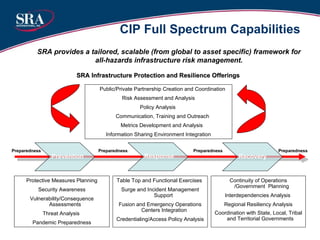
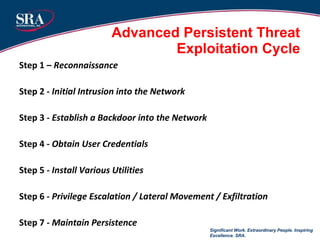
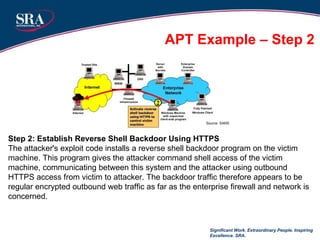
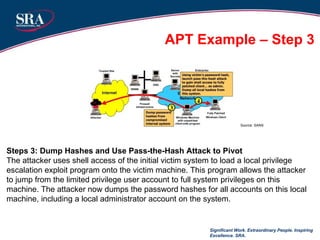
The document discusses cybersecurity threats and advanced persistent threats (APTs). It provides an overview of the evolution of cyber threats from early computer viruses and malware in the 1970s-1980s to increasingly sophisticated nation-state sponsored APTs. It describes APTs as targeted attacks aimed at data exfiltration that are advanced, persistent, and use complex techniques to maintain access and avoid detection. The document outlines the typical multi-stage exploitation cycle of APTs, from initial reconnaissance and intrusion to establishing backdoors, escalating privileges, and maintaining long-term persistence within the target network to exfiltrate data.







































![QUESTIONS? Significant Work. Extraordinary People. Inspiring Excellence. SRA. Craig Wilson Principal Infrastructure Protection and Resilience Division SRA International, Inc. [email_address]](https://image.slidesharecdn.com/craigwilson-101221033342-phpapp02/85/Craig-wilson-44-320.jpg)