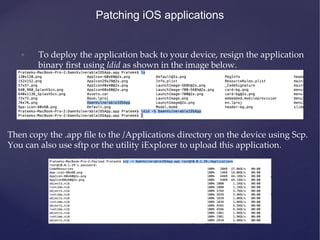
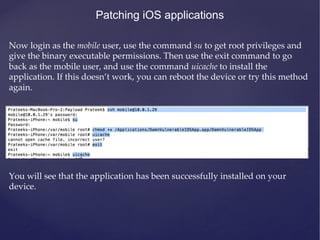
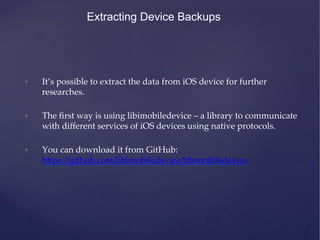
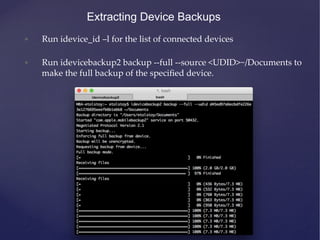
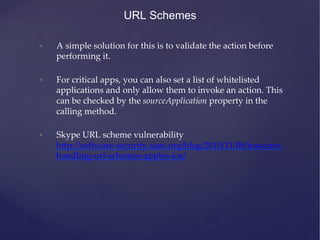
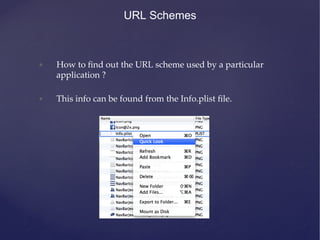
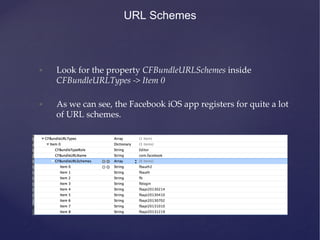
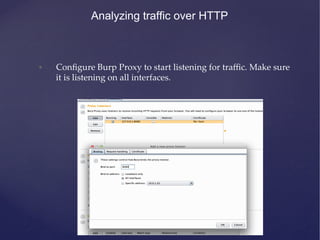
This document provides an agenda for a training on iOS application penetration testing. It covers topics such as setting up an iOS pen testing environment, understanding the iOS filesystem and Objective-C runtime, runtime analysis and manipulation, insecure data storage, analyzing network traffic, jailbreak detection, secure coding guidelines, and automated testing. Tools discussed include class-dump-z, cycript, clutch, and gdb for analyzing iOS applications.





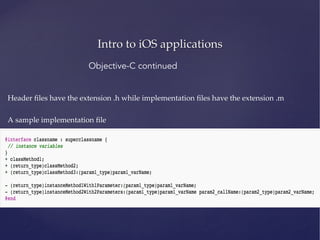
![Intro to iOS applications
Objective C continued
Instantiation
MyObject *o = [[MyObject alloc] init];
MyObject *o = [[MyObject alloc] initWithString:myString];
NSArray *myArray = [NSArray arrayWithObjects:object1,object2,object3,nil];
Calling Methods
[self doSomething];
[MainViewController performTaskWithID:[NSNumber numberWithInt:1]];](https://image.slidesharecdn.com/ios-app-security-presentation-150602200034-lva1-app6892/85/iOS-Application-Security-7-320.jpg)



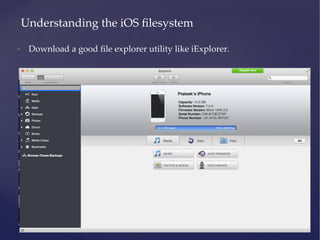


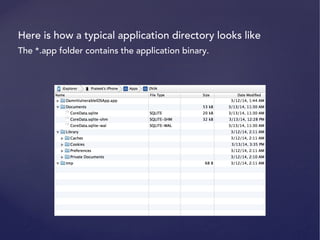
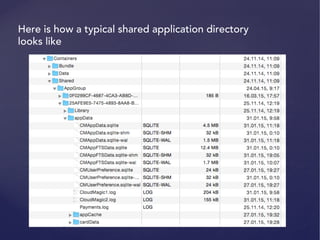

![Usage: otool -l [binaryName]](https://image.slidesharecdn.com/ios-app-security-presentation-150602200034-lva1-app6892/85/iOS-Application-Security-26-320.jpg)

![Usage: class-dump-z [binaryName]](https://image.slidesharecdn.com/ios-app-security-presentation-150602200034-lva1-app6892/85/iOS-Application-Security-28-320.jpg)
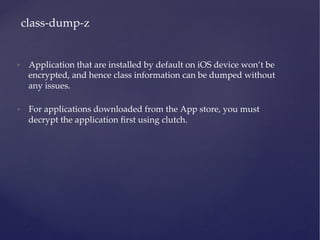
![Usage: clutch [App Name]
• Just using the clutch command will display a list of applications that can be
decrypted.
• Use “clutch [App Name]” to decrypt the application. The decrypted ipa file
will be stored in the location as shown below.](https://image.slidesharecdn.com/ios-app-security-presentation-150602200034-lva1-app6892/85/iOS-Application-Security-30-320.jpg)
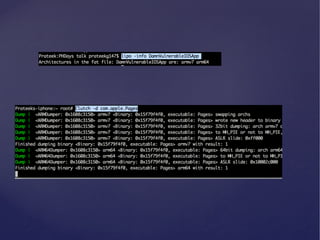
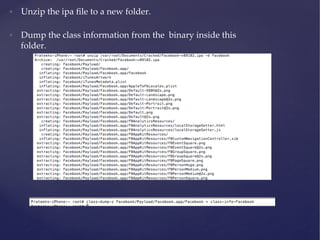

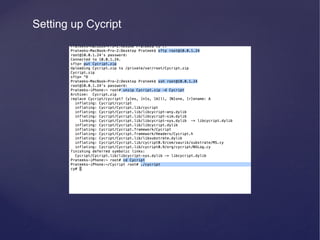
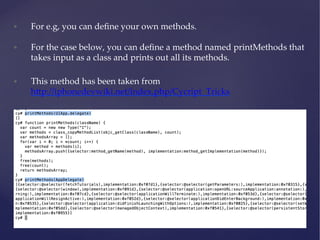
![Runtime analysis using Cycript
• You can hook into the runtime of an application by using the command
“cycript -‐‑p [PID]”
• Some cool things that you can do with Cycript can be found here
h6p://iphonedevwiki.net/index.php/Cycript_Tricks](https://image.slidesharecdn.com/ios-app-security-presentation-150602200034-lva1-app6892/85/iOS-Application-Security-35-320.jpg)
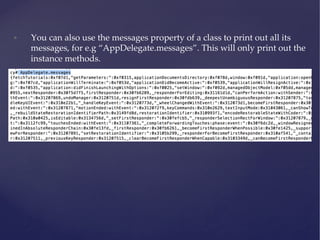


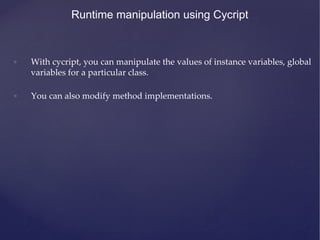
![Runtime manipulation demo
• In this case, we are manipulating the instance variable “urlToLoad” in the
view controller RuntimeManipulationDetailsVC for
DamnVulnerableiOSApp (h6p://damnvulnerableiosapp.com)
• The first step is to get a reference to the view controller.
• Once you get the reference, you can modify any of it’s variables.
• For e.g
UIApp.keyWindow.rootViewController.topViewController.topViewCont
roller.urlToLoad = [NSString stringWithFormat:@"ʺh6p://google.com"ʺ];](https://image.slidesharecdn.com/ios-app-security-presentation-150602200034-lva1-app6892/85/iOS-Application-Security-41-320.jpg)
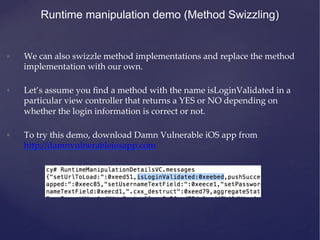
![• We can modify this method’s implementation to always return TRUE.
• As you can see, the code on the R.H.S is actually Javascript, this is the
beauty about Cycript, it can related both Objective-‐‑C and javascript
syntax.
Runtime manipulation demo (Method Swizzling)
• RuntimeManipulationDetailsVC.messages['ʹisLoginValidated'ʹ] =
function() {return TRUE;}](https://image.slidesharecdn.com/ios-app-security-presentation-150602200034-lva1-app6892/85/iOS-Application-Security-43-320.jpg)
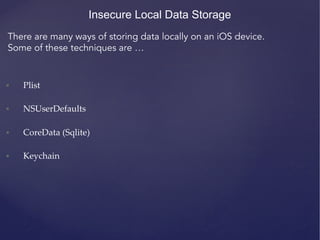


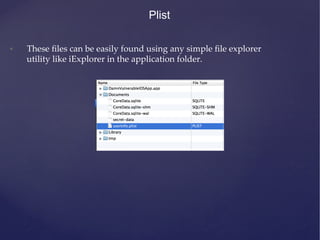
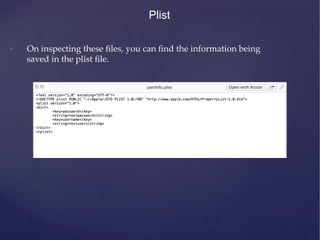

![NSUserDefaults
• Used for storing properties, objects that can persist even after an
application restart.
• Information is saved unencrypted inside the application sandbox
in a plist file with the name [BUNDLE_ID].plist inside the folder
Library -‐‑> preferences .
• Developers make a common mistake of storing critical data using
NSUserDefaults.](https://image.slidesharecdn.com/ios-app-security-presentation-150602200034-lva1-app6892/85/iOS-Application-Security-50-320.jpg)
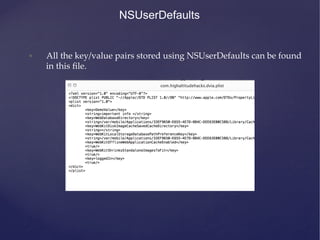
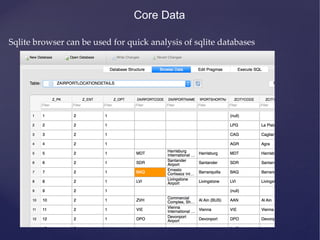
![NSUserDefaults
• All the information stored using NSUserDefaults can be found
inside the file [BUNDLE_ID].plist inside the folder Library -‐‑>
Preferences.](https://image.slidesharecdn.com/ios-app-security-presentation-150602200034-lva1-app6892/85/iOS-Application-Security-51-320.jpg)

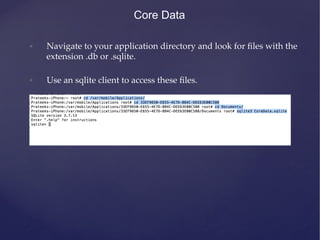


![Keychain
• One line implementation.
• Access group allows applications to share keychain data.
KeychainItemWrapper *wrapper = [[KeychainItemWrapper alloc]
initWithIdentifier:@“Identifier” accessGroup:nil];
The same access group has to be given from both the apps and both
the app ID’s have to be mentioned in the plist file for both the
applications.](https://image.slidesharecdn.com/ios-app-security-presentation-150602200034-lva1-app6892/85/iOS-Application-Security-59-320.jpg)
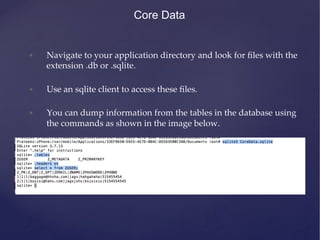
![Storing Data in Keychain
• Using Keychain is quite simple (especially with third-‐‑party
wrappers). One of them is SSKeychain (
h6ps://github.com/soffes/sskeychain):
• [SSKeychain setPassword:@”secretkey” forService:@”DVIA”
account:@”Admin”];
• NSString *pass = [SSKeychain passwordForService:@”DVIA”
account:@”Admin”];](https://image.slidesharecdn.com/ios-app-security-presentation-150602200034-lva1-app6892/85/iOS-Application-Security-60-320.jpg)







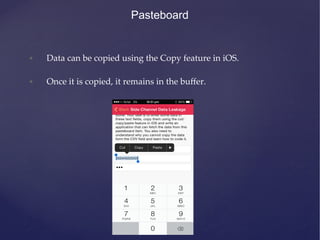
![Pasteboard
• Using the following command in Cycript or any other app can
dump out the contents of the pasteboard.
!
[UIPasteboard generalPasteboard].items[0]](https://image.slidesharecdn.com/ios-app-security-presentation-150602200034-lva1-app6892/85/iOS-Application-Security-74-320.jpg)
![Pasteboard
• For text fields that might contain secure information, make sure
the Secure property is set.
• Clear pasteboard contents when the application enters
background.
[UIPasteboard generalPasteboard].items[0]!
55544555555!
• Use pasteboard with specific identifiers, this makes it difficult for
other applications to fetch data from this pasteboard item.](https://image.slidesharecdn.com/ios-app-security-presentation-150602200034-lva1-app6892/85/iOS-Application-Security-75-320.jpg)


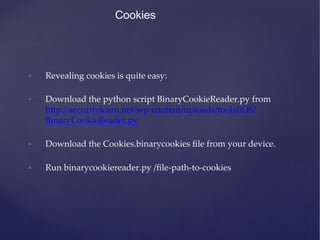
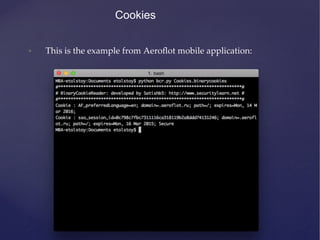
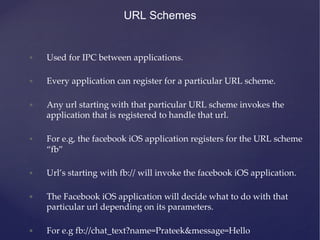
![Cookies
• Some applications create persistance cookies and store them in
cookies.binarycookies file in application’s home directory.
• The sample code for storing cookies:
• [[NSHTTPCookieStorage sharedHTTPCookieStorage]
setCookie:cookie];
• The path to cookies is: /Library/Cookies/Cookies.binarycookies
[UIPasteboard generalPasteboard].items[0]!
55544555555!](https://image.slidesharecdn.com/ios-app-security-presentation-150602200034-lva1-app6892/85/iOS-Application-Security-78-320.jpg)






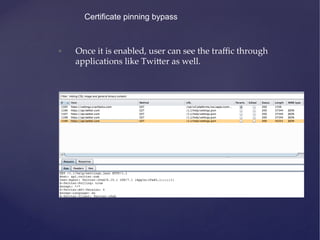


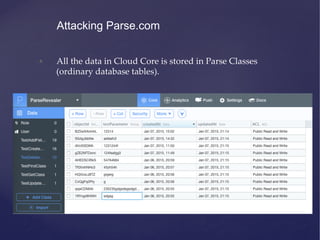
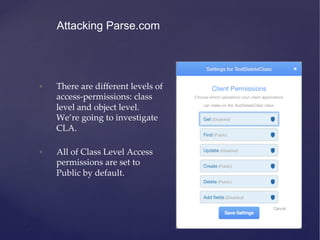
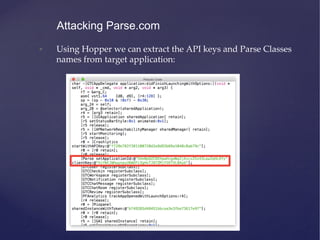
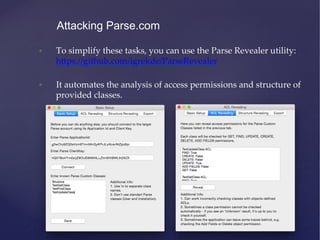
![• Now you can query the Parse API using these keys:
• [Parse setApplicationId:<APP_ID> clientKey:<CLIENT_KEY>]
• PFQuery *query = [PFQuery queryWithClassName:@”Target”];
• NSArray *data = [query findObjects];
• You can perform all the CRUD operations on class with Public
access permissions.
Attacking Parse.com](https://image.slidesharecdn.com/ios-app-security-presentation-150602200034-lva1-app6892/85/iOS-Application-Security-106-320.jpg)
![• Starting session:
[Flurry startSession:@”API_KEY”];
• Logging events:
[Flurry logEvent:@”EVENT_NAME” withParameters:params];
• Logging page views:
[Flurry logPageView];
Attacking Flurry.com](https://image.slidesharecdn.com/ios-app-security-presentation-150602200034-lva1-app6892/85/iOS-Application-Security-109-320.jpg)



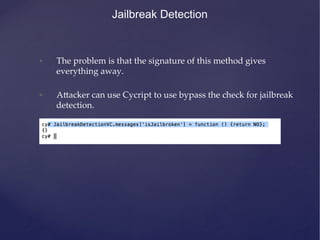
![+(BOOL)isJailbroken{
#if !(TARGET_IPHONE_SIMULATOR)
if ([[NSFileManager defaultManager] fileExistsAtPath:@"ʺ/Applications/Cydia.app"ʺ]){
return YES;
}else if([[NSFileManager defaultManager] fileExistsAtPath:@"ʺ/Library/MobileSubstrate/MobileSubstrate.dylib"ʺ]){
return YES;
}else if([[NSFileManager defaultManager] fileExistsAtPath:@"ʺ/bin/bash"ʺ]){
return YES;
}else if([[NSFileManager defaultManager] fileExistsAtPath:@"ʺ/usr/sbin/sshd"ʺ]){
return YES;
}else if([[NSFileManager defaultManager] fileExistsAtPath:@"ʺ/etc/apt"ʺ]){
return YES;
}
NSError *error;
NSString *stringToBeWri6en = @"ʺThis is a test."ʺ;
[stringToBeWri6en writeToFile:@"ʺ/private/jailbreak.txt"ʺ atomically:YES
encoding:NSUTF8StringEncoding error:&error];
if(error==nil){
//Device is jailbroken
return YES;
} else {
[[NSFileManager defaultManager] removeItemAtPath:@"ʺ/private/jailbreak.txt"ʺ error:nil];
}
if([[UIApplication sharedApplication] canOpenURL:[NSURL URLWithString:@"ʺcydia://package/com.example.package"ʺ]])
{
//Device is jailbroken
return YES;
}
#endif
//All checks have failed. Most probably, the device is not jailbroken
return NO;
}
Jailbreak Detection
Combining all these techniques, we get this method.](https://image.slidesharecdn.com/ios-app-security-presentation-150602200034-lva1-app6892/85/iOS-Application-Security-113-320.jpg)