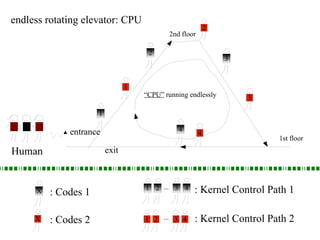
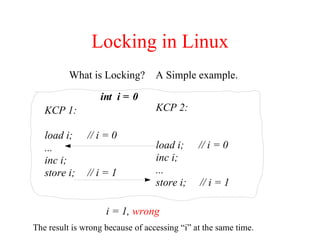
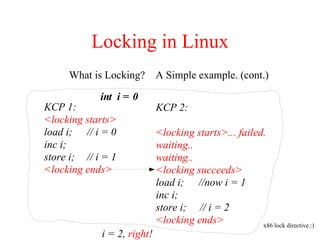
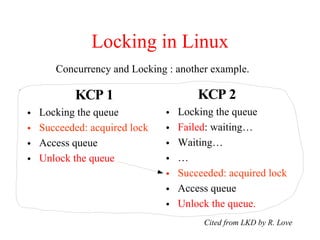
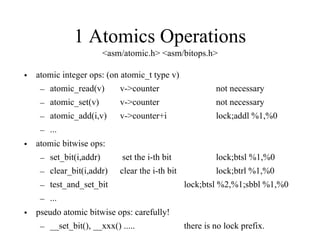
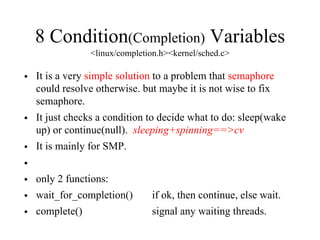
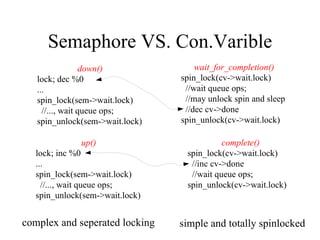
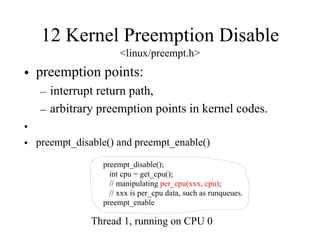
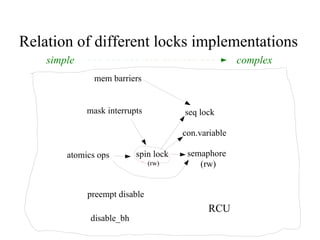
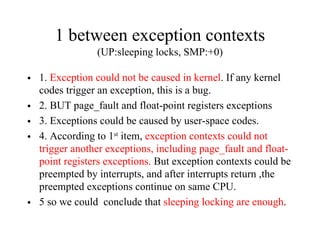
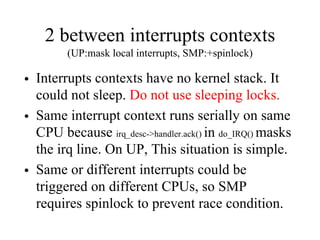
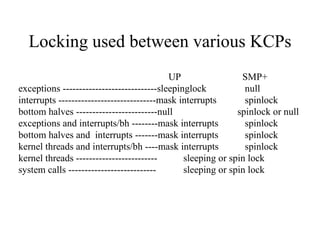
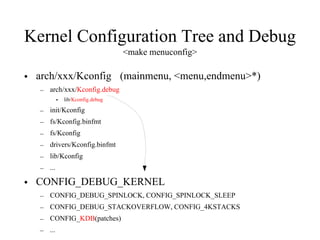
Kernel control paths include interrupts, exceptions, kernel threads, and system calls from user-space threads. Locking is needed between kernel control paths to prevent race conditions on shared data. The type of locking used depends on whether the kernel is single-processor or multi-processor, and whether the code can sleep or not. Spinlocks are generally used for synchronization between interrupt and bottom half contexts, while semaphores can be used for contexts that may sleep.