Used for remote power control.
– Intel SGX: Software Guard execution
– ARM Trust Zone
3
* F.Zhang and H.Zhang, SoK:A Study of Using Hardware-assisted Isolated Execution
Environments for Security[HASP16]
They are not programmable for a user.
They are programmable for a user.
They are used for TEE.](https://image.slidesharecdn.com/risc-v-day-tokyo20181018-suzaki-181018081042/75/RISC-V-Day-Tokyo2018-suzaki-3-2048.jpg)
![TEE projects on RISC-V
• Sanctum [MIT project, USENIX Sec’16]
• KeyStone [UCB project]
– https://keystone-enclave.org/
• MultiZone [Hex-Five product]
– https://hex-five.com/
• TEE WG of RISC-V Foundation
6
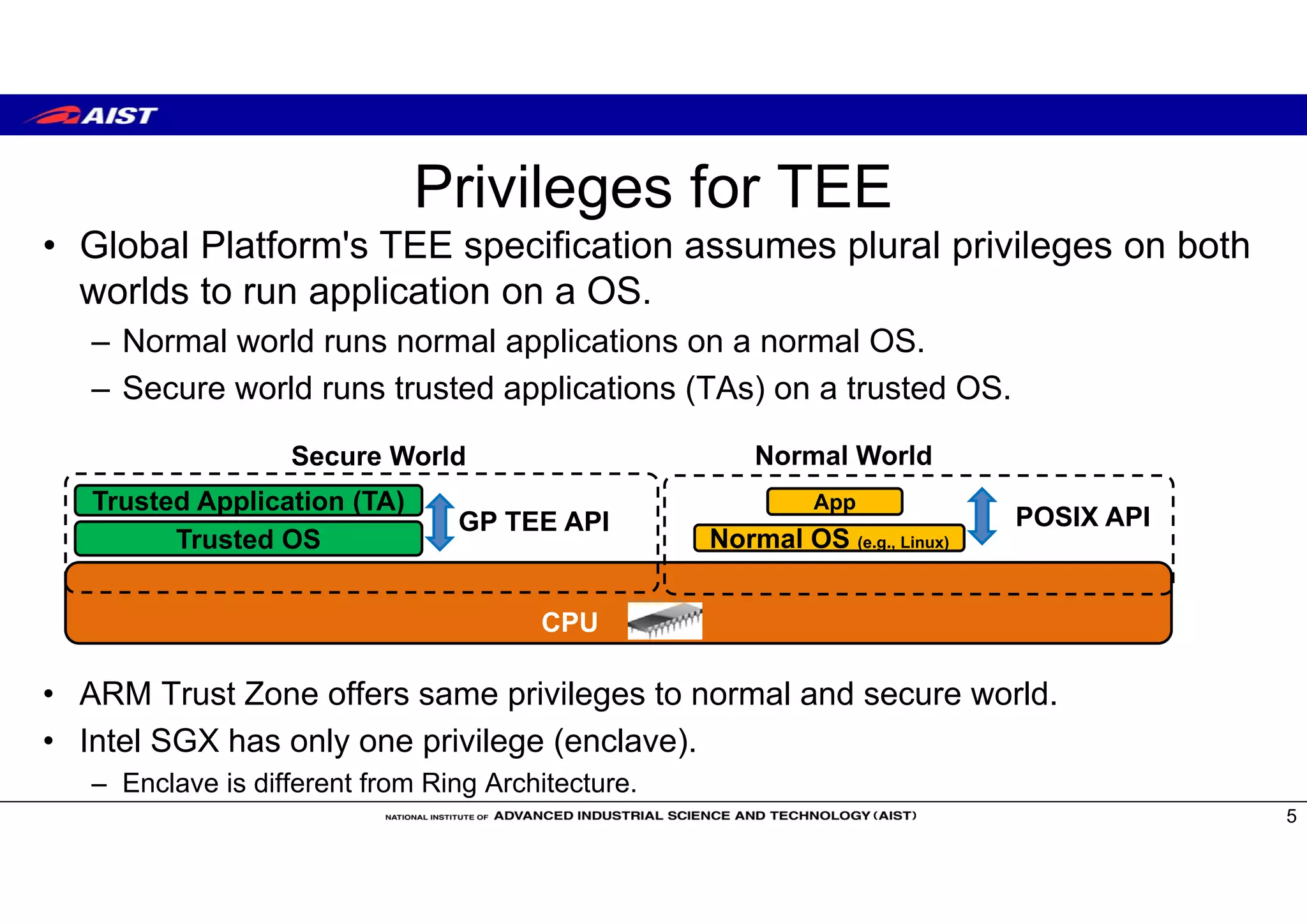
Intel SGX type
One special privilege (Enclave)
ARM Trust Zone type
plural privileges
easy to implement GlobalPlatform
style Trusted OS](https://image.slidesharecdn.com/risc-v-day-tokyo20181018-suzaki-181018081042/75/RISC-V-Day-Tokyo2018-suzaki-6-2048.jpg)
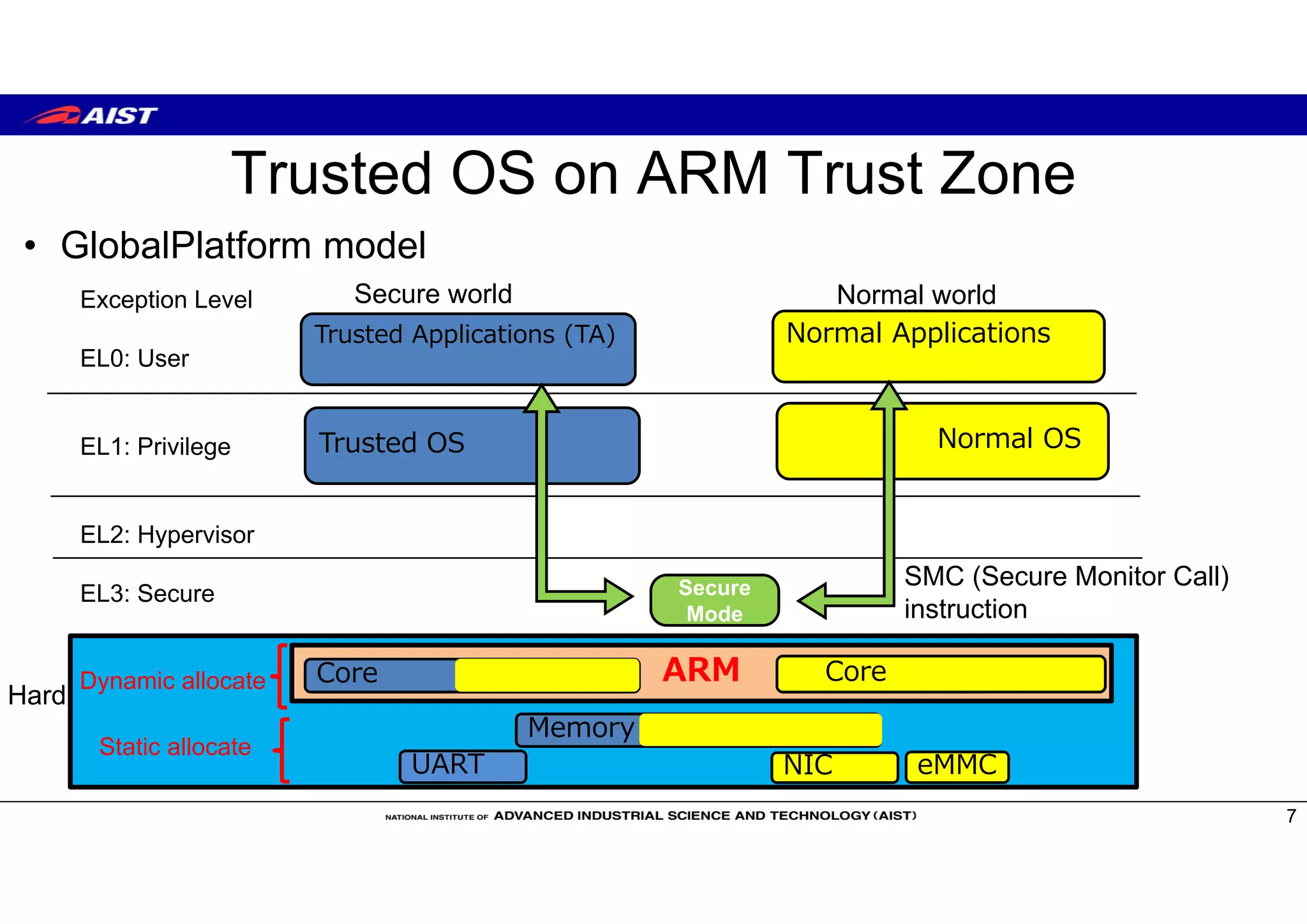
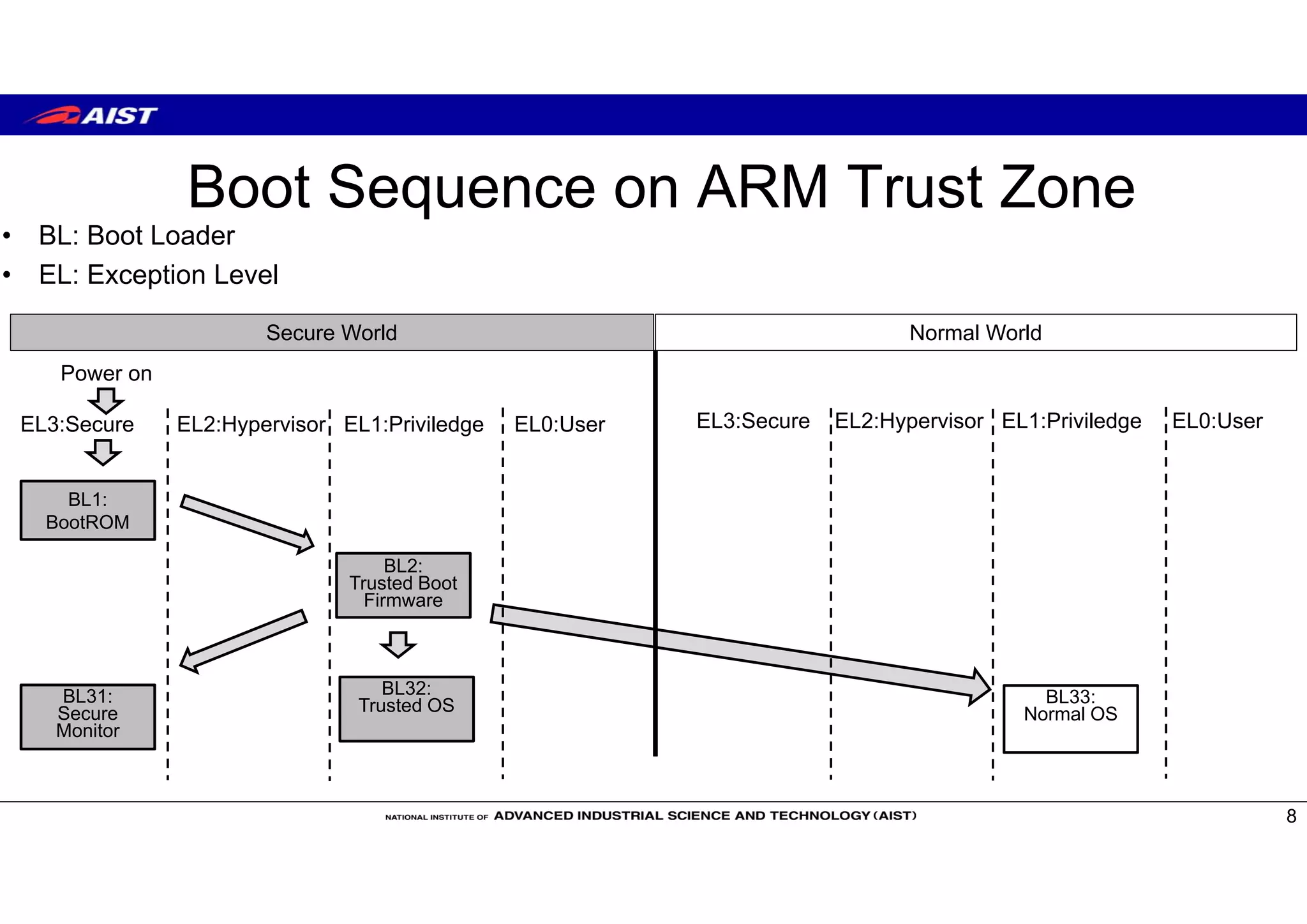
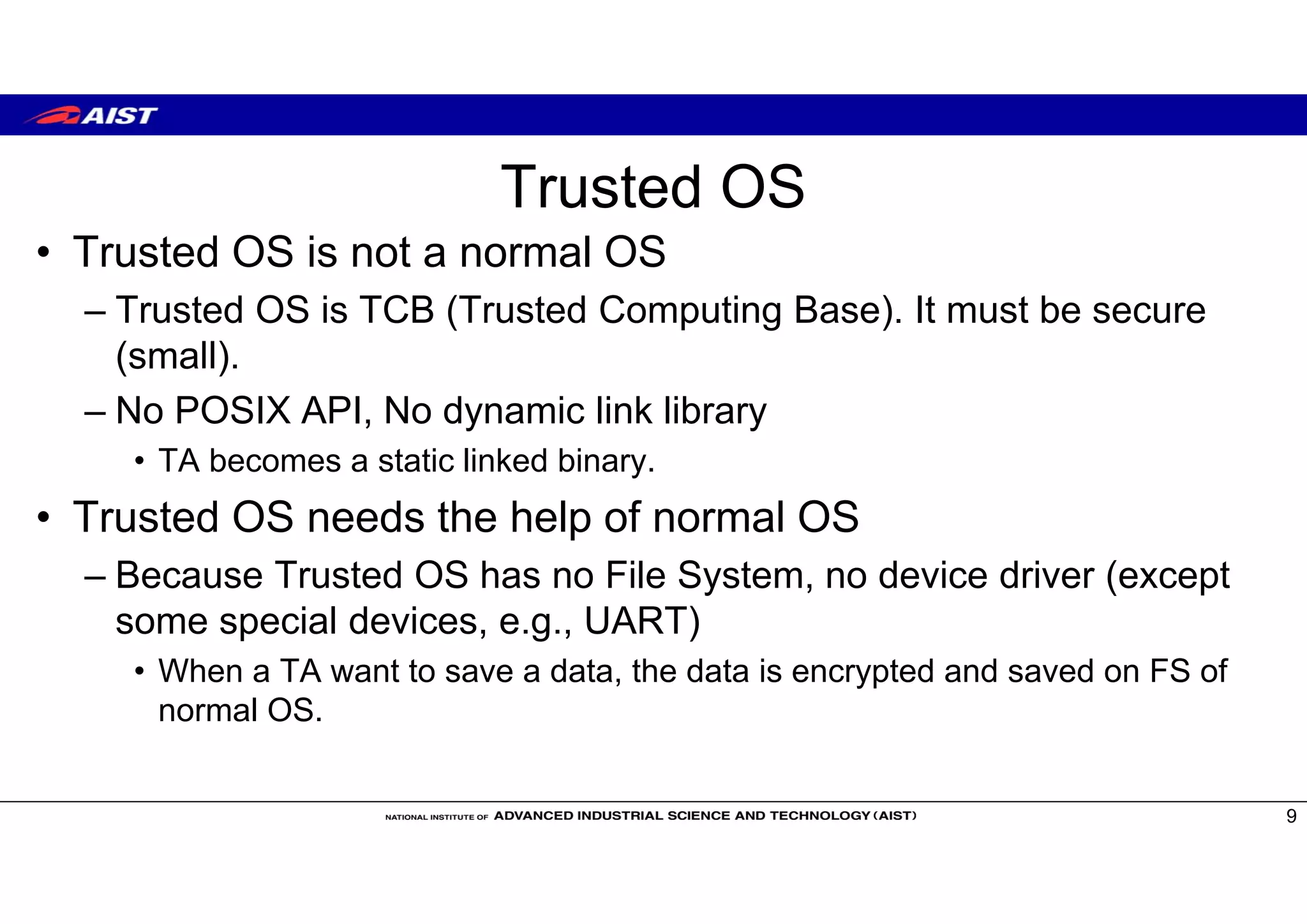
![Trusted OS
• Open Source Trusted OS
– OP-TEE (Linaro) https://github.com/OP-TEE
– Open-TEE (Aalto University[TrustCom15]) https://open-tee.github.io/
– Trusty (Google) https://source.android.com/security/trusty/index.html
– SierraTEE (Sierra) https://www.sierraware.com/open-source-ARM-TrustZone.html
• Enterprise Trusted OS
– Apple’s Secure Enclave
– Qualcomm’s QSEE
– Samsung’s Knox https://www.samsungknox.com/en
– Trastonic Kinibi and MobiCore
10](https://image.slidesharecdn.com/risc-v-day-tokyo20181018-suzaki-181018081042/75/RISC-V-Day-Tokyo2018-suzaki-10-2048.jpg)