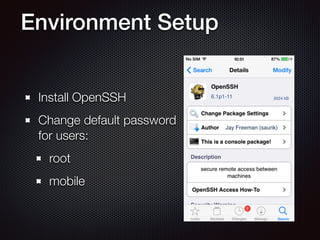
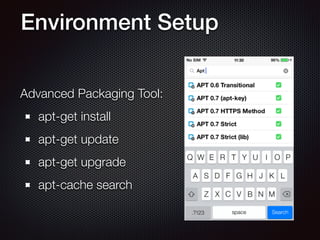
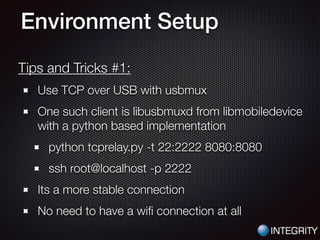
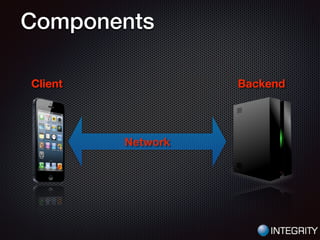
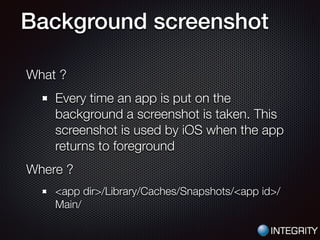
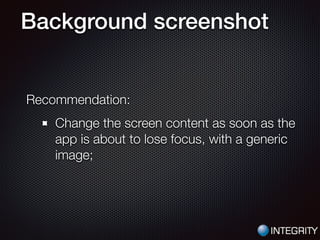
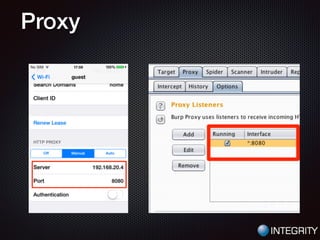
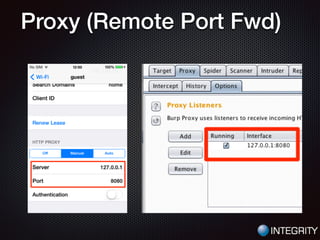
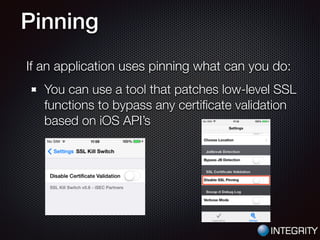
This document provides an overview of pentesting iOS apps. It discusses setting up an environment for analysis, including installing tools. It then covers static analysis techniques like inspecting app binaries and local data storage. Dynamic analysis techniques are also covered, like monitoring API calls, the filesystem, and network traffic. The document provides tips on bypassing protections like certificate pinning and resources for further learning.