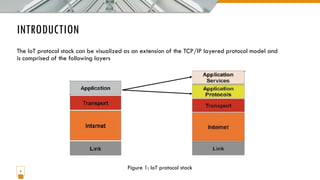
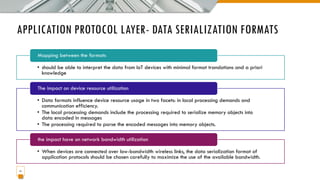
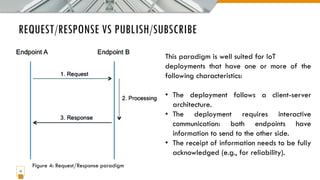
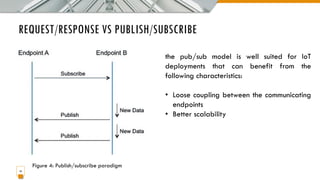
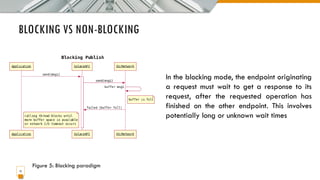
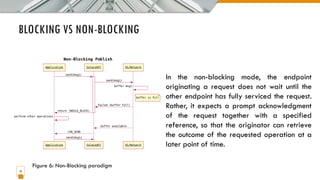
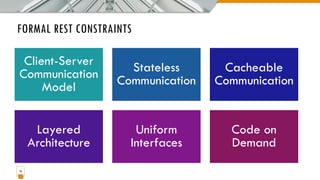
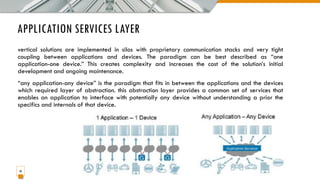
This document provides an overview of the IoT protocol stack, which extends the traditional TCP/IP layered model. It describes challenges at each layer, including link layer challenges related to device characteristics, traffic patterns, access methods, and scalability. Challenges at the internet layer for low-power lossy networks include resource constraints, energy optimization needs, traffic patterns, frame sizes, and unreliable connections. The application protocol layer must support data serialization formats, communication paradigms like request/response and publish/subscribe, and blocking versus non-blocking interactions. REST constraints for some application protocols are also outlined.