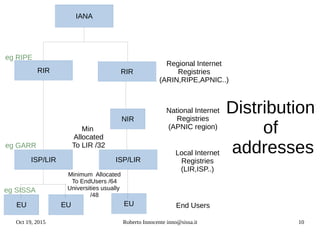
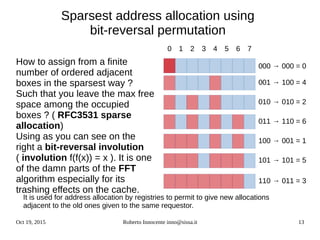
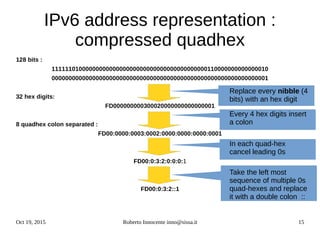
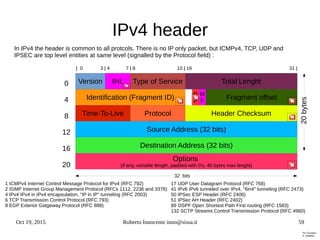
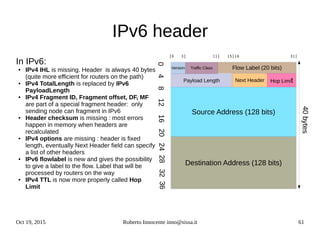
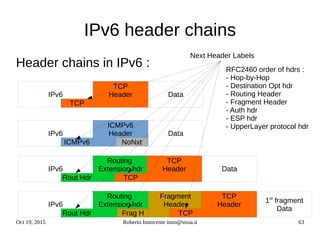
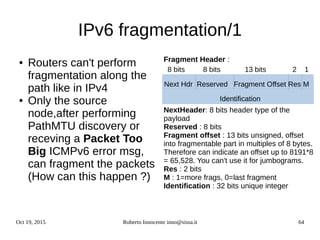
This document provides an overview of IPv6 including:
- The history and motivations for developing IPv6 due to IPv4 address exhaustion.
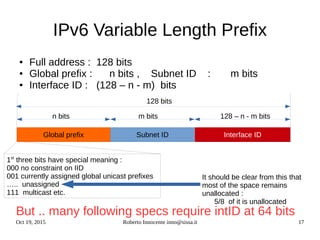
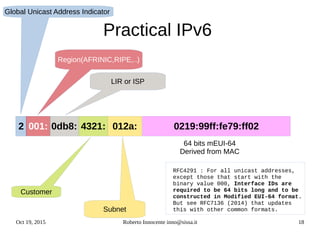
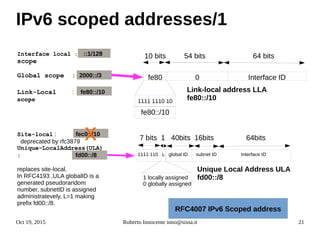
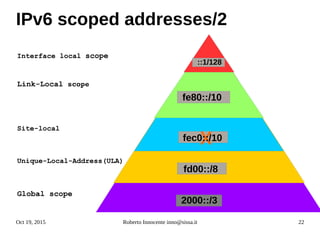
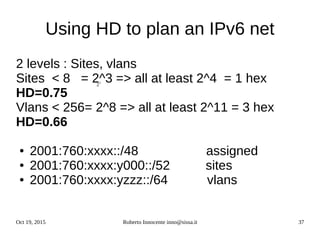
- An introduction to IPv6 addressing and prefixes.
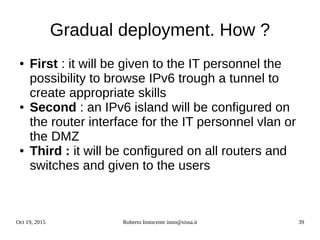
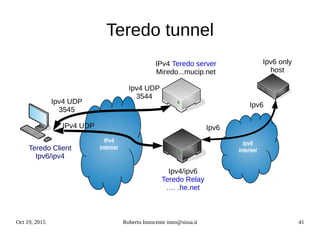
- Transition technologies like tunnels to help with gradual IPv6 deployment.
- IPv6 control protocols for tasks like neighbor discovery and routing.
- Details on how IPv6 addresses are represented textually and allocated.






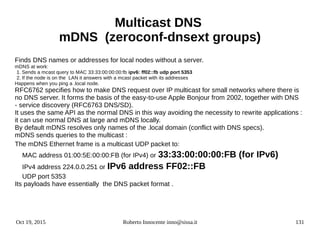
![Oct 19, 2015 Roberto Innocente inno@sissa.it 16
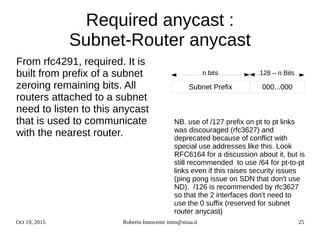
IPv6 prefix text representation
RFC4291 Text Representation of Address Prefixes
The text representation of IPv6 address prefixes is similar to the way IPv4 address prefixes are
written in Classless Inter-Domain Routing (CIDR) notation [CIDR]. An IPv6 address prefix is
represented by the notation:
ipv6-address/prefix-length
where
ipv6-address is an IPv6 address in any of the notations listed in Section 2.2.
prefix-length is a decimal value specifying how many of the leftmost contiguous bits of the
address comprise the prefix.
For example, the following are legal representations of the 60-bit prefix 20010DB80000CD3
(hexadecimal):
2001:0DB8:0000:CD30:0000:0000:0000:0000/60
2001:0DB8::CD30:0:0:0:0/60
2001:0DB8:0:CD30::/60
The following are NOT legal representations of the above prefix:
2001:0DB8:0:CD3/60 may drop leading zeros, but not trailing
zeros, within any 16-bit chunk of the address
2001:0DB8::CD30/60 address to left of "/" expands to
2001:0DB8:0000:0000:0000:0000:0000:CD30
2001:0DB8::CD3/60 address to left of "/" expands to
2001:0DB8:0000:0000:0000:0000:0000:0CD3](https://image.slidesharecdn.com/ipv6-12-18-151218114258/85/Ipv6-course-16-320.jpg)




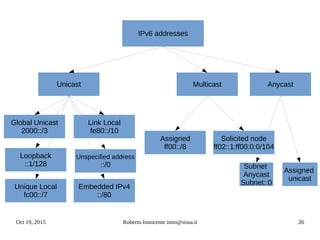

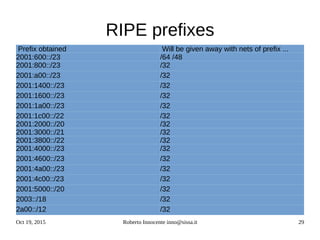




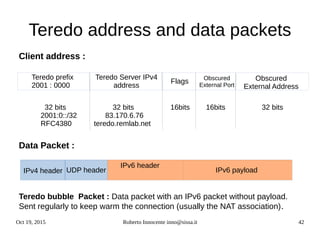
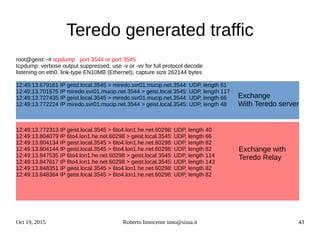


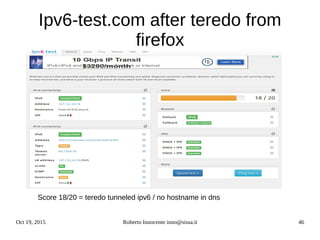
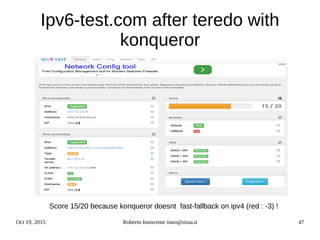
![Oct 19, 2015 Roberto Innocente inno@sissa.it 48
Ipv6 test sites
● ipv6.google.com
● ipv6-test.com
● test-ipv6.com
● [2001:200:dff:fff1:216:3eff:feb1:44d7]
(www.kame.net : turtle swimms if your reach
the site using ipv6)
● http://ip.bieringer.de/](https://image.slidesharecdn.com/ipv6-12-18-151218114258/85/Ipv6-course-48-320.jpg)




![Oct 19, 2015 Roberto Innocente inno@sissa.it 56
ssh to link local ipv6 address
inno@geist:~$ avahi-resolve -6n ghost.local
ghost.local fe80::b6b6:76ff:fe60:588c
inno@geist:~$ ssh -6 inno@fe80::b6b6:76ff:fe60:588c%eth0 #doesn't
work with .local%eth0
Welcome to Ubuntu 15.04 (GNU/Linux 3.19.3-031903-generic x86_64)
* Documentation: https://help.ubuntu.com/
Last login: Thu Sep 17 09:59:42 2015 from fe80::219:99ff:fe79:ff0%eth0
inno@ghost:~$ tail /var/log/auth.log
Sep 17 10:05:55 ghost sshd[4245]: Address fe80::219:99ff:fe79:ff0%eth0
maps to geist.local, but this does not map back to the address -
POSSIBLE BREAK-IN ATTEMPT!
Sep 17 10:05:55 ghost sshd[4245]: Accepted publickey for inno from
fe80::219:99ff:fe79:ff0%eth0 port 59205 ssh2: RSA
fe:6b:ef:53:f7:78:fe:55:5e:b8:b8:60:d1:d2:90:ab](https://image.slidesharecdn.com/ipv6-12-18-151218114258/85/Ipv6-course-56-320.jpg)

![Oct 19, 2015 Roberto Innocente inno@sissa.it 60
Header checksum,
Upper Layer Checksum
● A major decision for IPv6 was to eliminate the header checksum : it was due
to the fact that most of the errors revealed were due to the memory of
routers when this checksum is in any case recalculated and so it was not of
any help.
● UDP and TCP provide a checksum by themselves that covers not the real
header (that changes along the way [ think about the HopLimit] and would
require expensive recalculations, but a pseudo header (that doesn't change,
same strategy as IPv4) that will be checked only by the destination.
Source address
16 bytes
Destination address
16 bytes
Upper layer packet-length (4 bytes)
Zeroes (3 bytes) Next Header
0 31
IPv6
pseudo-header](https://image.slidesharecdn.com/ipv6-12-18-151218114258/85/Ipv6-course-60-320.jpg)


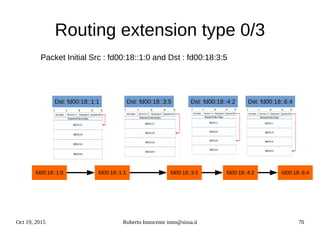

![Oct 19, 2015 Roberto Innocente inno@sissa.it 72
IPv6 on Ethernet
Max size of ethernet frames was since the beginning established in 1518 bytes.
IPv4 was encapsulated on Ethernet II using a 16 bits ether-type of 0x0800 (look at
/etc/ethertypes).
NB. IPv4 Arp uses a different ethertype of 0x0806.
IPv6 uses the 0x86dd ethertype for all its functions ICMPv6, Neighbor Discovery, Router
Discovery, …
08:44:54.554797 f0:79:59:62:02:42 (oui Unknown) > 00:19:99:79:0f:f0 (oui Unknown), ethertype IPv6 (0x86dd), length 118: (hlim 64,
nextheader ICMPv6 (58) payload length: 64) linux.local > geist.local: [icmp6 sum ok] ICMP6, echo reply, seq 1
Ethernet II header = 14 bytes + 4 bytes FrameCheckSequence = RFC894 encapsulation 18 bytes
IPv6 packets sent over Ethernet II have a maximum transmission unit of 1500 (9000 for ethernet jumbograms)
and a minimum size of 46 (to comply with the minimum ethernet frame size of 64 bytes: eventually should be
padded to 46 bytes).
Ethernet 802.3 header = 14 bytes + 8 bytes LLC/SNAP hdr + 4 bytes FCS = RFC1042 encapsulation 26 bytes
IPv6 over 802.3 Ethernet (very rare now) and LLC/SNAP encapsulation has an MTU of 1492 bytes due to the 8
bytes of the LLC/SNAP header.
IEEE 802.11 Wireless has an MTU of 2312 bytes
FDDI has an MTU of 4352 bytes
With the large diffusion of VLANs use the max size of Ethernet frames has been increased for the purpose of
including the VLAN tag (4 bytes) to 1522 bytes, Leaving the MTU to 1500 and 1492.](https://image.slidesharecdn.com/ipv6-12-18-151218114258/85/Ipv6-course-72-320.jpg)
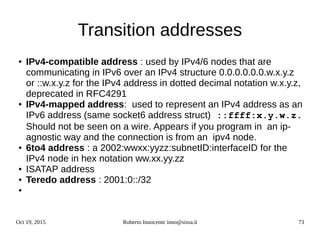

![Oct 19, 2015 Roberto Innocente inno@sissa.it 75
sockets
struct in_addr {
__be32 s_addr;
};
#define __SOCK_SIZE__ 16/*
sizeof(structsockaddr) */
struct sockaddr_in {
__kernel_sa_family_t
sin_family; /*Addressfamily*/
__be16 sin_port; /* Port number */
struct in_addr
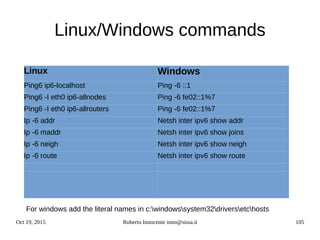
sin_addr; /*Internet
address*/
/* Pad to size of `struct
sockaddr'. */
unsigned char __pad[__SOCK_SIZE__
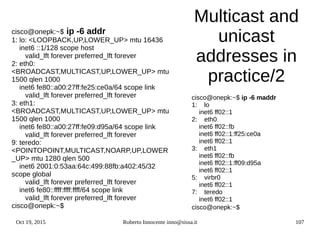
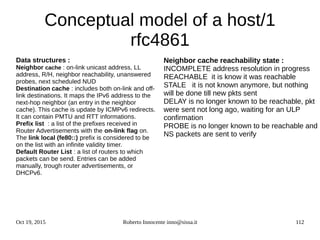
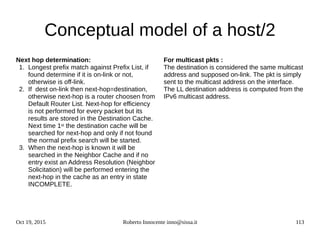
sizeof(short int)sizeof(unsigned
short int) sizeof(struct
in_addr)];
};
struct sockaddr_in6 {
sa_family_t sin6_family;
/*AF_INET6 */
in_port_t sin6_port; /*port
number*/
uint32_t sin6_flowinfo; /*IPv6
flow */
struct in6_addr
sin6_addr; /*IPv6 address*/
uint32_t sin6_scope_id; /*Scope
ID*/
};
struct in6_addr {
unsigned char s6_addr[16]; /* IPv6
address*/
};
struct addrinfo {
int ai_flags;
int ai_family;
int ai_socktype;
int ai_protocol;
socklen_t ai_addrlen;
struct sockaddr
*ai_addr;
char *ai_canonname;
struct addrinfo *ai_next;
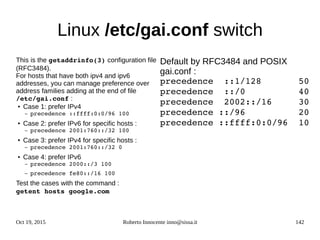
};
family
flags
*next
*addr
addrlen
type](https://image.slidesharecdn.com/ipv6-12-18-151218114258/85/Ipv6-course-75-320.jpg)
![Oct 19, 2015 Roberto Innocente inno@sissa.it 76
IPv4/IPv6 network programming/2
#include <stdio.h>
#include <string.h>
#include <sys/types.h>
#include <sys/socket.h>
#include <netinet/in.h>
#include <arpa/inet.h>
#include <netdb.h>
#define RECEIVEBUFFERLENGTH 1024
void main(int argc, char *argv[])
{
int SocketFileDescriptor;
int ReturnValue;
struct in6_addr ServerAddress;
struct addrinfo *LinkedListOfResultingAi=NULL;
char ServerName[255];
char ServerPort[] = "80";
char QueryString[] = "GET / HTTP/1.0nn";
char ReceiveBuffer[RECEIVEBUFFERLENGTH];
strcpy(ServerName, argv[1]);
ReturnValue = getaddrinfo(ServerName,
ServerPort, NULL, &LinkedListOfResultingAi);
SocketFileDescriptor = socket
(LinkedListOfResultingAi->ai_family,
LinkedListOfResultingAi->ai_socktype,
LinkedListOfResultingAi->ai_protocol);
ReturnValue = connect
(SocketFileDescriptor, LinkedListOfResultingAi-
>ai_addr, LinkedListOfResultingAi->ai_addrlen);
ReturnValue = send(SocketFileDescriptor,
QueryString, sizeof(QueryString), 0);
ReturnValue = recv(SocketFileDescriptor,
ReceiveBuffer, RECEIVEBUFFERLENGTH, 0);
printf(ReceiveBuffer,"%sn");
}
All checks and close and free removed, don't use as a pattern for real work !
getaddrinfo()
recv()
send()
connect()
socket()](https://image.slidesharecdn.com/ipv6-12-18-151218114258/85/Ipv6-course-76-320.jpg)
![Oct 19, 2015 Roberto Innocente inno@sissa.it 77
IPv4/IPv6 network programming/3
#include <stdio.h>
#include <string.h>
#include <sys/types.h>
#include <sys/socket.h>
#include <netinet/in.h>
#include <arpa/inet.h>
#include <string.h>
#define RECEIVEBUFFERLENGTH 1024
void main(int argc, char* argv[])
{
int SocketFileDescriptor;
int DescriptorOfAcceptedSocket;
int ReturnValue;
int on, ReturnValuedsize=RECEIVEBUFFERLENGTH;
char ReceiveBuffer[RECEIVEBUFFERLENGTH];
struct sockaddr_in6 ServerAddress, ClientAddress;
int AddressLength=sizeof(ClientAddress);
char IPv6Address[INET6_ADDRSTRLEN];
char* StringToSend = "HTTP/1.1 200 OKrnDate: Thu, 22
Oct 2015 08:17:45 GMTinServer: ApachenConnection:
closenContent-Type: text/htmlnn<!DOCTYPE HTML
PUBLIC "-//W3C//DTD HTML 4.0
Transitional//EN">n<html>n<head></head><body>hello !
</body></html>n";
uint16_t ServerPort;
sscanf(argv[1],"%hd",&ServerPort);
printf("Listening on port %dn",ServerPort);
SocketFileDescriptor = socket(AF_INET6, SOCK_STREAM, 0);
setsockopt(SocketFileDescriptor, SOL_SOCKET, SO_REUSEADDR,
(char *)&on,
sizeof(on));
memset((void*)&ServerAddress, 0, sizeof(ServerAddress));
ServerAddress.sin6_family = AF_INET6;
ServerAddress.sin6_port = htons(ServerPort);
ServerAddress.sin6_addr = in6addr_any;
bind(SocketFileDescriptor,(struct sockaddr *)
&ServerAddress,
sizeof(ServerAddress));
listen(SocketFileDescriptor, 10);
printf("Waiting client connectionsn");
DescriptorOfAcceptedSocket=accept(SocketFileDescriptor,
NULL, NULL);
getpeername(DescriptorOfAcceptedSocket,(struct sockaddr
*)&ClientAddress,
&AddressLength);
if(inet_ntop(AF_INET6, &ClientAddress.sin6_addr,
IPv6Address,
sizeof(IPv6Address)))
{
printf("Address client %s, port%dn",IPv6Address,
ntohs(ClientAddress.sin6_port));
}
ReturnValue = recv(DescriptorOfAcceptedSocket,
ReceiveBuffer,
sizeof(ReceiveBuffer)-1, 0);
if (ReturnValue>0) ReceiveBuffer[ReturnValue]= '0';
printf(ReceiveBuffer,"%sn");
printf("We received %d bytesn", ReturnValue);
printf("Sending %d bytesn", (int)strlen(StringToSend));
printf(StringToSend,"%sn");
ReturnValue = send(DescriptorOfAcceptedSocket, StringToSend,
(int)strlen(StringToSend),0);
}
All checks and close and free removed, don't use as a working example !
socket()
recv()
accept()
listen()
bind()
IPv4 client addr printed as ::ffff:x.y.z.w](https://image.slidesharecdn.com/ipv6-12-18-151218114258/85/Ipv6-course-77-320.jpg)




![Oct 19, 2015 Roberto Innocente inno@sissa.it 92
Questions 2
● How do you use a numeric address in an URL ?
– [2001:760:……]
● Length of IPv4 header ? Length of IPv6 header ?
– Variable 20.. , fixed 40 bytes
● Why header checksum was abandoned in IPv6 ?
– Because errors were mostly caused by bad memory in routers were header checksum is in any case recalculated
●
Is there any remnant of fragment management in the IPv6 header ?
– No, it is part of an extension header
● If in an extension header the next header field =TCP , what will be the nextheader field in the TCP header ?
– Tcp header is just the normal tcp header, it is not an ipv6 extension header and has no next header field
● Components of ICMPv6 ?
– ND neighbour discovery, RD router discovery , MLD multicast listener discovery
● Fragmentation can manage packets up to how many bytes ?
– 64 K
● What is a jumbogram in IPv6 lingo ? how many bytes in it ?
–
A packet with the jumbo payload option in an icmpv6 header, up to 232 -1 bytes
● Important flags of Router Advertisement packets ?
– Managed stateful flag, Other stateful flag . Options of prefixes : On-link prefix, Autonomous Address configuration prefix](https://image.slidesharecdn.com/ipv6-12-18-151218114258/85/Ipv6-course-92-320.jpg)









![Oct 19, 2015 Roberto Innocente inno@sissa.it 108
ndisc6
Neighbor discovery :
root@geist:~# ndisc6 hawx.local eth0
Soliciting hawx.local (fe80::219:99ff:fe7b:feab) on eth0...
Target linklayer address: 00:19:99:7B:FE:AB
from fe80::219:99ff:fe7b:feab
Trace of it :
root@geist:~# tcpdump i eth0 e ip6
tcpdump: verbose output suppressed, use v or vv for full protocol decode
listening on eth0, linktype EN10MB (Ethernet), capture size 262144 bytes
11:27:27.847150 00:19:99:79:0f:f0 (oui Unknown) > 33:33:00:00:00:fb (oui Unknown), ethertype IPv6 (0x86dd),
length 90: geist.local.mdns > ff02::fb.mdns: 0 AAAA (QM)? hawx.local. (28)
11:27:27.847541 00:19:99:7b:fe:ab (oui Unknown) > 33:33:00:00:00:fb (oui Unknown), ethertype IPv6 (0x86dd),
length 112: hawx.local.mdns > ff02::fb.mdns: 0* [0q] 1/0/0 (Cache flush) AAAA fe80::219:99ff:fe7b:feab (50)
11:27:27.848084 00:19:99:79:0f:f0 (oui Unknown) > 33:33:ff:7b:fe:ab (oui Unknown), ethertype IPv6 (0x86dd),
length 86: geist.local > ff02::1:ff7b:feab: ICMP6, neighbor solicitation, who has hawx.local, length 32
11:27:27.848337 00:19:99:7b:fe:ab (oui Unknown) > 00:19:99:79:0f:f0 (oui Unknown), ethertype IPv6 (0x86dd),
length 86: hawx.local > geist.local: ICMP6, neighbor advertisement, tgt is hawx.local, length 32
11:27:28.922283 00:19:99:79:0f:f0 (oui Unknown) > 33:33:00:00:00:fb (oui Unknown), ethertype IPv6 (0x86dd),
length 152: geist.local.mdns > ff02::fb.mdns: 0 PTR (QM)?
0.f.f.0.9.7.e.f.f.f.9.9.9.1.2.0.0.0.0.0.0.0.0.0.0.0.0.0.0.8.e.f.ip6.arpa. (90)
11:27:28.922514 00:19:99:79:0f:f0 (oui Unknown) > 33:33:00:00:00:fb (oui Unknown), ethertype IPv6 (0x86dd),
length 171: geist.local.mdns > ff02::fb.mdns: 0* [0q] 1/0/0 (Cache flush) PTR geist.local. (109)
11:27:29.023351 00:19:99:79:0f:f0 (oui Unknown) > 33:33:00:00:00:fb (oui Unknown), ethertype IPv6 (0x86dd),
length 152: geist.local.mdns > ff02::fb.mdns: 0 PTR (QM)?
b.a.e.f.b.7.e.f.f.f.9.9.9.1.2.0.0.0.0.0.0.0.0.0.0.0.0.0.0.8.e.f.ip6.arpa. (90)
11:27:29.023796 00:19:99:7b:fe:ab (oui Unknown) > 33:33:00:00:00:fb (oui Unknown), ethertype IPv6 (0x86dd),
length 170: hawx.local.mdns > ff02::fb.mdns: 0* [0q] 1/0/0 (Cache flush) PTR hawx.local. (108)
11:27:32.853122 00:19:99:7b:fe:ab (oui Unknown) > 00:19:99:79:0f:f0 (oui Unknown), ethertype IPv6 (0x86dd),
length 86: hawx.local > geist.local: ICMP6, neighbor solicitation, who has geist.local, length 32
11:27:32.853163 00:19:99:79:0f:f0 (oui Unknown) > 00:19:99:7b:fe:ab (oui Unknown), ethertype IPv6 (0x86dd),
length 78: geist.local > hawx.local: ICMP6, neighbor advertisement, tgt is geist.local, length 24
Solicited-node-multicast address](https://image.slidesharecdn.com/ipv6-12-18-151218114258/85/Ipv6-course-108-320.jpg)
![Oct 19, 2015 Roberto Innocente inno@sissa.it 109
rdisc6
Discover routers on the LAN :
root@geist:~# rdisc6 m eth0
Soliciting ff02::2 (ff02::2) on eth0...
Hop limit : 64 ( 0x40)
Stateful address conf. : No
Stateful other conf. : No
Router preference : medium
Router lifetime : 1800 (0x00000708) seconds
Reachable time : unspecified (0x00000000)
Retransmit time : unspecified (0x00000000)
Prefix : fd00:b3:18::/64
Valid time : 86400 (0x00015180) seconds
Pref. time : 14400 (0x00003840) seconds
MTU : 1280 bytes (valid)
Source linklayer address: 00:19:99:79:0F:F0
from fe80::219:99ff:fe79:ff0
Trace of it :
root@geist:~# tcpdump e i eth0 ip6
tcpdump: verbose output suppressed, use v or vv for full protocol decode
listening on eth0, linktype EN10MB (Ethernet), capture size 262144 bytes
12:57:17.164777 00:19:99:79:0f:f0 (oui Unknown) > 33:33:00:00:00:02 (oui Unknown), ethertype IPv6
(0x86dd), length 62: geist.local > ip6allrouters: ICMP6, router solicitation, length 8
12:57:17.164996 00:19:99:79:0f:f0 (oui Unknown) > 33:33:00:00:00:01 (oui Unknown), ethertype IPv6
(0x86dd), length 118: geist.local > ip6allnodes: ICMP6, router advertisement, length 64
12:57:18.247996 00:19:99:79:0f:f0 (oui Unknown) > 33:33:00:00:00:fb (oui Unknown), ethertype IPv6
(0x86dd), length 152: geist.local.mdns > ff02::fb.mdns: 0 PTR (QM)?
0.f.f.0.9.7.e.f.f.f.9.9.9.1.2.0.0.0.0.0.0.0.0.0.0.0.0.0.0.8.e.f.ip6.arpa. (90)
12:57:18.248221 00:19:99:79:0f:f0 (oui Unknown) > 33:33:00:00:00:fb (oui Unknown), ethertype IPv6
(0x86dd), length 171: geist.local.mdns > ff02::fb.mdns: 0* [0q] 1/0/0 (Cache flush) PTR
geist.local. (109)
Router Advertisement Flags :
M=0, O=0 no dhcpv6
ip6-allrouters multicast](https://image.slidesharecdn.com/ipv6-12-18-151218114258/85/Ipv6-course-109-320.jpg)
![Oct 19, 2015 Roberto Innocente inno@sissa.it 110
tracepath6
Discovers hops and Path MTU :
root@geist:~# tracepath6 b www.tudelft.nl
1?: [LOCALHOST] 0.058ms pmtu 1280
1: miredo.surfnet.nl (2001:610:168:a:145:220:0:46) 101.349ms
1: miredo.surfnet.nl (2001:610:168:a:145:220:0:46) 32.535ms
2: onweer.as1101.net (2001:610:168:a::1) 77.222ms
3: XE116.JNR01.Asd001A.surf.net (2001:610:f01:8152::153)
77.039ms
4: AE0.500.JNR01.Asd002A.surf.net (2001:610:e08:80::81)
67.500ms
5: 2001:610:f02:6096::98 (2001:610:f02:6096::98) 70.445ms
6: 2001:610:908:112:131:180:77:102
(2001:610:908:112:131:180:77:102) 34.837ms reached
Resume: pmtu 1280 hops 6 back 6](https://image.slidesharecdn.com/ipv6-12-18-151218114258/85/Ipv6-course-110-320.jpg)

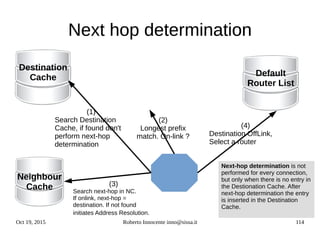
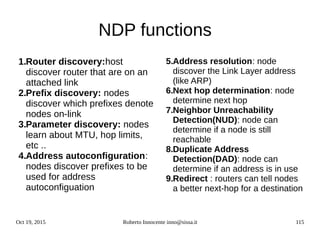
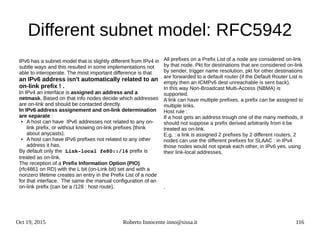
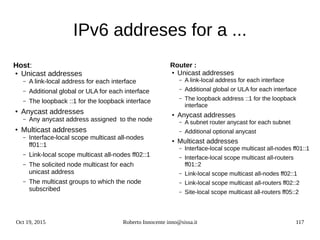




![Oct 19, 2015 Roberto Innocente inno@sissa.it 124
/etc/radvd.conf
By default radvd would read all
interface routable addresses and
would advertise their prefixes.
Anyway the behaviour can be
controlled per interface.
Therefore its configurations is made
by one or more interface definitions :
interface eth0 {
List of interface opt
List of prefix
List of clients
List of routes
List of RDNSS
List of DNSSL
};
prefix prefix/length {
List of prefix opt
};
route prefix/length {
List of route opt
};
RDNSS ip [ip] [ip] {
List of rdnss opt
};
DNSSL suffix [suffix] [suffix]{
List of dnssl opt
};
INTERFACE
OPTIONS
IgnoreIfMissing on|off
AdvSendAdvert on|off
UnicastOnly on|off
MaxRtrAdvInterval seconds
MinRtrAdvInterval seconds
MinDelayBetweenRAs seconds
AdvManagedFlag on|off
AdvOtherConfigFlag on|off
AdvLinkMTU integer
AdvReachableTime
milliseconds
AdvRetransTimer
milliseconds
AdvCurHopLimit integer
AdvDefaultLifetime seconds
AdvDefaultPreference low|
medium|high
AdvSourceLLAddress on|off
AdvHomeAgentFlag on|off
AdvHomeAgentInfo on|off
HomeAgentLifetime seconds
HomeAgentPreference integer
AdvMobRtrSupportFlag on|off
AdvIntervalOpt on|off
PREFIX OPTIONS
AdvOnLink on|off
AdvAutonomous on|off
AdvRouterAddr on|off
AdvValidLifetime seconds|infinity
AdvPreferredLifetime seconds|
infinity
DeprecatePrefix on|off
DecrementLifetimes on|off
Base6Interface name
Base6to4Interface name
ROUTE OPTIONS
AdvRouteLifetime seconds|infinity
AdvRoutePreference low|medium|
high
RemoveRoute on|off
RDNSS, DNSSL OPTIONS
AdvRDNSSLifetime seconds|infinity
FlushRDNSS on|off
AdvDNSSLLifetime seconds|
infinity;
FlushDNSSL on|off](https://image.slidesharecdn.com/ipv6-12-18-151218114258/85/Ipv6-course-124-320.jpg)
![Oct 19, 2015 Roberto Innocente inno@sissa.it 126
Ubuntu
/etc/network/interfaces
Auto method:
● privext (0
off,1=on,2=p
refer)
● accept_ra
int (0=off,
1=on,2=on+fw
d)
● dhcp int
(0=off,1=sta
teless dhcp)
Static method:
address address Address (colon
delimited/netmask) required
netmask mask Netmask (number of bits, eg 64)
gateway address Default gateway (colon
delimited), required
media type Medium type, driver dependent
hwaddress address Hardware address
mtu size MTU size
accept_ra int Accept router advertisements
(0=off, 1=on, 2=on+forwarding)
autoconf (0=off,1=on) stateless autoconf
privext int Privacy extensions (RFC3041)
(0=off, 1=assign, 2=prefer)
scope Address validity scope.
Possible values: global, site, link, host
preferredlifetime int Time that
address remains preferred
dadattempts Number of attempts
to settle DAD (0 to disable). Default
value: "60"
dadinterval DAD state polling
interval in seconds. Default value:
"0.1"
Manual method :
hwaddress address
Hardware
address
mtu sizeMTU size
Dhcp method :
hwaddress addr
accept_ra int
autoconf int
iface eth? inet6 [ auto | static | manual | dhcp ]](https://image.slidesharecdn.com/ipv6-12-18-151218114258/85/Ipv6-course-126-320.jpg)

![Oct 19, 2015 Roberto Innocente inno@sissa.it 129
Simple Service Discovery Protocol
SSDP
It is a text protocol that uses HTTPU (Http over UDP), the proposal
was described in an internet draft in 1999 that expired, it was then
used by UpnP and appears in their docs, used by windows.
Services are announced by hosts sending the announcements,
UDP port 1800 , to the following addresses:
239.255.255.250 (IPv4 site-local address)
[FF02::C] (IPv6 link-local)
[FF05::C] (IPv6 site-local)
[FF08::C] (IPv6 organization-local)
[FF0E::C] (IPv6 global)
Microsoft implements it in MediaPlayer and Server using the link-
local address, using port 2869.
IPv6 ff0x::c](https://image.slidesharecdn.com/ipv6-12-18-151218114258/85/Ipv6-course-129-320.jpg)



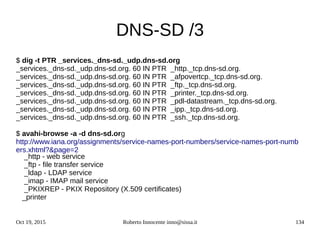
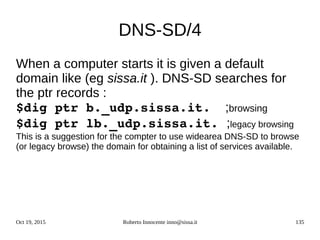

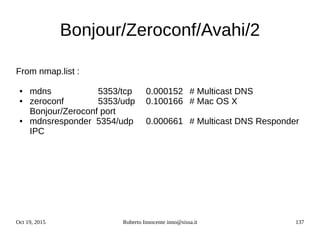



![Oct 19, 2015 Roberto Innocente inno@sissa.it 141
Linux IPv6 Name resolution
The GNU name service switch configuration /etc/nsswitch.conf decides in which order to
search for host names :
hosts: files mdns_minimal [NOTFOUND=return] dns
This line specifies to consult first the file /etc/hosts, then to consult the avahi ipv6 database
(mdns6) for .local names and, if not found, return without proceeding. Then for other (not .local)
addresses consult the internet dns.
With this configuration (getent applies exactly these rules) :
root@geist:~# getent hosts geist.local
fe80::219:99ff:fe79:ff0 geist.local
Unfortunately many applications dont use the GNU name service for host names.
The commands host and nslookup use only dns services and dont resolve .local names :
root@geist:~# host geist.local
Host geist.local not found: 3(NXDOMAIN)
root@geist:~# nslookup geist.local
Server: 2001:4860:4860::8888
Address: 2001:4860:4860::8888#53
** server can't find geist.local: NXDOMAIN](https://image.slidesharecdn.com/ipv6-12-18-151218114258/85/Ipv6-course-141-320.jpg)



![Oct 19, 2015 Roberto Innocente inno@sissa.it 146
Default ip6tables on
RedHat/CentOS/Fedora
Routing header type 0 is a threat only if the
node is forwarding packets.
Configuration is in file /etc/sysconfig/ip6tables :
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:RHFirewall1INPUT [0:0]
A INPUT j RHFirewall1INPUT
A FORWARD j RHFirewall1INPUT
A RHFirewall1INPUT i lo j ACCEPT
A RHFirewall1INPUT i eth0 j ACCEPT
A RHFirewall1INPUT i br0 j ACCEPT
A RHFirewall1INPUT p icmpv6 j ACCEPT
A RHFirewall1INPUT p 50 j ACCEPT
A RHFirewall1INPUT p 51 j ACCEPT
A RHFirewall1INPUT p udp dport 5353 d ff02::fb j
ACCEPT
A RHFirewall1INPUT p udp m udp dport 631 j ACCEPT
A RHFirewall1INPUT p tcp m tcp dport 631 j ACCEPT
A RHFirewall1INPUT p udp m udp dport 32768:61000 j
ACCEPT
A RHFirewall1INPUT p tcp m tcp dport 32768:61000 !
syn j ACCEPT
A RHFirewall1INPUT j REJECT rejectwith icmp6adm
prohibited
COMMIT
● To open ssh, insert before the last
reject :
– A RHFirewall1INPUT m tcp
p tcp dport 22 j ACCEPT
● And restart everything typing :
– sudo service ip6tables restart
● Automatic set up of a restricted fw by script :
.
.
#!/bin/bash
IPT="/sbin/ip6tables"
IF="eth0"
$IPT -F;$IPT -X;$IPT -t mangle -F;$IPT -t mangle -X
#unlimited access to loopback
$IPT -A INPUT -i lo -j ACCEPT; $IPT -A OUTPUT -o lo -j ACCEPT
# DROP all incomming traffic
$IPT -P INPUT DROP; $IPT -P OUTPUT DROP; $IPT -P FORWARD DROP
# Allow full outgoing connection but no incomming stuff
$IPT -A INPUT -i $IF -m state --state ESTABLISHED,RELATED -j ACCEPT
$IPT -A OUTPUT -o $IF -m state --state NEW,ESTABLISHED,RELATED -j ACCEPT
# allow incoming ICMP ping pong stuff
$IPT -A INPUT -i $IF -p ipv6-icmp -j ACCEPT
$IPT -A OUTPUT -o $IF -p ipv6-icmp -j ACCEPT
############# add your rules below ############
### open IPv6 port 22
$IPT -A INPUT -i $IF -p tcp --destination-port 22 -j ACCEPT
##################
# log everything else
$IPT -A INPUT -i $IF -j LOG; $IPT -A INPUT -i $IF -j DROP](https://image.slidesharecdn.com/ipv6-12-18-151218114258/85/Ipv6-course-146-320.jpg)
![Oct 19, 2015 Roberto Innocente inno@sissa.it 147
ip6tables by butler
ufw (Uncomplicated Firewall)
It manages at the same time (by default)
ipv4 and ipv6 filters using iptables and
ip6tables. We say it is ip-agnostic
because the rules apply to both stacks.
● sudo aptget install ufw
Be sure in /etc/default/ufw
there is a line : IPV6=yes.
Do the following :
ufw status
ufw default deny
ufw logging on
ufw allow 22/tcp
ufw enable
ufw status
This will configure the ip[6]tables firewall to (for
both ipv4 and ipv6) :
● Block any incoming connection except ssh
● Let go all outgoing connections
It will insert automatically for ipv6 proper defaults
that :
● Will drop pkts with routing header RH0 on all
chains
● Will drop NDP pkts with hop limit less than 255
● If the pkt belongs to an established connection
pass it on
● Accept echo replies from link local addresses
● Accept some safe icmp pkts
● Allow dhcp
● Allow mDNS
● Drop pkts not belonging to an established
connection
There is a graphical interface too : aptget install gufw
Status: active
To Action From
-- ------ ----
22/tcp ALLOW Anywhere
22/tcp (v6) ALLOW Anywhere (v6)](https://image.slidesharecdn.com/ipv6-12-18-151218114258/85/Ipv6-course-147-320.jpg)












![Oct 19, 2015 Roberto Innocente inno@sissa.it 166
ipv6calc
ipv6calc mac_to_eui64 00:19:99:79:0f:f0
No action type specified,try autodetection...found
type: geneui64
219:99ff:fe79:ff0
ipv6calc q i
2001:0:53aa:64c:109d:f226:6c85:e7b5
Address type: unicast, globalunicast, productive,
teredo
Country Code: IT
Error getting AS number from IPv6 address
Registry for address: reserved(RFC4380#6)
IPv4 address: 147.122.24.74 (TEREDOCLIENT)
IPv4 address type: unicast, global
Country Code: IT
IPv4 registry[147.122.24.74]: RIPENCC
GeoIP country name and code for [147.122.24.74]: Italy
(IT)
IPv4 address: 83.170.6.76 (TEREDOSERVER)
IPv4 address type: unicast, global
Country Code: A2
IPv4 registry[83.170.6.76]: RIPENCC
GeoIP country name and code for [83.170.6.76]:
Satellite Provider (A2)
Address type is Teredo and included IPv4 server address
is: 83.170.6.76 and client port: 3545
IPv4 registry for Teredo server address: RIPENCC
ipv6calc q out revnibbles.arpa
2001:0:53aa:64c:109d:f226:6c85:e7b5
5.b.7.e.5.8.c.6.6.2.2.f.d.9.0.1.c.4.
6.0.a.a.3.5.0.0.0.0.1.0.0.2.ip6.arpa
.](https://image.slidesharecdn.com/ipv6-12-18-151218114258/85/Ipv6-course-166-320.jpg)



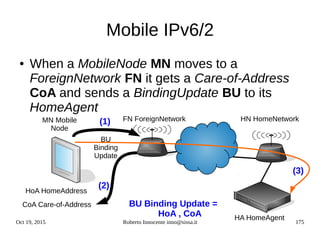
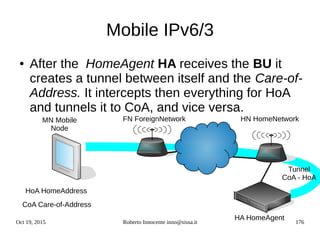


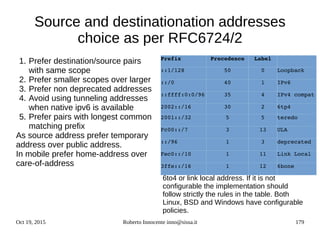



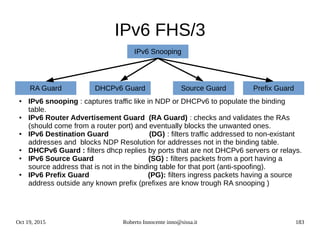
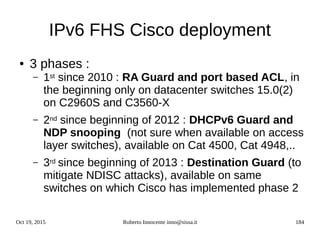

![Oct 19, 2015 Roberto Innocente inno@sissa.it 186
IPv6 Alcatel-Lucent snooping
Alcatel AOS >6.7.1R01 :
● ipv6 helper dhcp-snooping enable
- Globally enables dhcpv6 snooping and dhcpv6 pkts are filtered
● ipv6 helper dhcp-snooping vlan
● Ipv6 helper dhcp-snooping port 1/24 [ trusted | block | client-only-untrusted |client-
only-trusted]
● ipv6 helper dhcp-snooping linkagg number [ trusted | block | client-only-untrusted |
client-only-trusted]
● ipv6 helper dhcp-snooping binding enable
- The binding table contains the linklocal address, ipv6 address, vlan, interface info
● ipv6 helper dhcp-snooping ip-source-filter port 1/64 enable](https://image.slidesharecdn.com/ipv6-12-18-151218114258/85/Ipv6-course-186-320.jpg)
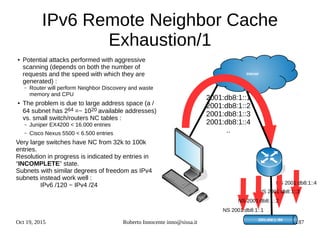
![Oct 19, 2015 Roberto Innocente inno@sissa.it 189
IPv6 Remote Neighbor Cache
Exhaustion- Remedies/3
Linux ( > 3. ) :
● Garbage collection over Neighbor Table or Cache :
– if entries are < gc_thresh1 (default = 128) it exits doing nothing
– If entries are > gc_thresh1 (default = 128), entries are cleaned and the process is repeated every gc_interval seconds
– If entries are > gc_thresh2 (default = 512) for more than 5 seconds then the gc is run (independently from gc_interval)
– If entries = gc_thresh3 (default = 1024) : gc runs continuously
To see the GC at work list all NUD (Network Unreachability Detection) entries and count them :
● ip 6 neigh show nud all | wc
● ip 6 ntable
You can change these defaults, trying to keep them scaled as they are :
gc_thresh3 = 2 * gc_thresh2 = 4 * gc_thresh1
● ip 6 ntable change name name [dev DEV] parms
With which we can change thresh1, thresh2, thresh3, gc_interval, … most of the kernel parameters related to
NDISC.
If you use the system as a router better values are :
● gc_interval = 3600 ms
● gc_stale_time = 3600 ms
● gc_thresh1 = 1024, gc_thresh2 = 2048, gc_thresh3 = 4096](https://image.slidesharecdn.com/ipv6-12-18-151218114258/85/Ipv6-course-189-320.jpg)
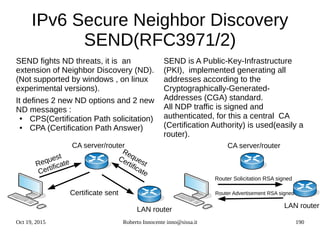
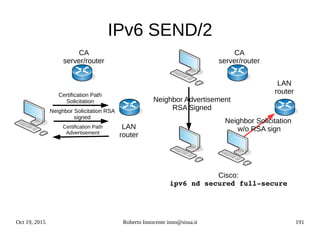
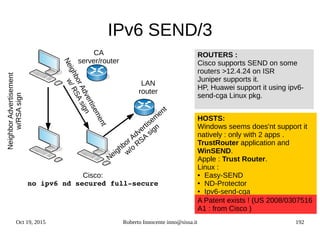
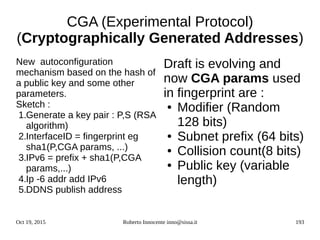
![Oct 19, 2015 Roberto Innocente inno@sissa.it 194
Configuring SEND (Secure ND)
Cisco :
● crypto key generate rsa label key-label on
devicename:
● ipv6 cga modifier rsakeypair key-label
sec-label 1
● crypto pki trustpoint name
● enrollment url url [pem]
● revocation-check
● exit
● crypto pki authenticate name
● ipv6 nd secured sec-level value
● interface gi0/0
● ipv6 cga rsakeypair key-label
● ipv6 address address/prefix-len link-
local cga
● ipv6 nd secured timestamp
● exit
● ipv6 nd secured full-secure
Juniper :
Generate RSA key pair:
● request security pki generate key-
pair type rsa certificate-id certificate-
id-name size size
● set protocols neighbor-discovery
secure security-level secure-
messages-only
● set protocols neighbor-discovery
secure cryptographic-address key-
length 1024
● set protocols neighbor-discovery
secure cryptographic-address key-
pair /var/etc/rsa_key
● set protocols neighbor-discovery
secure timestamp](https://image.slidesharecdn.com/ipv6-12-18-151218114258/85/Ipv6-course-194-320.jpg)