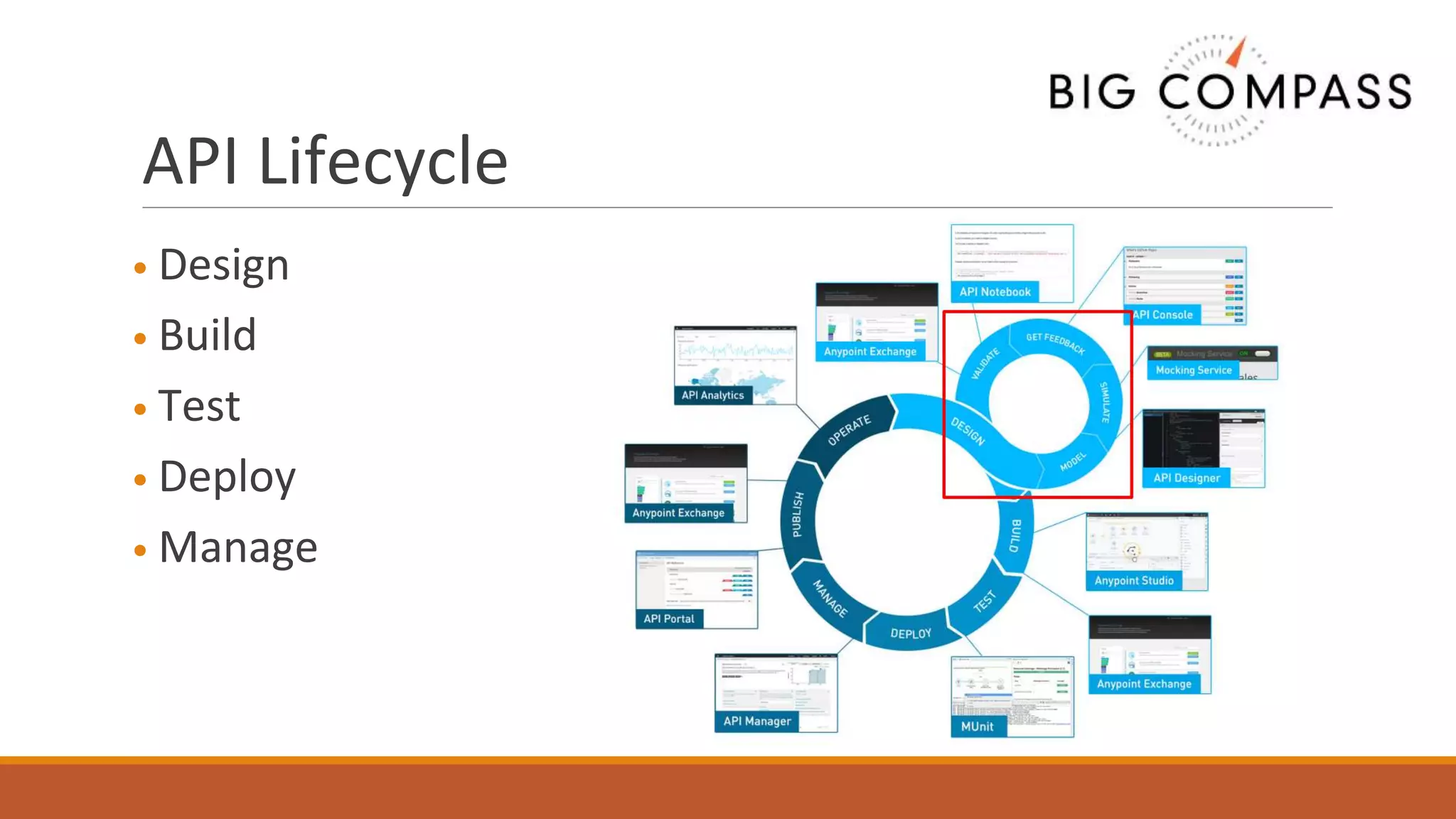
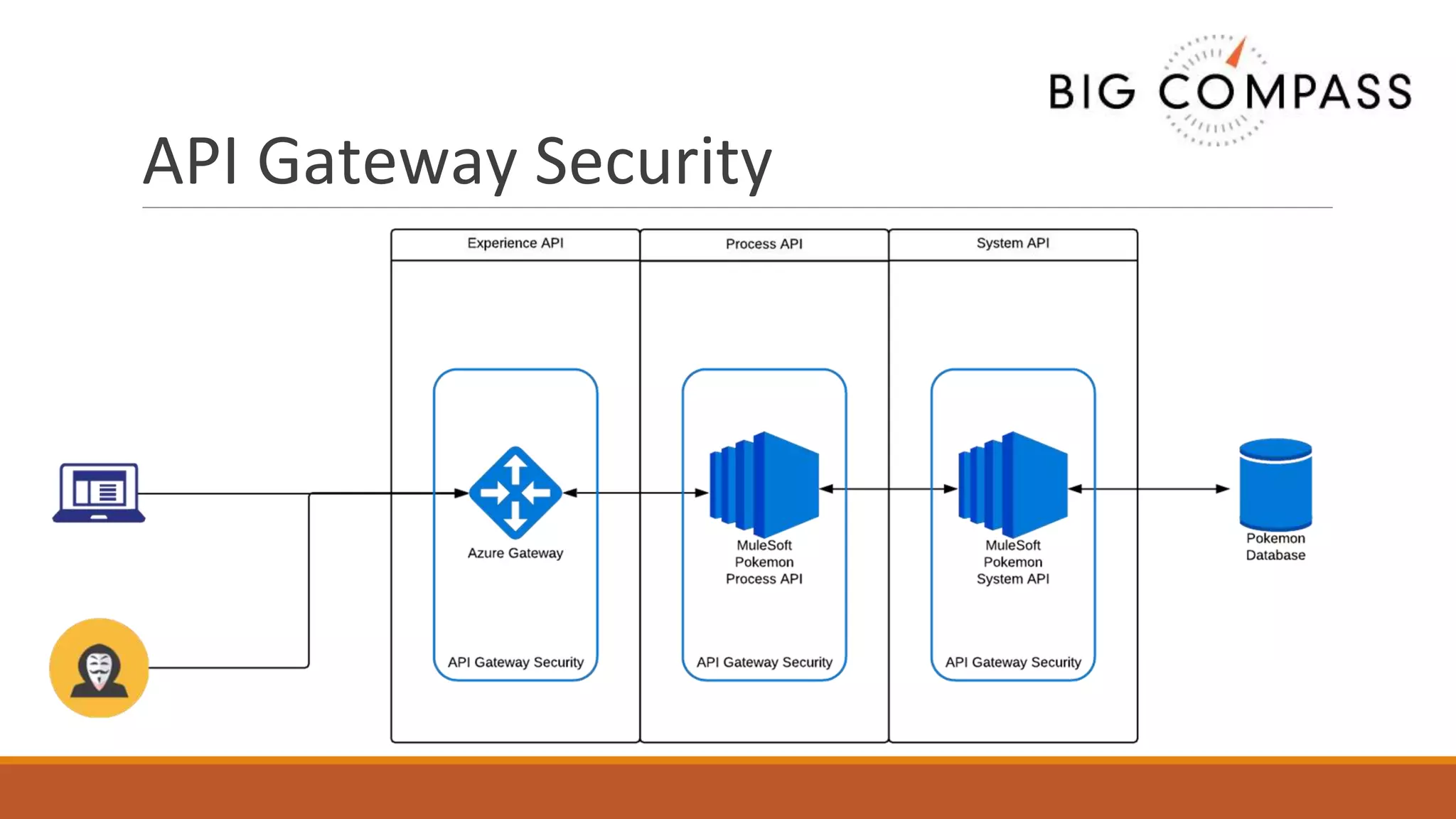
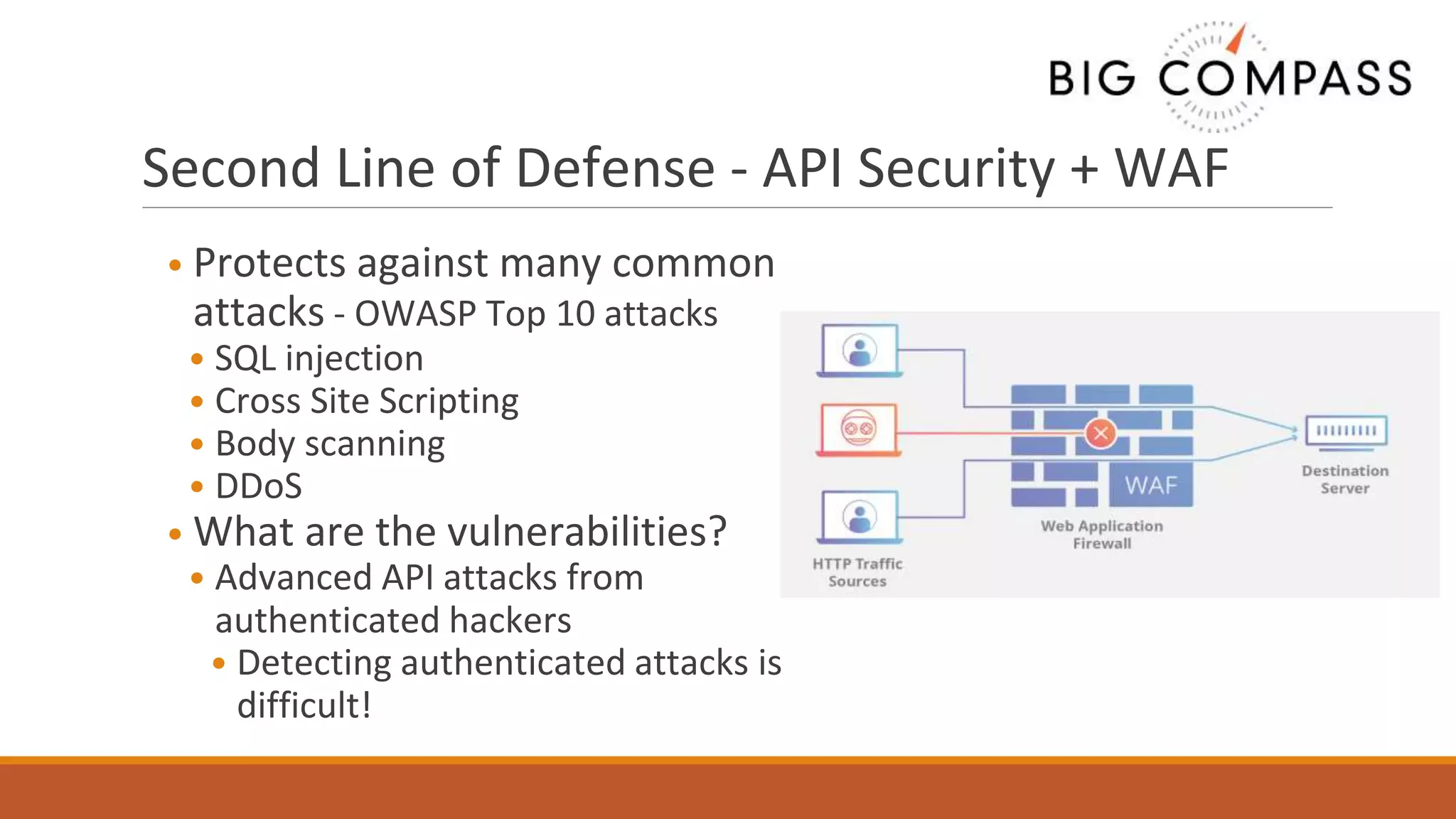
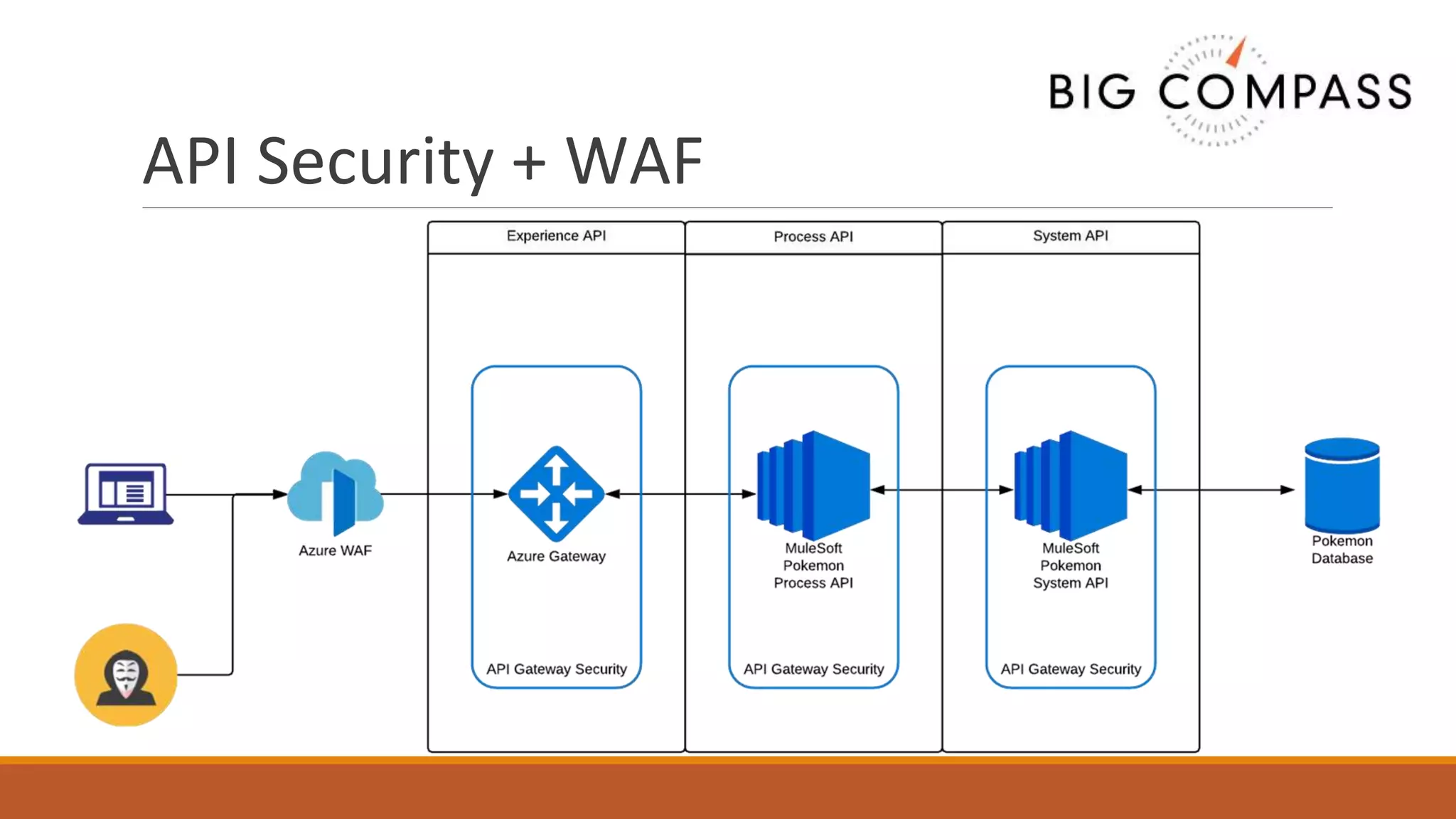
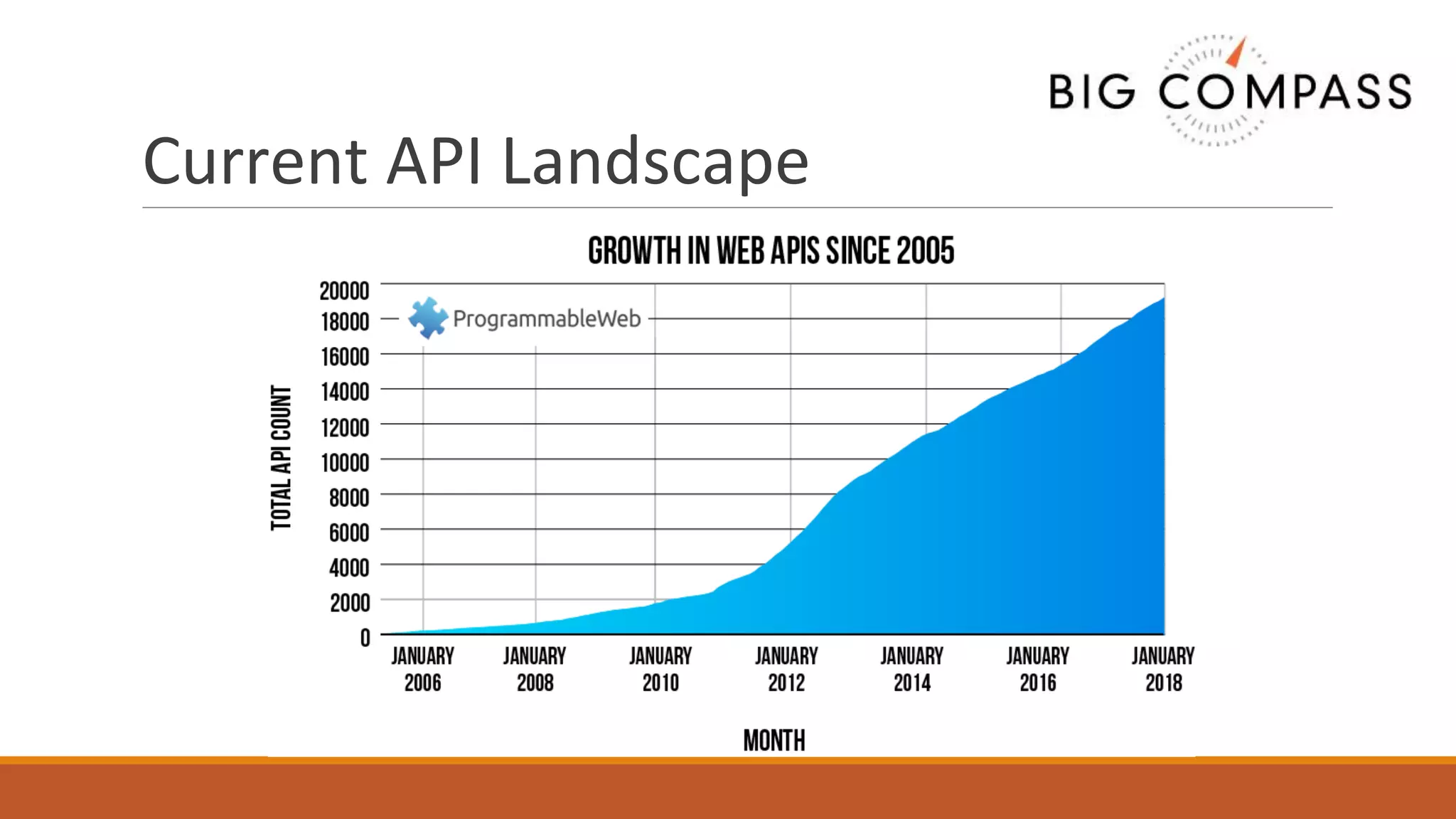
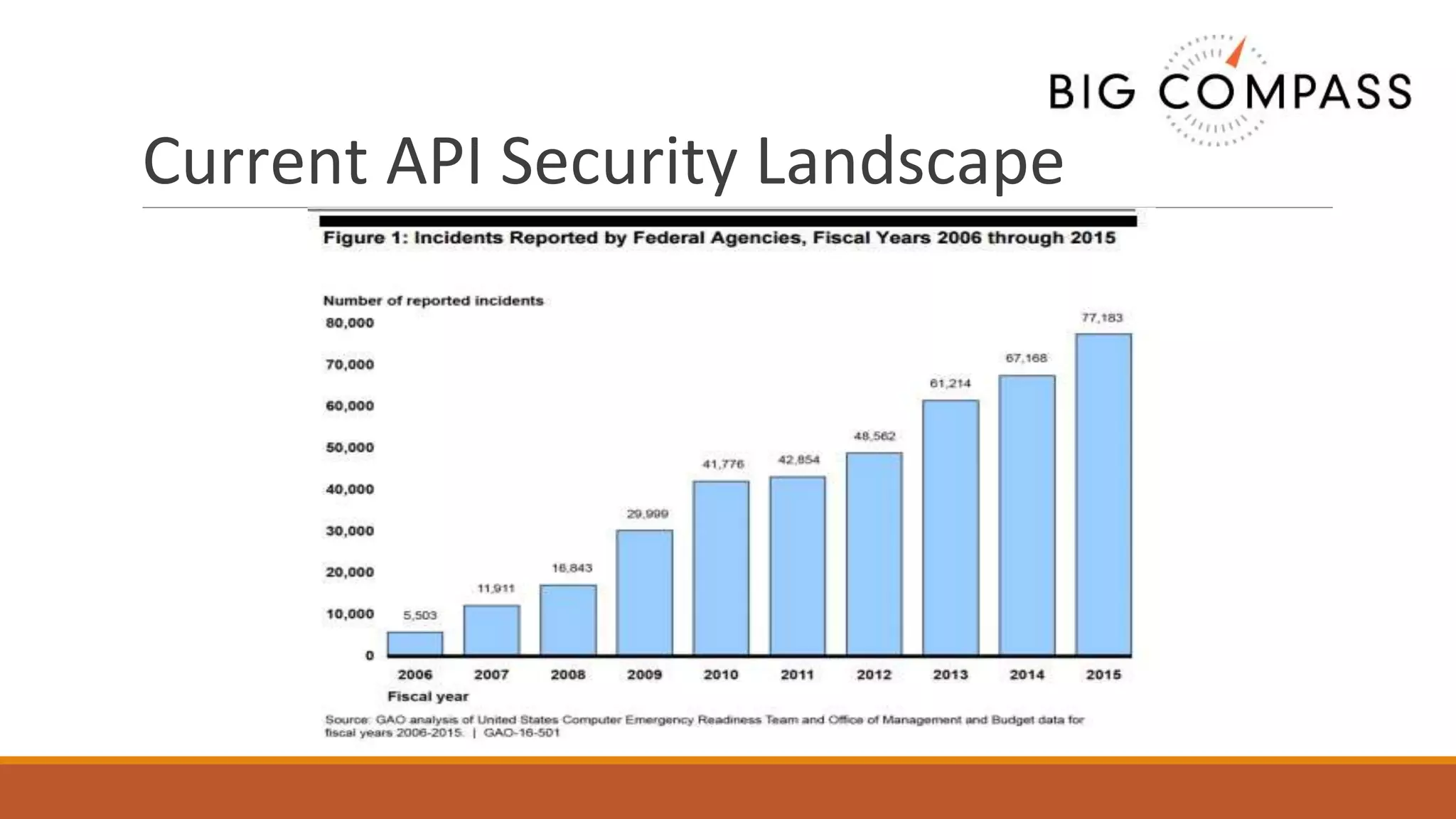
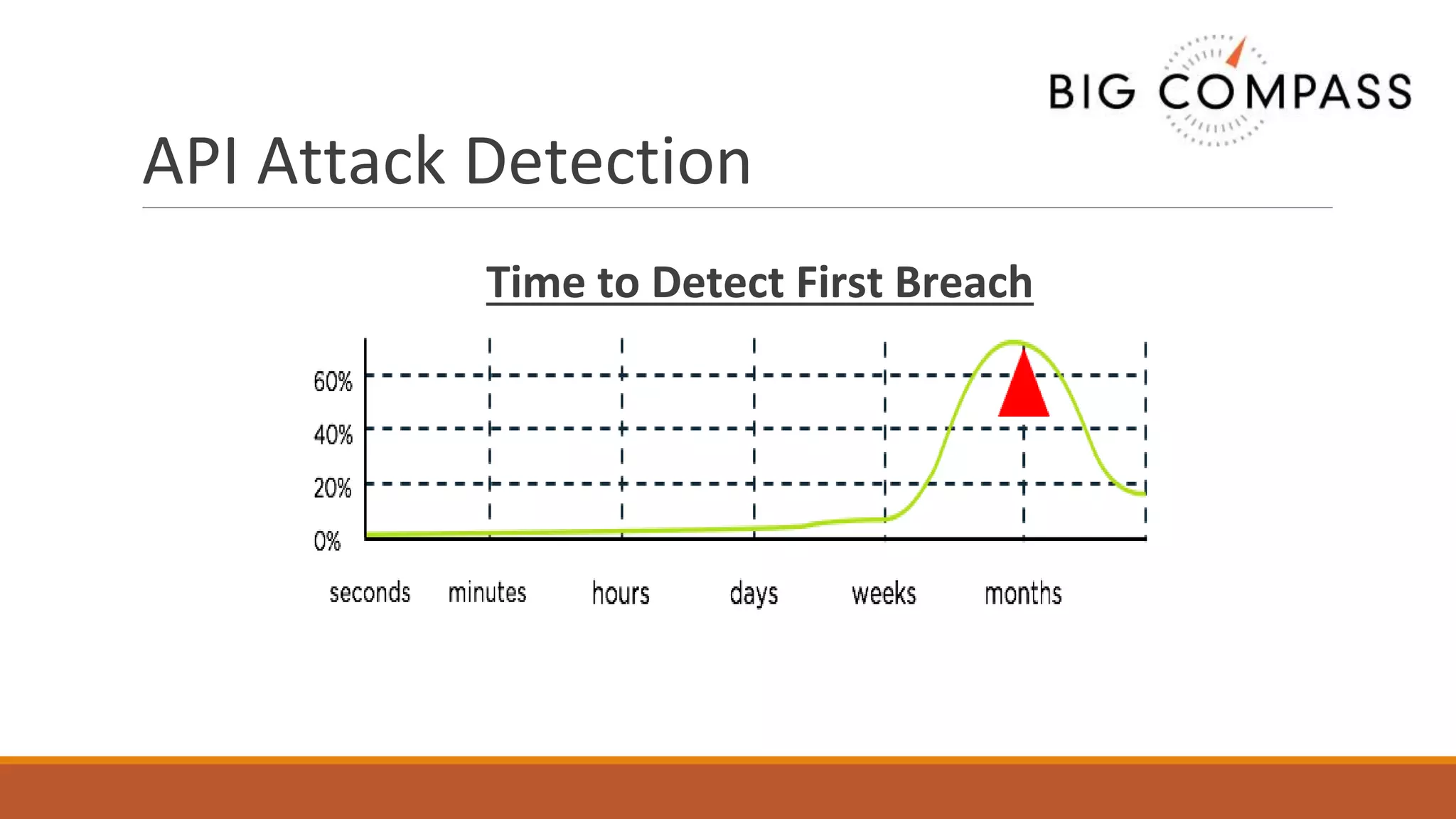
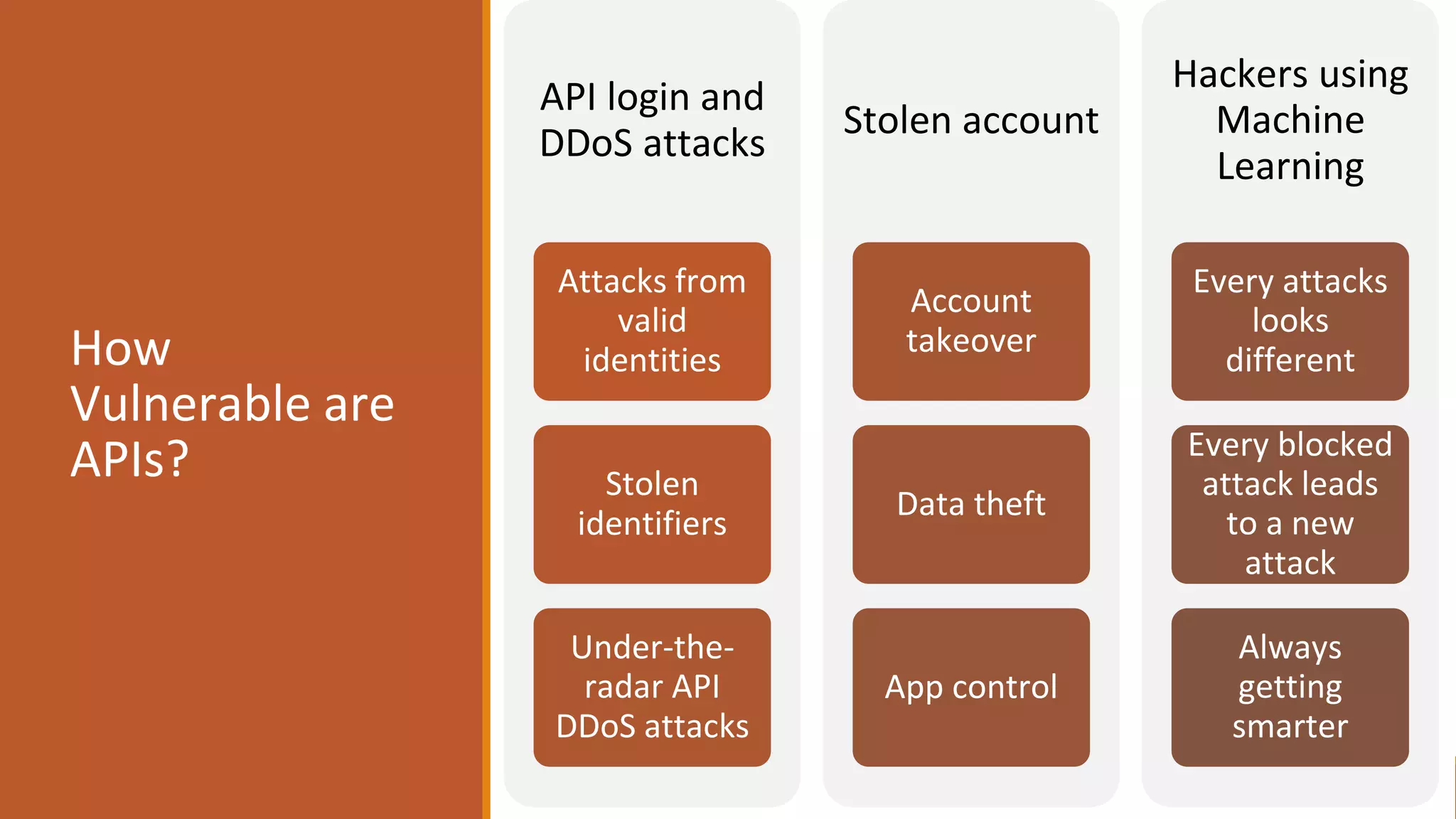
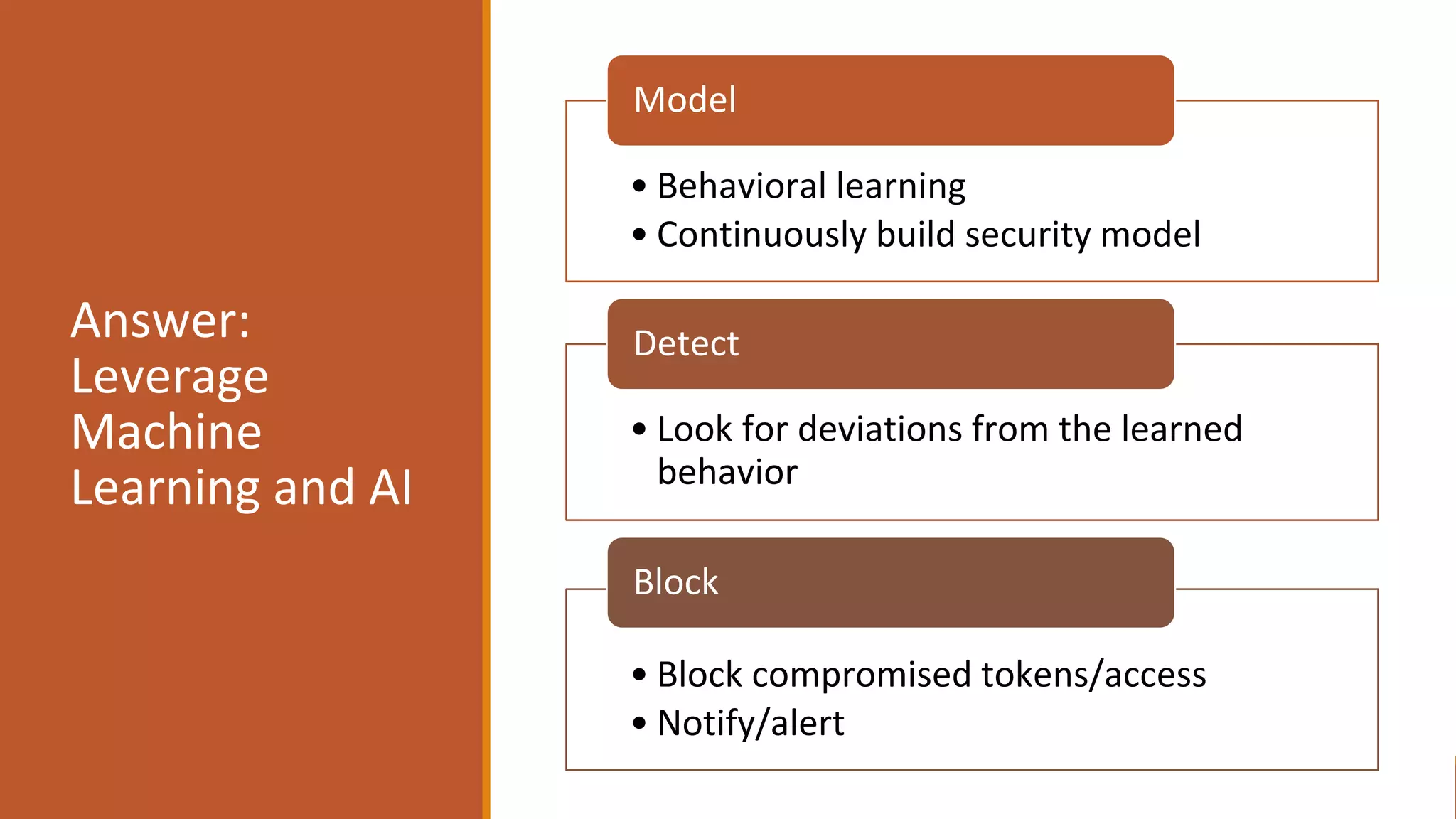
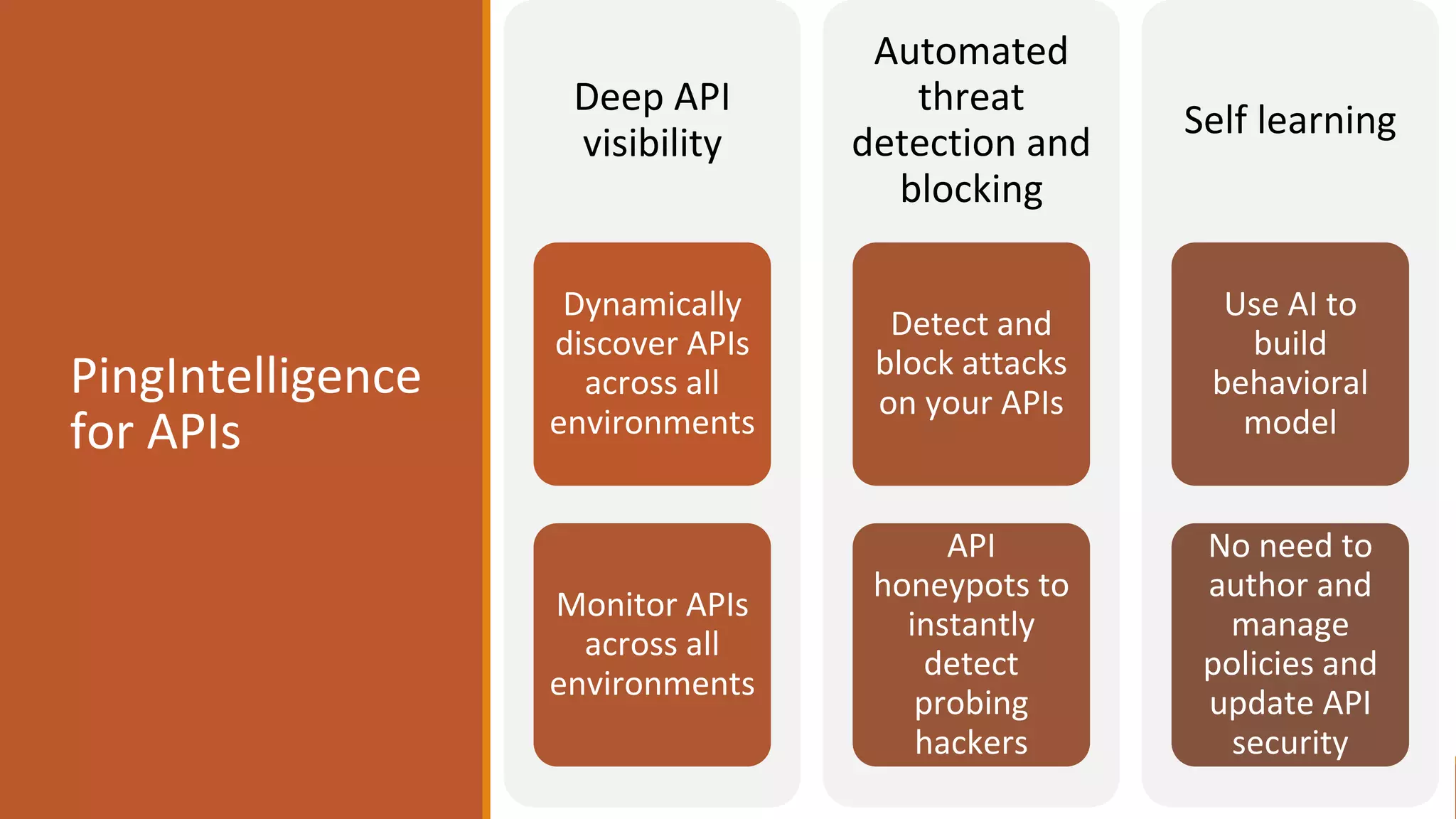
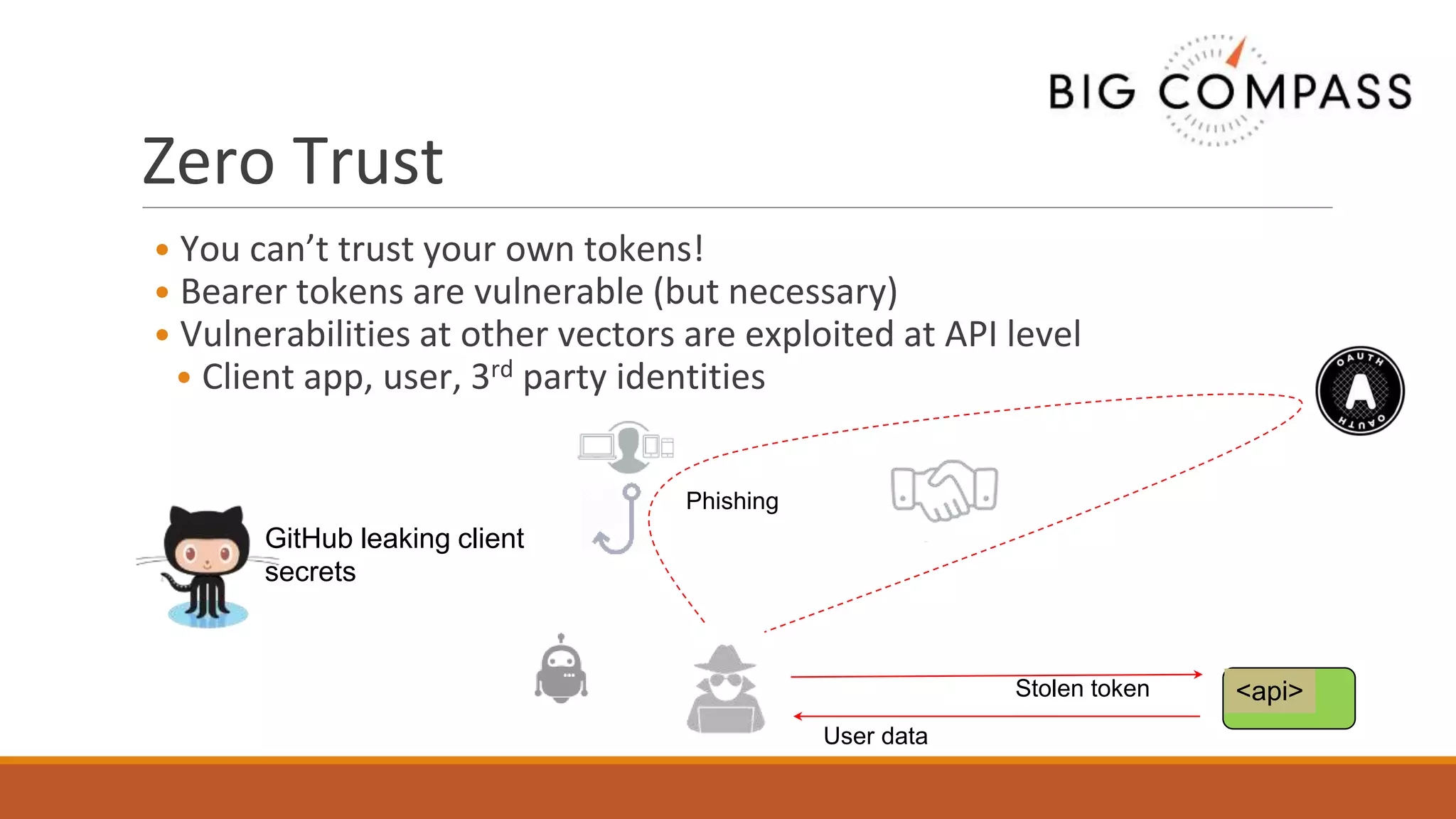
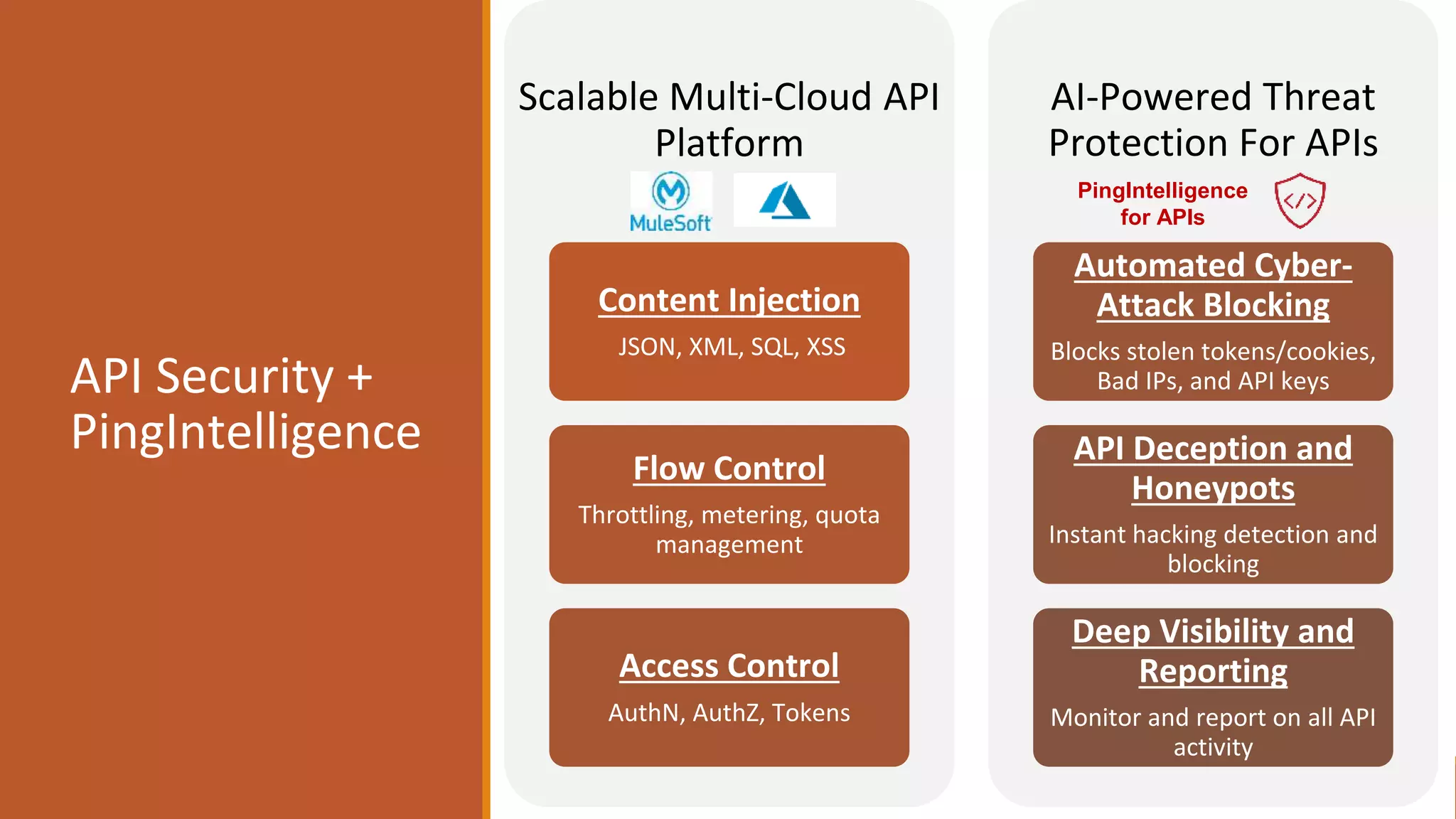
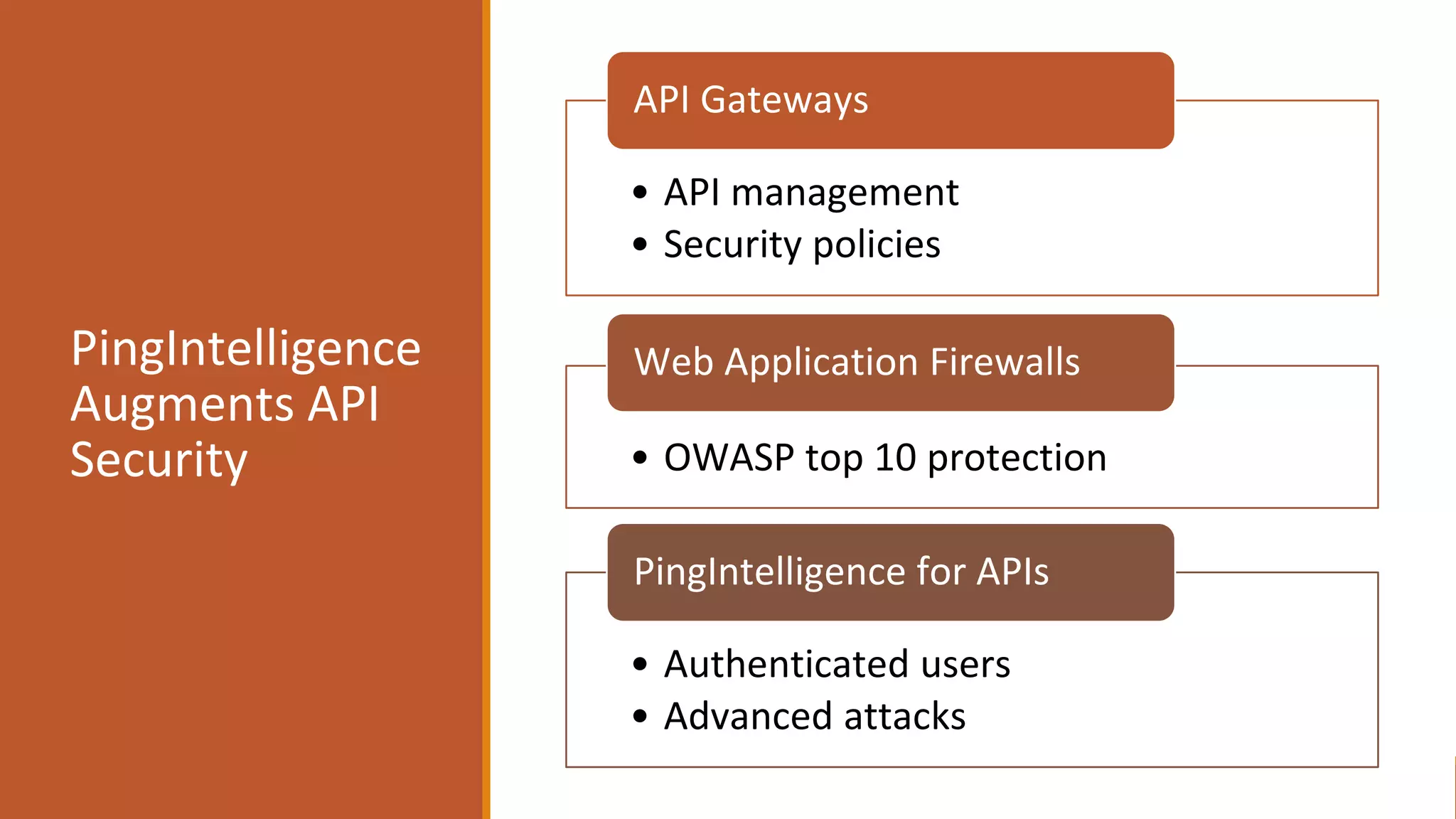
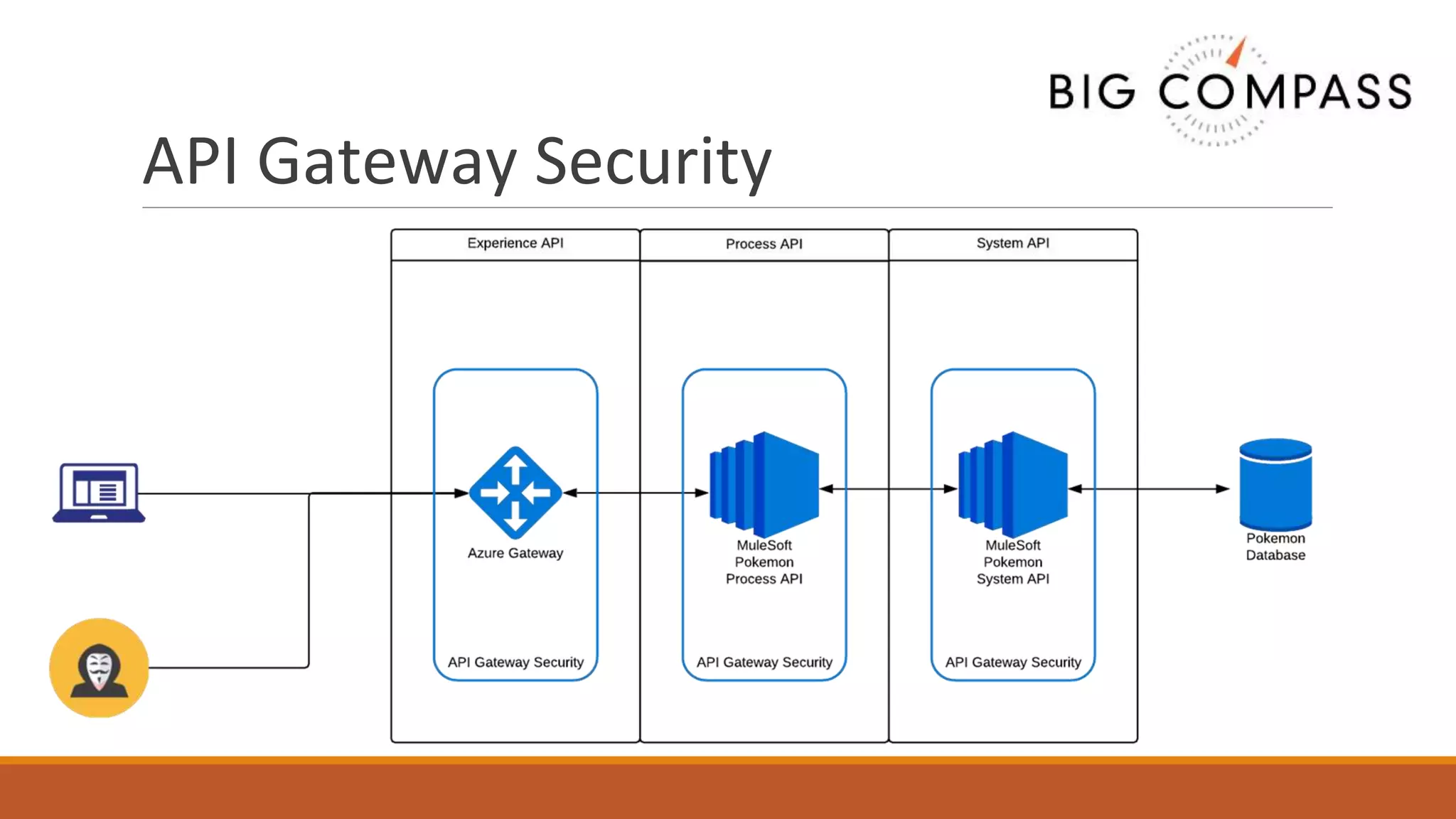
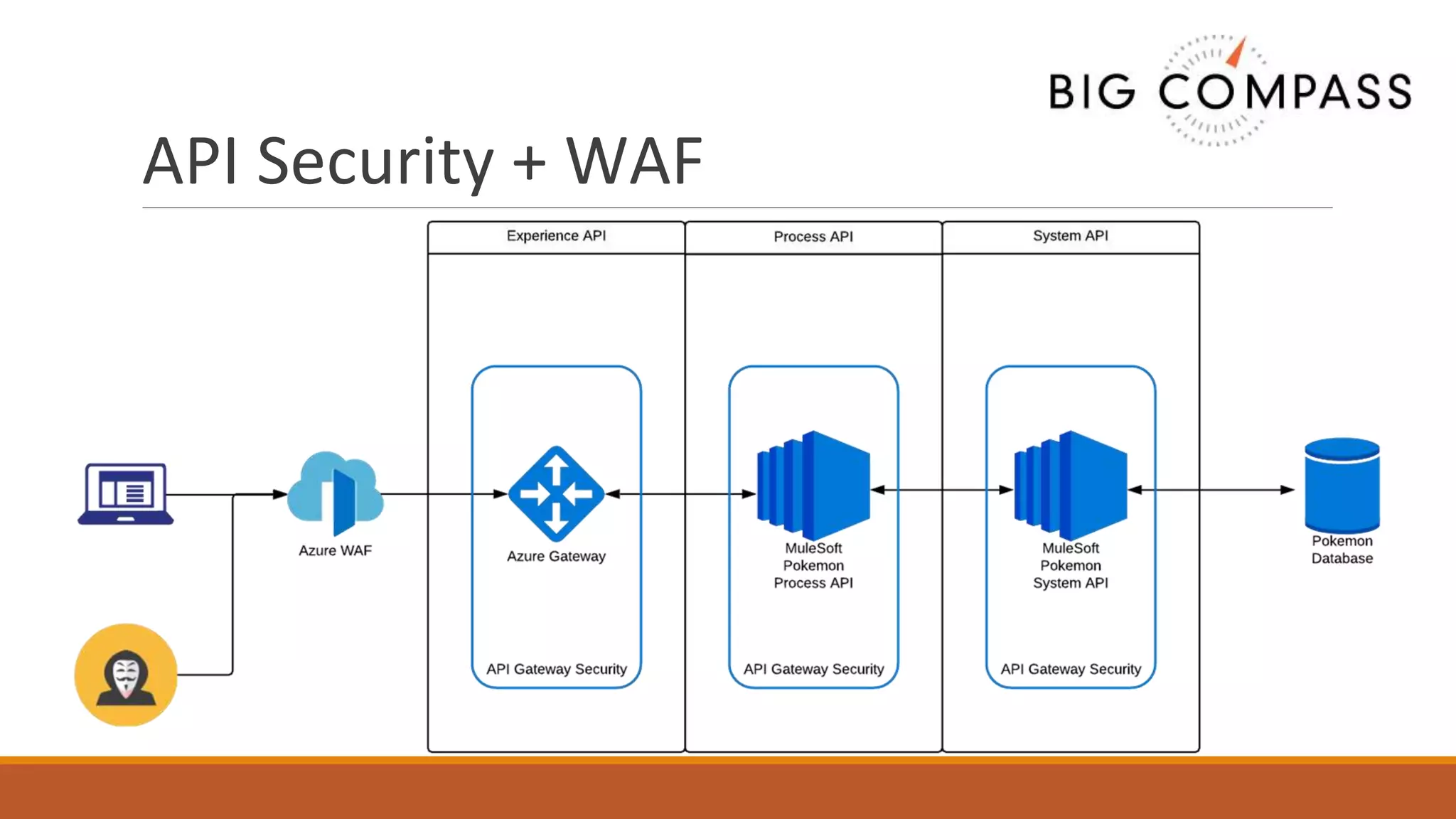
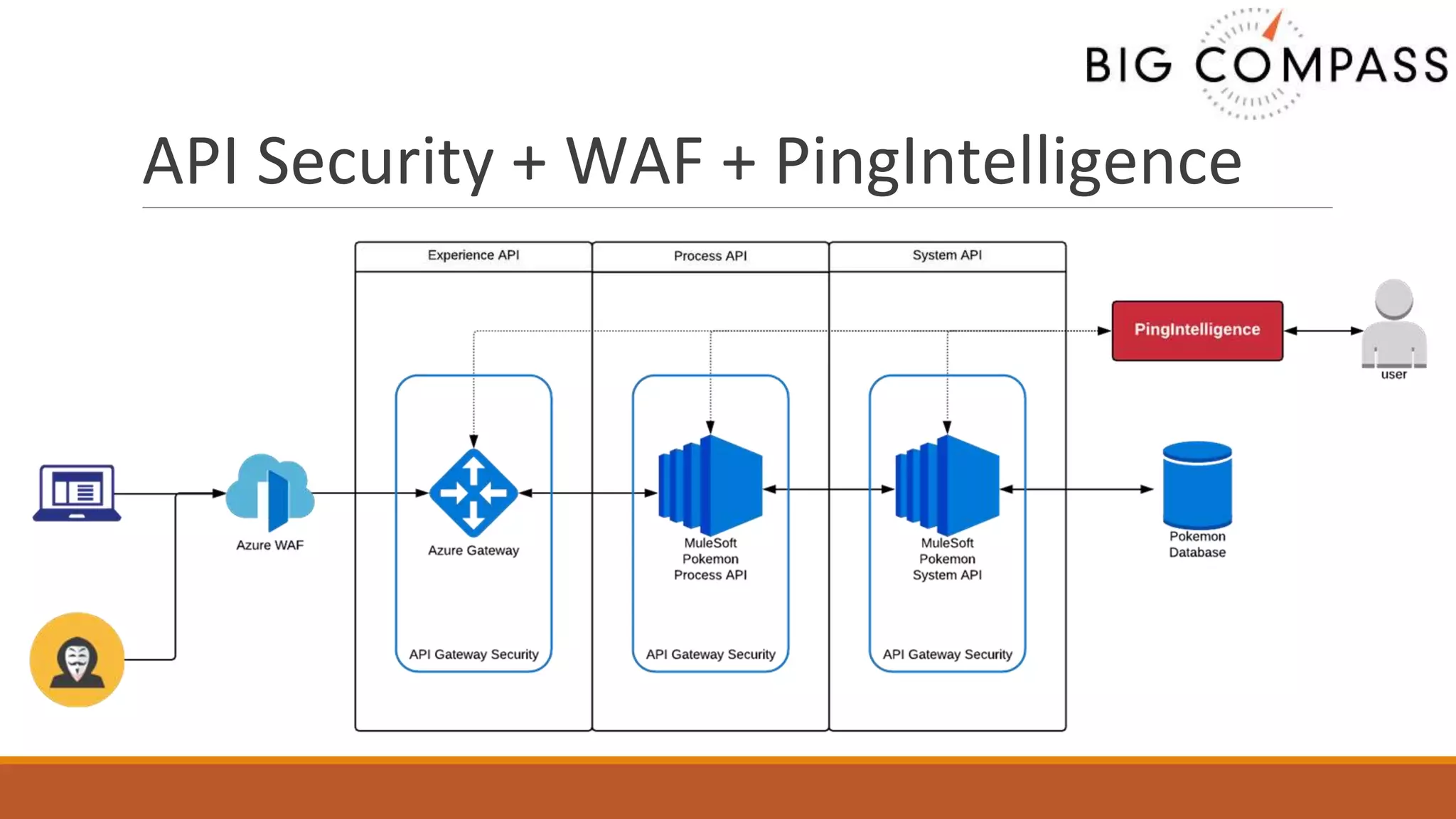
The document outlines critical aspects of API security, emphasizing the need for a layered approach involving API management, gateway security, and advanced threat detection using AI and machine learning. It highlights the current vulnerabilities in the API landscape, noting that many organizations lack confidence in their ability to detect malicious activities and emphasizing the importance of a zero trust strategy. Additional insights include the necessity for automated threat detection and the role of technologies like PingIntelligence in enhancing API security.