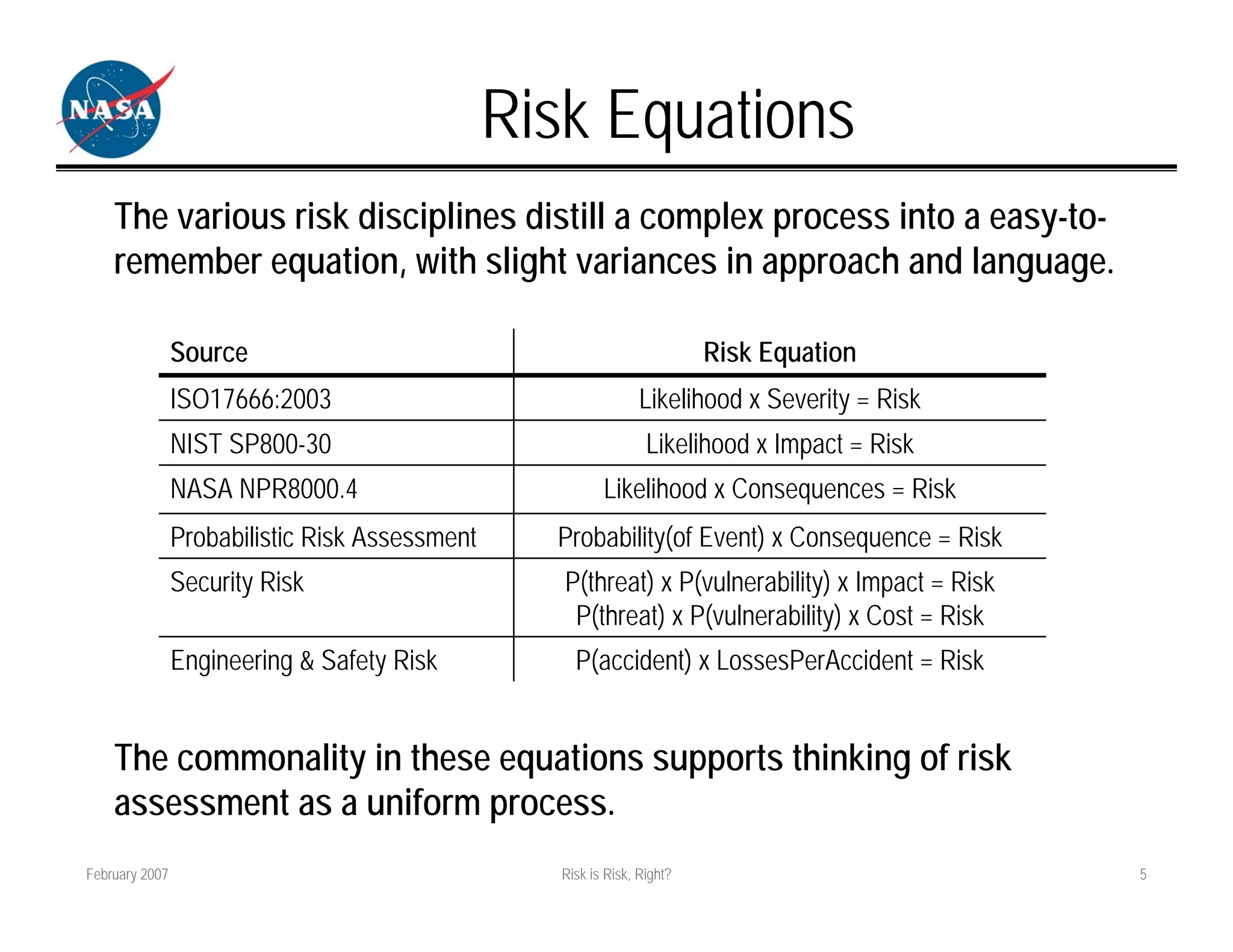
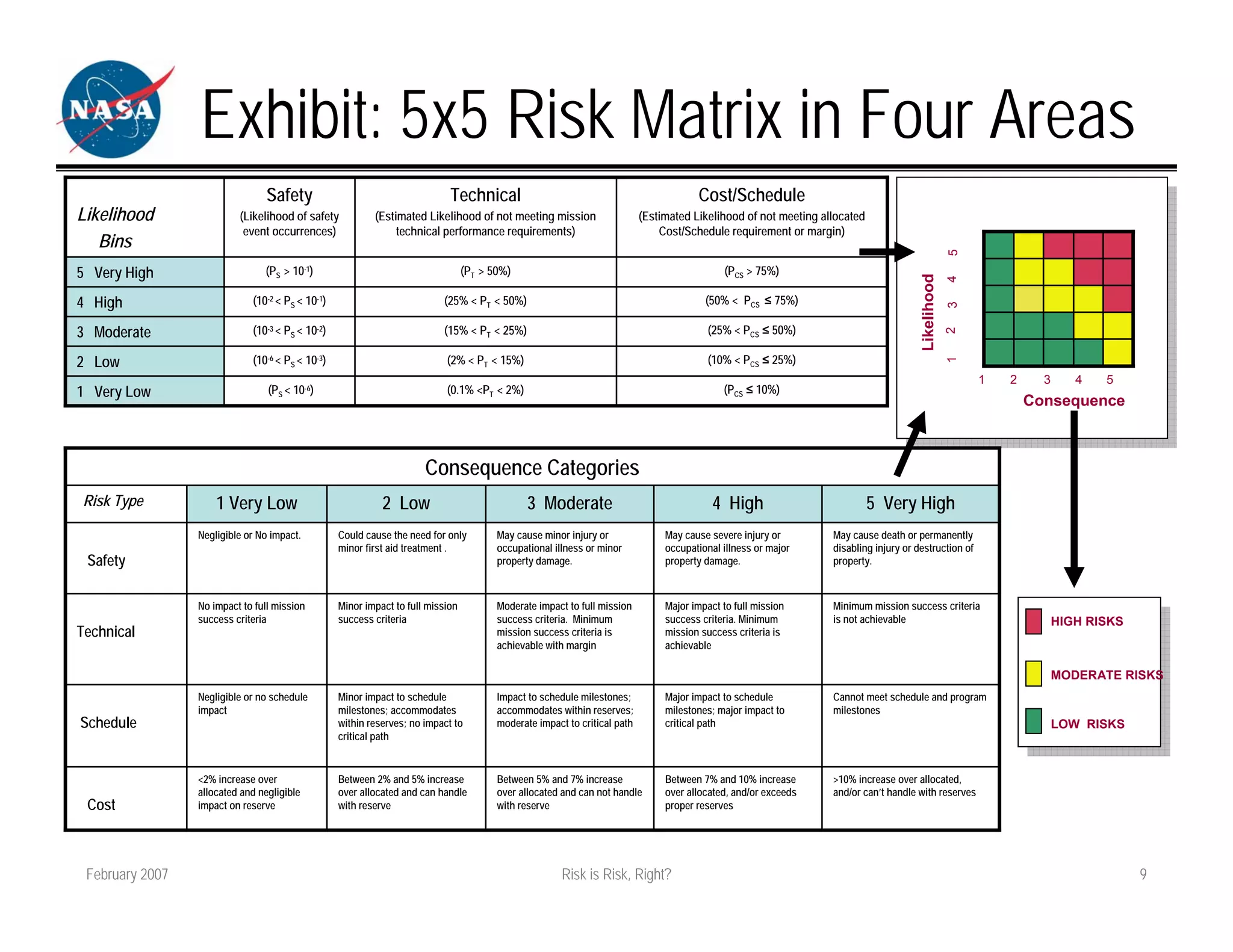
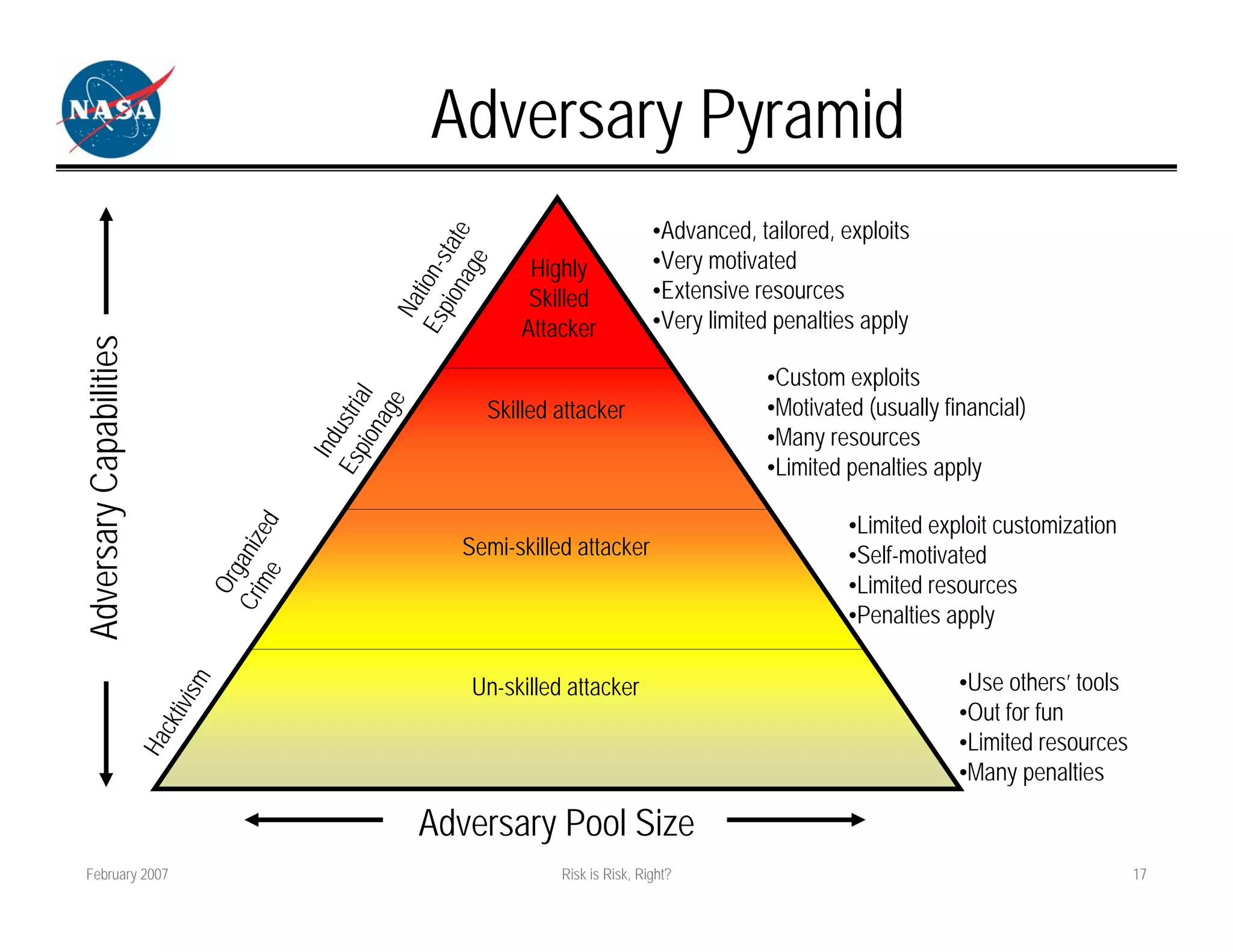
The document discusses how different fields approach risk assessment but use similar frameworks involving likelihood and impact/consequences. It reviews common risk equations and challenges in evaluating likelihood, threats/vulnerabilities, and impact. The document also compares how project management, engineering, and security approach risk management.