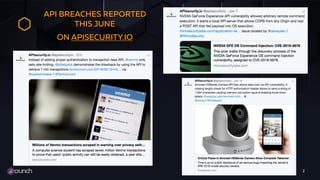
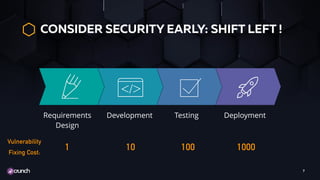
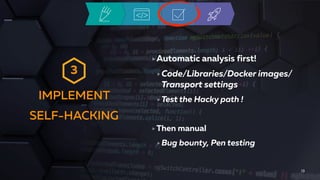
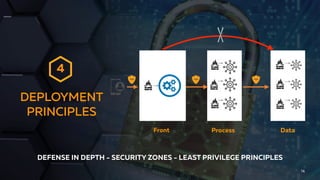
Isabelle Mauny, the Chief Product Officer and co-founder of 42Crunch, addresses concerns about recent API breaches and emphasizes the importance of integrating security early in application development. She advocates for adopting a 'shift left' approach, teaching API security across teams, and automating security measures. The document also provides resources and best practices for effective API security management.