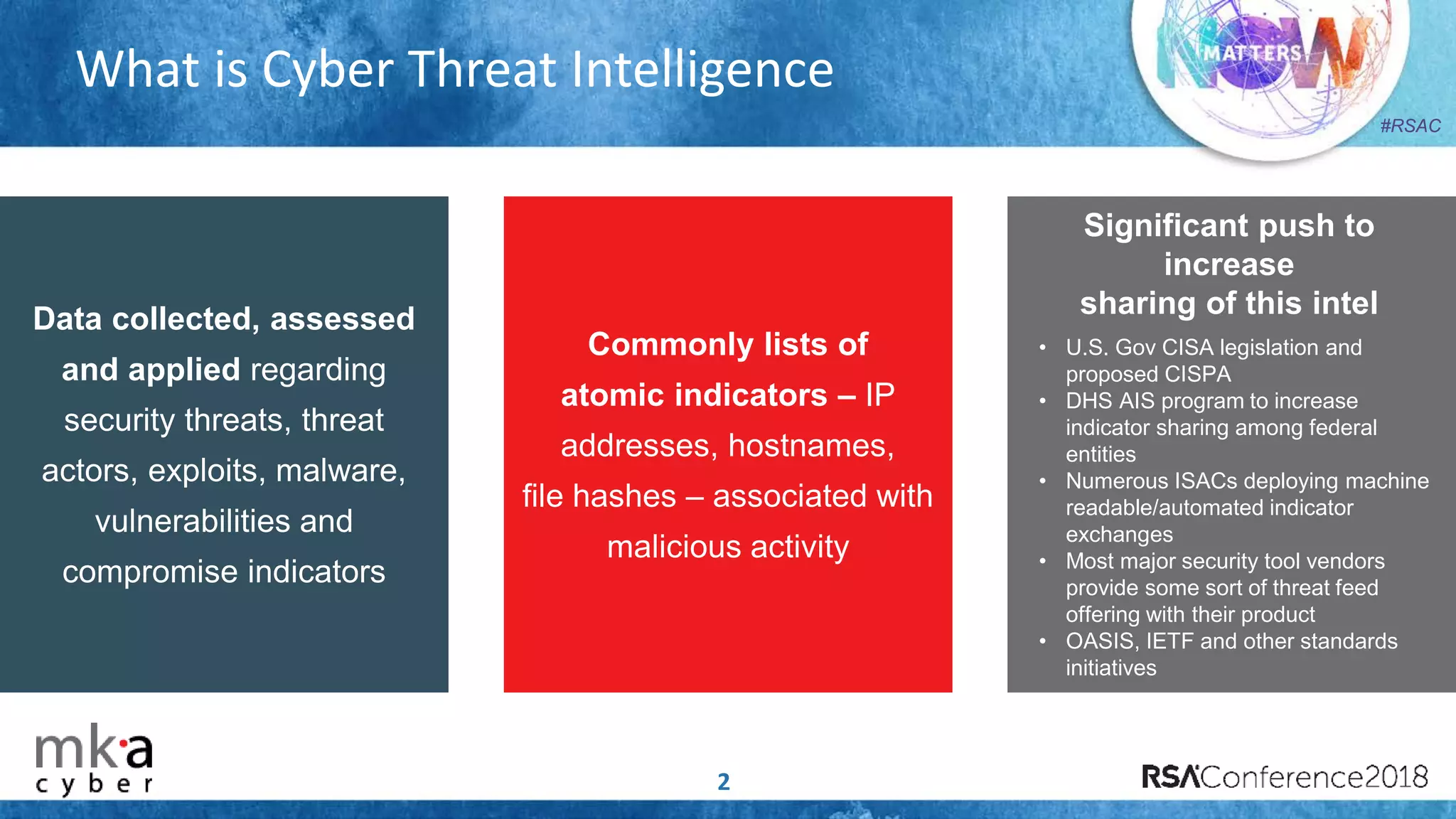
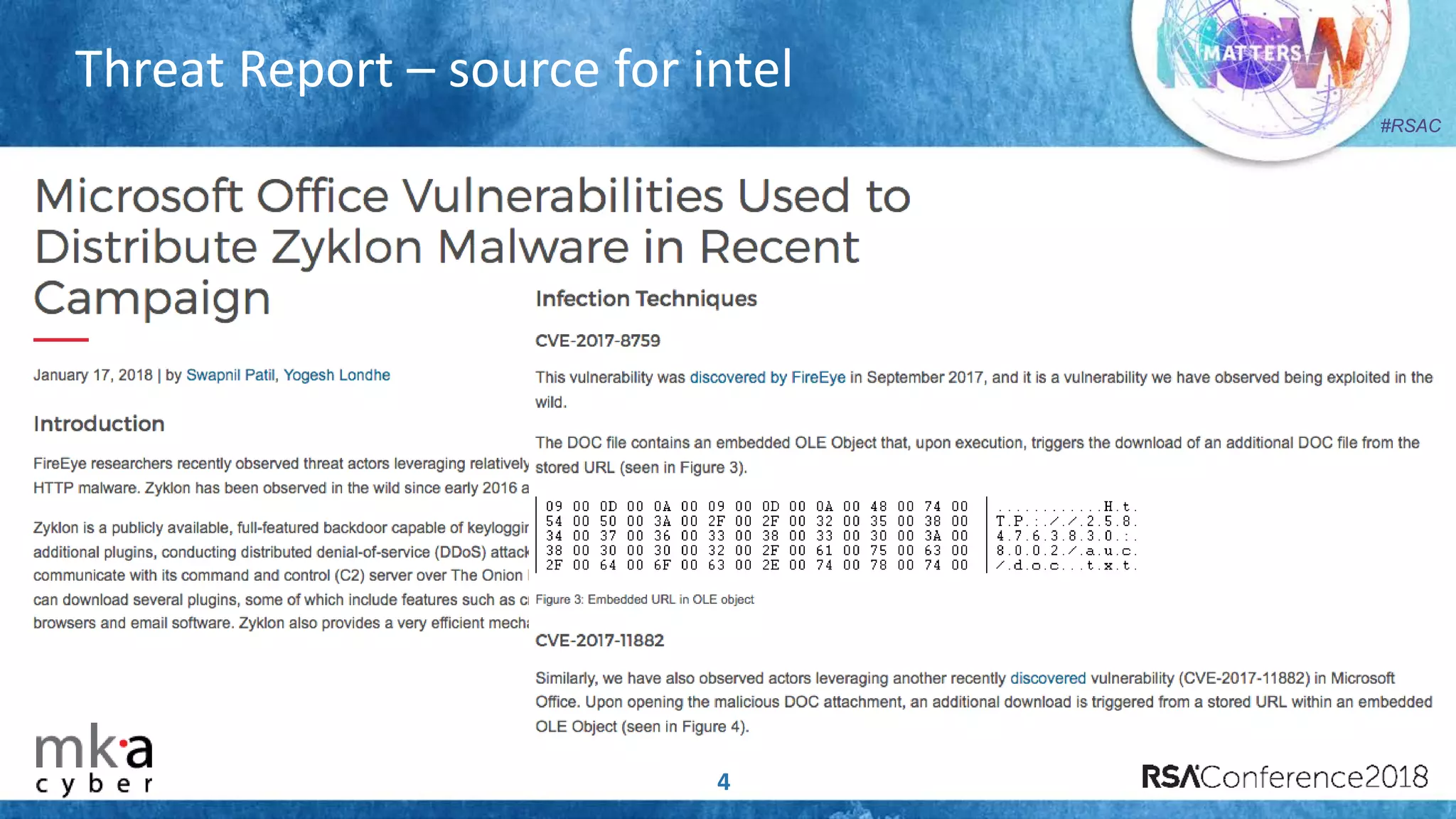
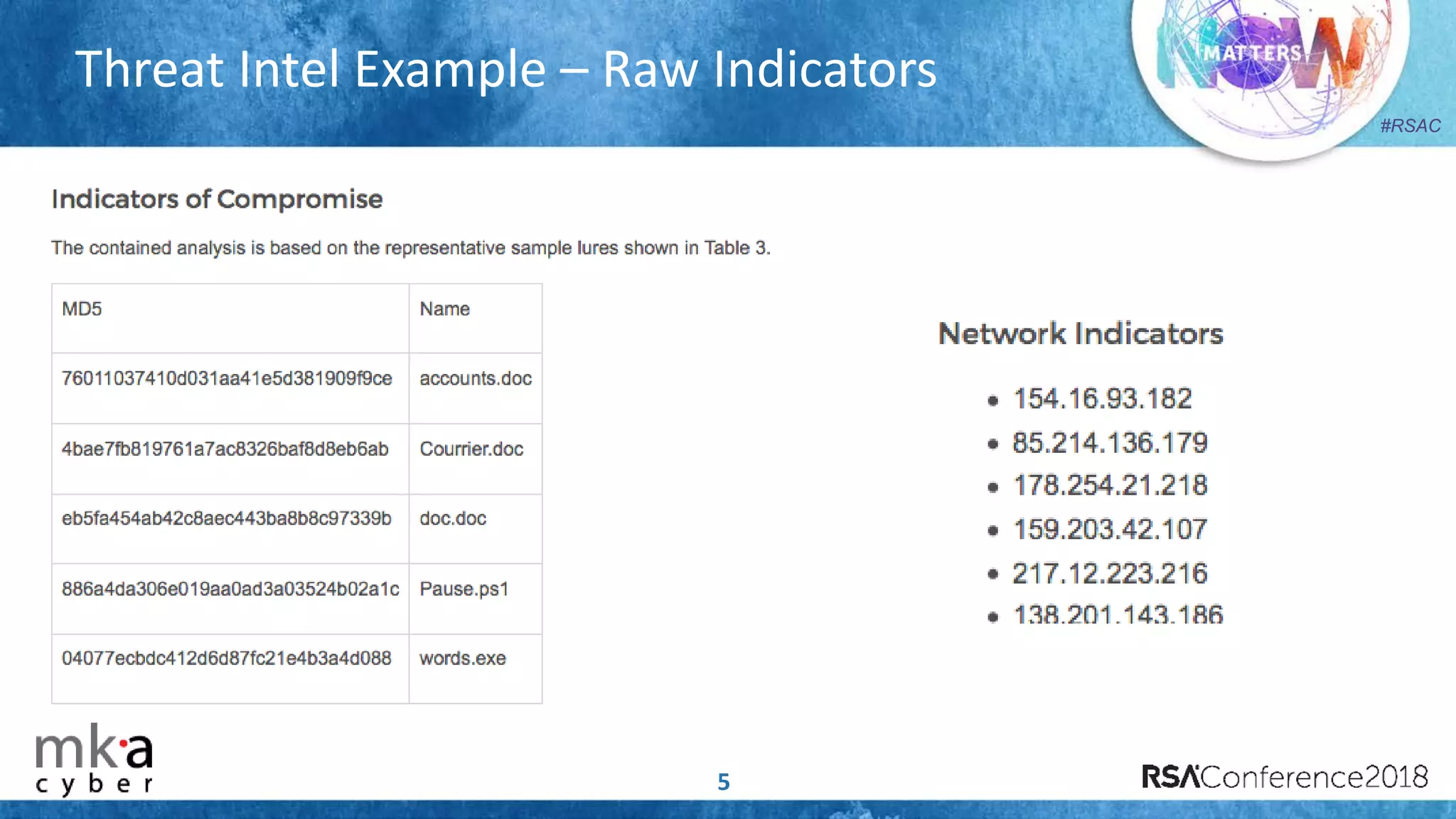
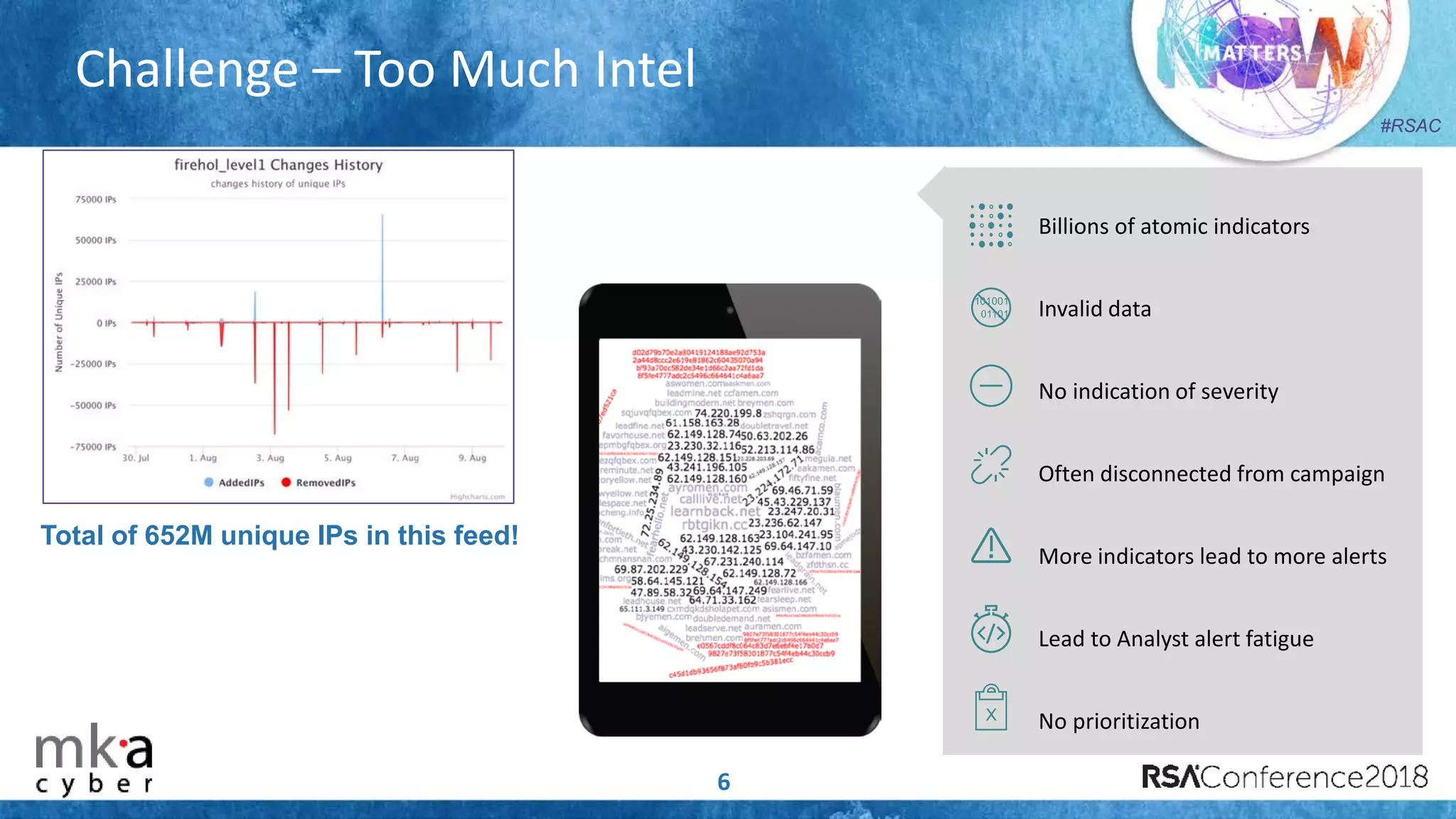
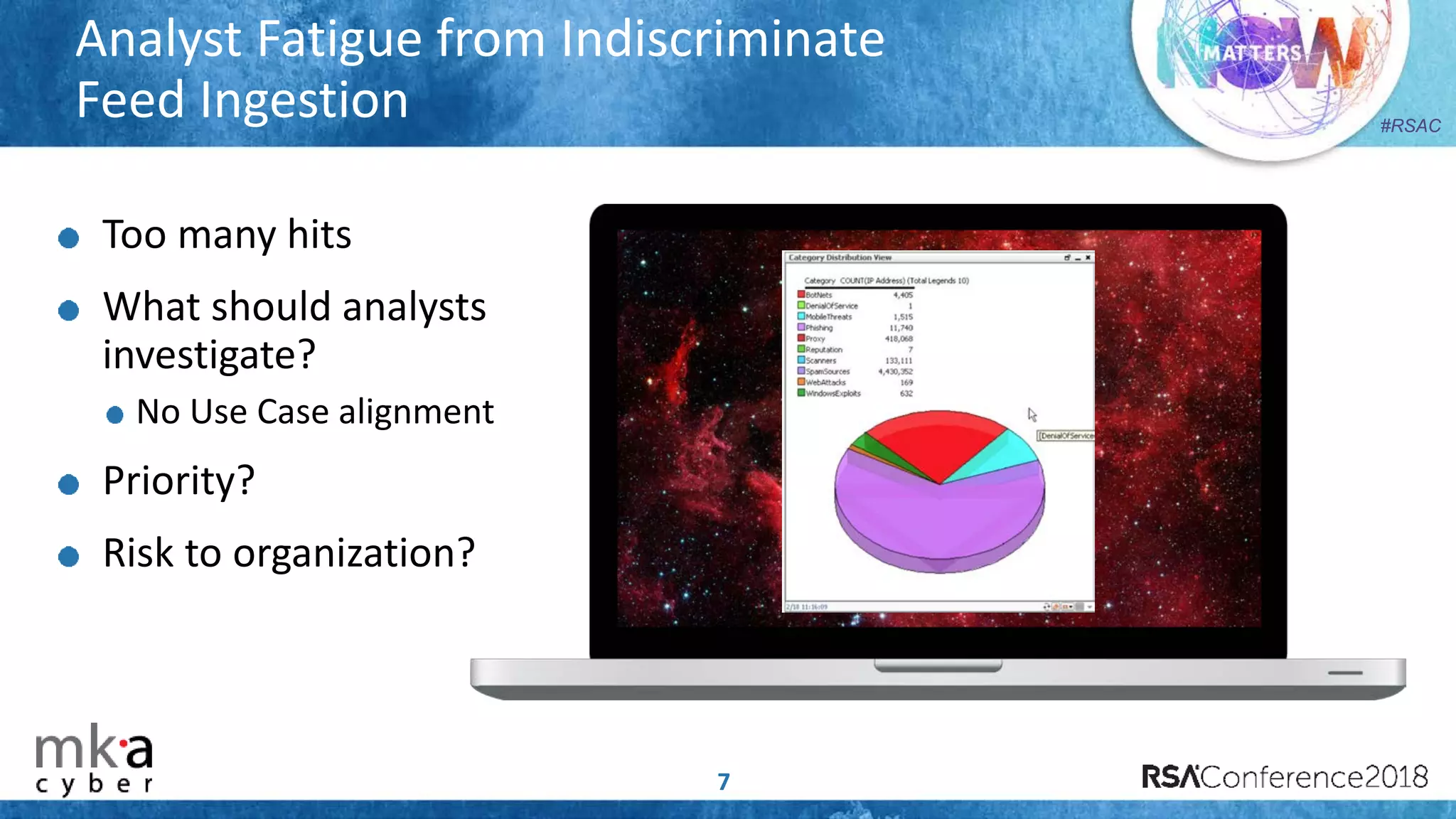
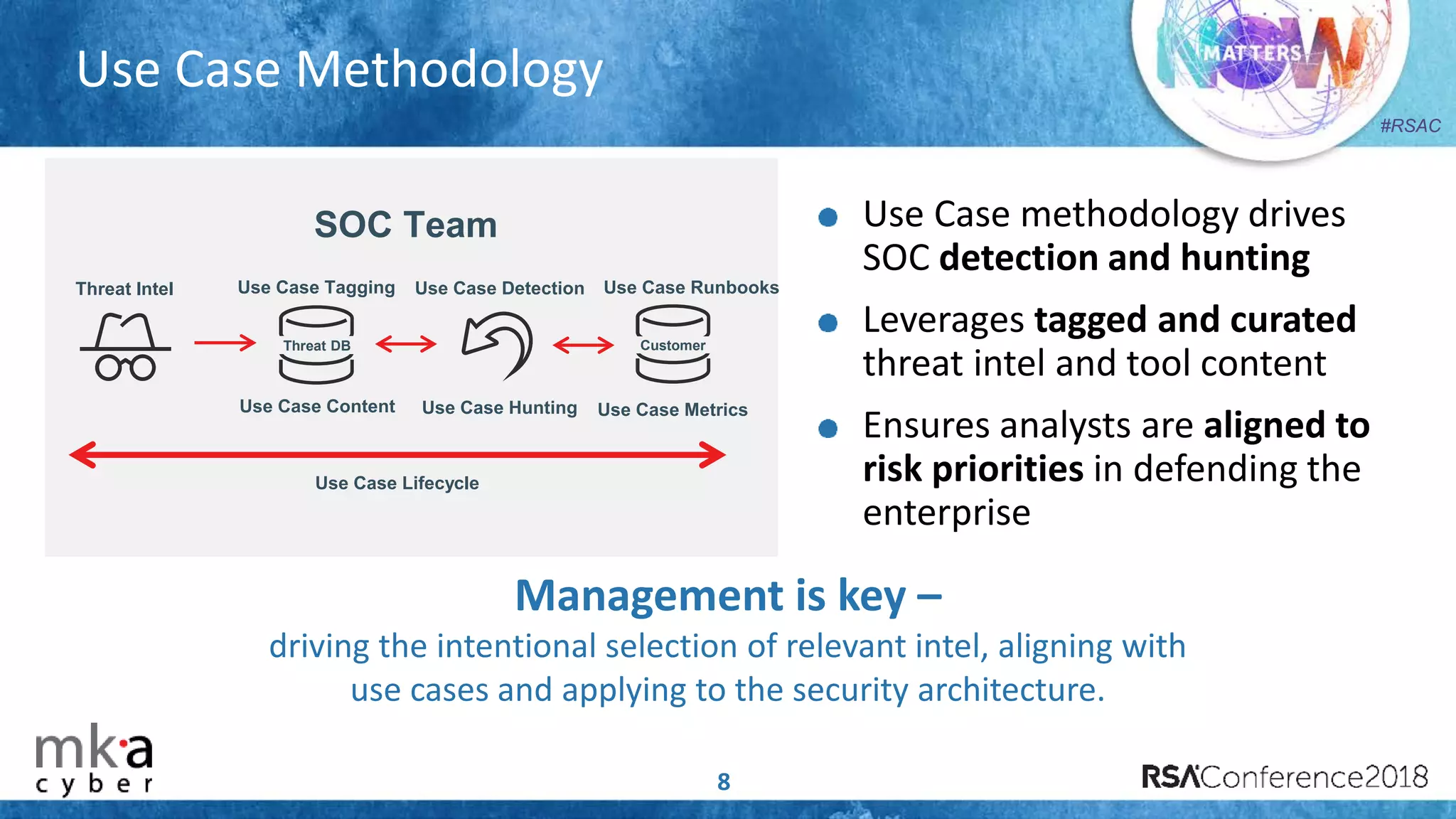
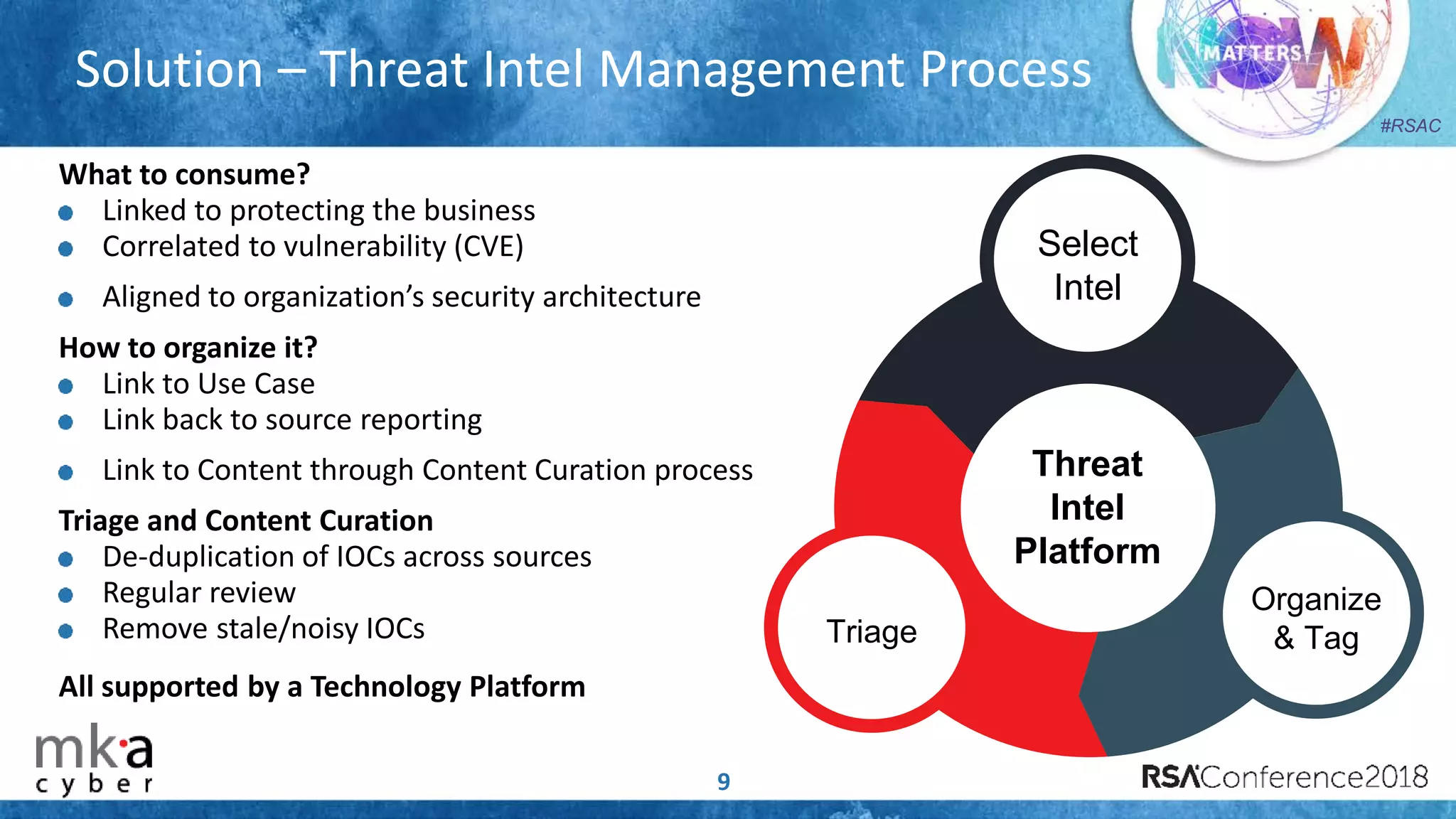
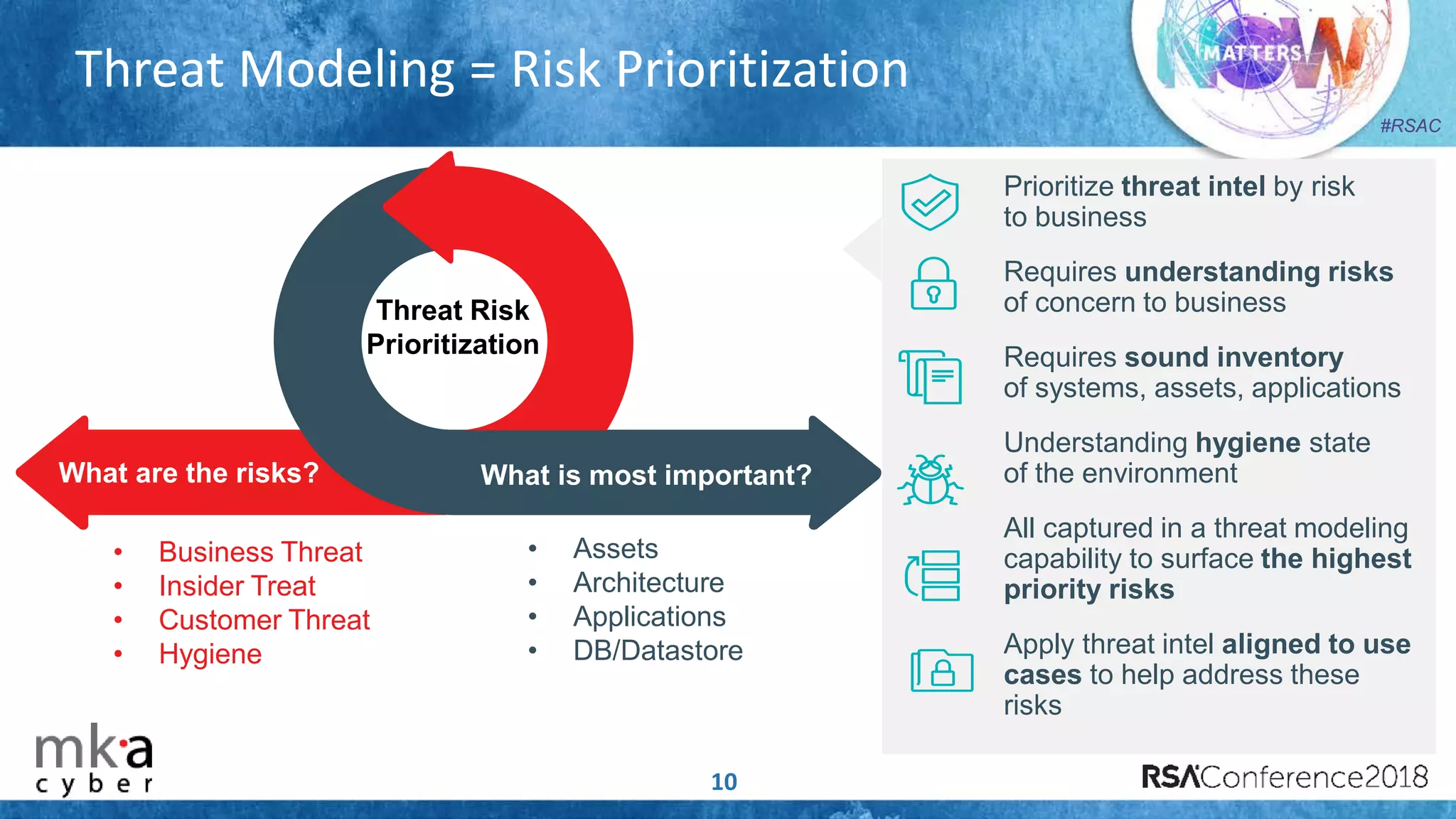
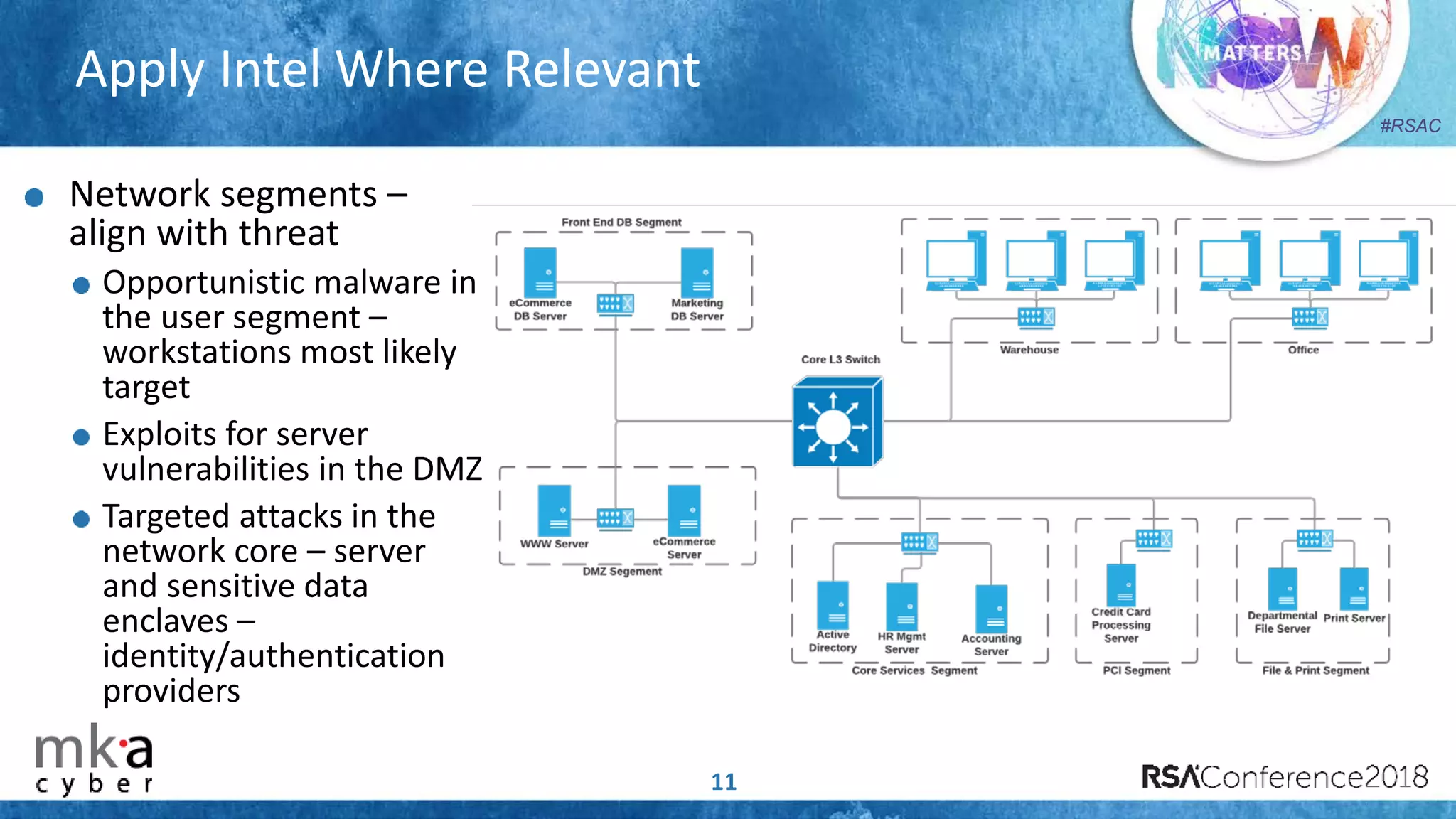
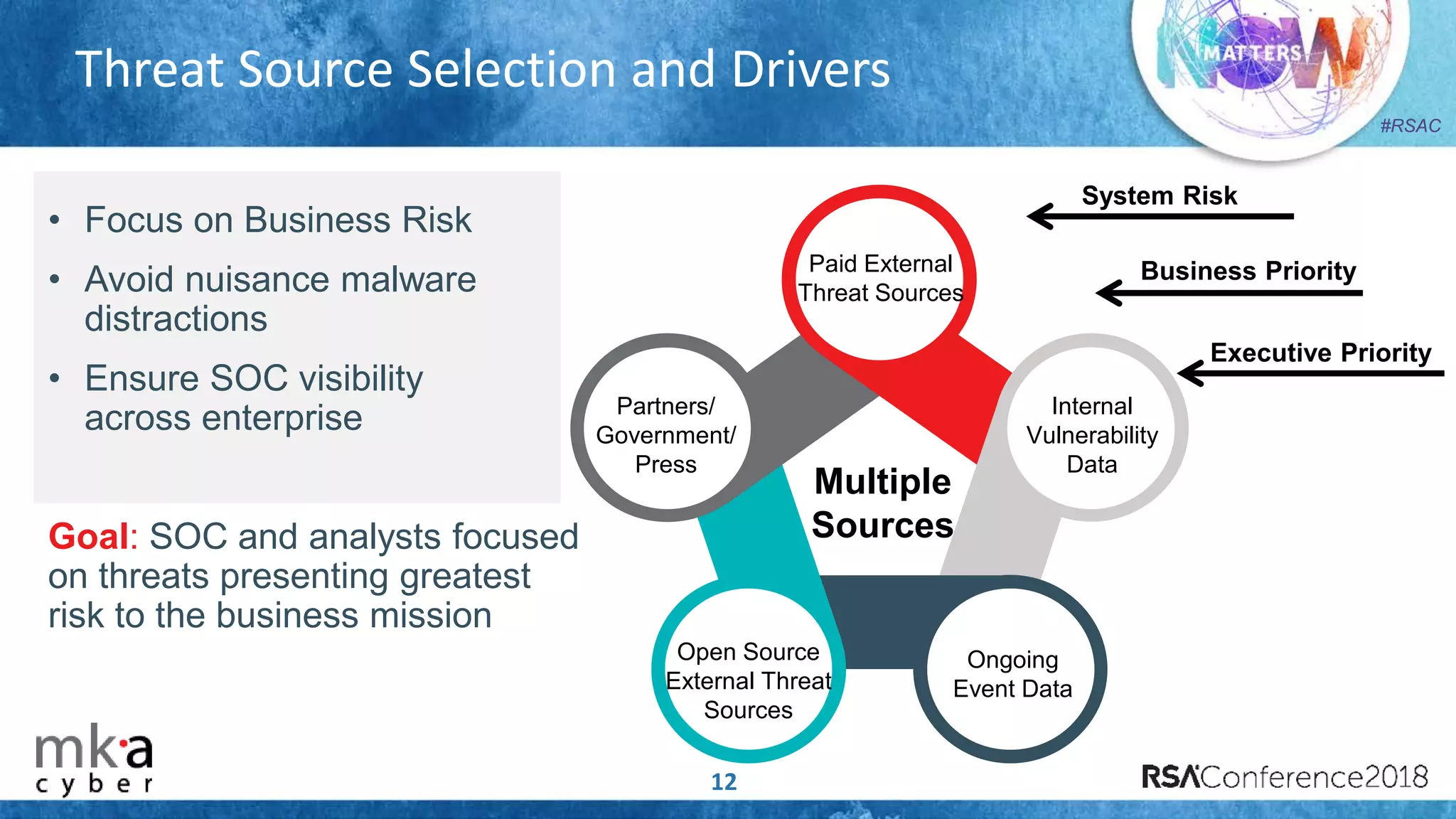
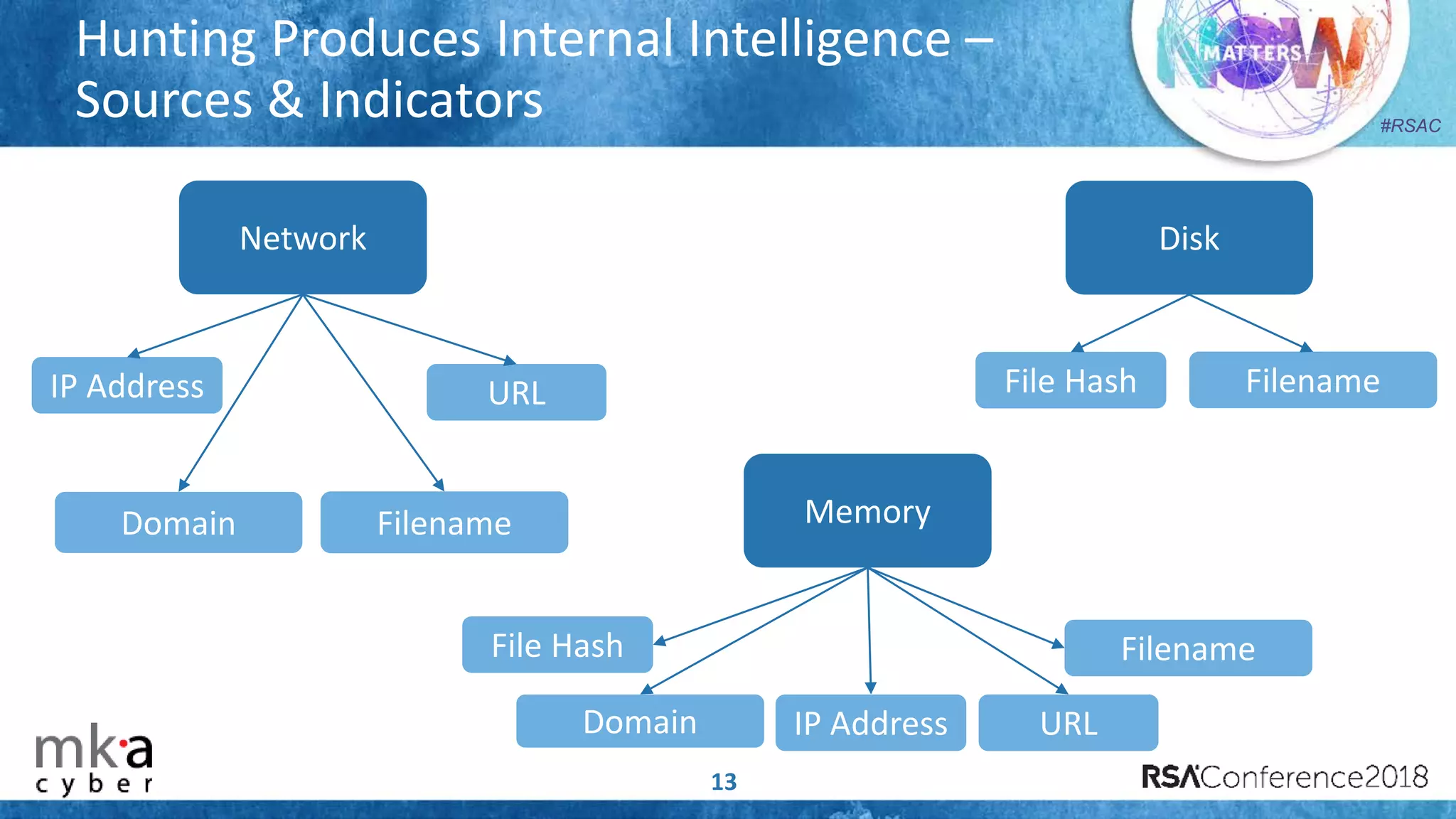
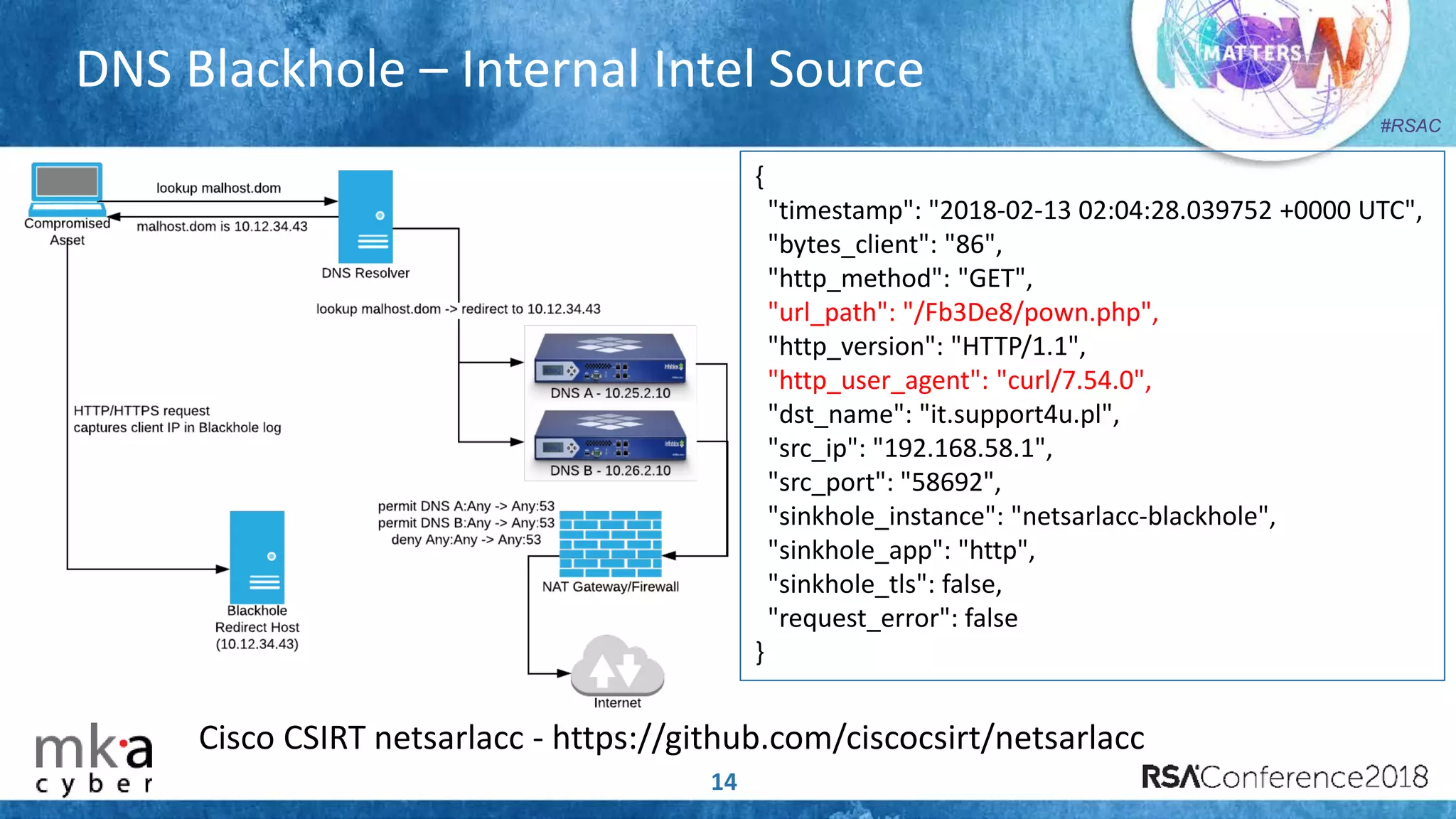
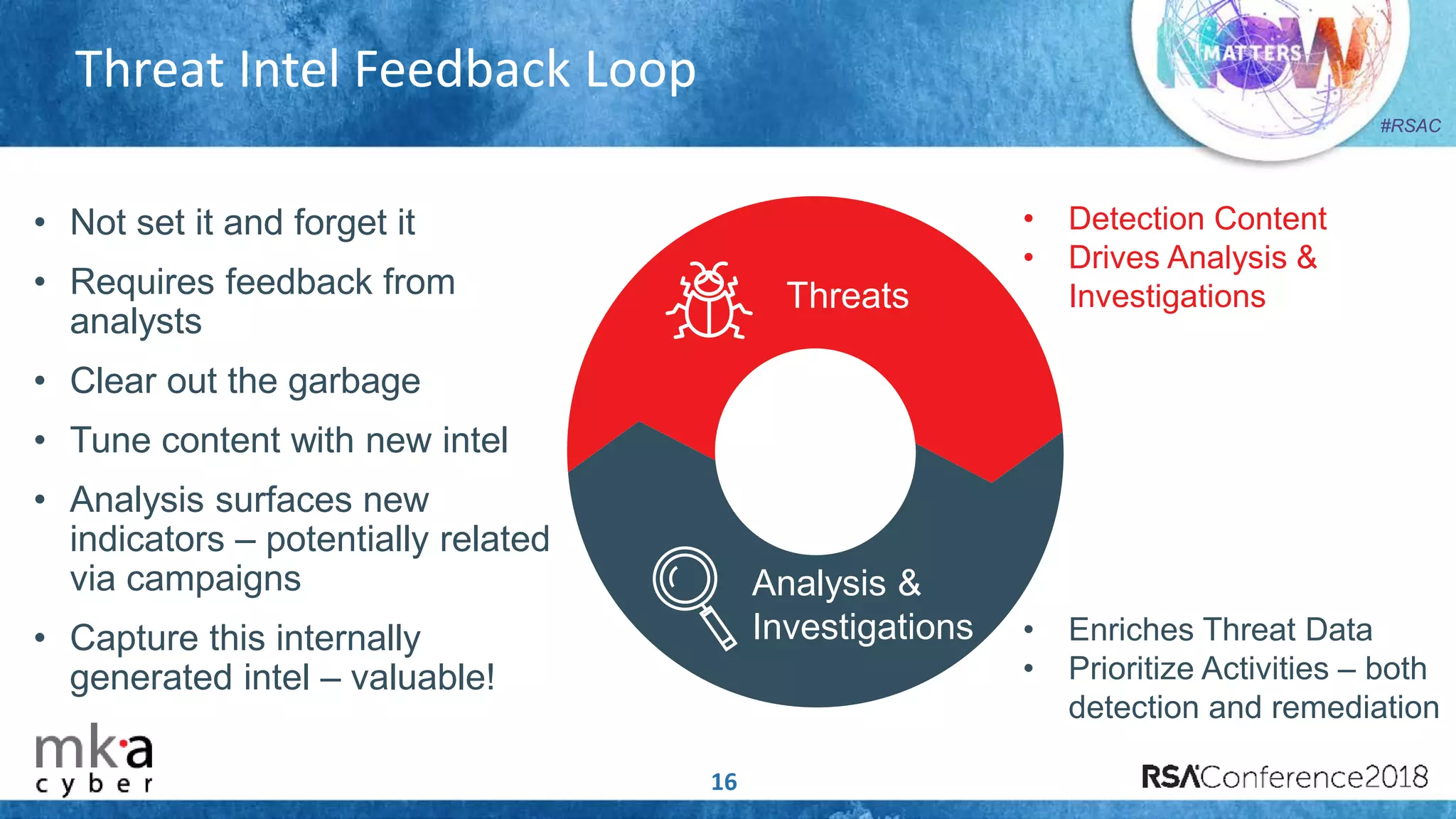
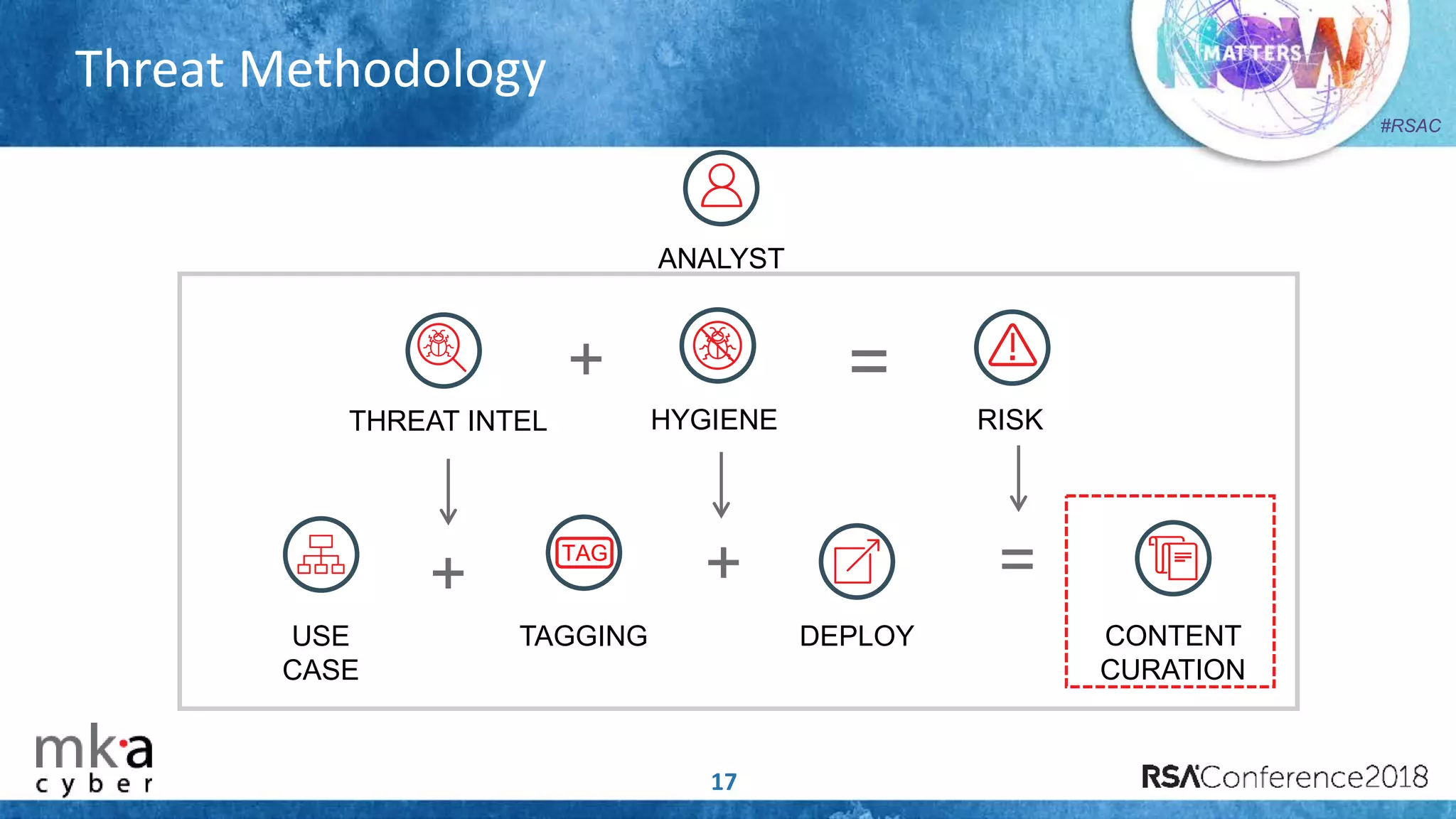
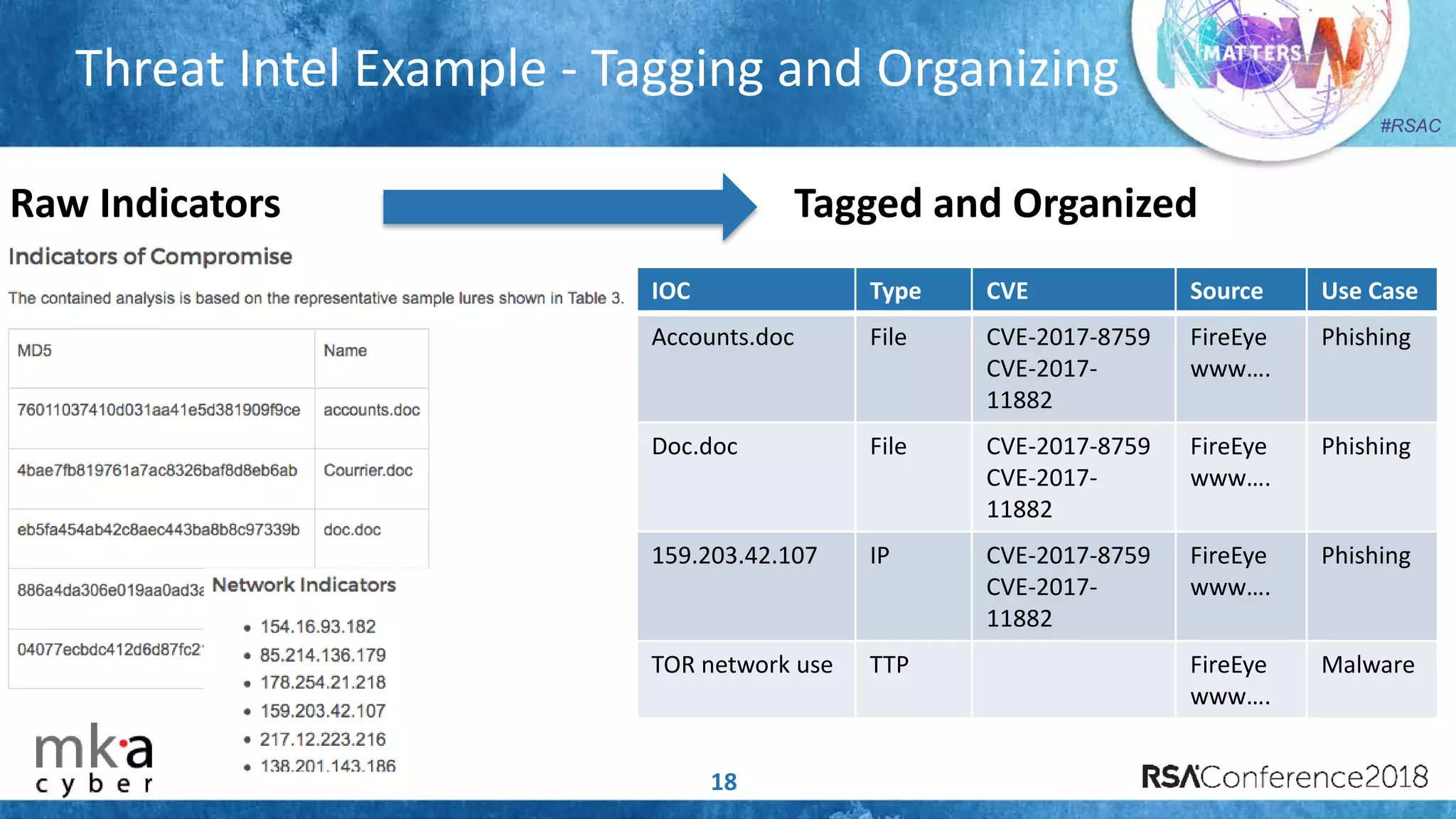
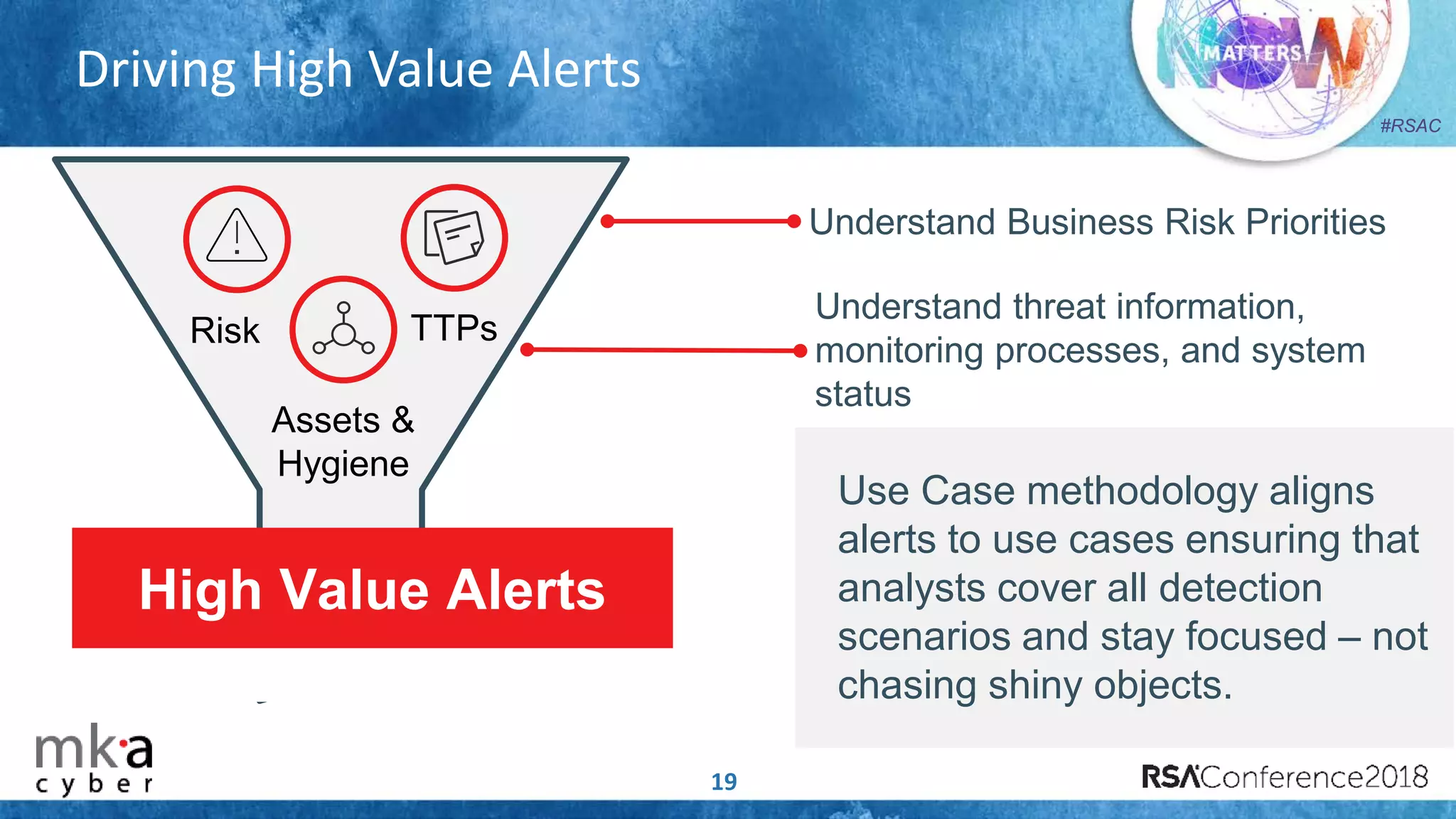
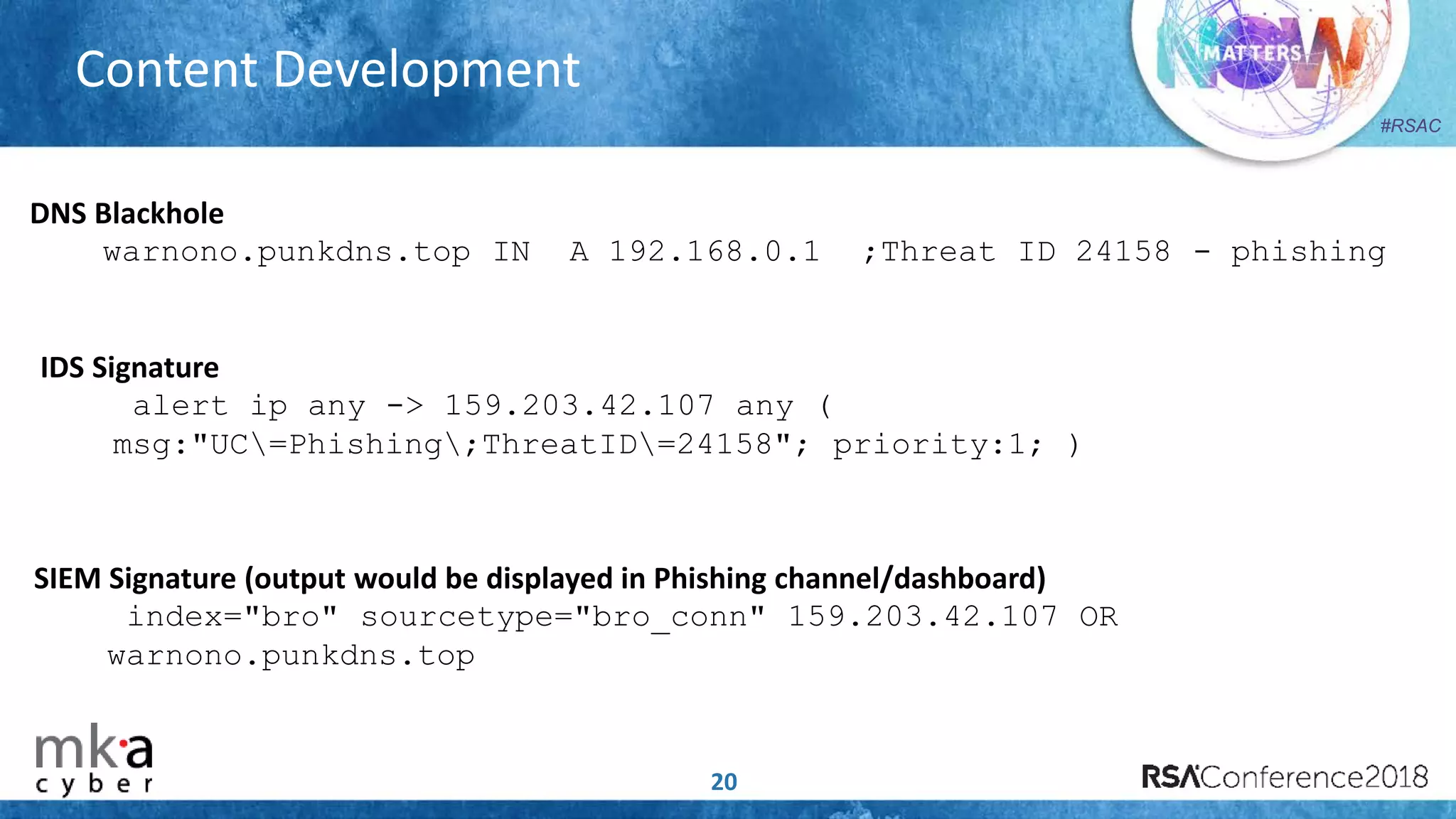
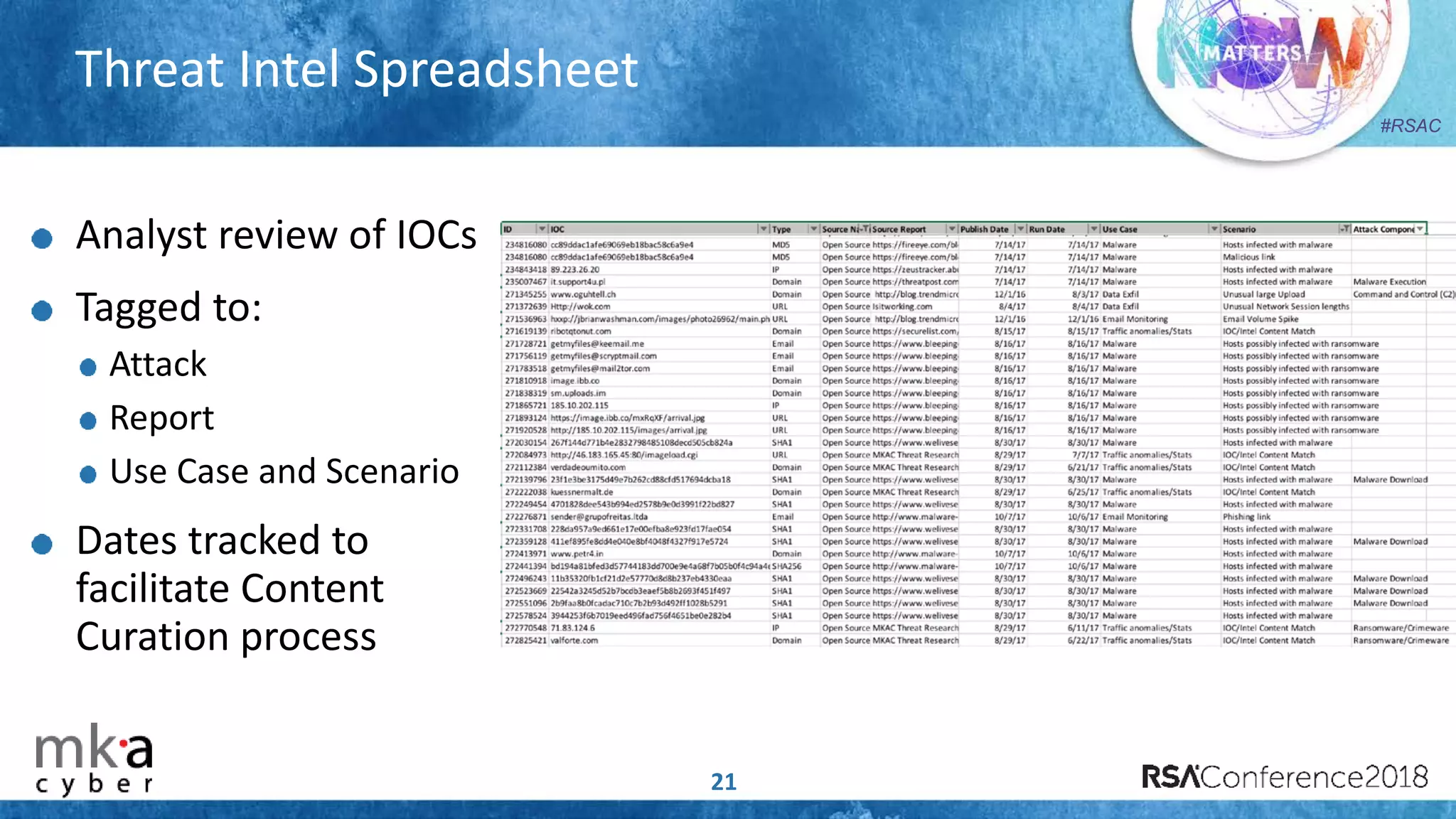
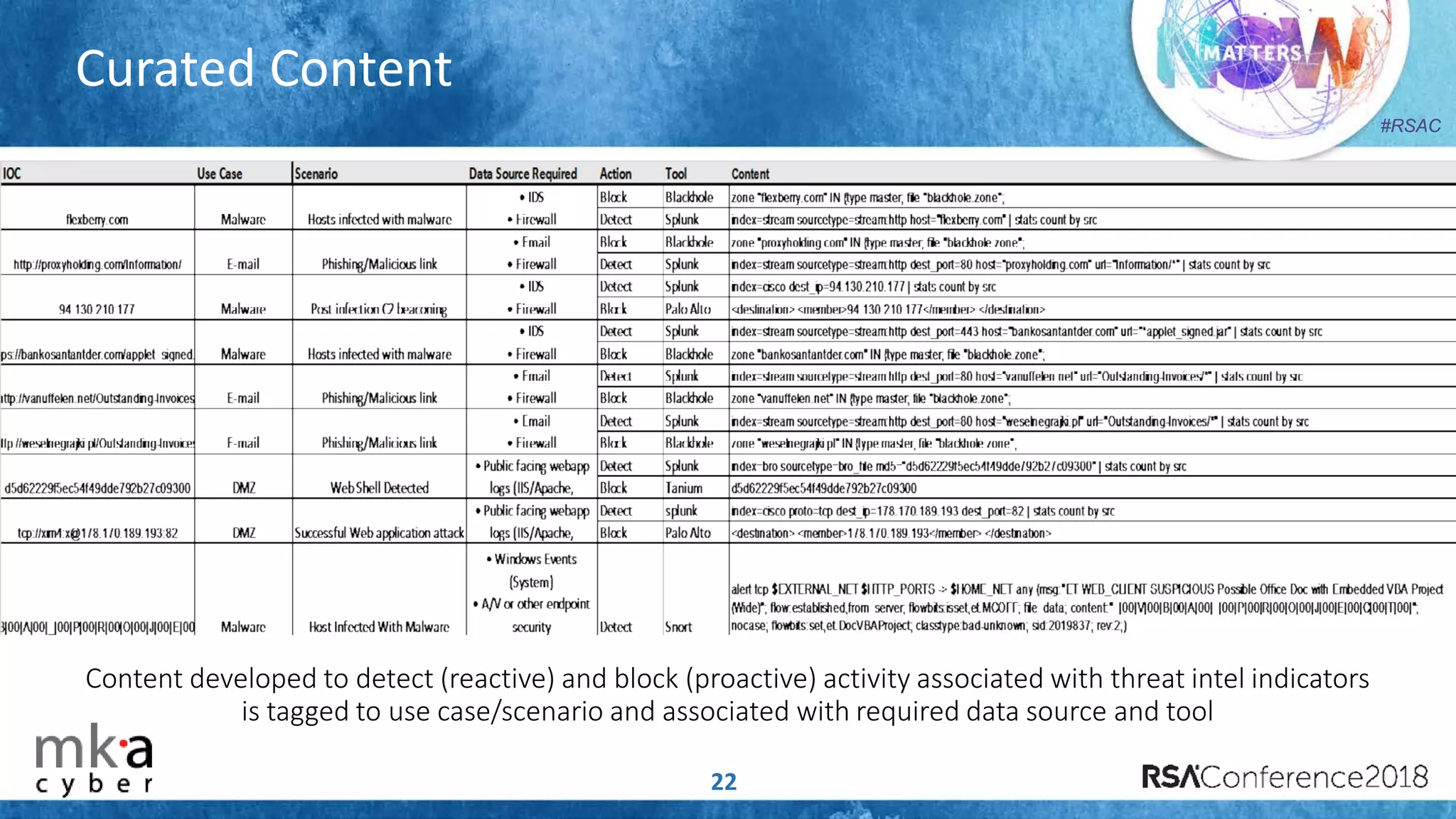
The document discusses the importance of effective cyber threat intelligence (CTI) management to enhance security operations and reduce analyst fatigue caused by excess irrelevant data. It emphasizes the necessity for organizations to align CTI with their specific use cases and business risks, ensuring that threat data is prioritized and curated for relevance. A structured approach towards threat intel, including feedback loops and continuous improvement processes, is crucial for deriving actionable insights and enhancing overall security posture.