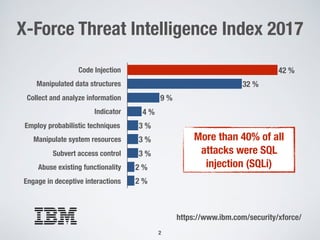
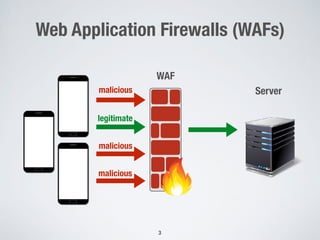
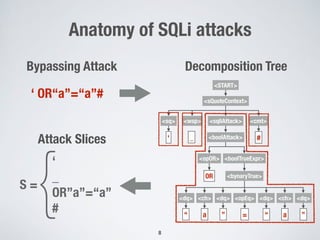
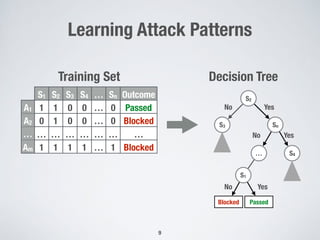
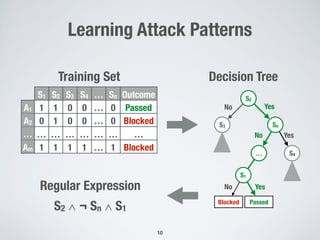
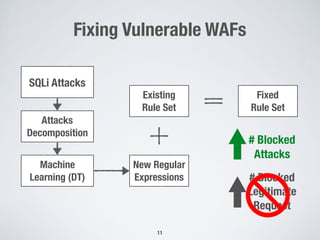
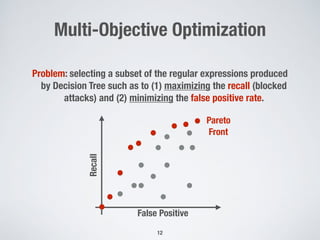
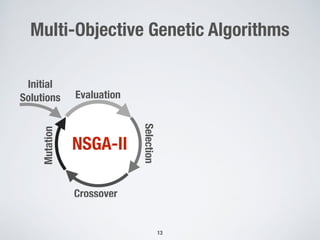
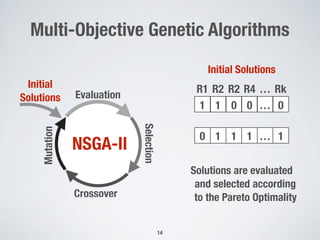
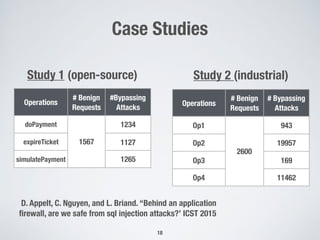
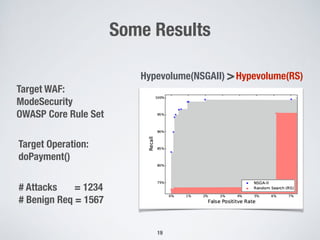
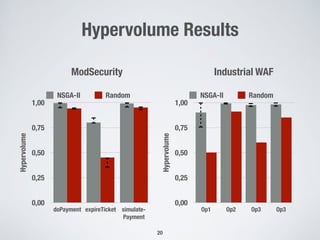
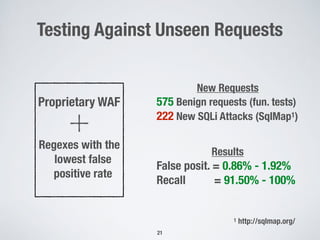
This document discusses automatically repairing web application firewalls (WAFs) based on successful SQL injection attacks. It presents an approach to learn patterns from SQLi attacks that bypass a WAF's existing rules. A decision tree is used to generate regular expressions from attack slices. A multi-objective genetic algorithm then selects a subset of regular expressions to maximize blocked attacks while minimizing false positives. An empirical evaluation on two case studies shows the approach is effective at identifying bypassing attacks with low false positive rates compared to random search.