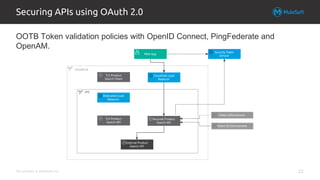
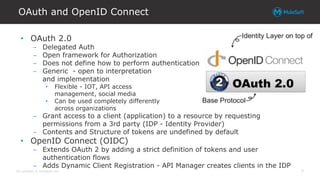
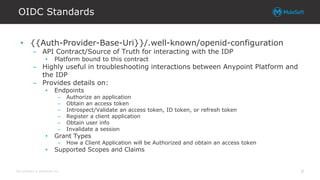
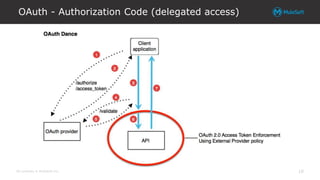
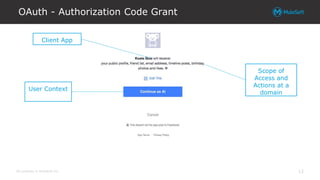
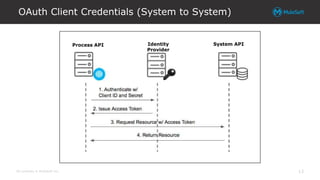
The document explores integrating OAuth and data access control into the Anypoint platform, emphasizing a zero-trust security model that prioritizes understanding and validating identities and contexts over traditional perimeter defense. It details the implementation of OAuth 2.0 and OpenID Connect for secure API communication, highlighting various authorization flows and the importance of scopes, claims, and token validation. Additionally, it discusses common pitfalls, lessons learned, and alternative security methods to enhance API protection.





![All contents © MuleSoft Inc.
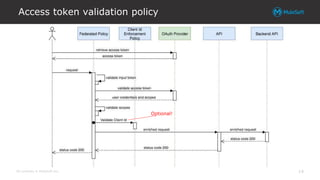
Validating Tokens
16
• OpenID Connect Access Token Validation Policy
– Validates token in the Authorization header against the IDP (cannot reference a
different target)
– By default validates token issued to valid client app
• Can be disabled!
– Allows token to be validated by downstream API it was not issued for
– Expose Headers will make all claim/user info available to the API for RBAC/ABAC
• JWT Validation
– Locally validates the contents of the token against the configured policy and IDP
public key
– Can validate token was issued to the expected client app/ID
– Can validate custom claims against literals or DW expressions
• claim : vars.claimSet.claim == attributes.queryParams.claim
– Cannot be used if the IDP is issuing Opaque tokens
– Token can be encrypted, and signed (IDP configuration)
– Claim information passed to the API
#[authentication.properties.claims.<claimName>]](https://image.slidesharecdn.com/securingapis-oauthandfinegrainedaccesscontrol-200409193820/85/Securing-ap-is-oauth-and-fine-grained-access-control-16-320.jpg)


![All contents © MuleSoft Inc.
Pitfalls and Lessons learned
19
• Not even OIDC is consistent (Up to the IDP)
– +/- Dynamic Client Registration (OneLogin, Azure AD)
– +/- Support for Client Credentials Grants (Salesforce, Okta)
– Leverage what you can from OIDC and augment with other API Security controls
• Register system to system clients with Auth code grant types, but only use client
ID/secret policies, or add Client Credentials if supported
• Anypoint Platform depends on the well-known-configuration data
– You may have to build interactions directly to the IDP
– You may have to build custom validation policies
• Client Based policies can be driven by access token validation
– Reference #[authentication.principal]
• OAuth Spec has a gap that has not been addressed
– On-behalf-of tokens to allow systems to obtain tokens needed to fulfill an
experience call - In-draft
– Azure AD has implemented a flow to accomplish this
– Example presented today gets close](https://image.slidesharecdn.com/securingapis-oauthandfinegrainedaccesscontrol-200409193820/85/Securing-ap-is-oauth-and-fine-grained-access-control-19-320.jpg)