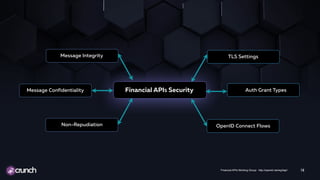
This document discusses the need for API security as APIs increasingly expose enterprise data and processes both internally and externally. It notes that while APIs may seem invisible without a GUI, they can be easily discovered and are vulnerable to the same threats as web applications if not properly secured. The document advocates for a holistic approach to API security that considers authentication, authorization, integrity, confidentiality and other aspects. It also emphasizes that the right security measures depend on the type of API and calls for collaboration between operations, development, security and business teams to implement proper API security.