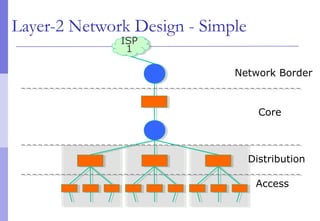
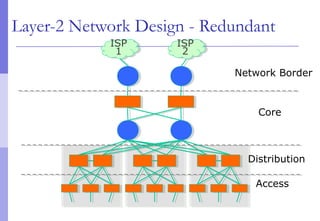
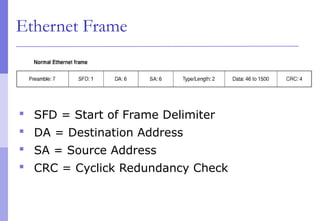
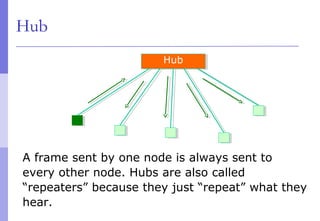
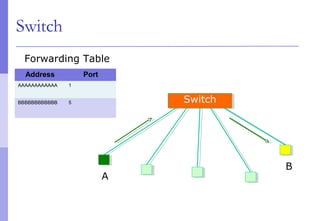
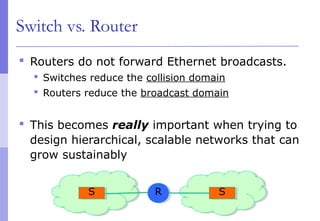
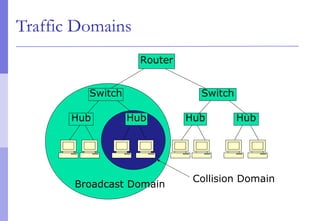
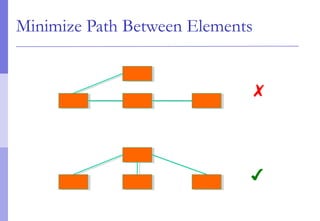
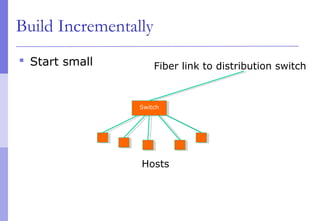
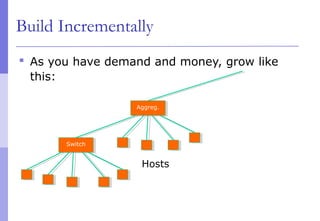
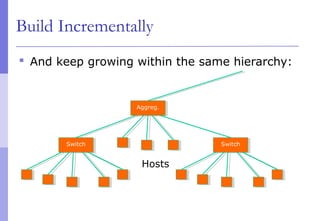
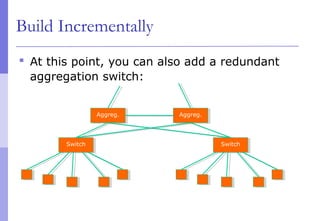
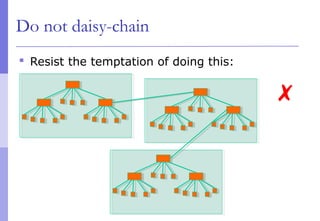
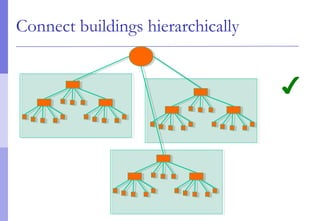
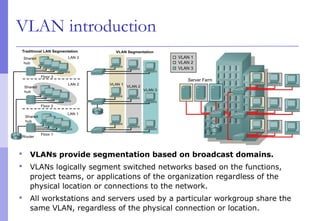
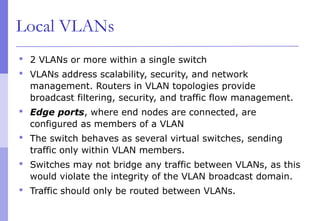
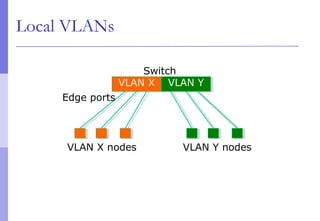
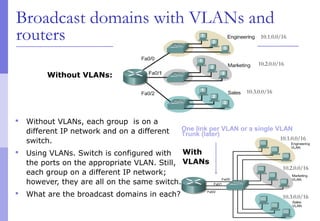
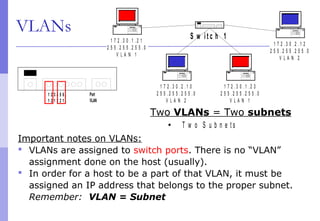
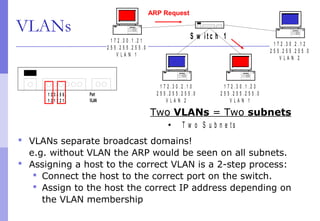
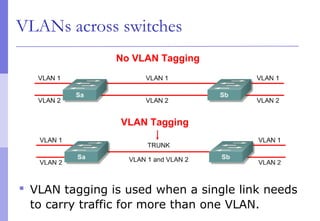
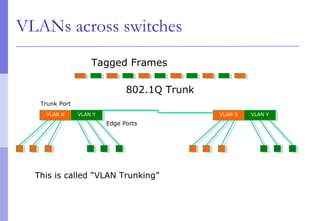
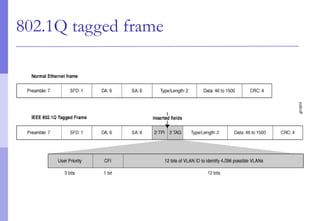
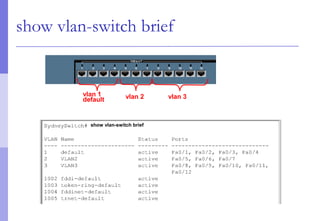
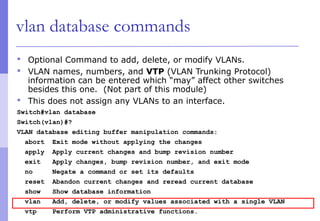
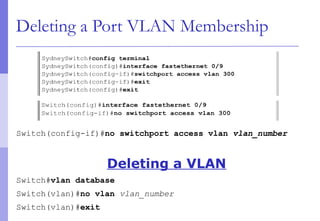
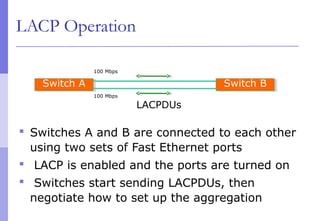
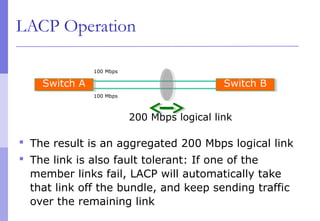
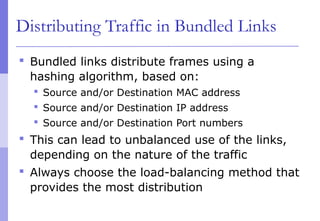
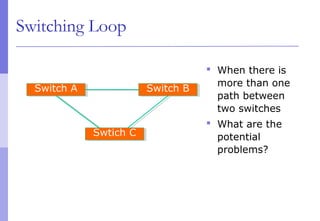
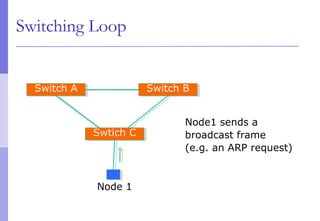
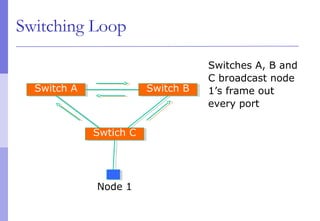
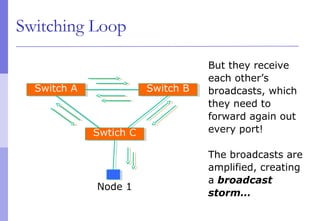
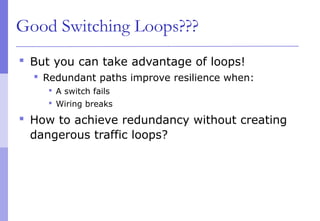
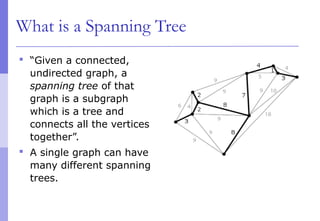
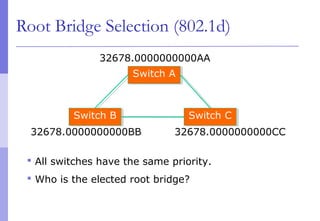
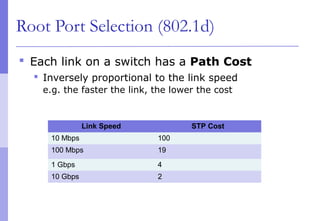
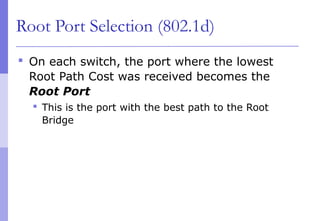
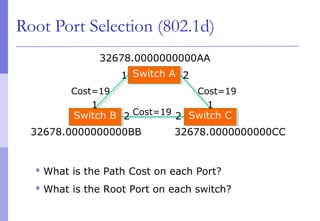
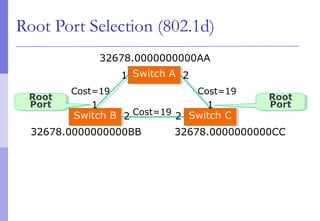
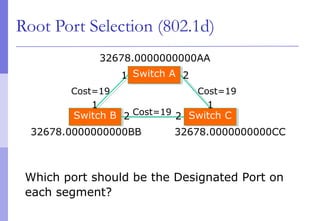
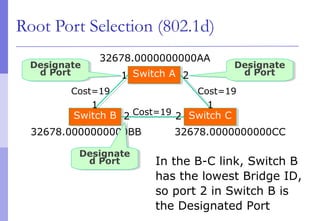
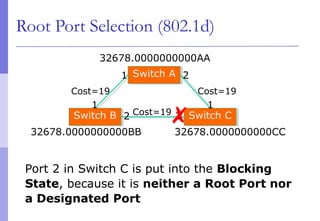
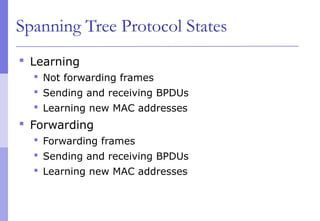
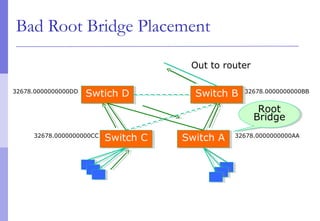
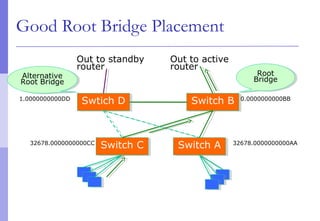
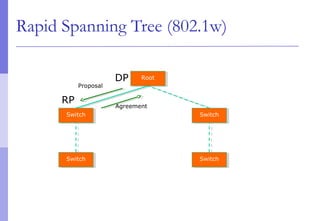
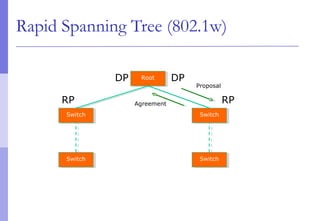
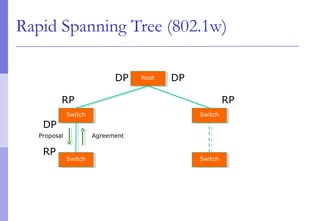
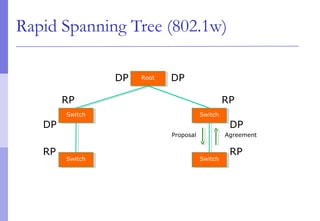
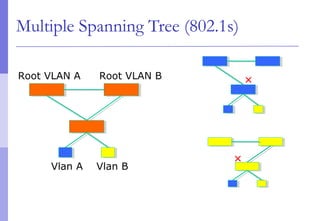
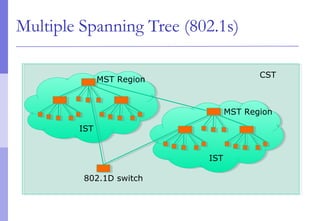
The document discusses layer 2 network design concepts. It describes a hierarchical network design with core, distribution, and access layers. It covers layer 2 protocols like Ethernet and switches, and how switches reduce collision domains compared to hubs. The document also covers VLANs, how they segment broadcast domains, and how VLAN traffic can cross switches using 802.1Q trunking. Finally, it discusses link aggregation using LACP for increased bandwidth or redundancy.