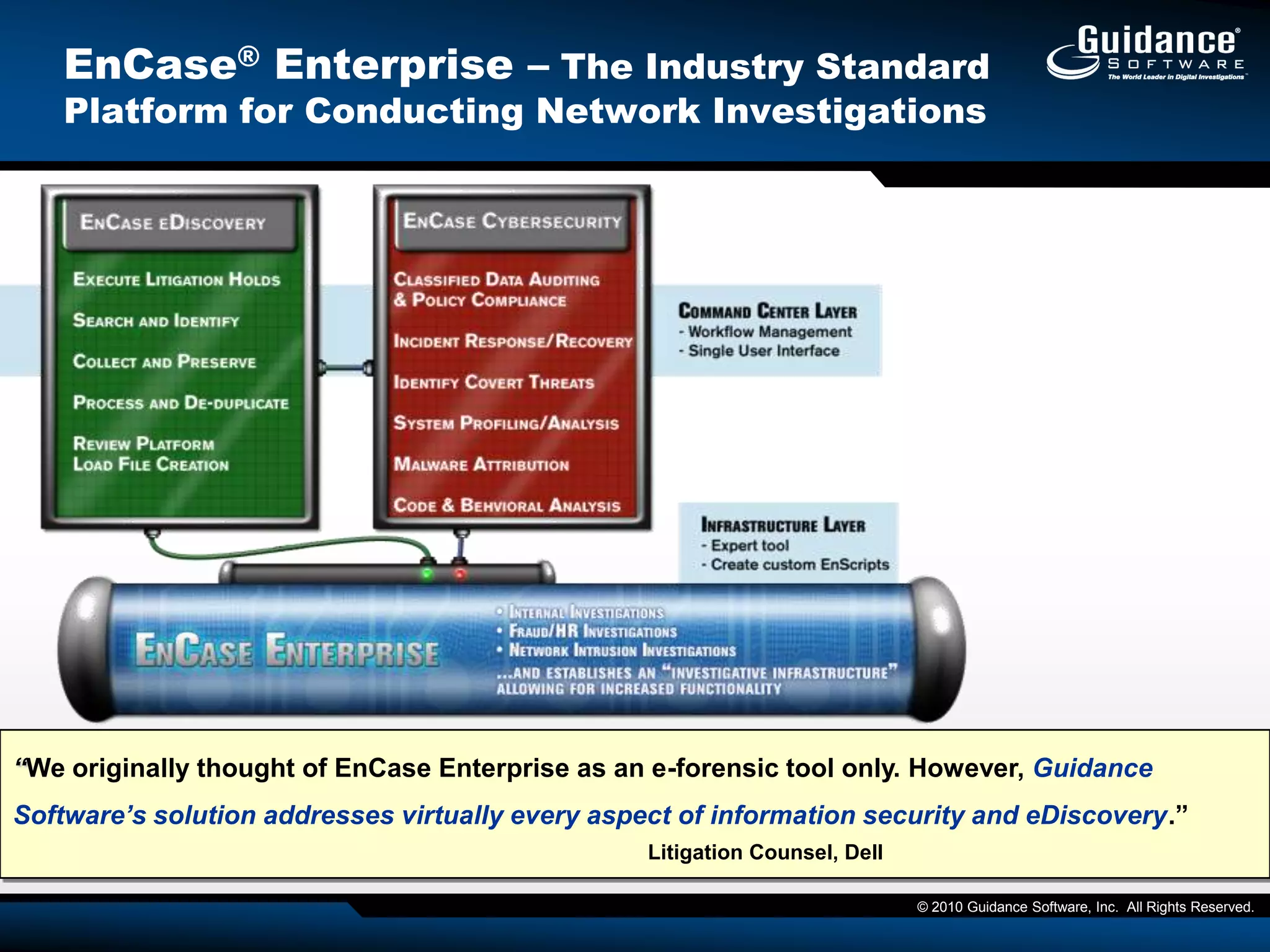
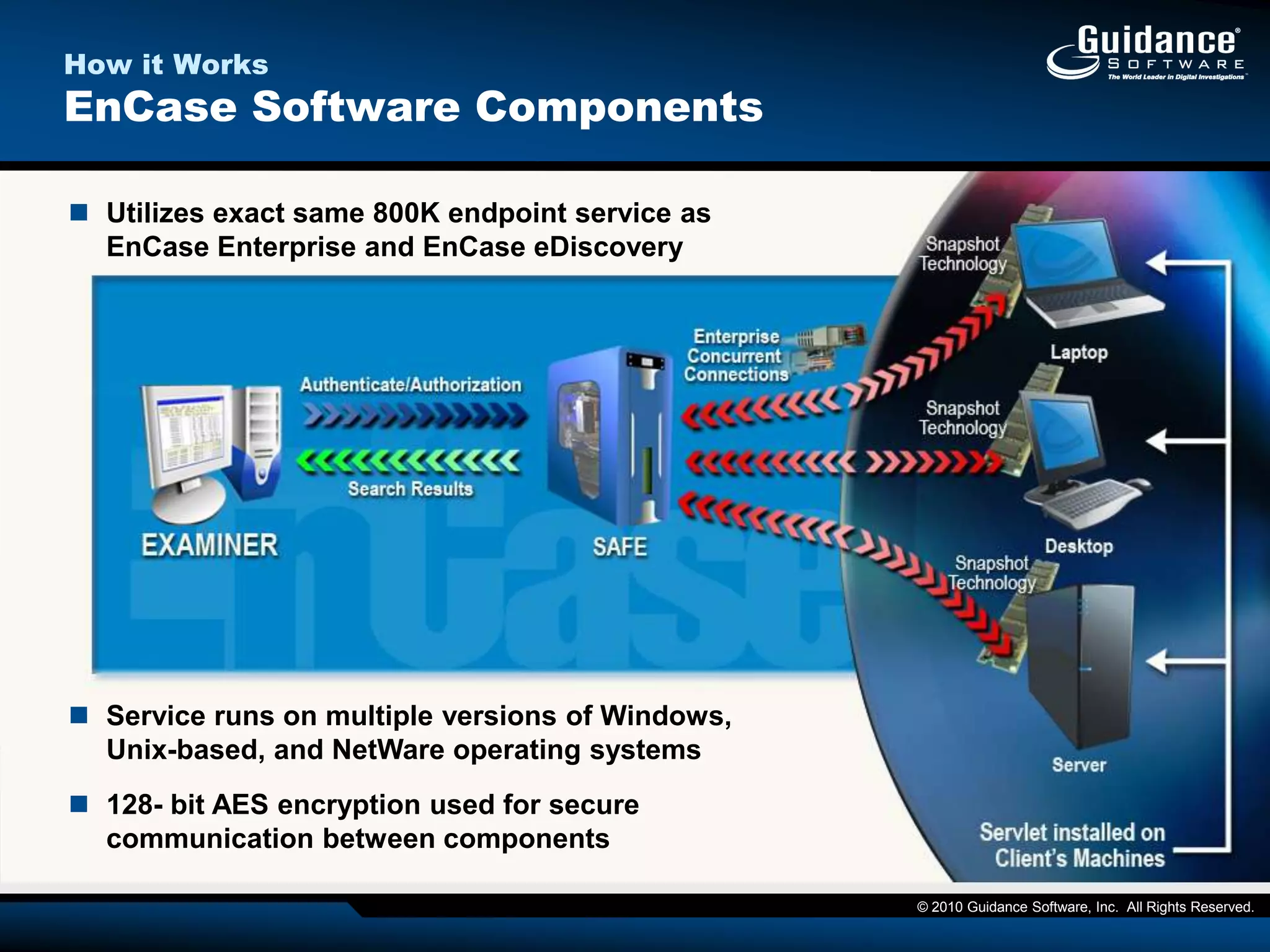
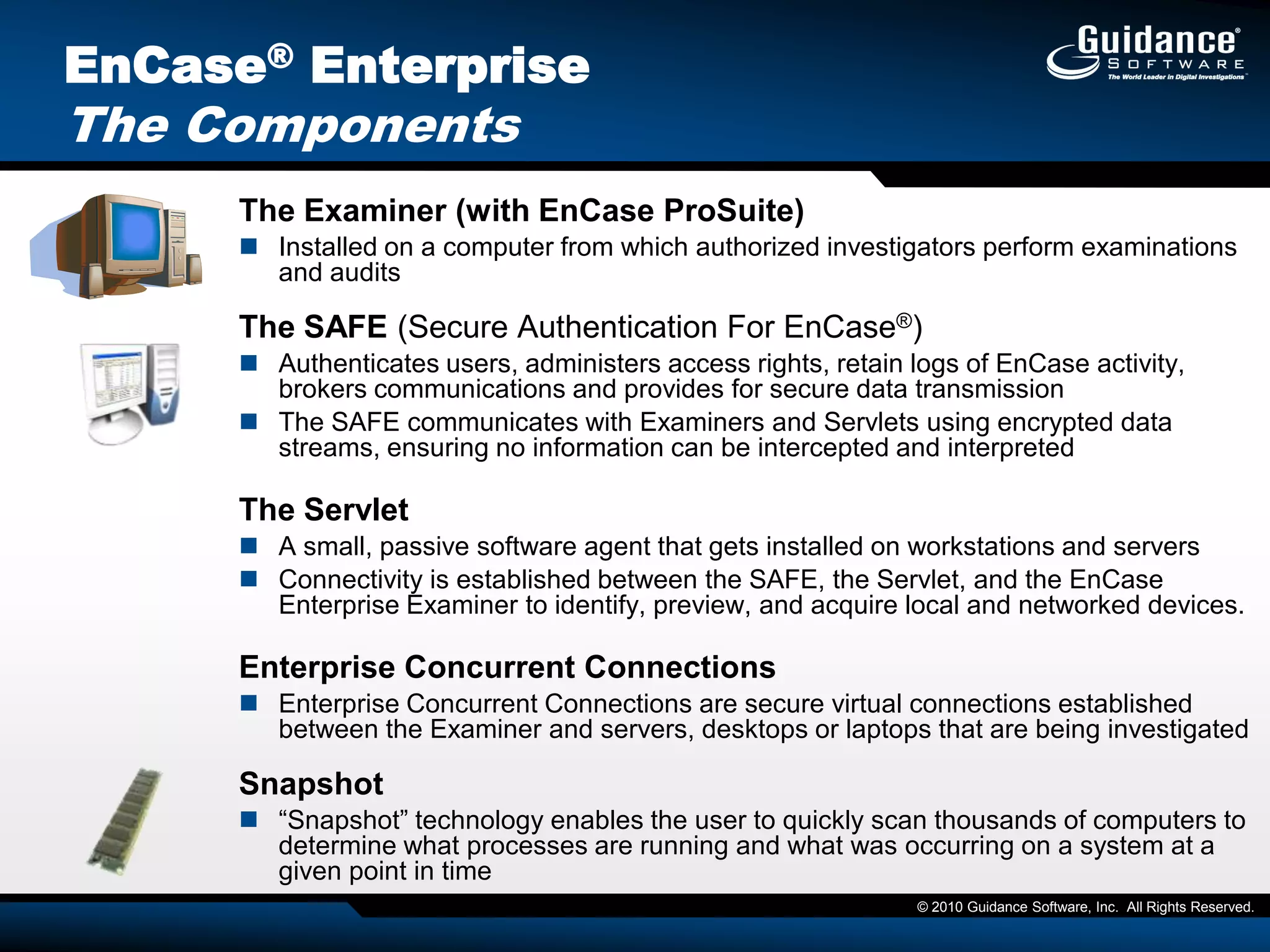
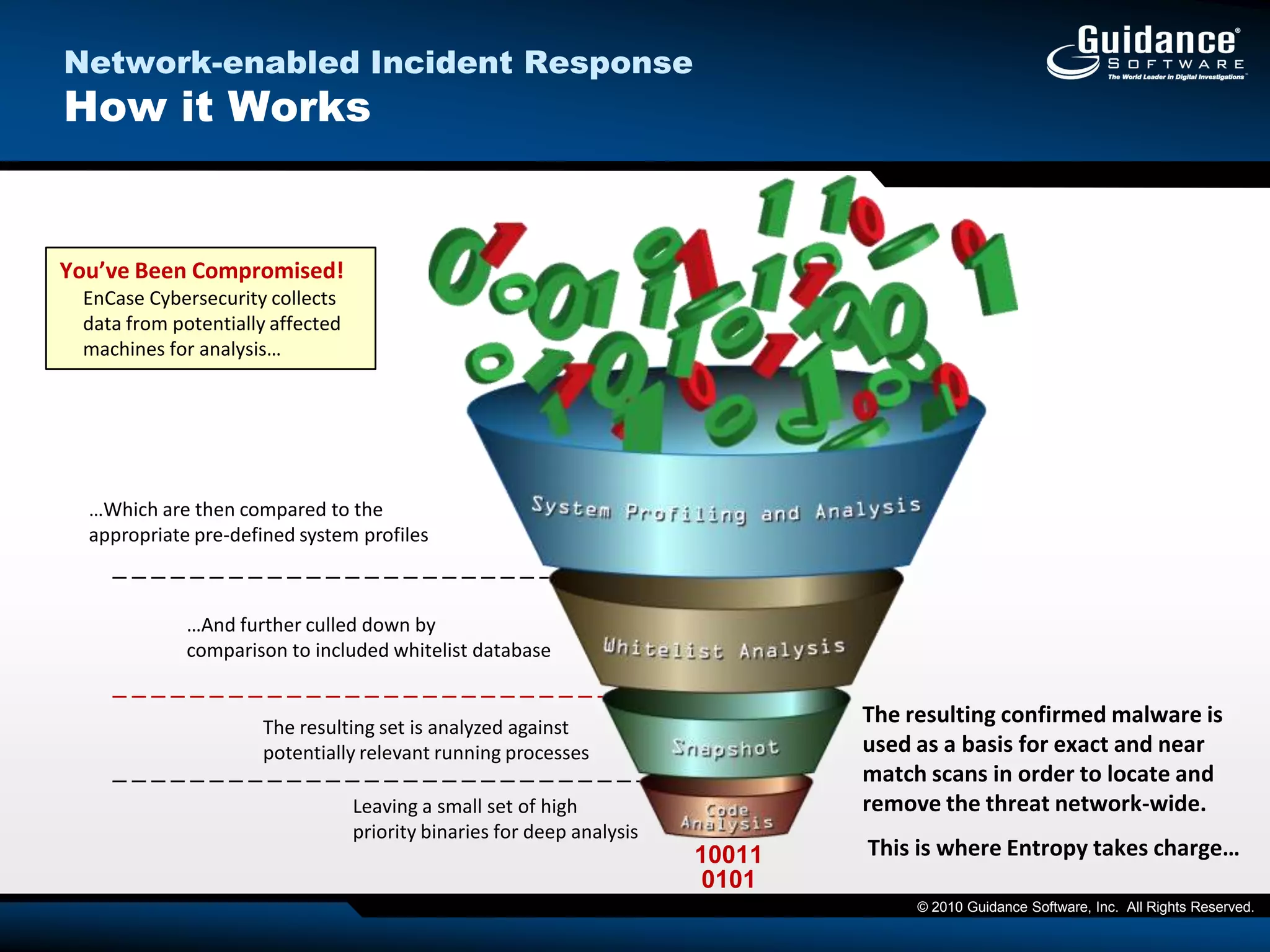
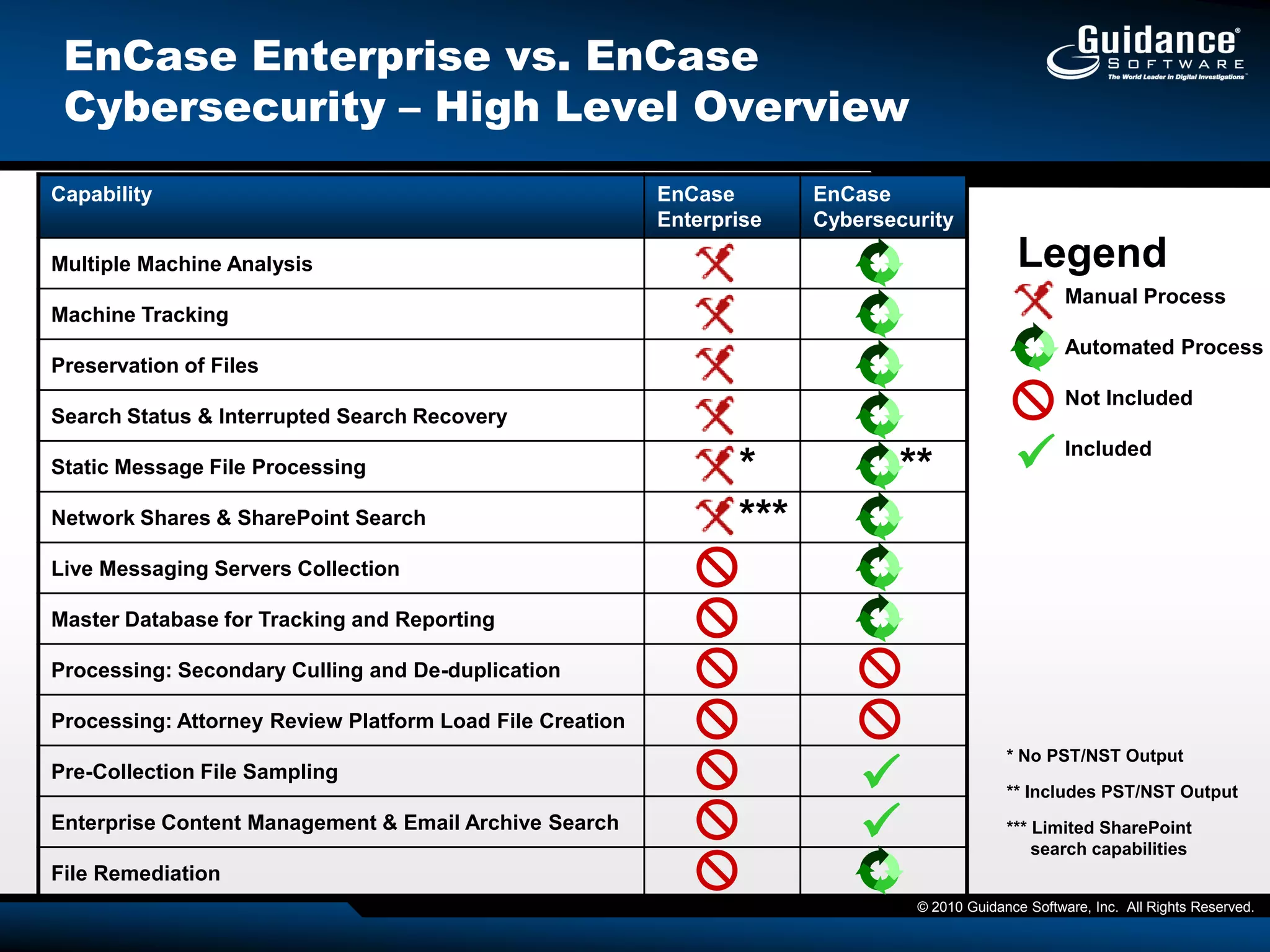
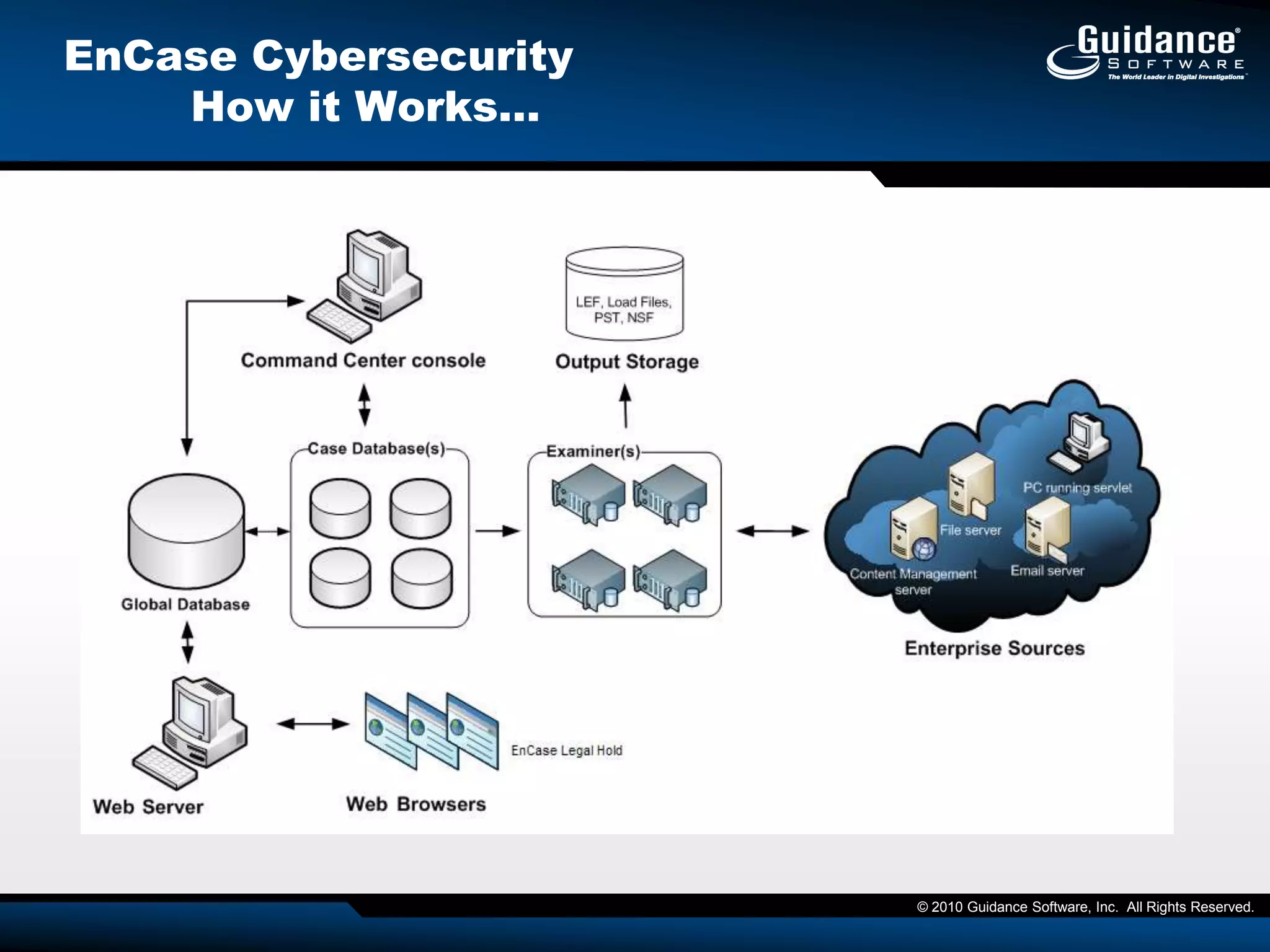
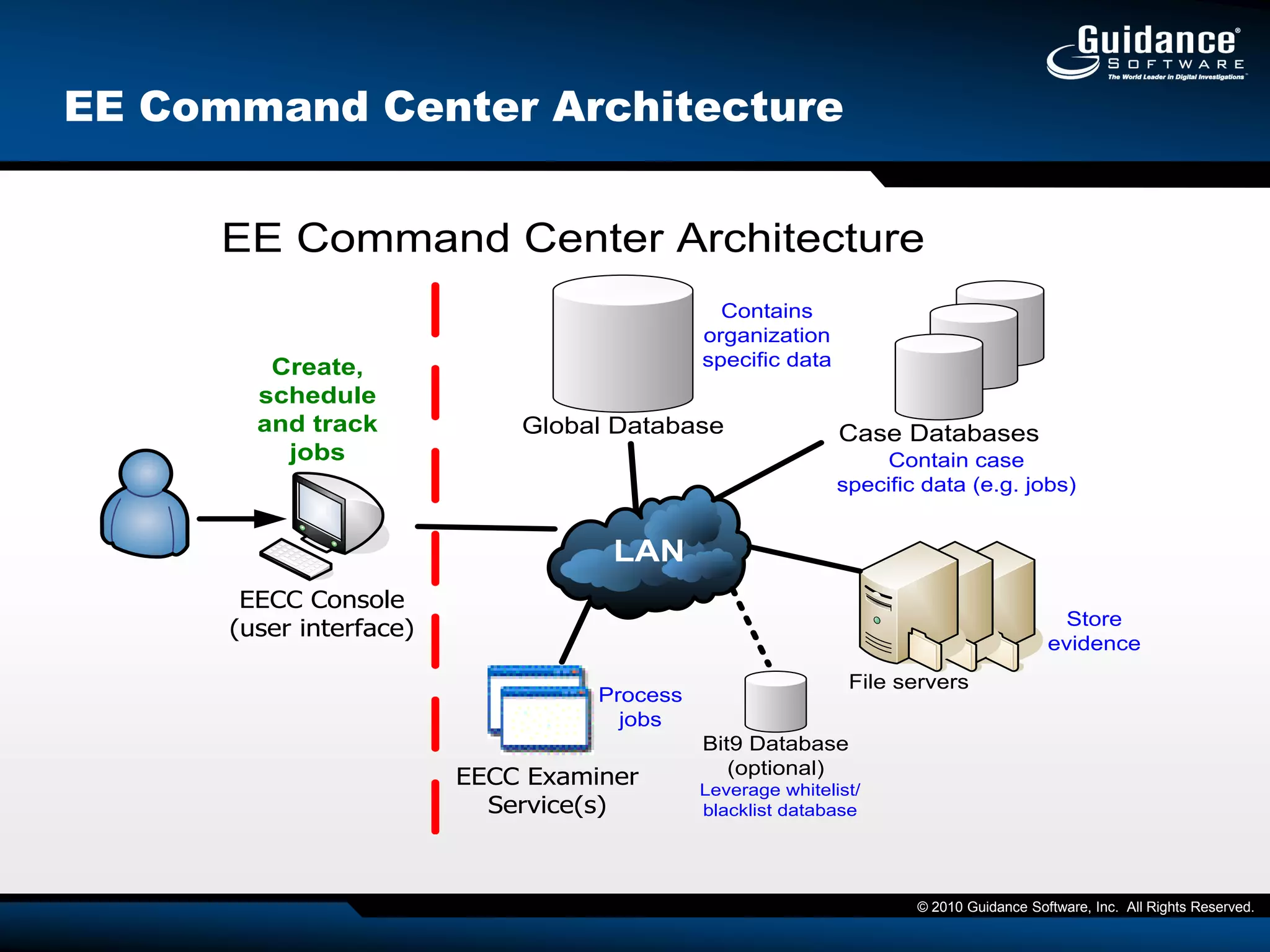
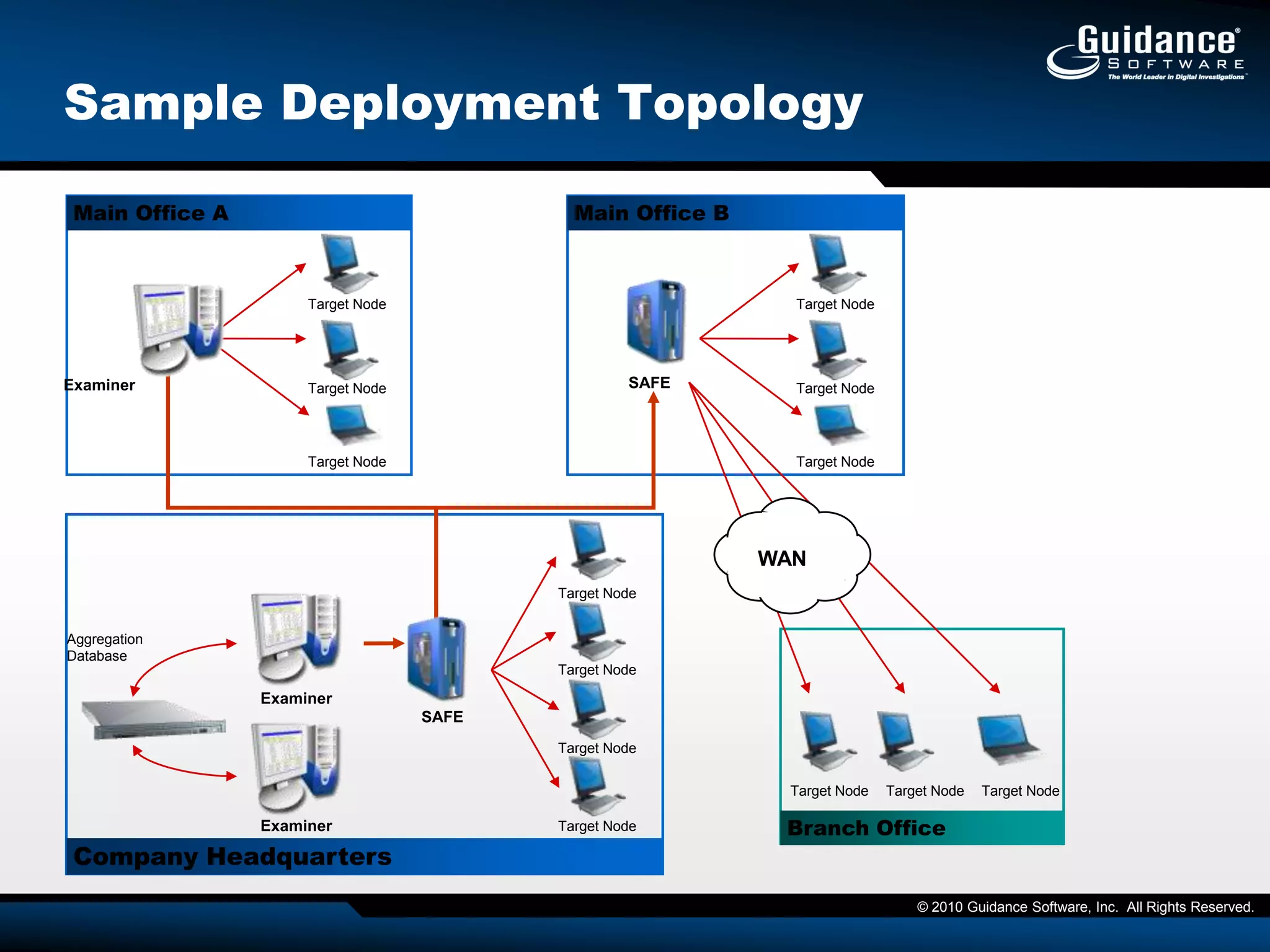
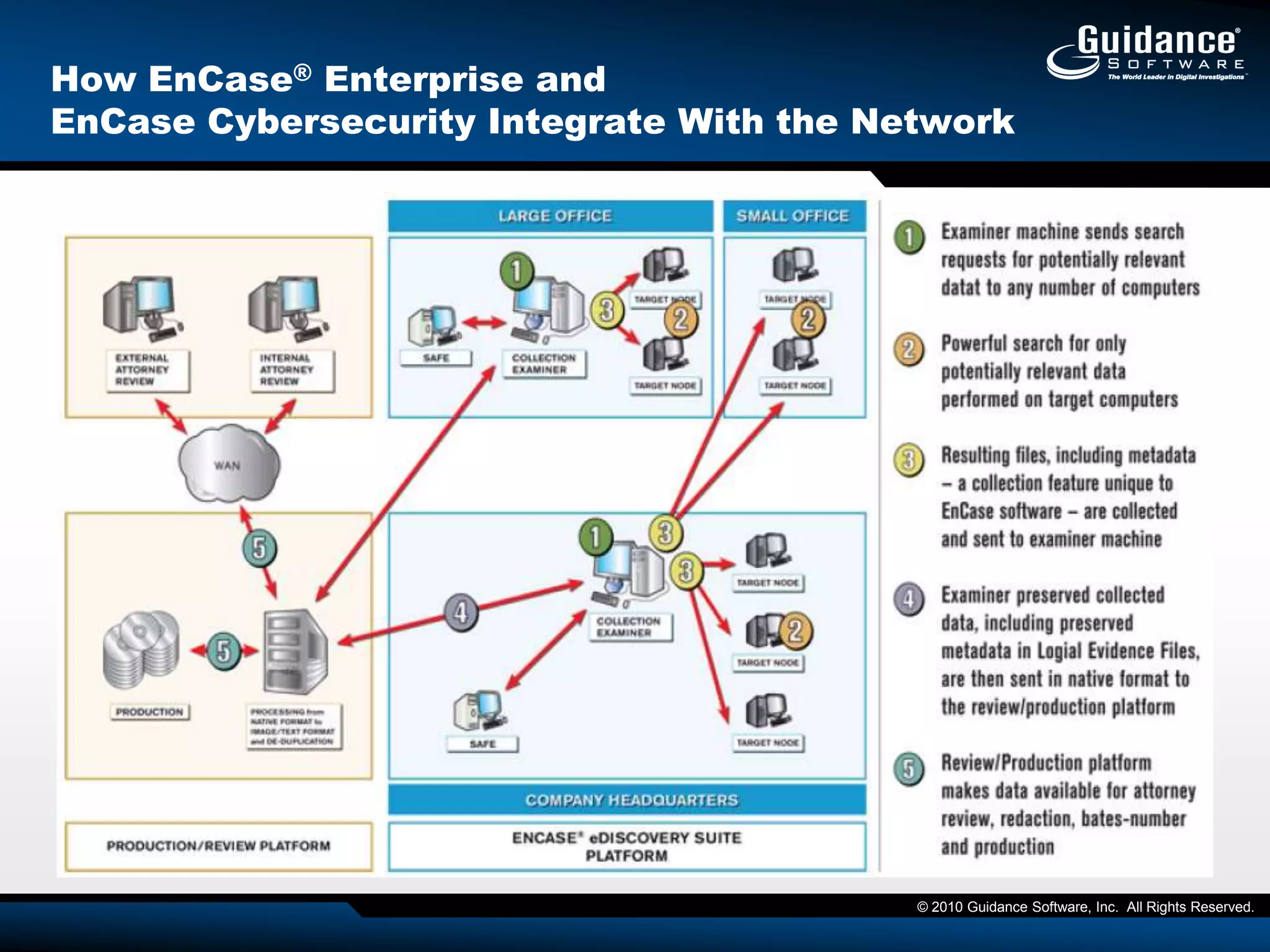
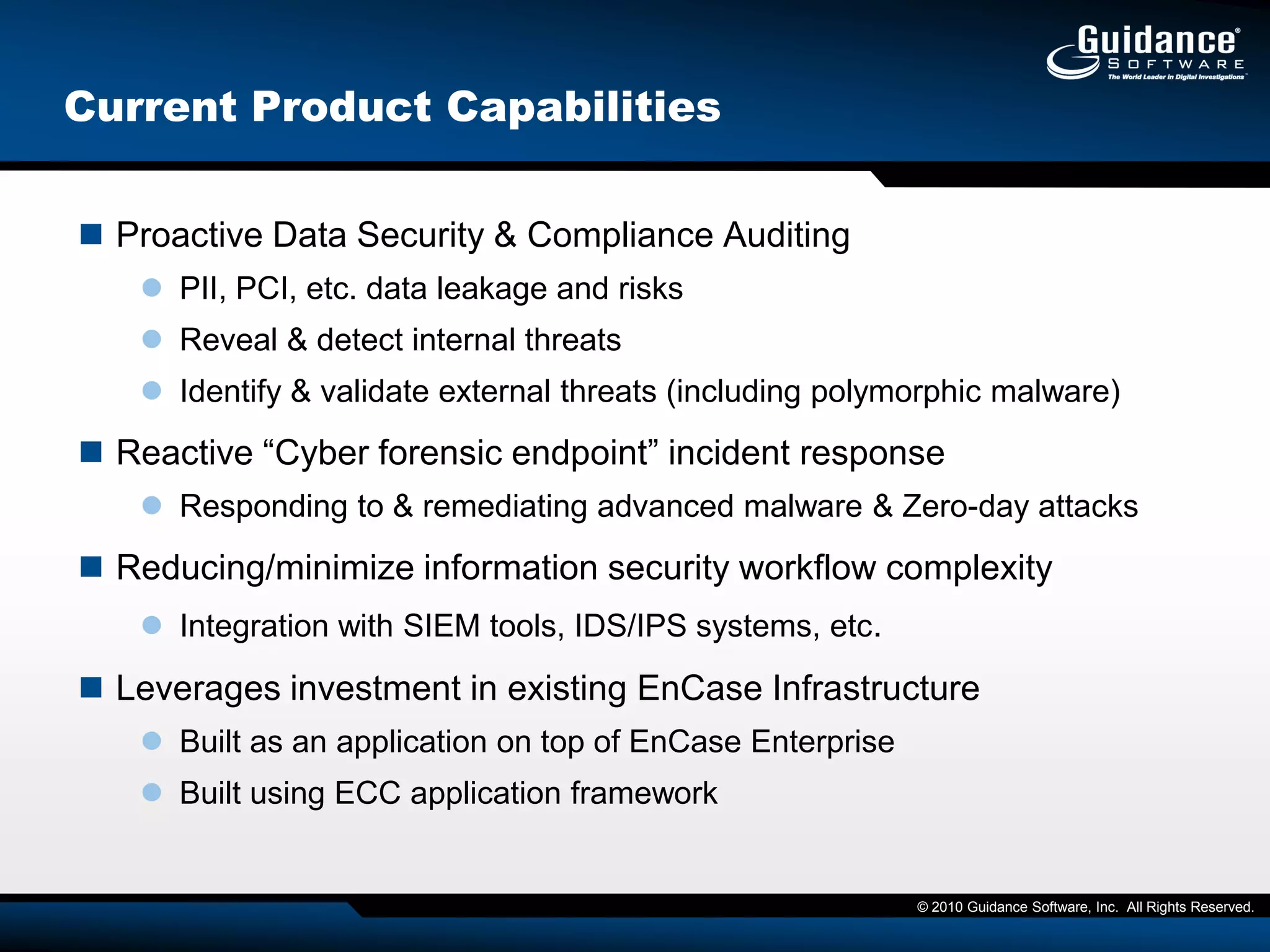
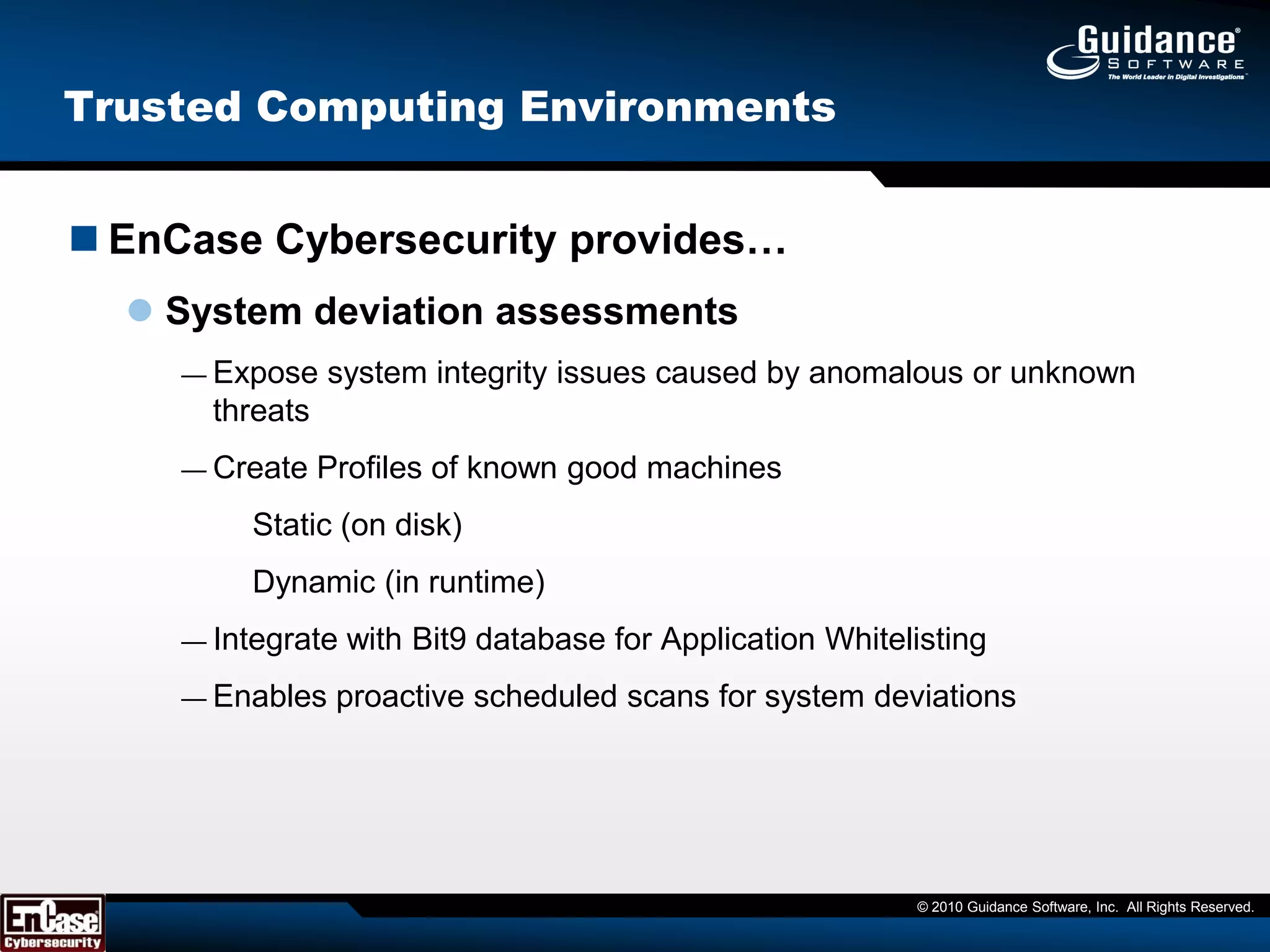
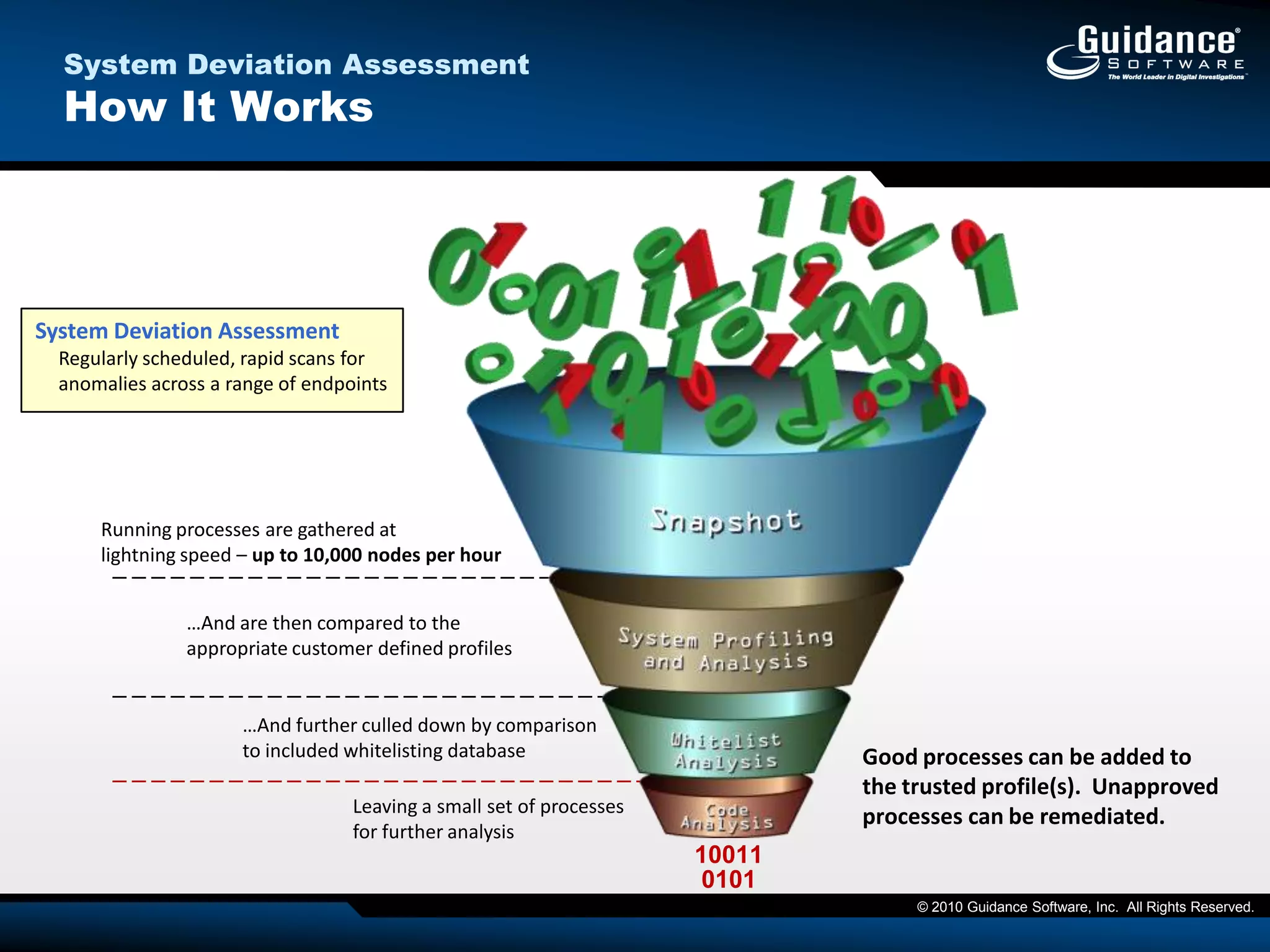
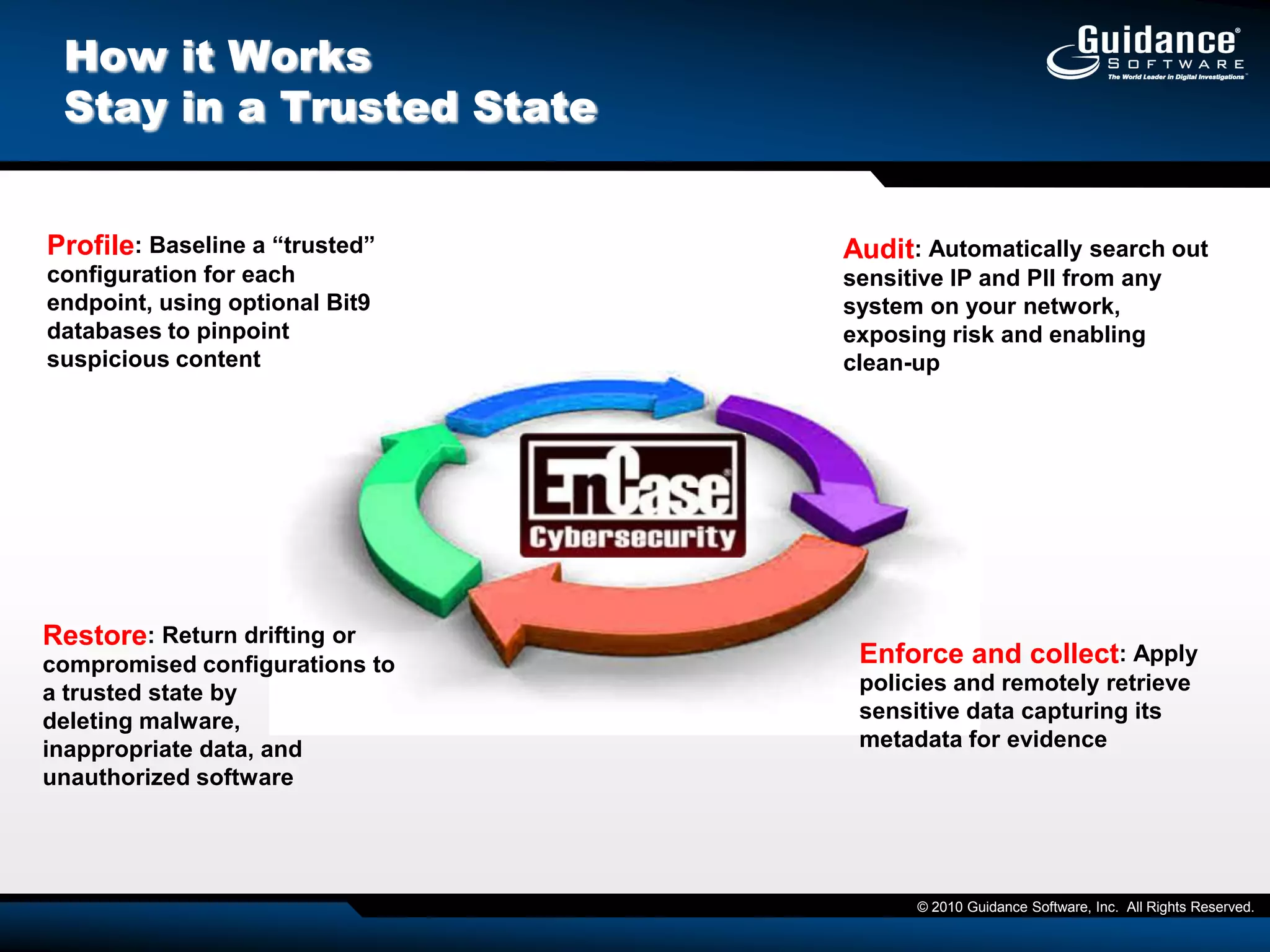
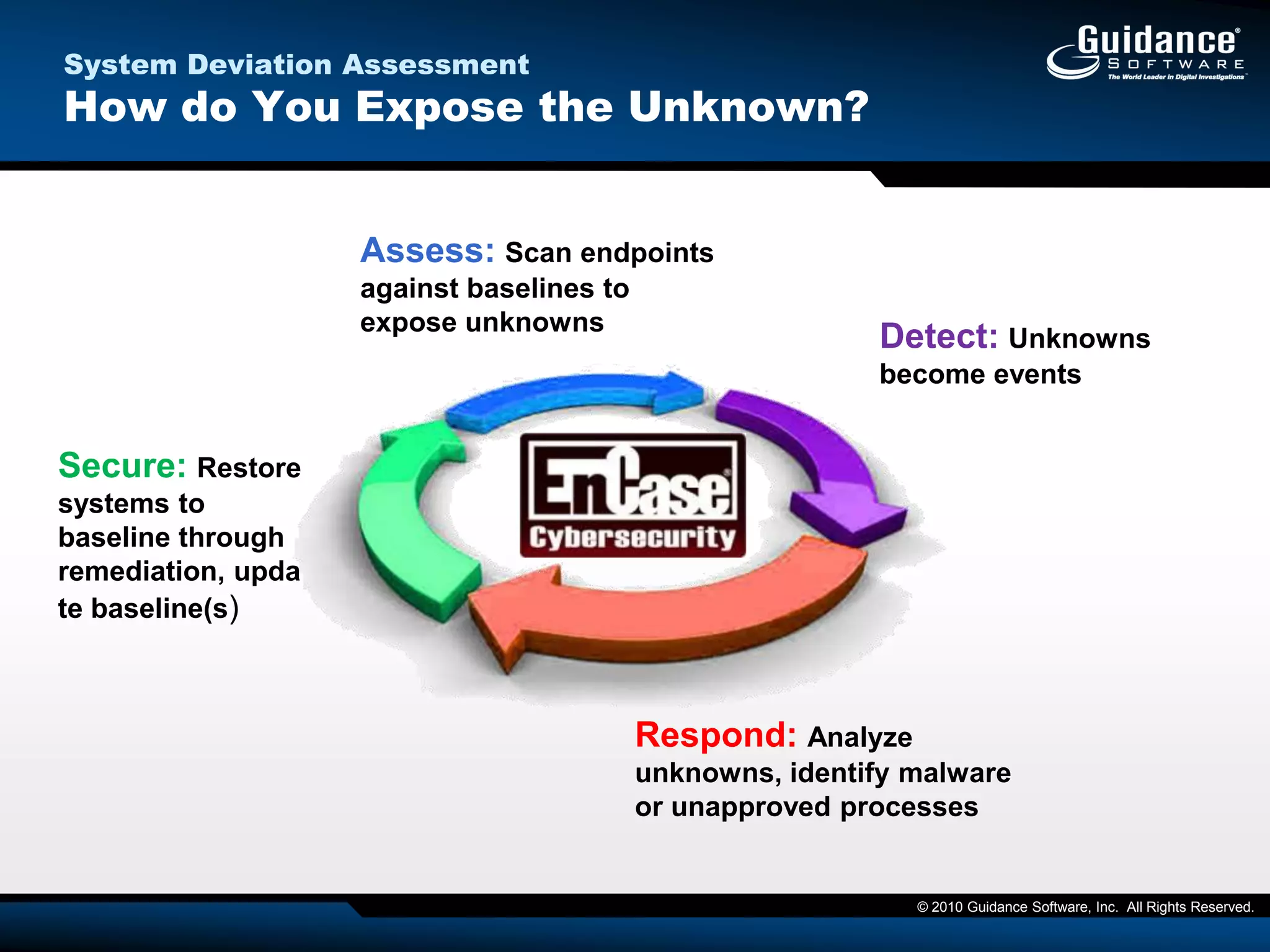
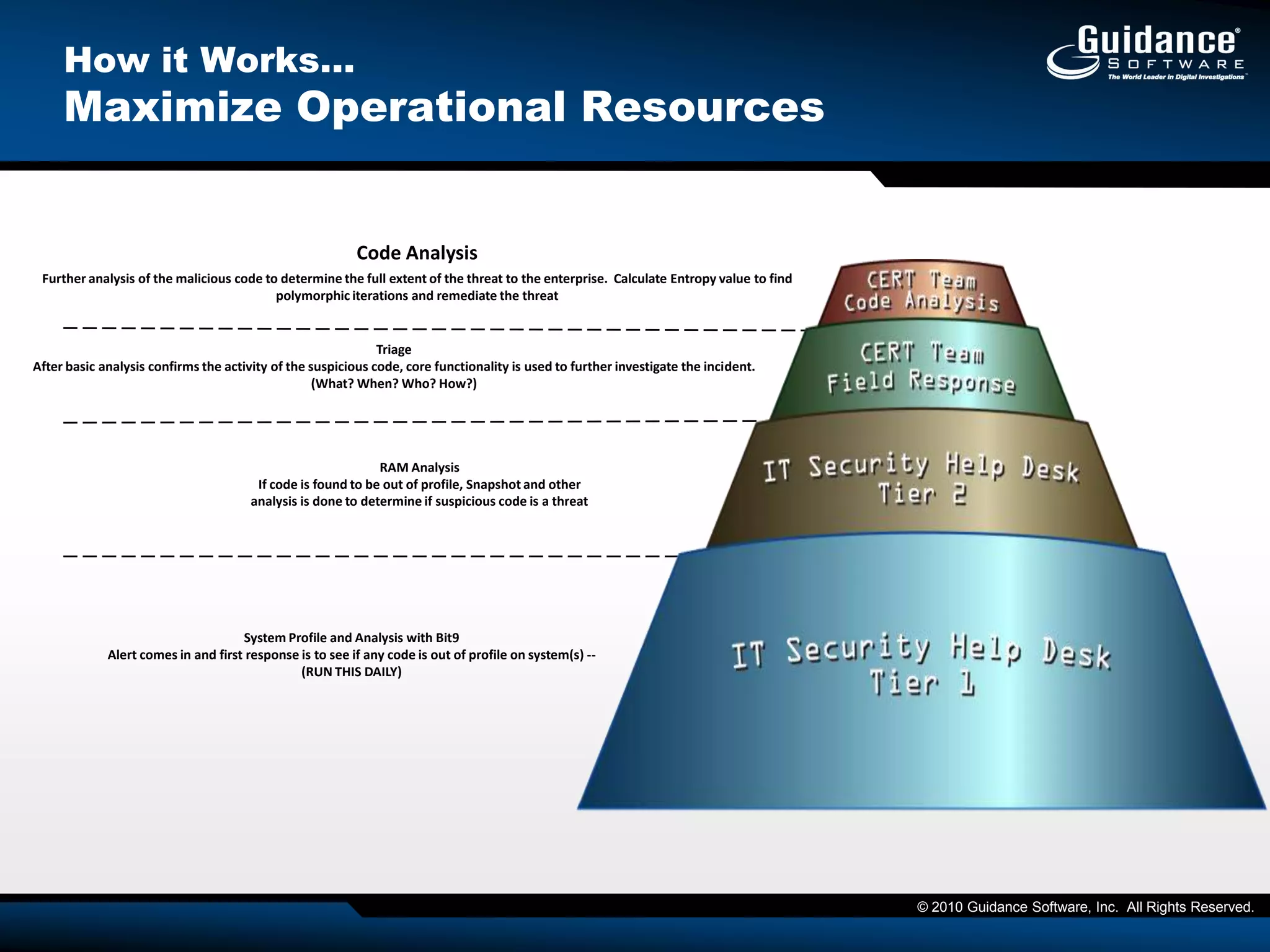
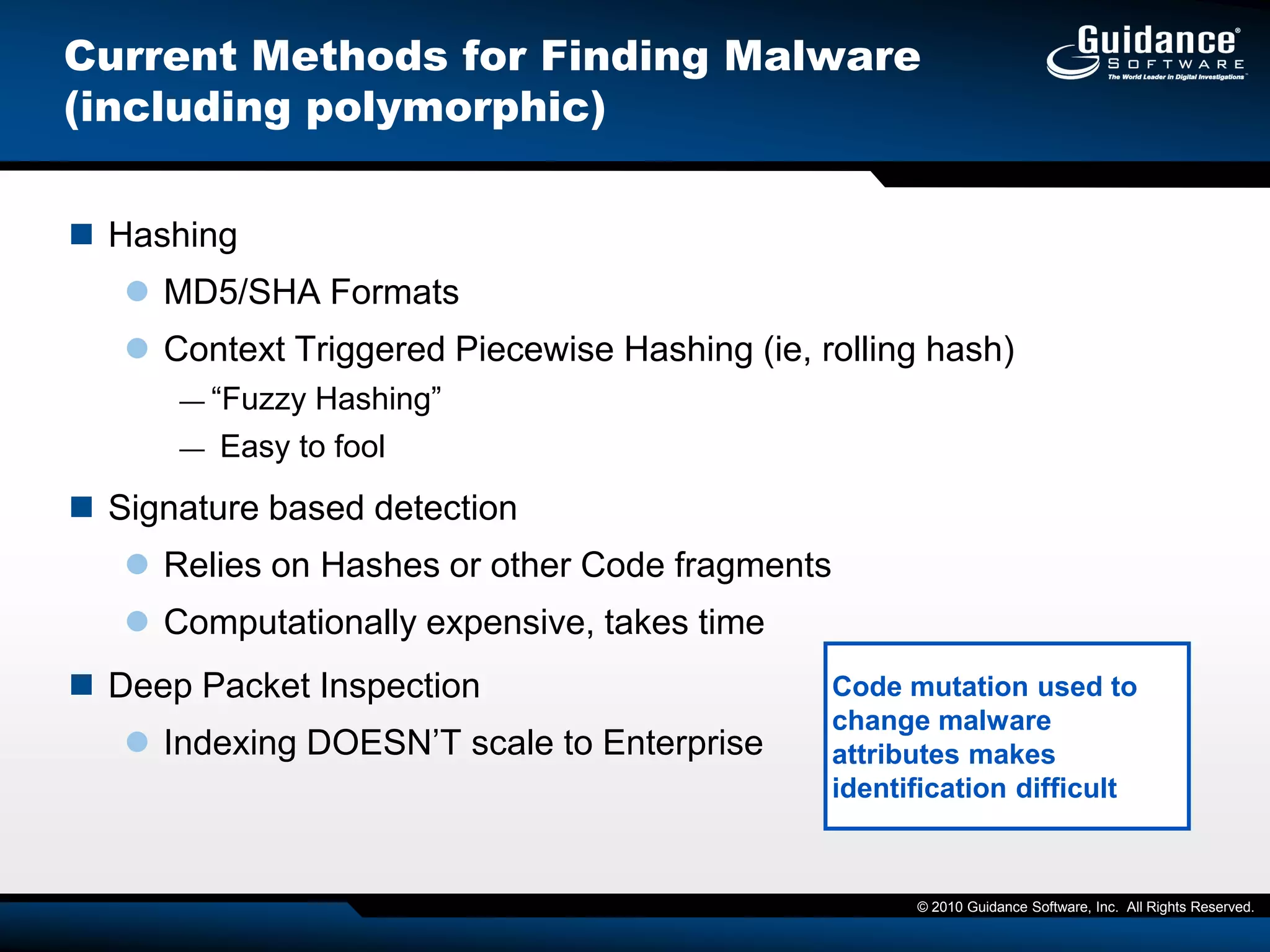
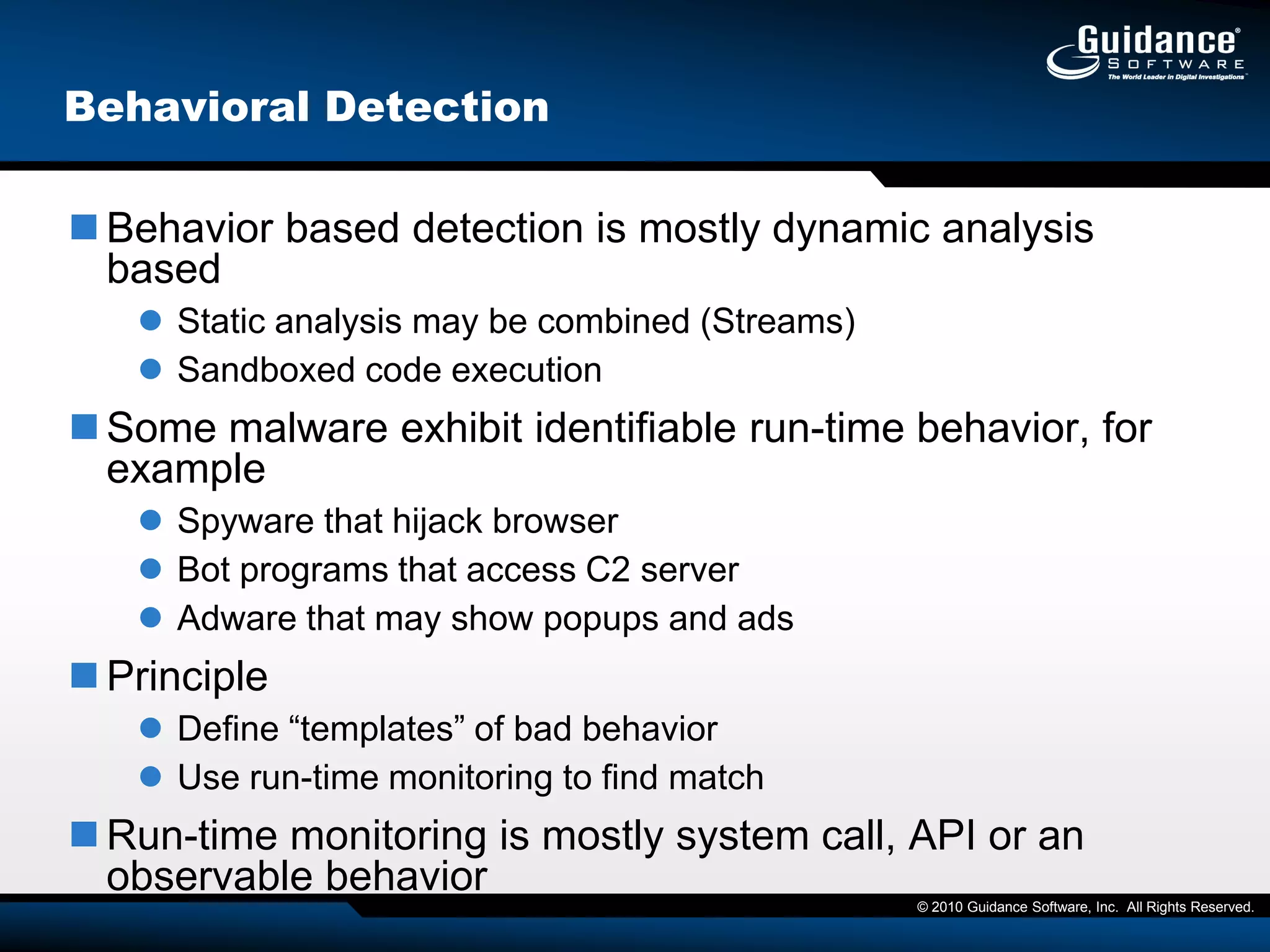
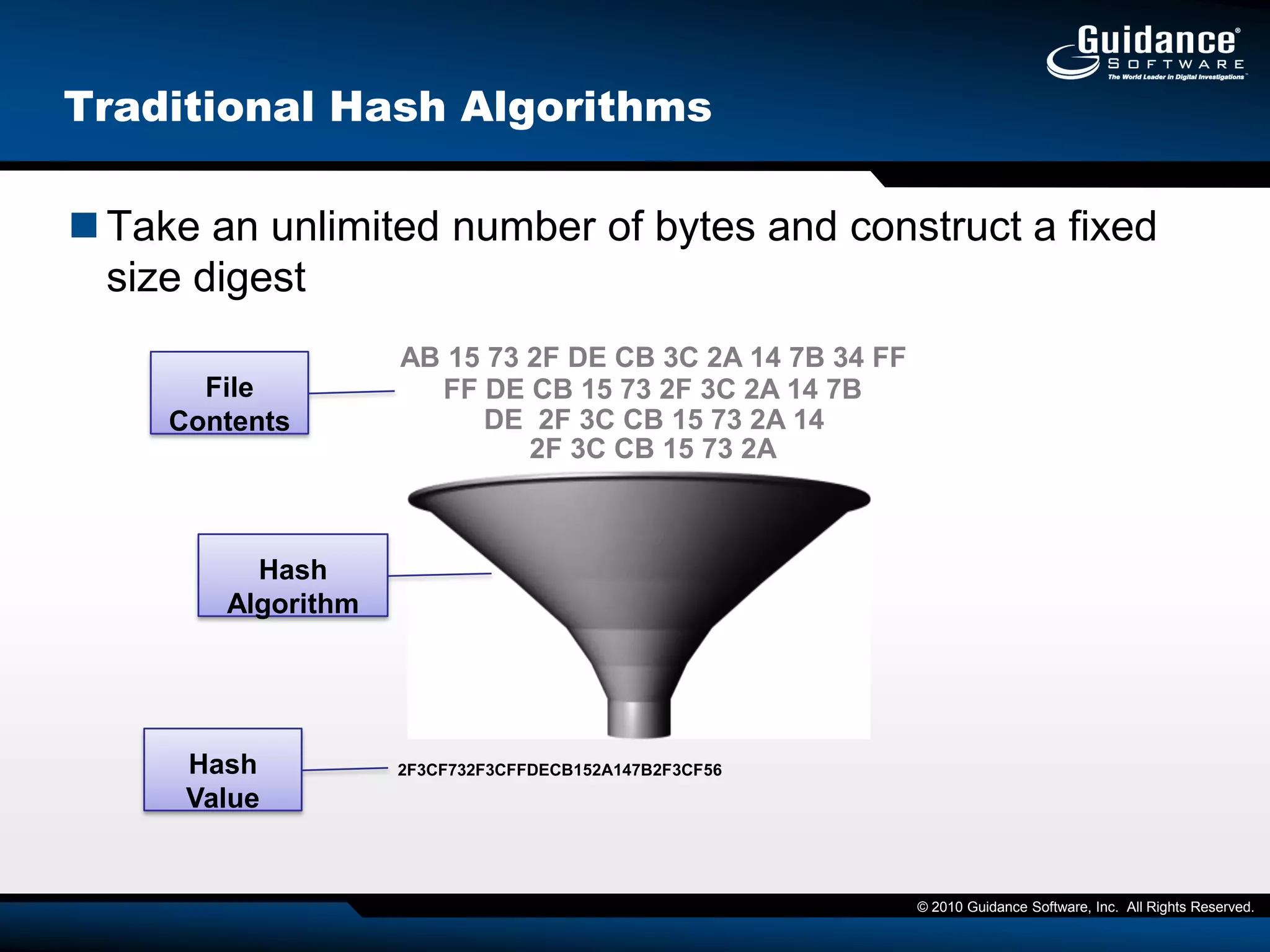
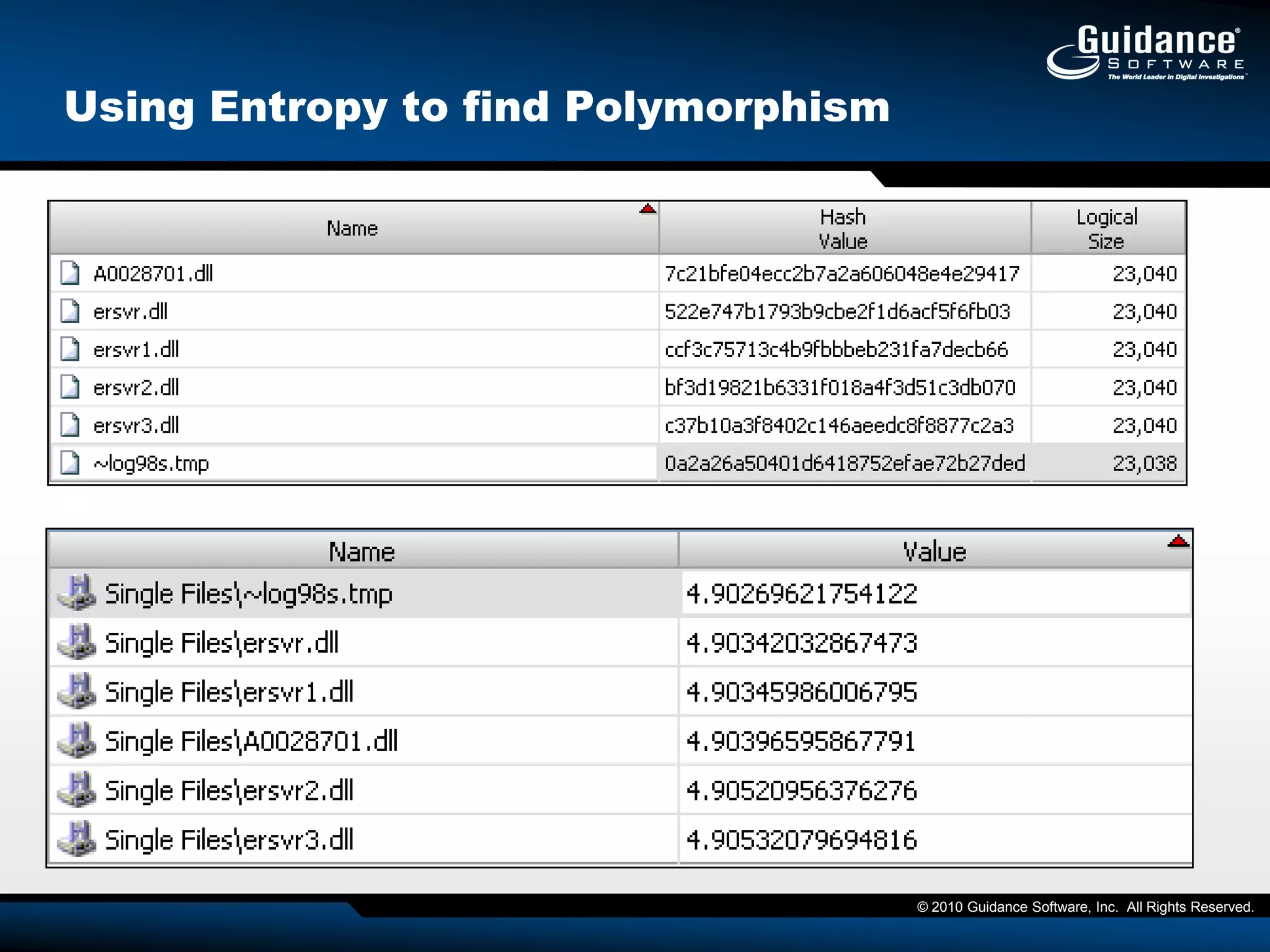
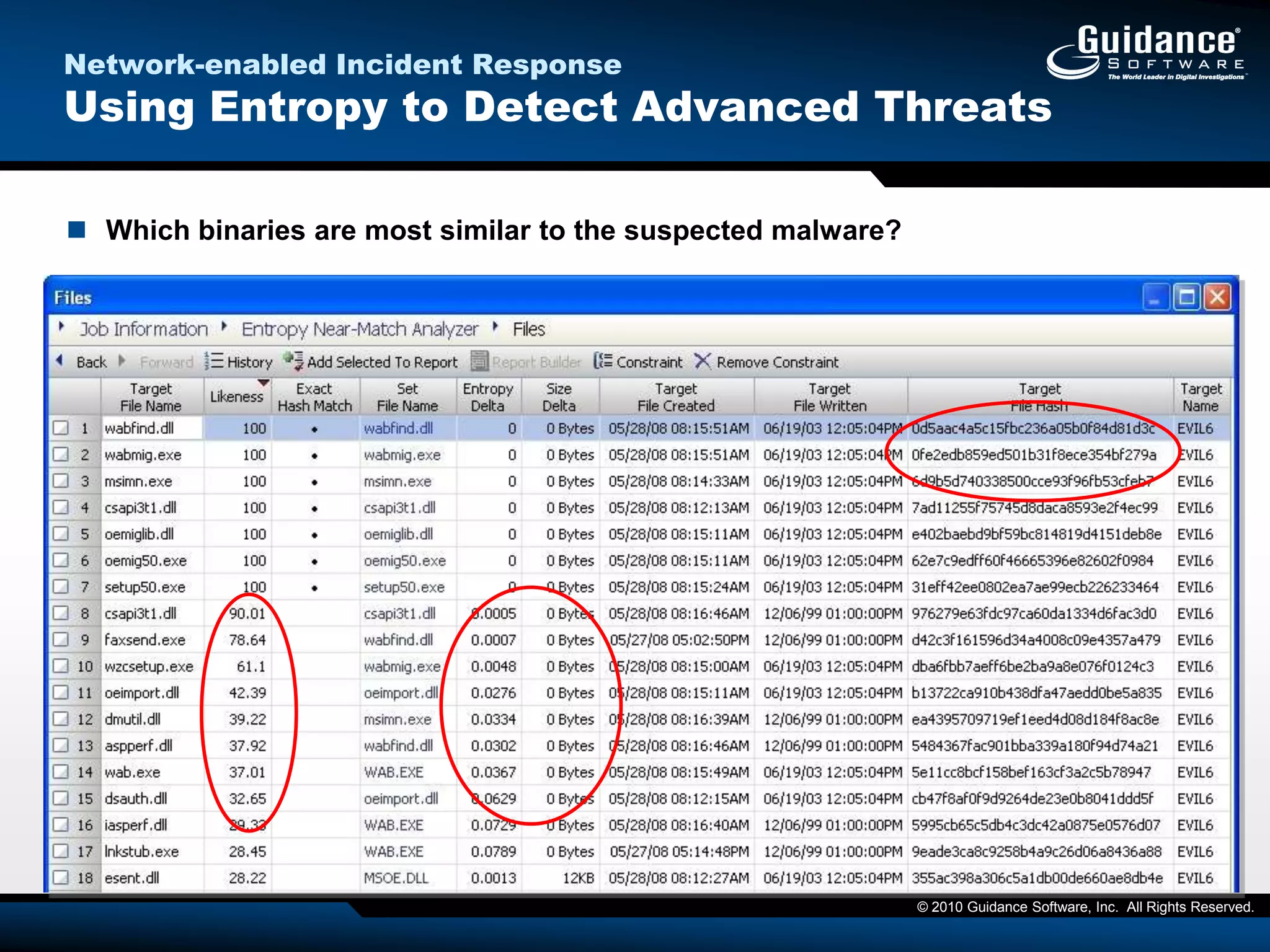
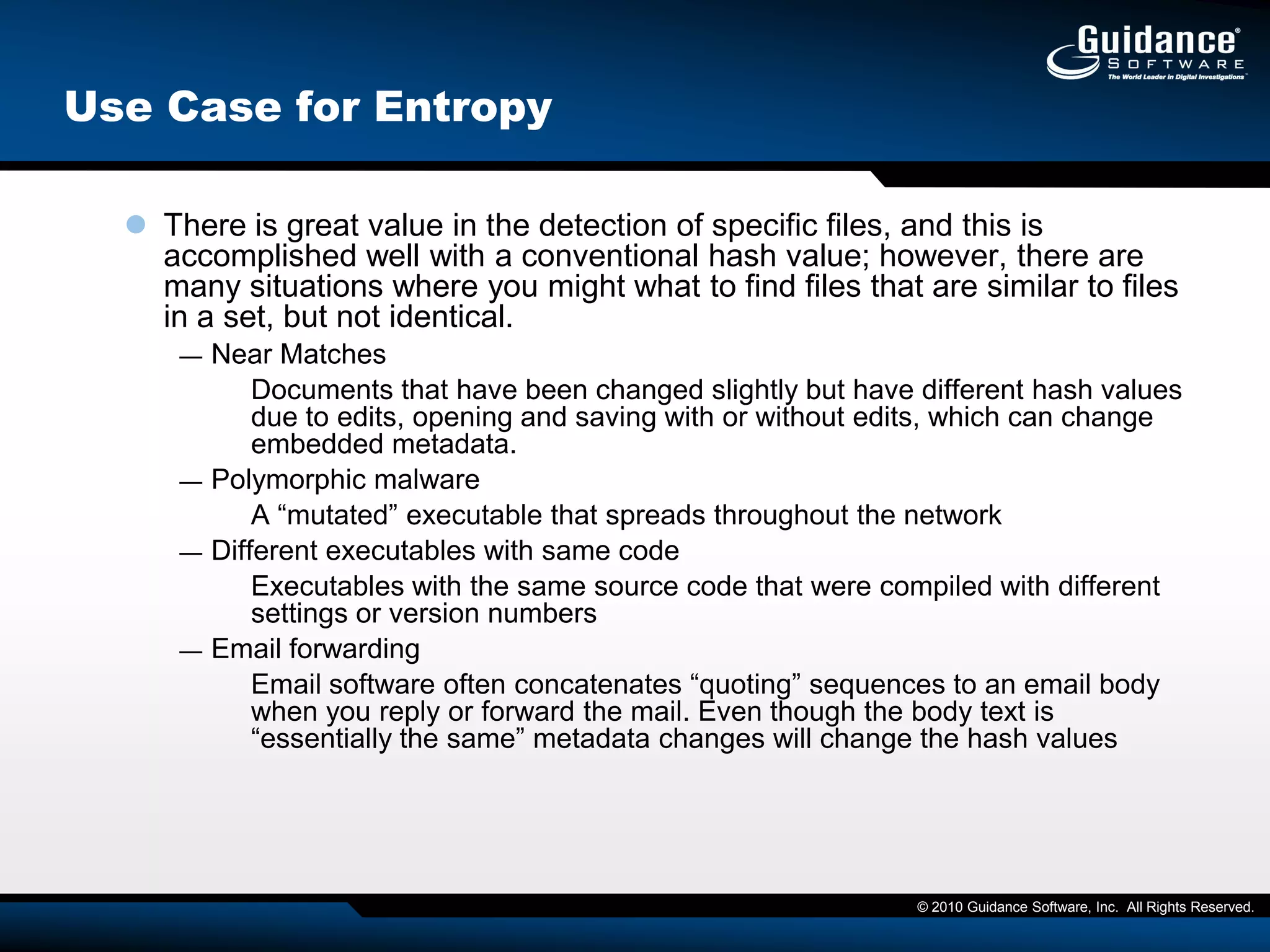
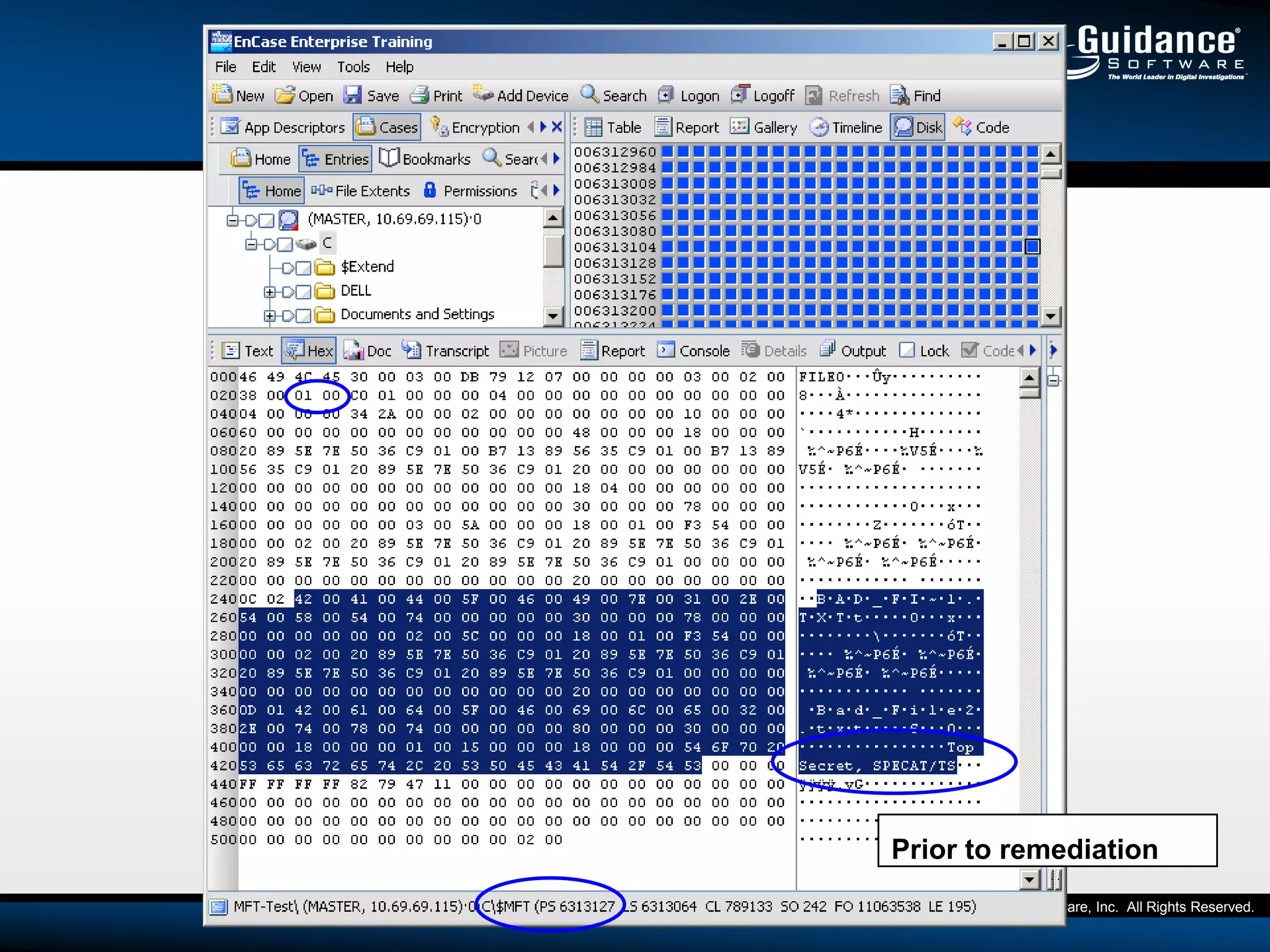
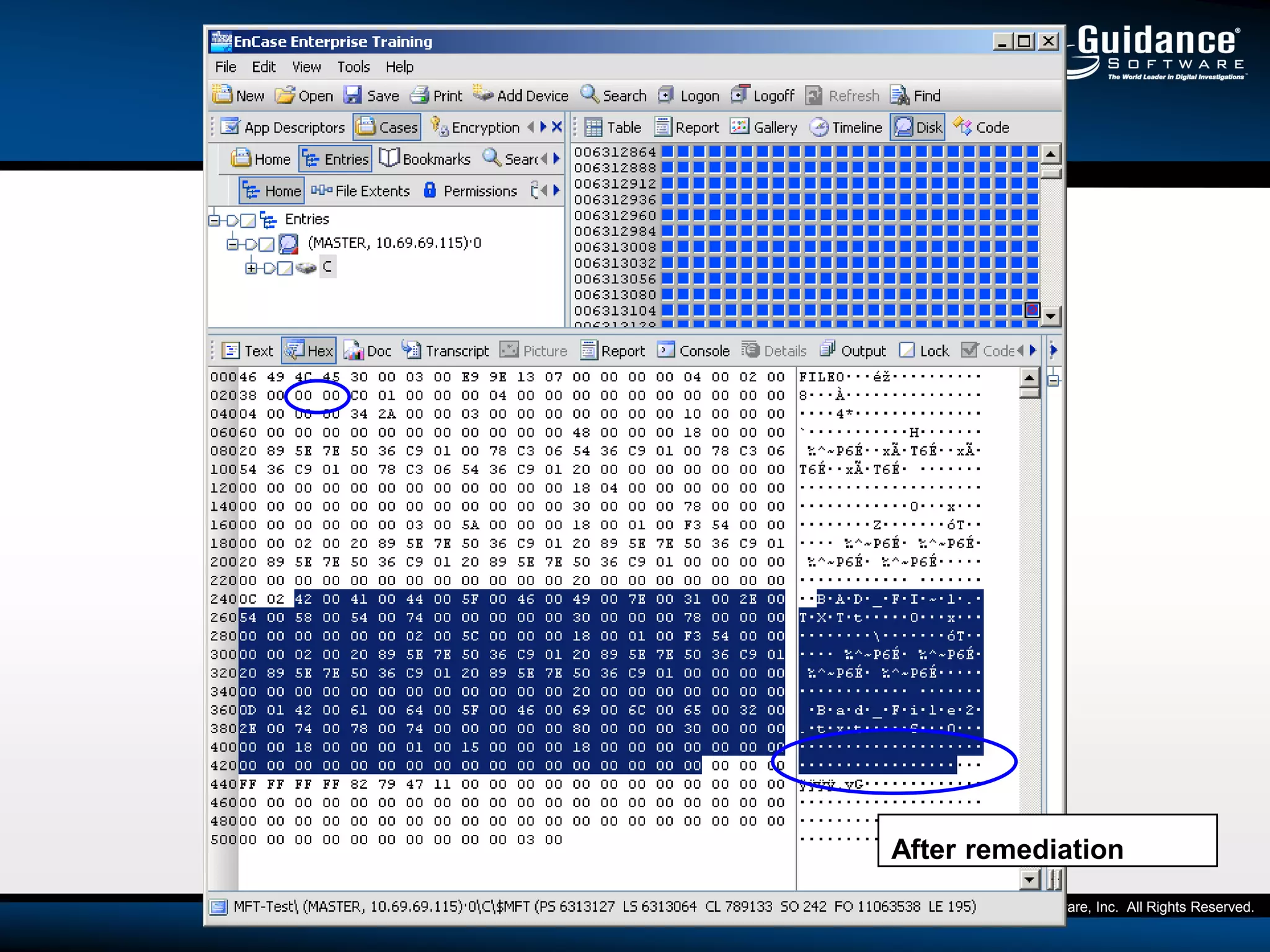
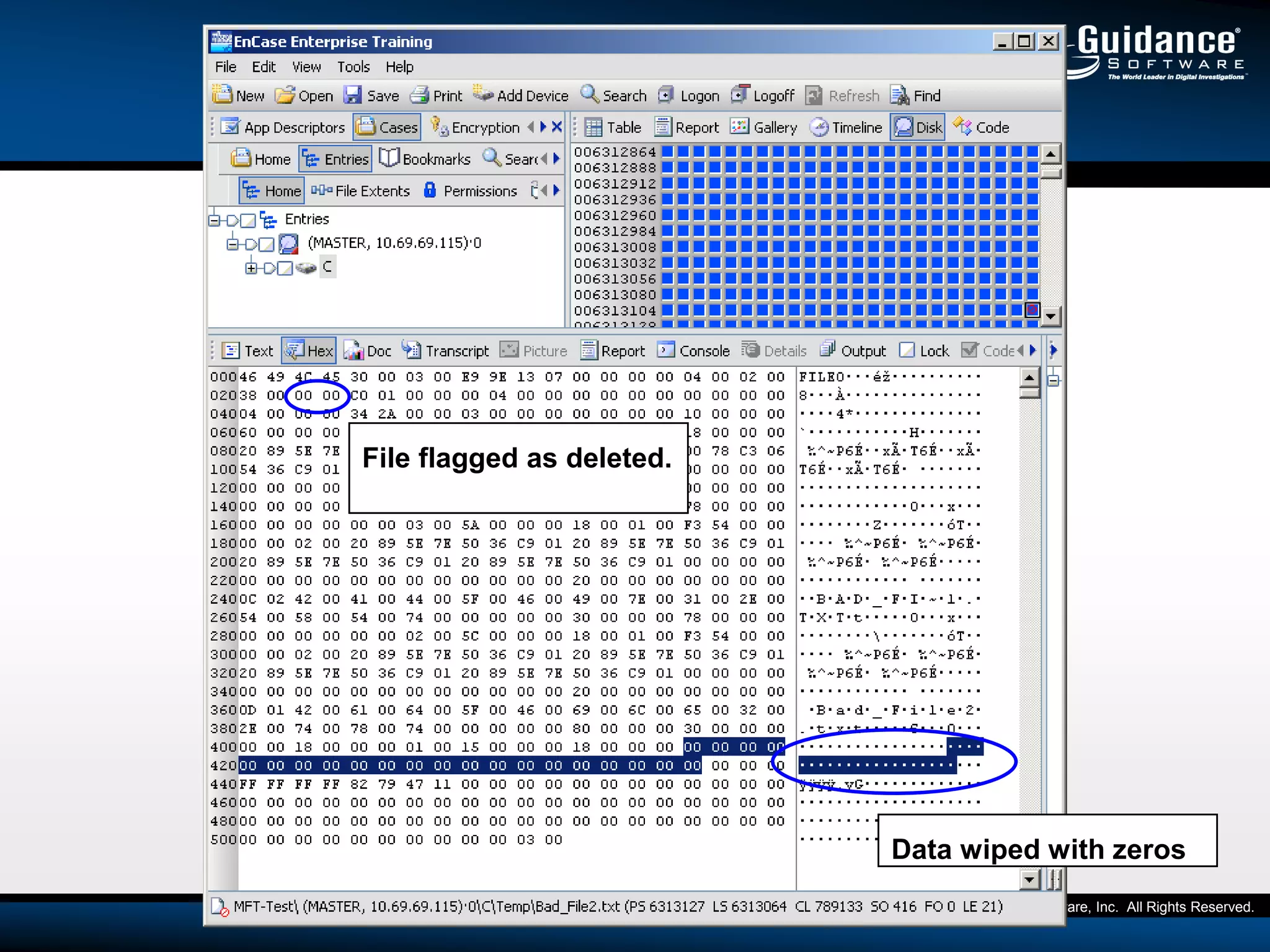
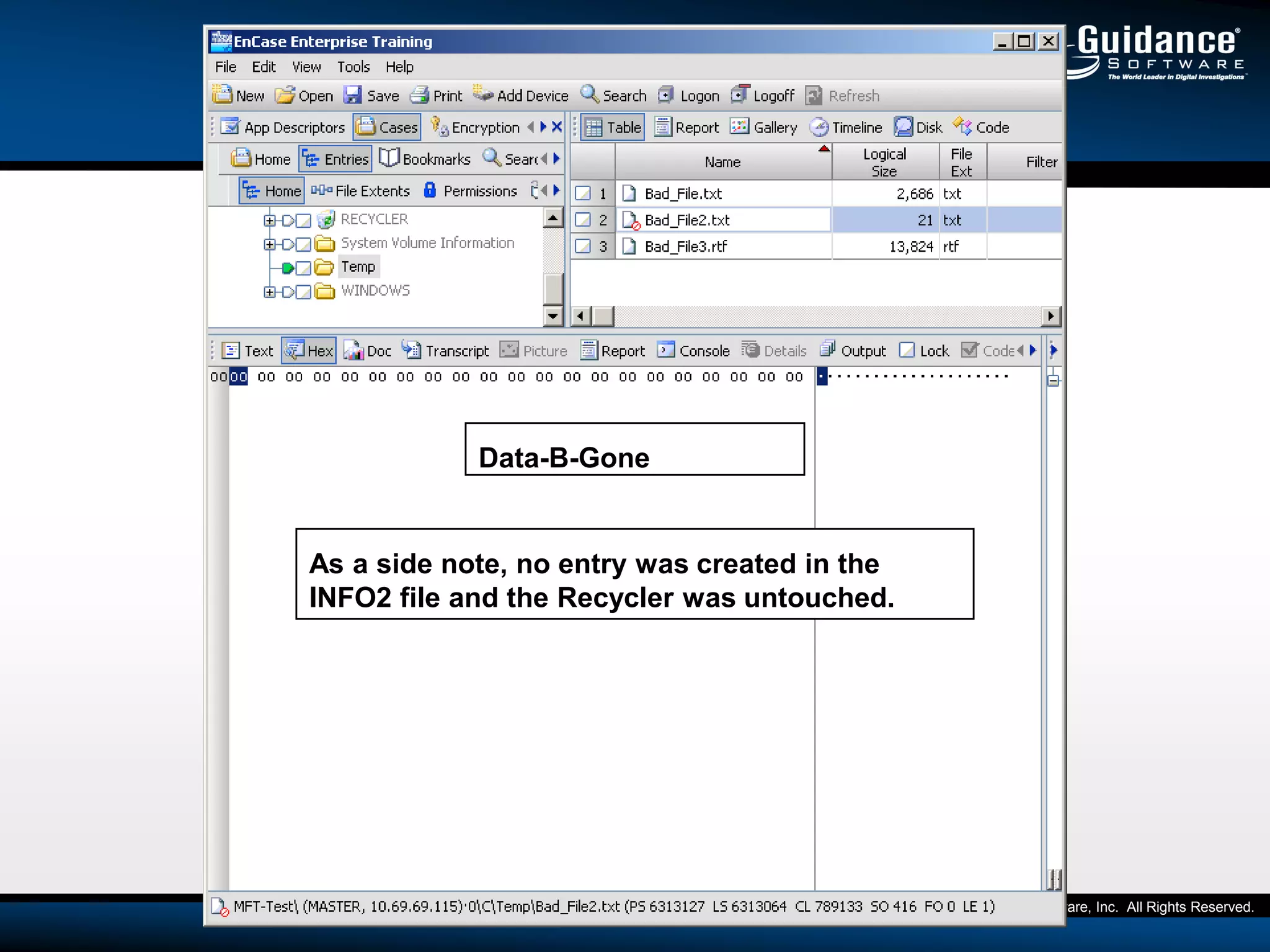
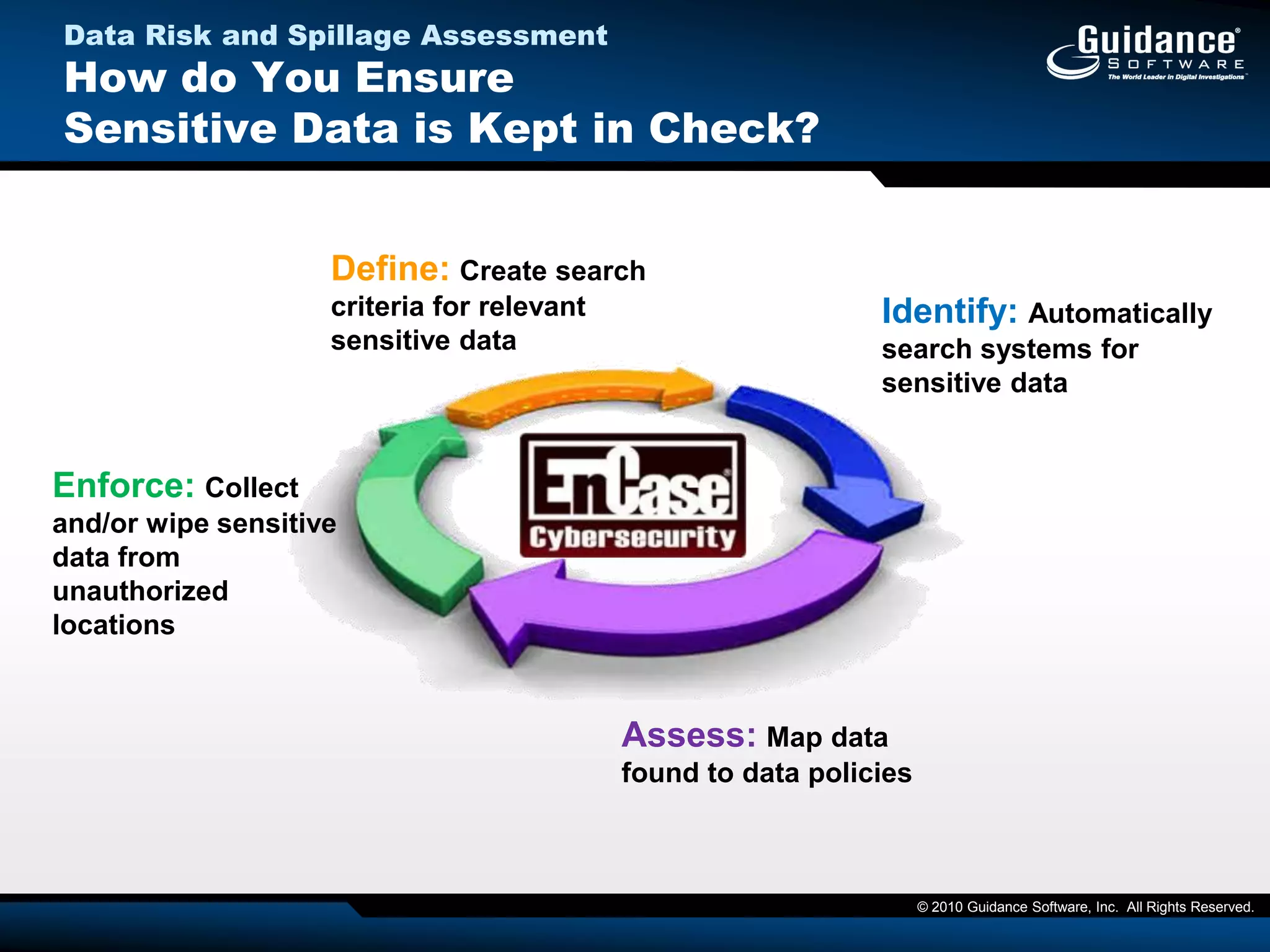
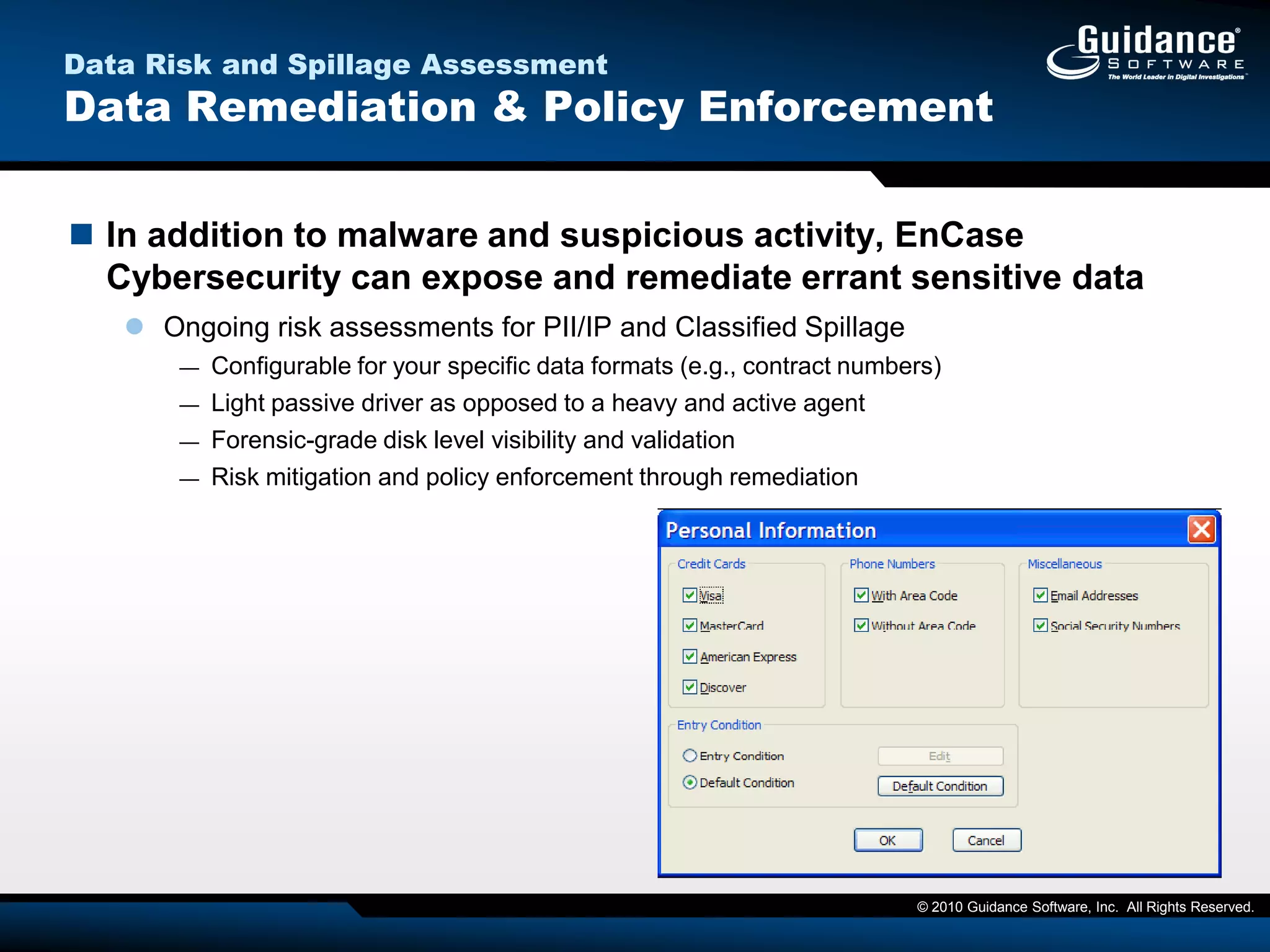
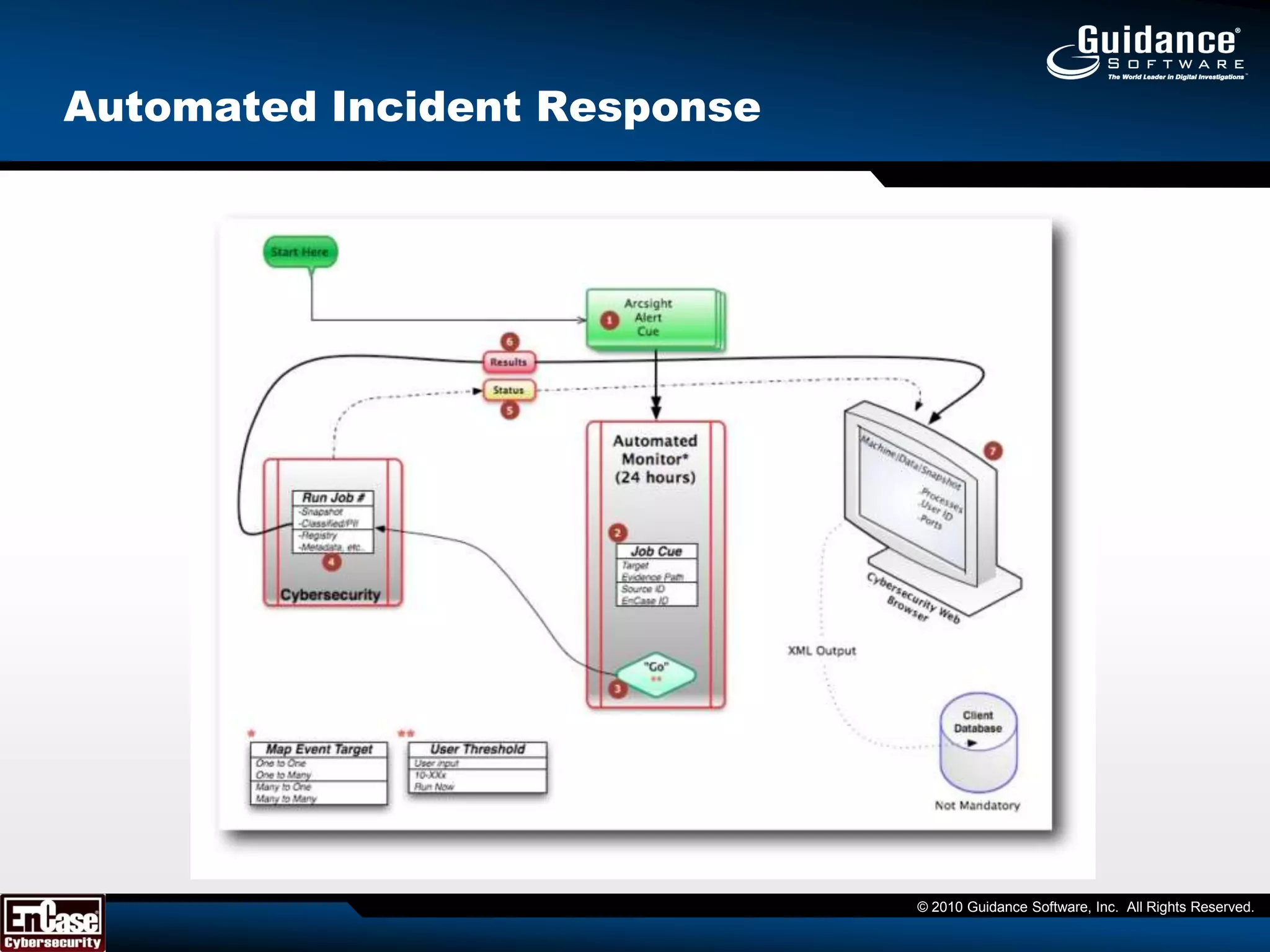
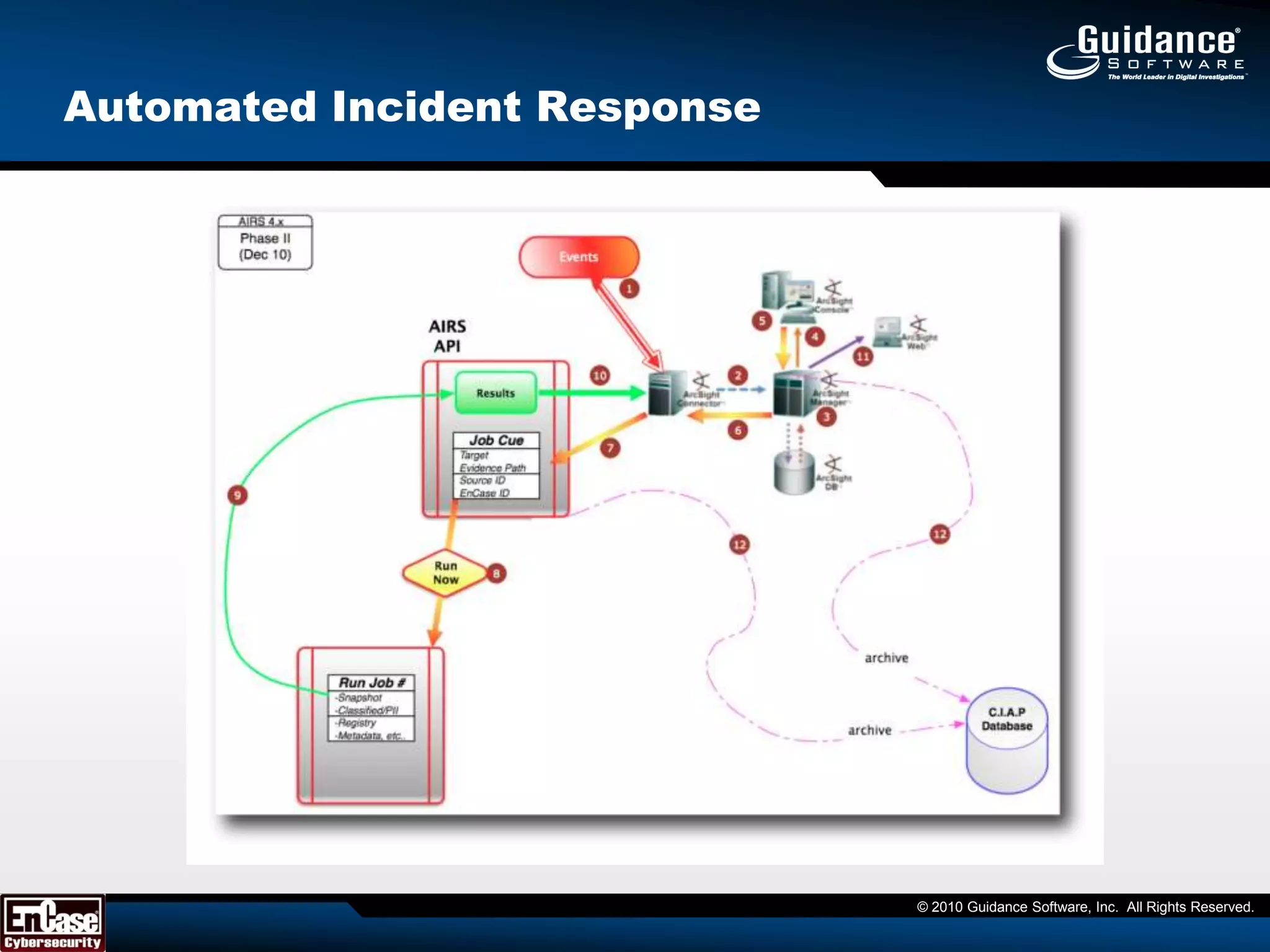
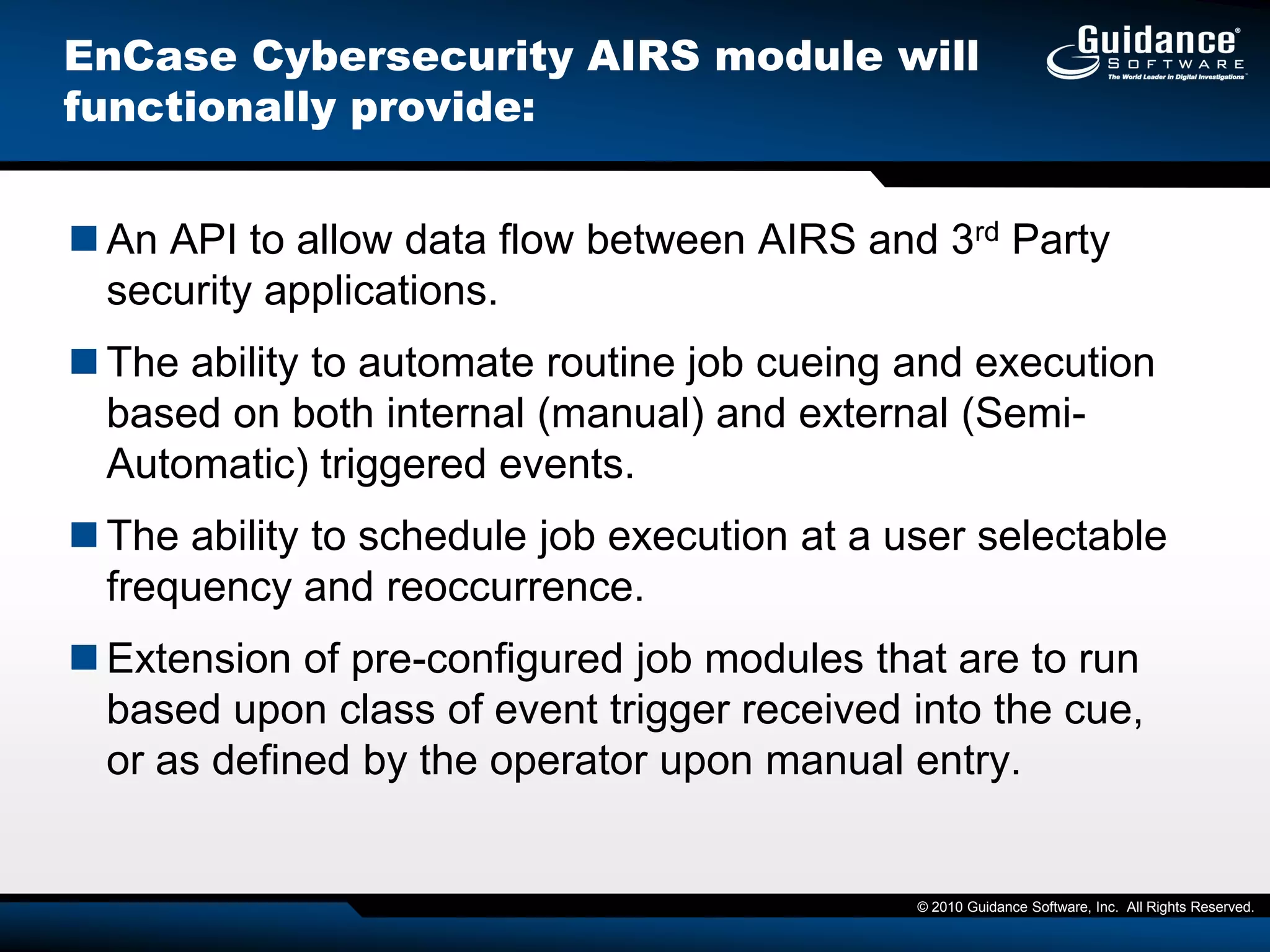
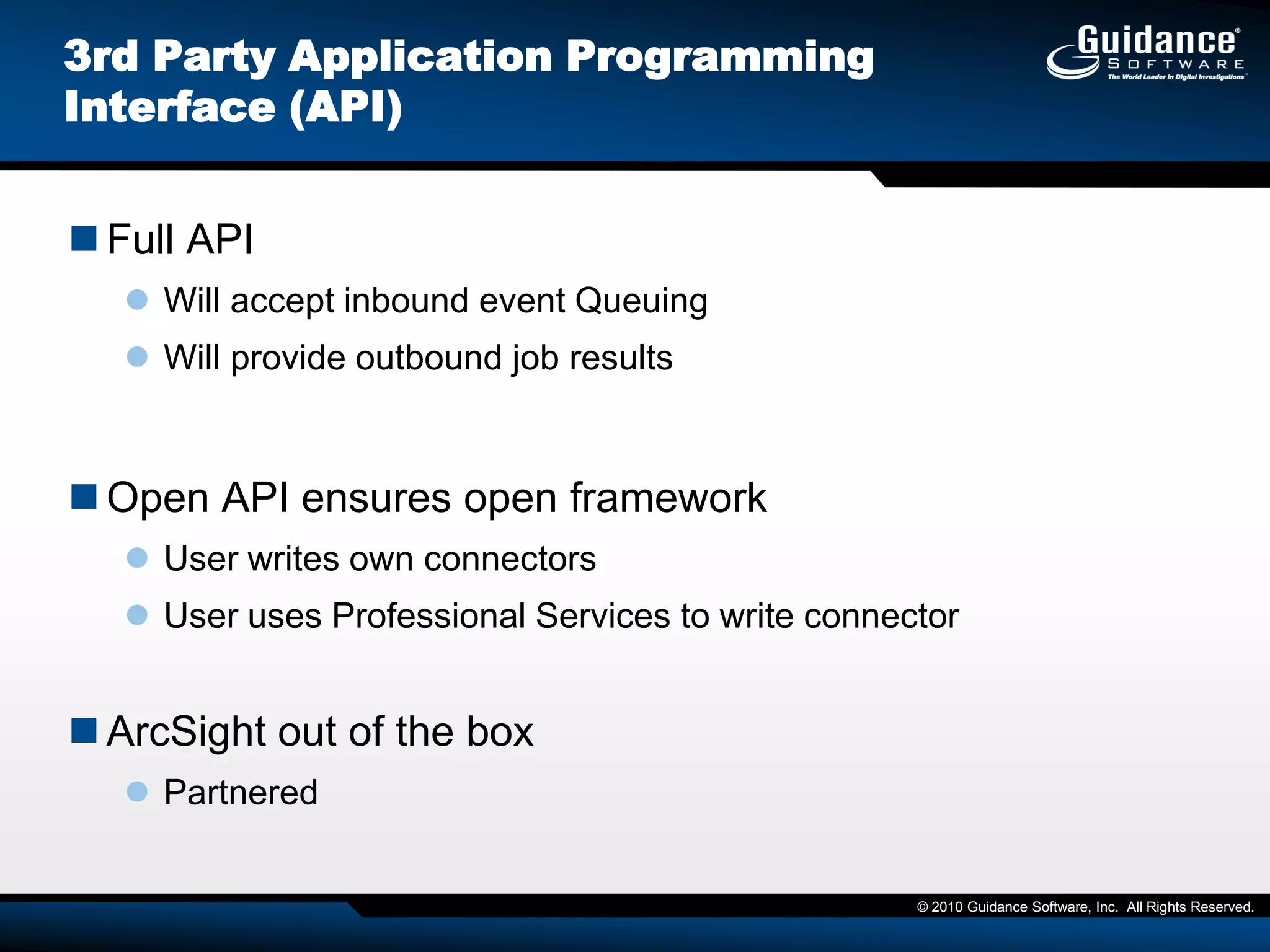
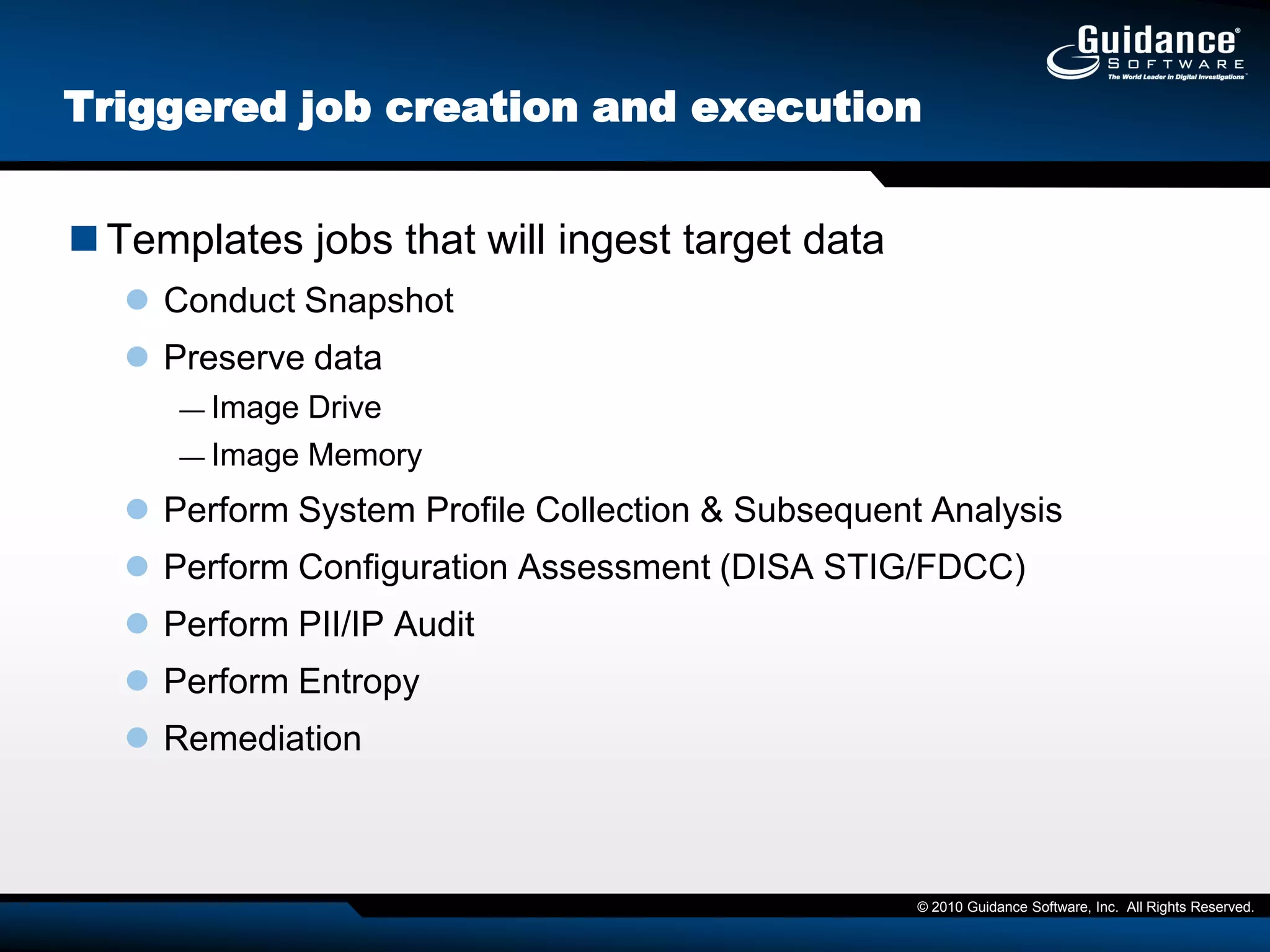
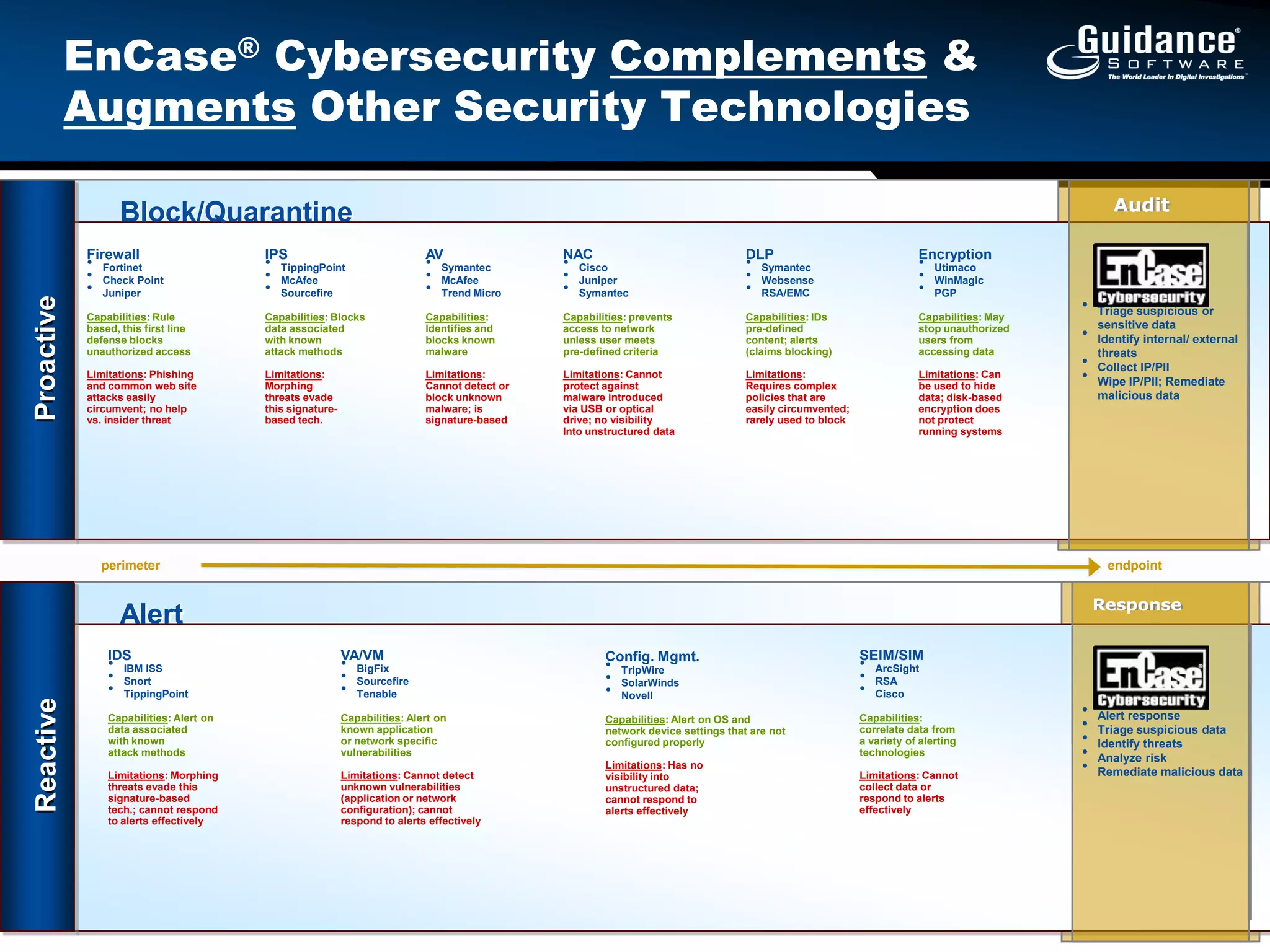
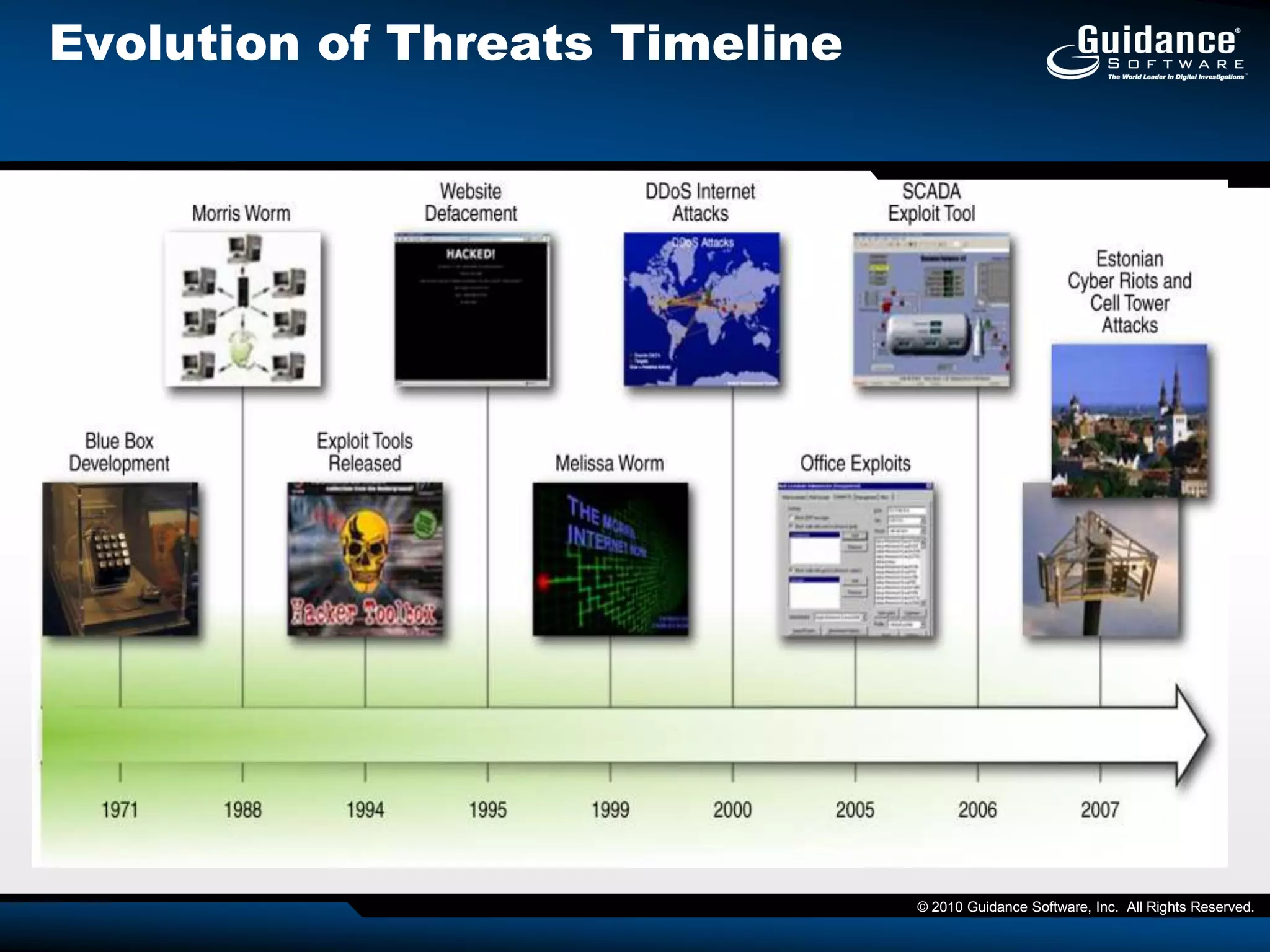
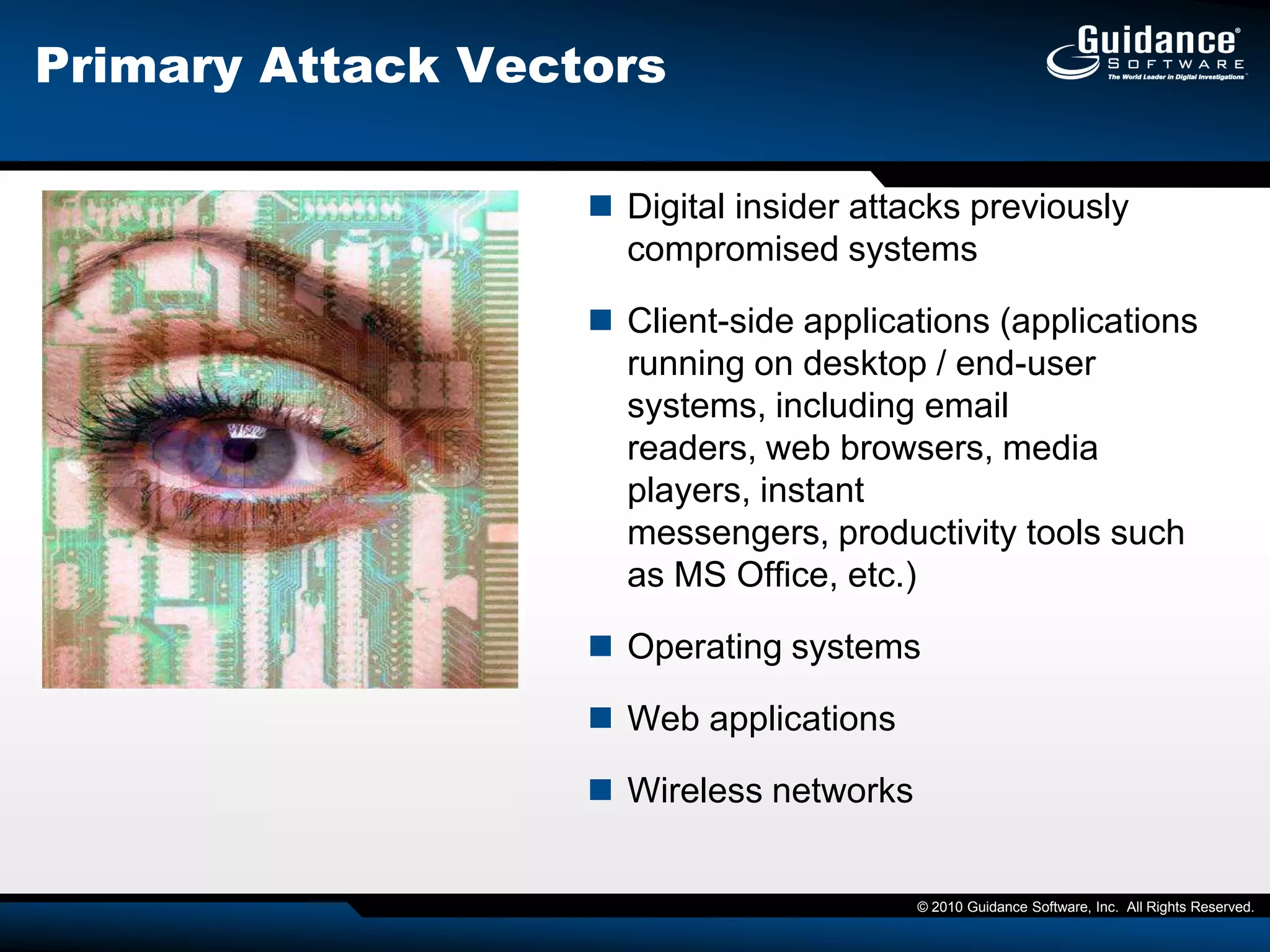
The document discusses the evolution of incident response and data auditing within cybersecurity, emphasizing the challenges posed by advanced threats, such as polymorphic malware and insider attacks. It highlights the importance of tools like Encase Cybersecurity for proactive data security, compliance auditing, and incident response, while also detailing the methods for malware detection and the significance of system deviation assessments. The need for continuous adaptation to new technologies and evolving tactics used by cybercriminals is underscored throughout the document.


![Superior Court Forensic Expert (Expert Witness Junkie)Experience:United States Navy Career: - Electronic/Information/Cyber Warfare & SIGINTSr. Cyber Advisor to US STRATCOM [Team BAH under USAMS]](https://image.slidesharecdn.com/brazilcybersecurityfinaljim-100809115709-phpapp01/75/Cybersecurity-Jim-Butterworth-7-2048.jpg)
![Commercial Intrusion and Forensic Expert to US NAVY HQ [CACI]](https://image.slidesharecdn.com/brazilcybersecurityfinaljim-100809115709-phpapp01/75/Cybersecurity-Jim-Butterworth-8-2048.jpg)