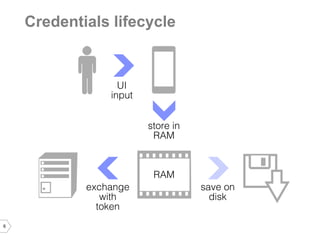
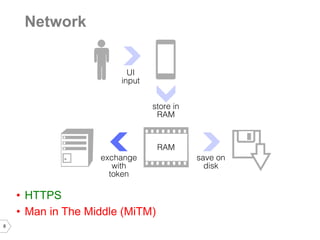
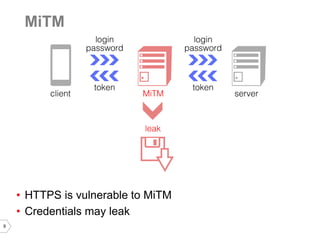
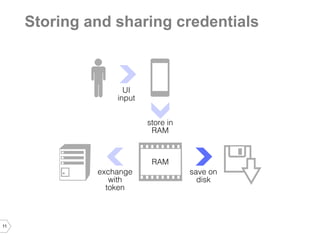
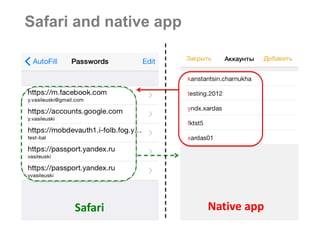
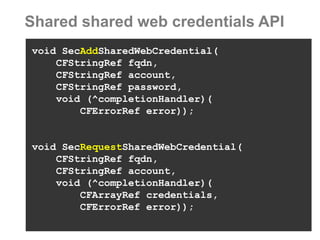
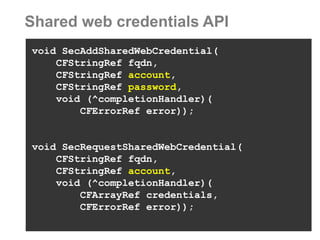
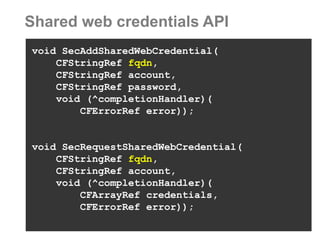
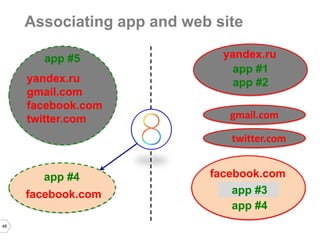
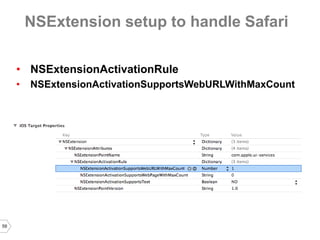
The document discusses sharing credentials between native iOS apps and Safari, highlighting methods for secure credential storage and sharing, including the use of keychains and the shared web credentials API. It addresses vulnerabilities such as man-in-the-middle attacks and outlines the importance of SSL pinning for security. Additionally, it provides insights on the differences in credential sharing capabilities between iOS 7 and iOS 8, including implementation details and user experience considerations.




































![50
•Multiple app prefixes (AppStore, AdHoc, Debug)
•Multiple bundles (AppStore, inhouse)
•Different certificates for every domain
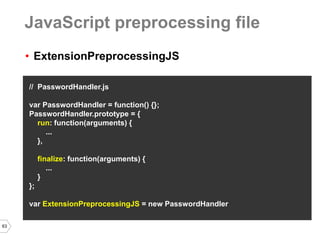
// apps.json content
{"webcredentials":{"apps":["APPSTORE_PREFIX.ru.yandex.app1", "APPSTORE_PREFIX.ru.yandex.app2"]}}
cat apps.json | openssl smime -sign –inkey certs/key.pem – signer certs/cert.pem -noattr -nodetach -outform DER > apple- app-site-association
apple-app-site-association](https://image.slidesharecdn.com/charnukhavasileuskiv2-140821121638-phpapp02/85/iOS-8-50-320.jpg)







![58
•UIActivityViewController
•NSURL
NSString *stringURL = @"https://yandex.ru";
NSURL *pageURL = [NSURL URLWithString:stringURL];
UIActivityViewController *activityVC = [[UIActivityViewController alloc]
initWithActivityItems:@[pageURL, stringURL]
applicationActivities:nil];
[mainVC presentViewController:activityVC
animated:YES
completion:nil];
Displaying activities within Safari](https://image.slidesharecdn.com/charnukhavasileuskiv2-140821121638-phpapp02/85/iOS-8-58-320.jpg)



![64
run: function(arguments) {
var loginInput = document.getElementsByName("login")[0]
var loginInputText = loginInput.value
var passwdInput = document.getElementsByName("passwd")[0]
var passwdInputText = passwdInput.value
arguments.completionFunction({
”login" : loginInputText, ”passwd" : passwdInputText})
}
finalize: function(arguments) {
var loginInput = document.getElementsByName("login")[0]
var loginInputText = arguments["login"]
loginInput.value = loginInputText;
var passwdInput = document.getElementsByName("passwd")[0]
var passwdInputText = arguments["passwd"]
passwdInput.value = passwdInputText
}
Getting values from DOM](https://image.slidesharecdn.com/charnukhavasileuskiv2-140821121638-phpapp02/85/iOS-8-64-320.jpg)
![65
run: function(arguments) {
var loginInput = document.getElementsByName("login")[0]
var loginInputText = loginInput.value
var passwdInput = document.getElementsByName("passwd")[0]
var passwdInputText = passwdInput.value
arguments.completionFunction({
”login" : loginInputText, ”passwd" : passwdInputText})
}
finalize: function(arguments) {
var loginInput = document.getElementsByName("login")[0]
var loginInputText = arguments["login"]
loginInput.value = loginInputText;
var passwdInput = document.getElementsByName("passwd")[0]
var passwdInputText = arguments["passwd"]
passwdInput.value = passwdInputText
}
Getting values from DOM](https://image.slidesharecdn.com/charnukhavasileuskiv2-140821121638-phpapp02/85/iOS-8-65-320.jpg)
![66
•NSExtensionJavaScriptFinalizeArgumentKey
•kUTTypePropertyList
NSDictionary *js =
@{NSExtensionJavaScriptFinalizeArgumentKey:
@{@"login" : self.login, @"passwd": self.passwd}};
NSItemProvider *pItem = [[NSItemProvider alloc]
initWithItem:js
typeIdentifier:(NSString *)kUTTypePropertyList];
NSExtensionItem *eItem = [[NSExtensionItem alloc] init];
eItem.attachments = @[providerItem];
[self.extensionContext
completeRequestReturningItems:@[eItem]
completionHandler:nil];
Setting values to DOM](https://image.slidesharecdn.com/charnukhavasileuskiv2-140821121638-phpapp02/85/iOS-8-66-320.jpg)



