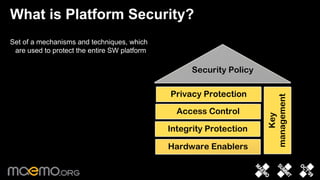
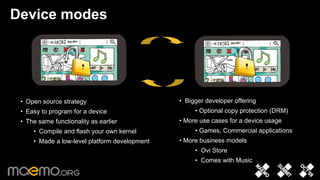
1) The document discusses platform security for the Maemo 6 operating system. It describes mechanisms like access control, hardware enablers, and integrity protection to secure the software platform.
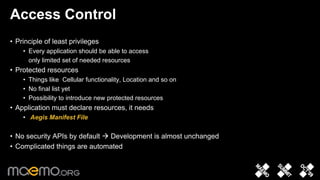
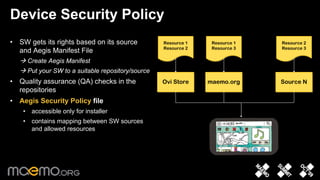
2) Access control is based on a classical Unix multi-user model extended with application-level controls. Applications must declare needed resources in a manifest file.
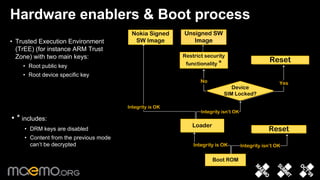
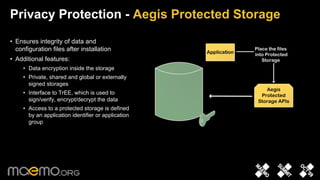
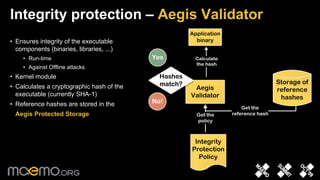
3) Integrity protection validates executables against reference hashes stored securely to prevent offline attacks.