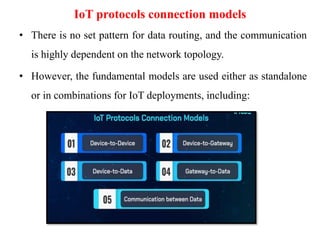
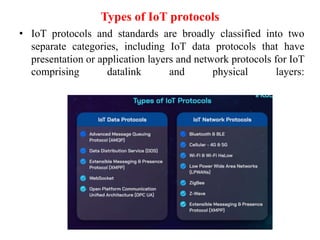
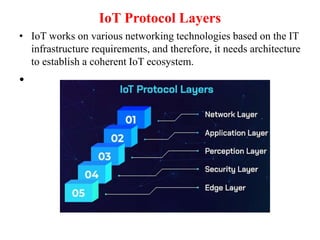
This document discusses IoT protocols for data communication and connection models. It describes the key pillars of IoT protocols as being device, connectivity, data, and analytics. It also outlines various types of IoT data protocols like AMQP, DDS, XMPP, and WebSocket that establish end-to-end communication. Additionally, it covers IoT network protocols like Bluetooth, LPWANs, ZigBee, Z-Wave and others that facilitate secured communication between IoT devices over the internet.