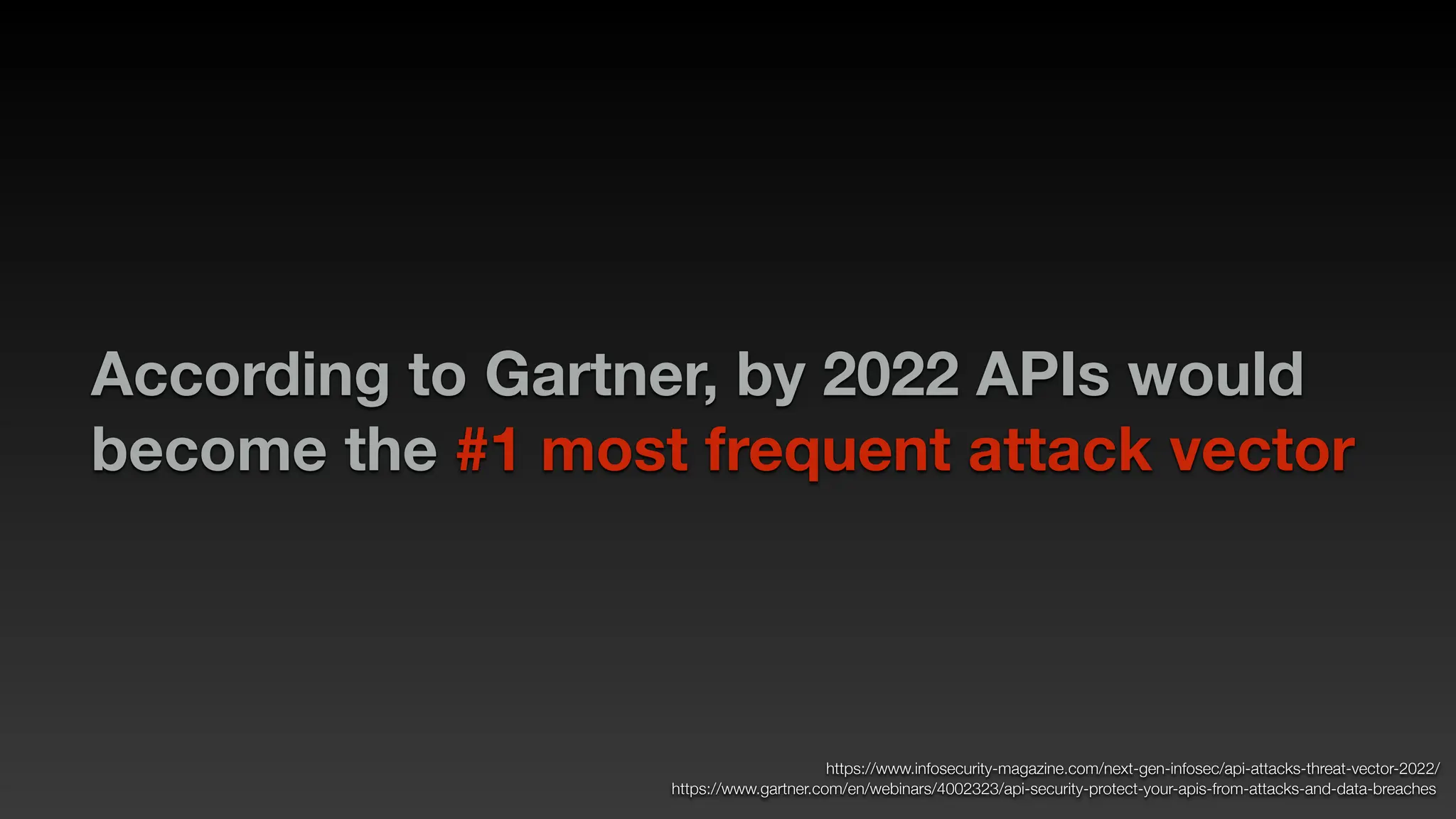
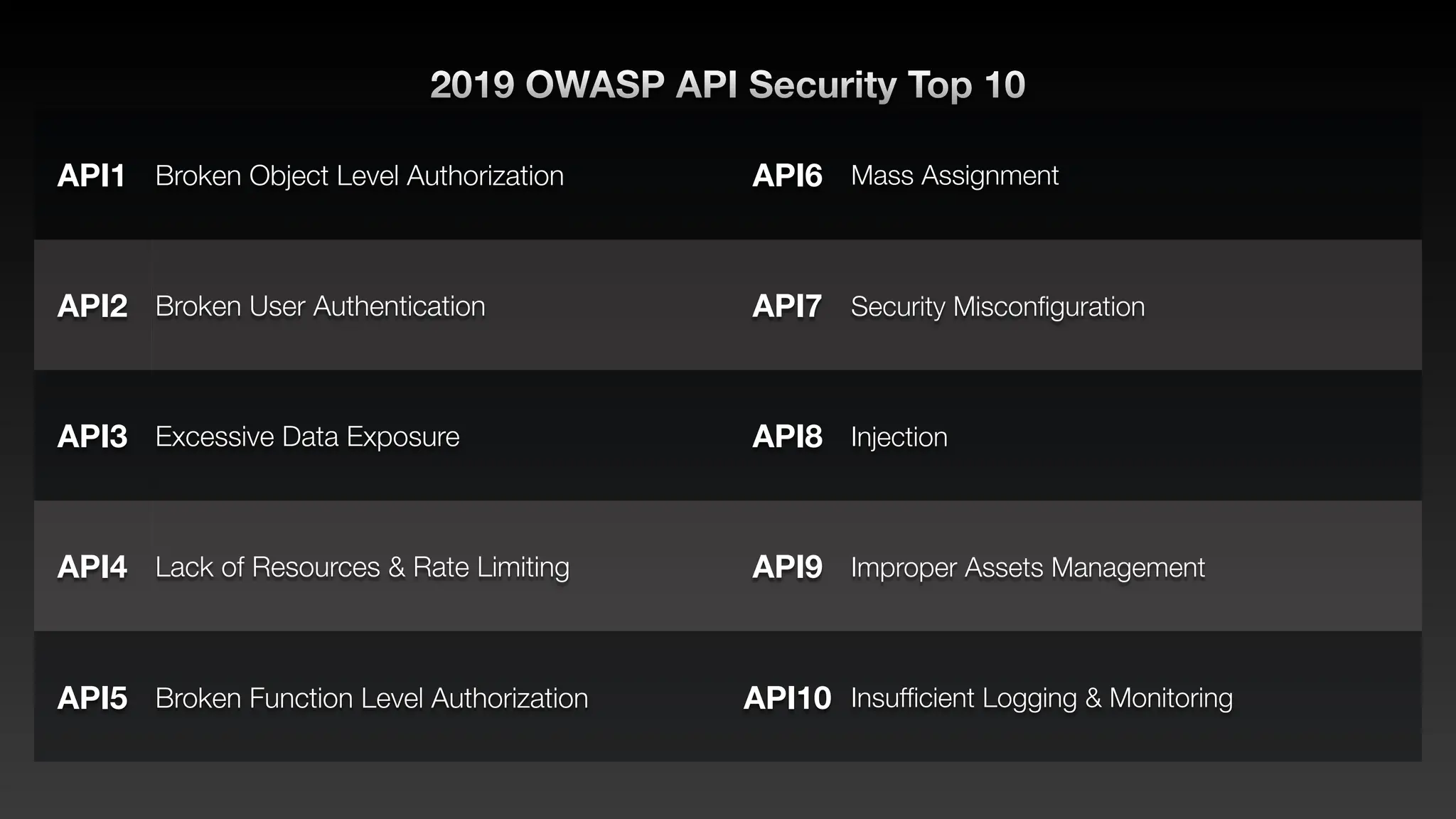
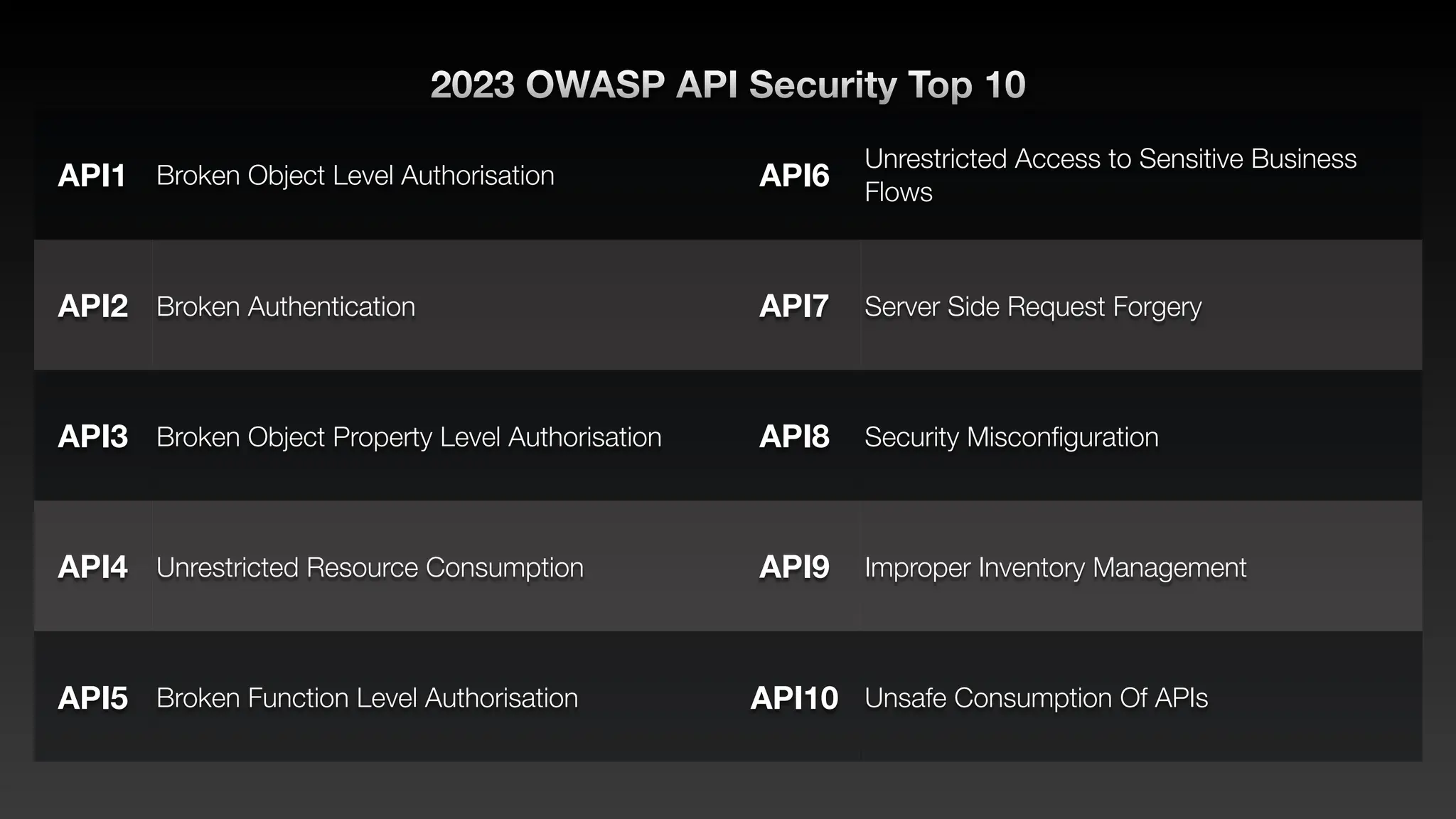
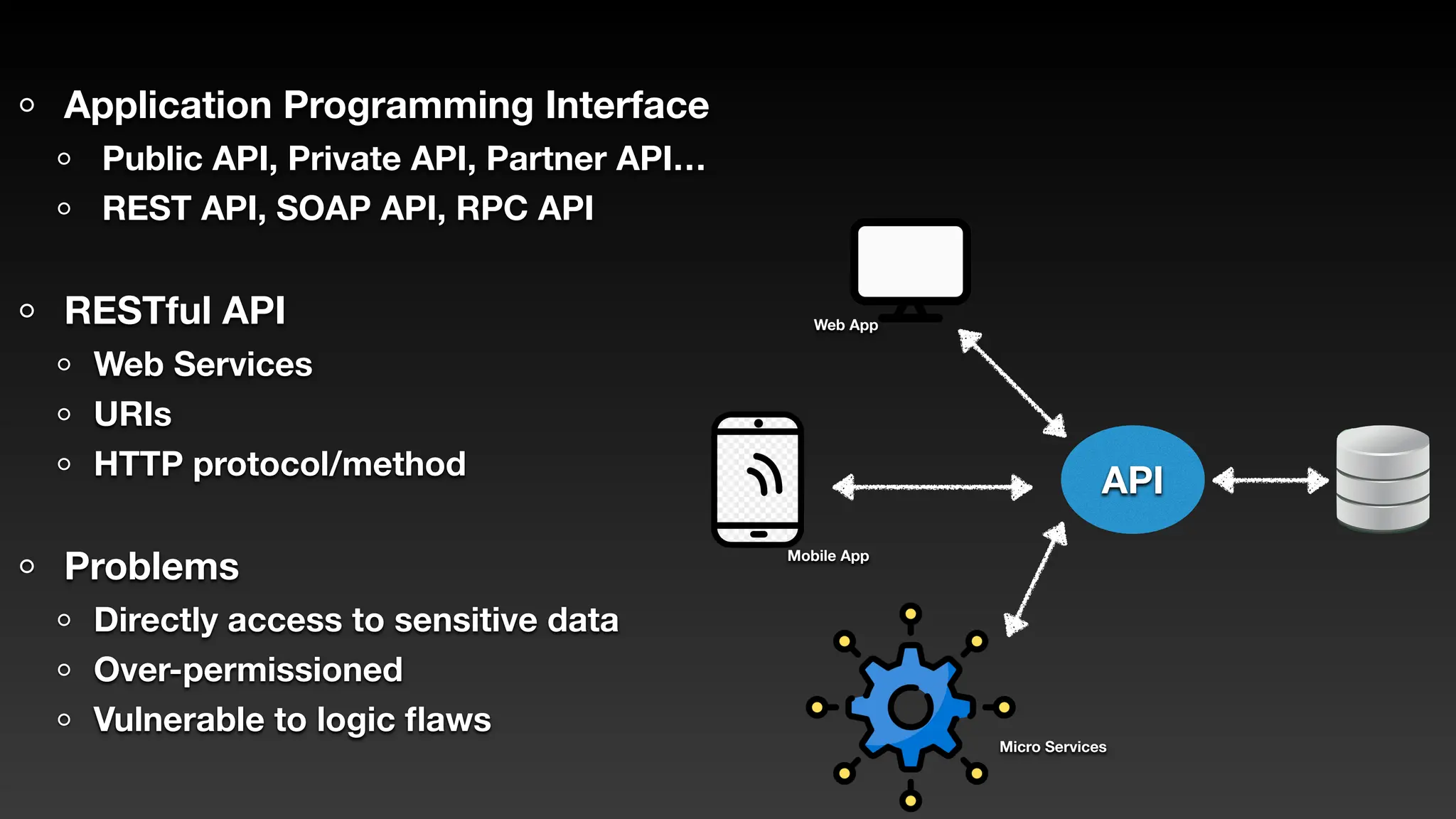
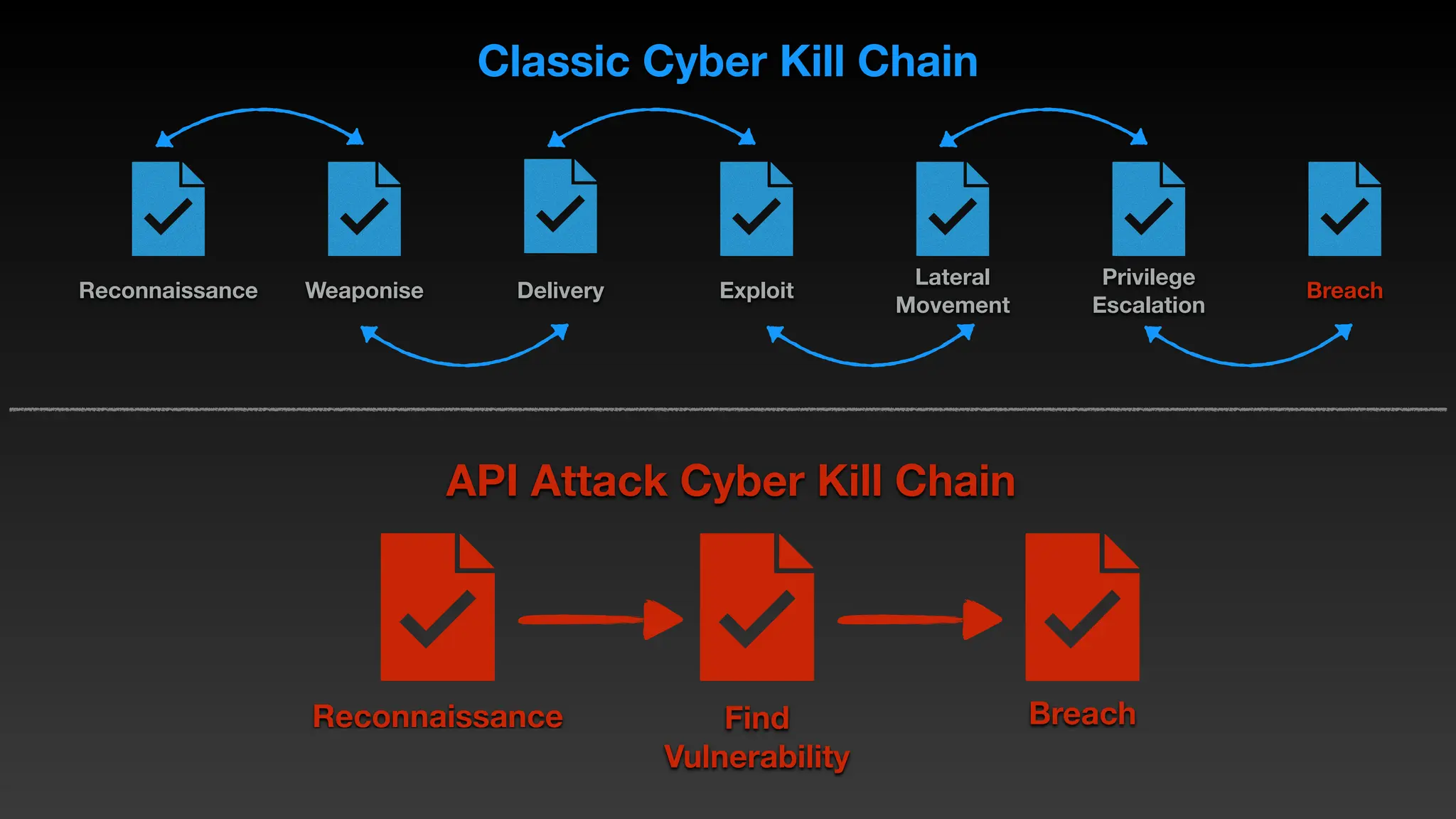
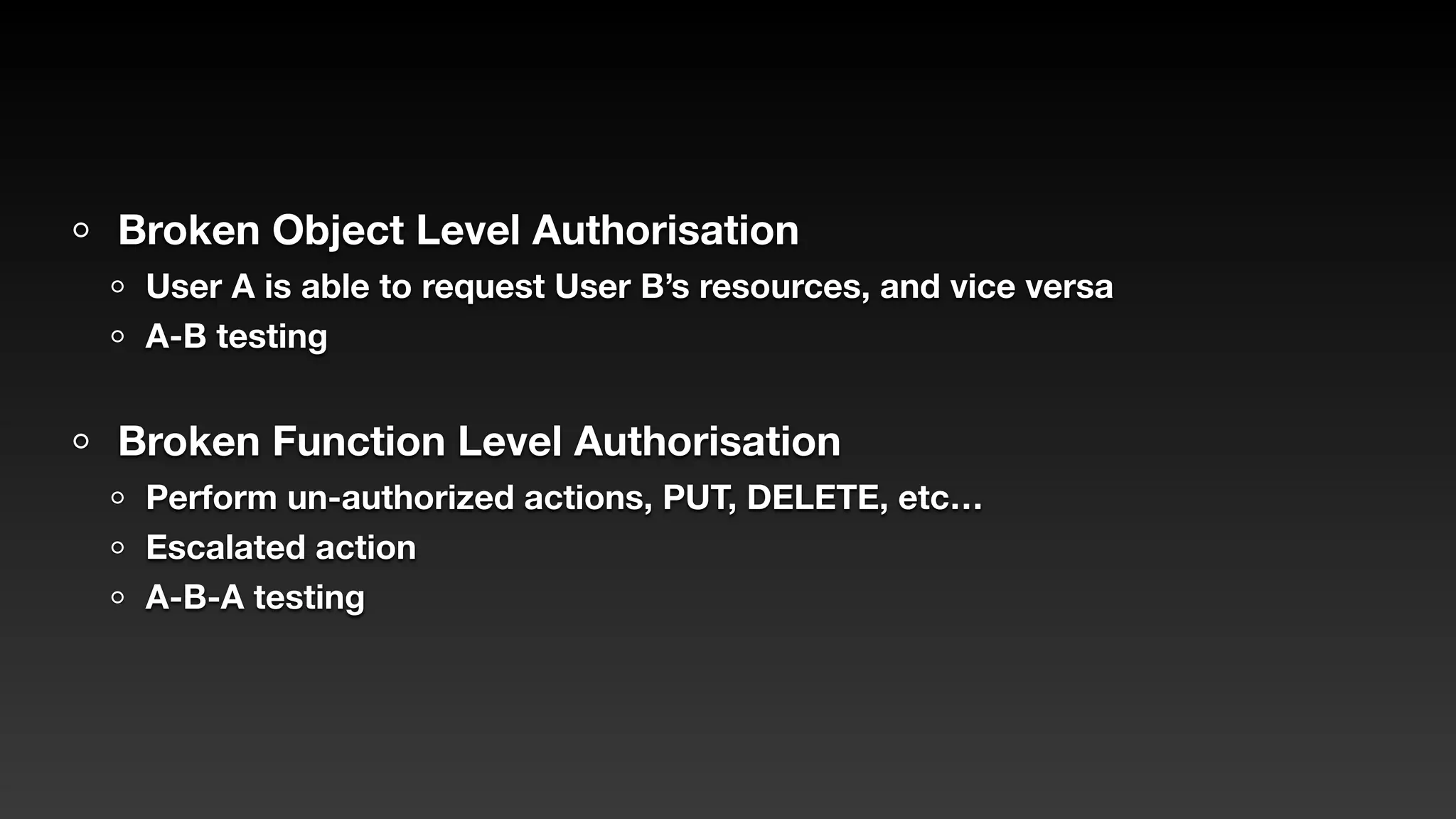
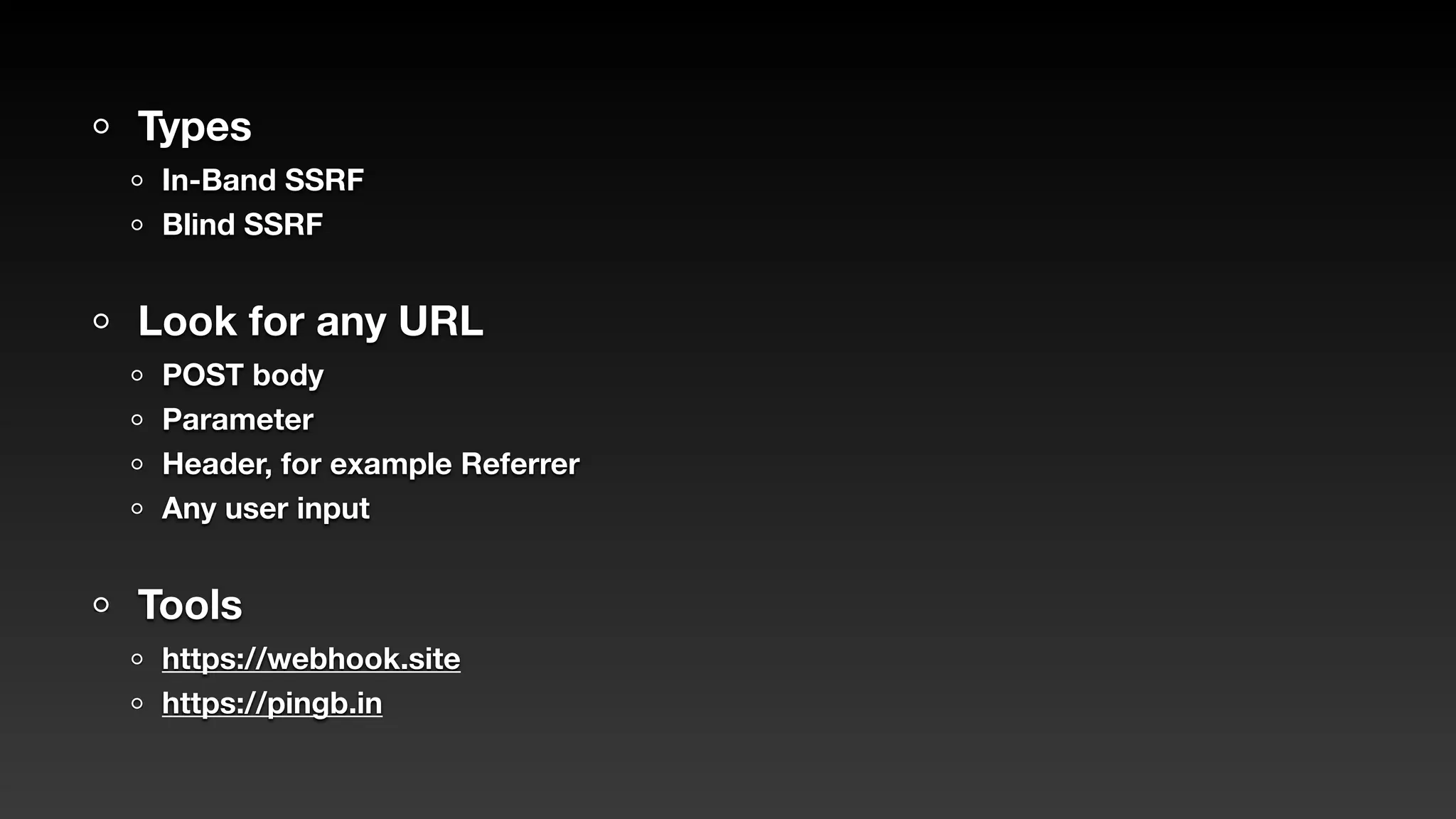
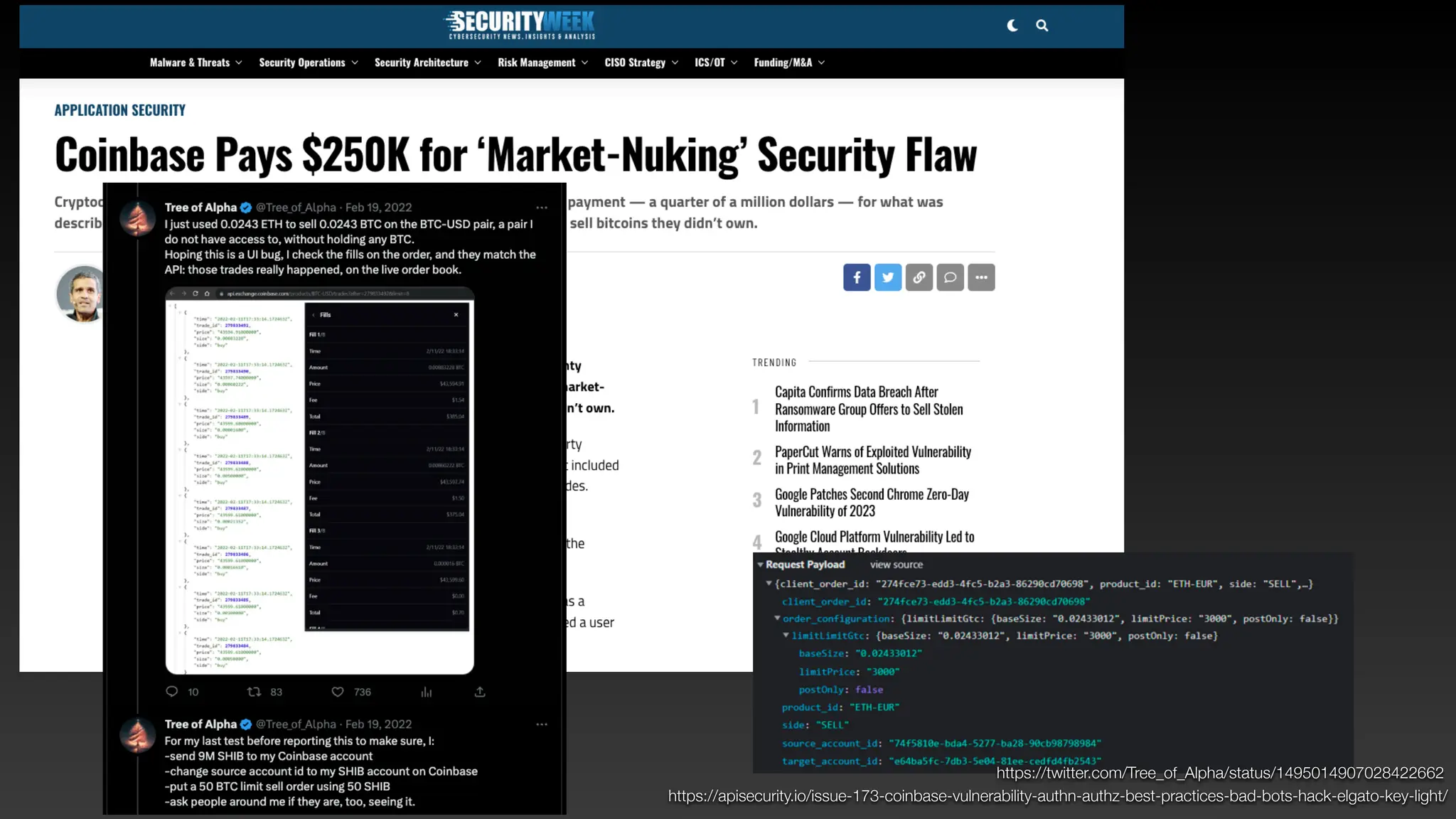
Jie Liau gave a presentation on API security. The presentation covered how APIs have become a primary attack vector, the OWASP API Security Top 10 risks, real world API attacks on companies like Coinbase, T-Mobile, and Instagram, and tools for testing API security like Postman and Burpsuite. It also provided details on API security issues like broken authentication, authorization, inventory management, and server side request forgery. The goal was to educate attendees on the growing API attack surface and best practices for securing APIs.
![curl -X GET https://127.0.0.1/info
https://www.linkedin.com/in/jieliau
https://github.com/jieliau
https://www.facebook.com/jie.liau
https://twitter.com/0xJieLiau
https://jieliau.medium.com/
{
"Name": "Jie Liau",
"Experiences": [
“How You API Be My API. - Session speaker in iThome CYBERSEC 2023”,
"Building Your Container Botnet in 1 Minute. - Session speaker in iThome CYBERSEC 2021",
"Container Security. - Session speaker in InfoSec 2020",
"Protecting Your Internet Route Integrity. - Session speaker in iThome CYBERSEC 2020",
"The Dark Side. - Seminar speaker in CSE, Yuan Ze University 2018",
"The Tor Network. - Session speaker in TDOH Conference 2017",
"What Does Network Operation Looks Like. - Seminar speaker in CSE, Yuan Ze University 2016"
],
"Certi
fi
cations": [
"CCIE",
"OSCP",
"CEH"
]
}](https://image.slidesharecdn.com/owaspapitalk-231128142428-8bfb9718/75/OWASPAPISecurity-2-2048.jpg)