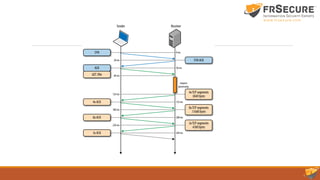
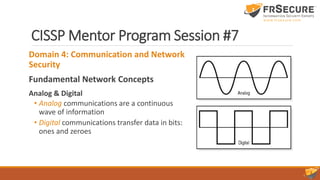
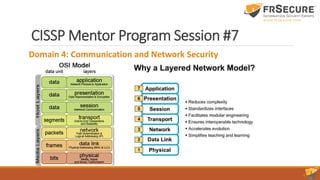
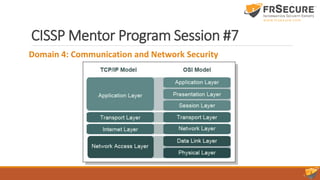
This document summarizes the seventh session of a CISSP mentor program. It reviews Domain 3 on security engineering, including perimeter defenses, site selection and configuration, and system defenses. It then provides a quiz on these topics. The session concludes with a review of Domain 4 on communication and network security, covering network architecture, secure network devices and protocols, and secure communications. Key terms are defined, such as the OSI and TCP/IP models, LANs/WANs, circuit switching vs. packet switching, and the layers of the OSI model.



























































![CISSP Mentor Program Session #7
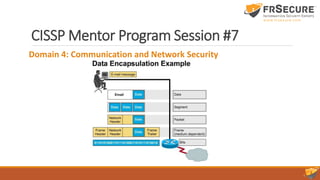
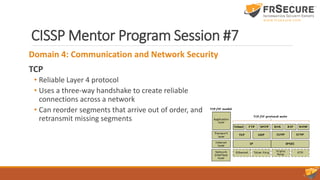
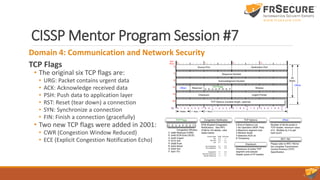
Domain 4: Communication and Network Security
The TCP/IP Model - Application Layer
• aka the Process Layer:
• Emphasis is on maximum flexibility for software developers.
• Handles all high level protocols:
• FTP, HTTP, SMTP [ TCP examples ]
• TFTP, SNMP, DHCP, DNS, BOOTP [ UDP examples ]
• Data representation, encoding and dialog control.
• Ensures data is properly packaged for the next layer.](https://image.slidesharecdn.com/slidedeckcisspclasssession7-160518020657/85/Slide-Deck-CISSP-Class-Session-7-63-320.jpg)