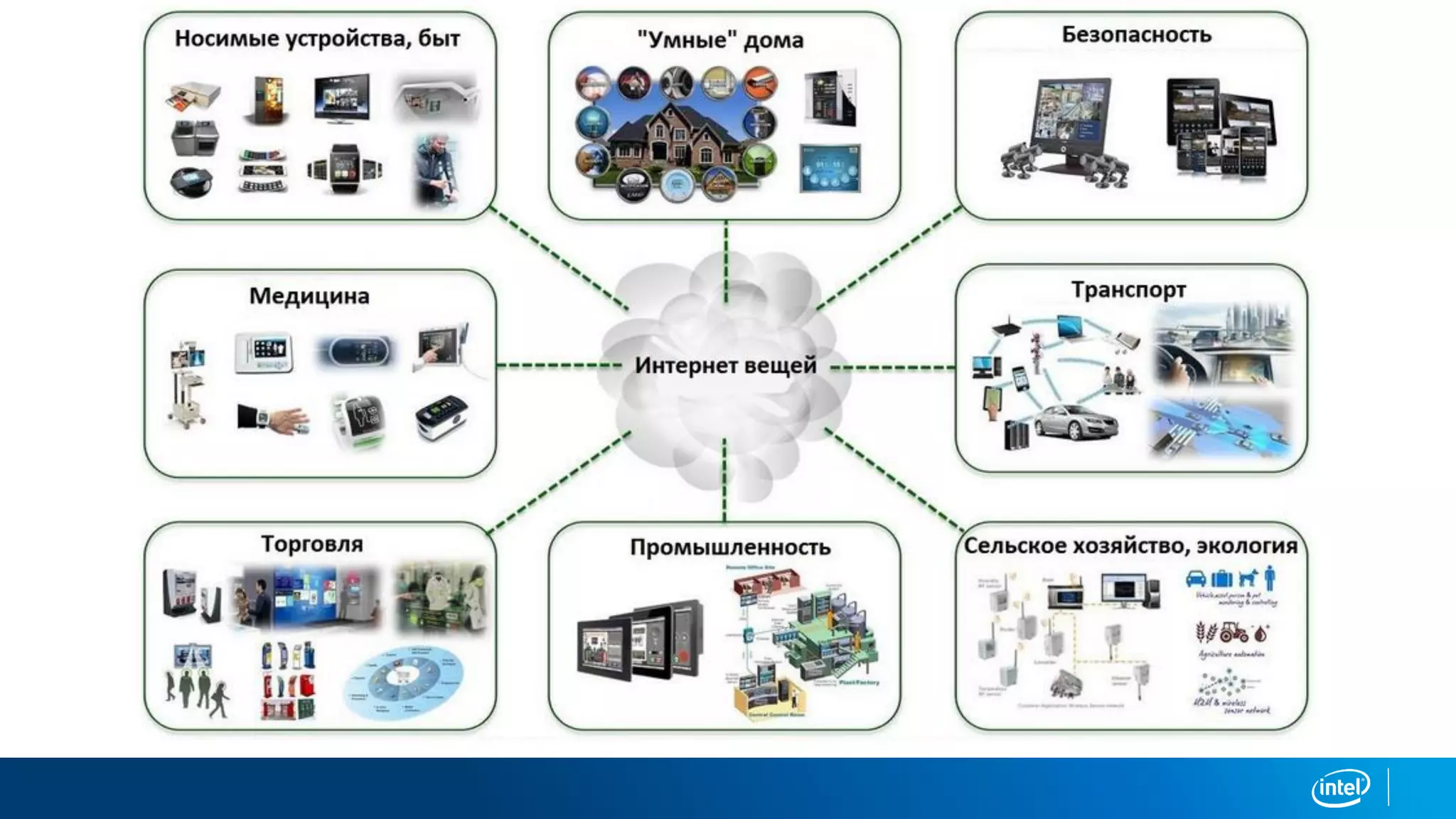
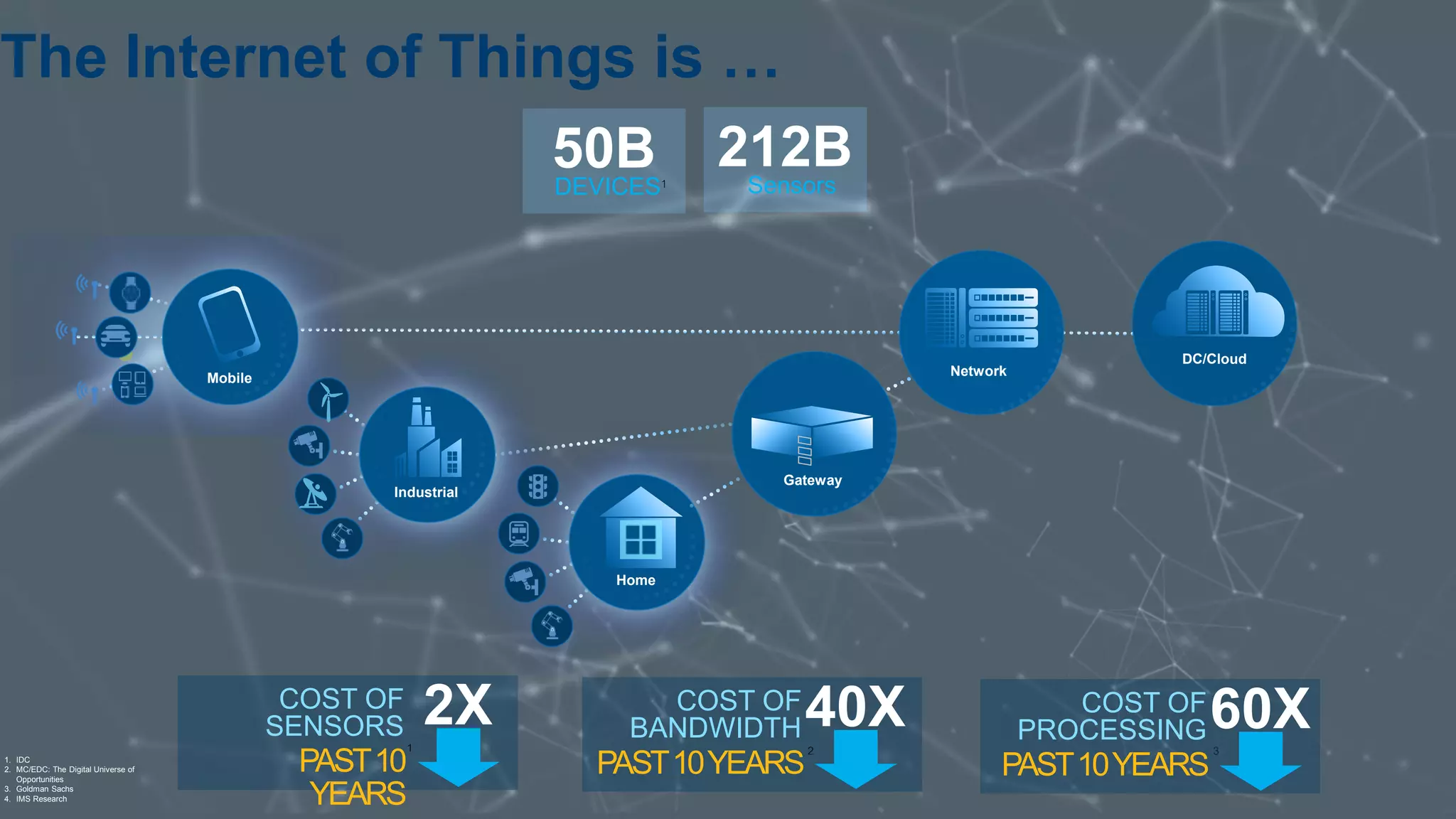
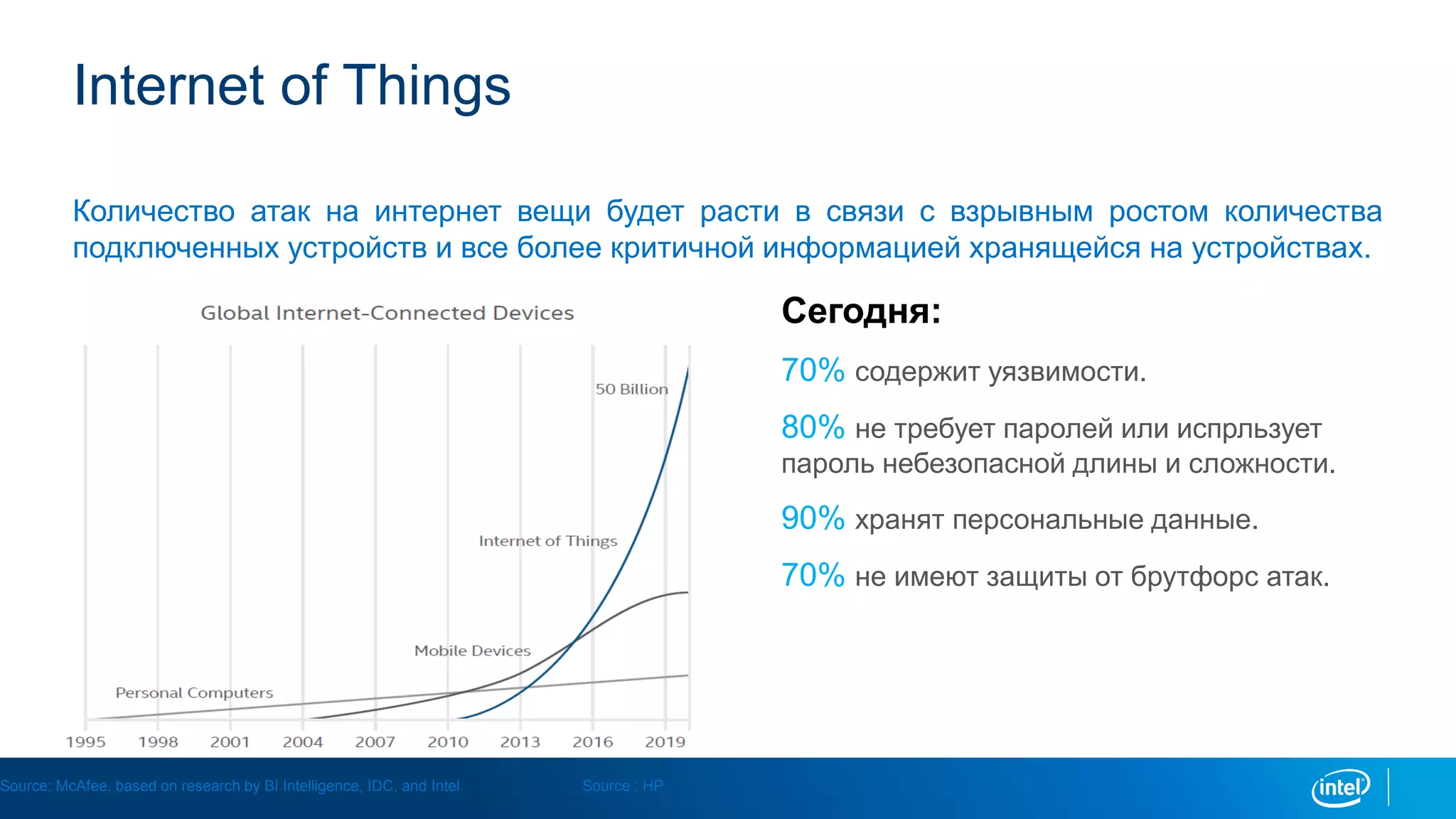
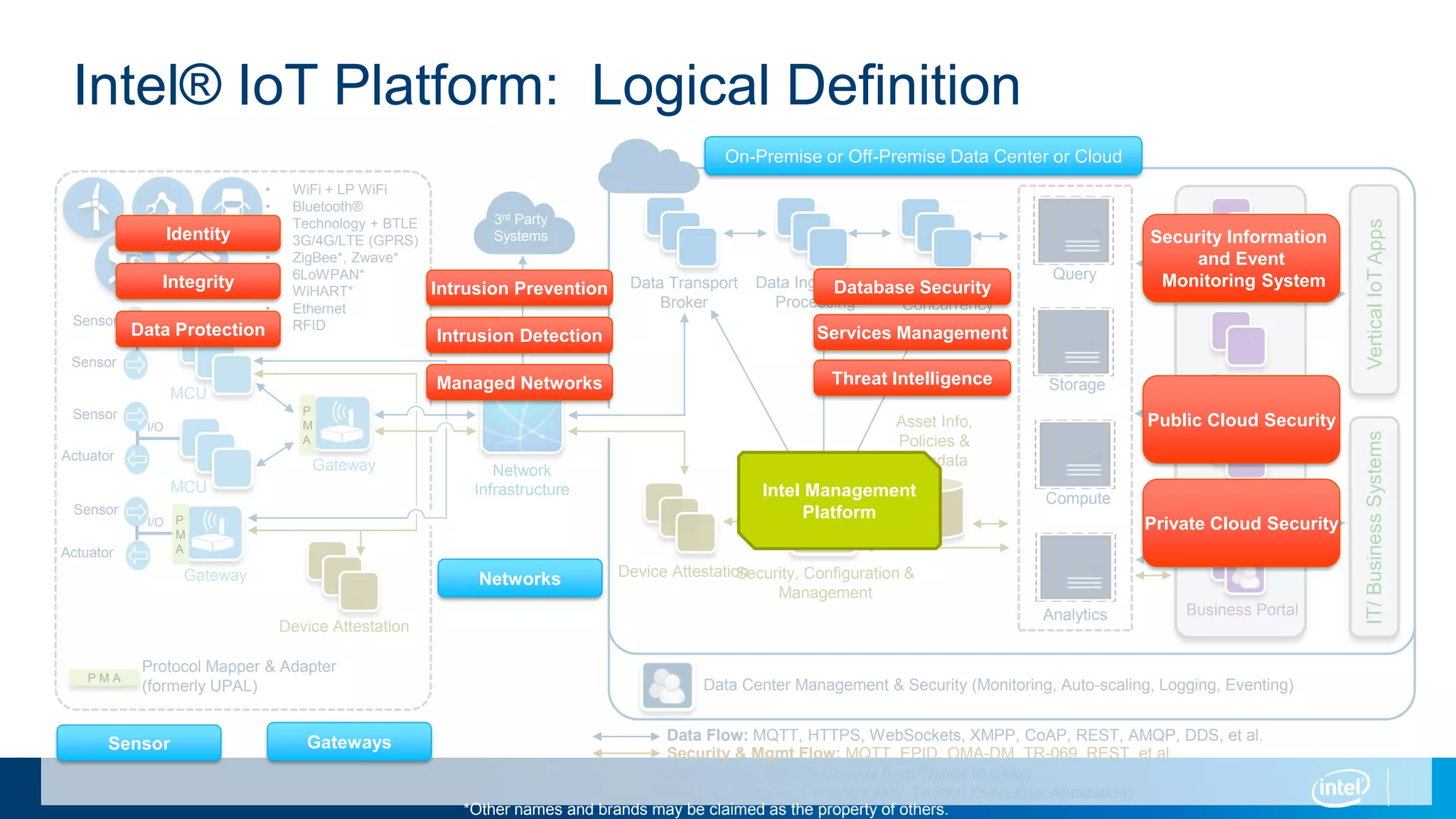
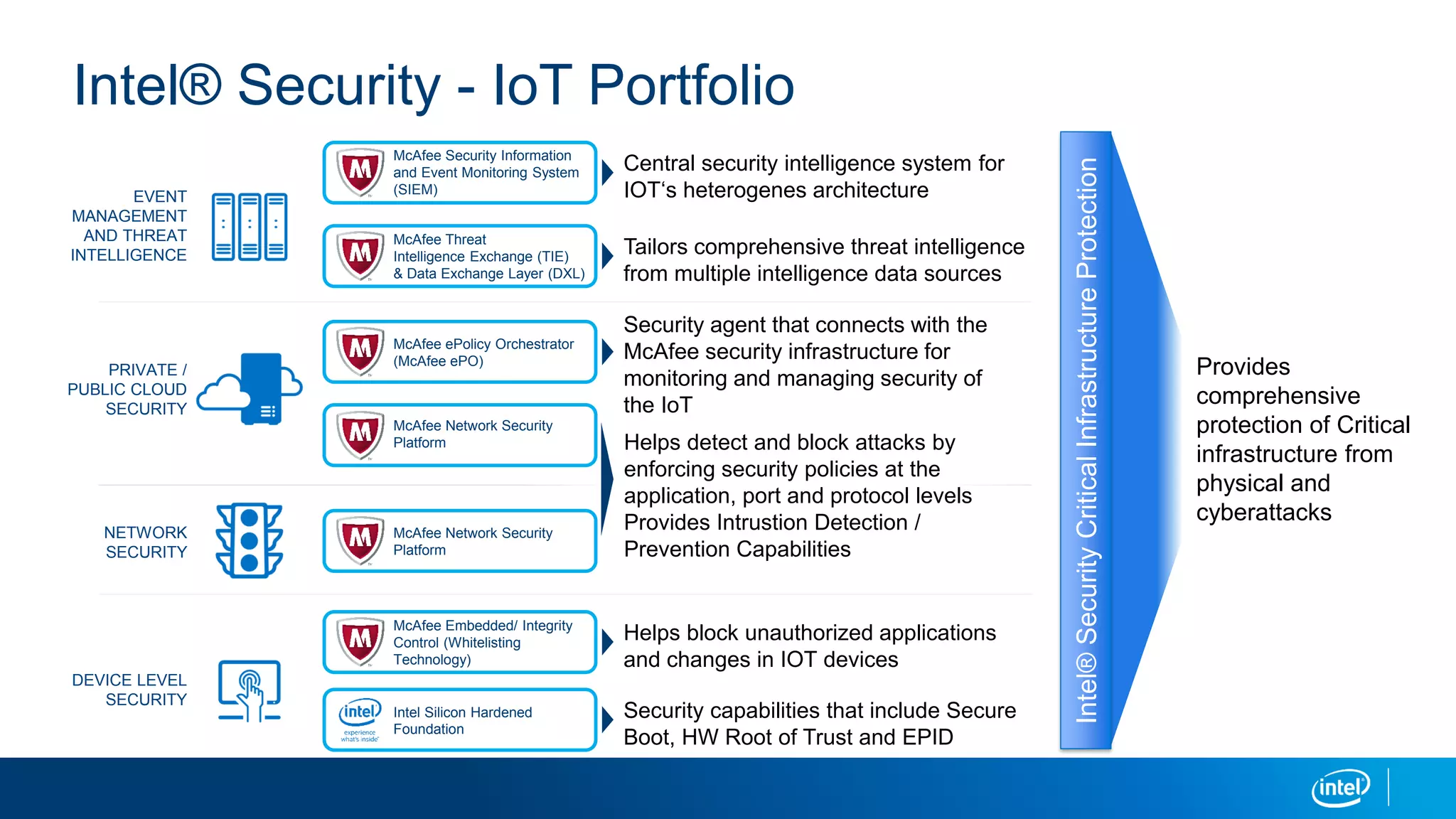
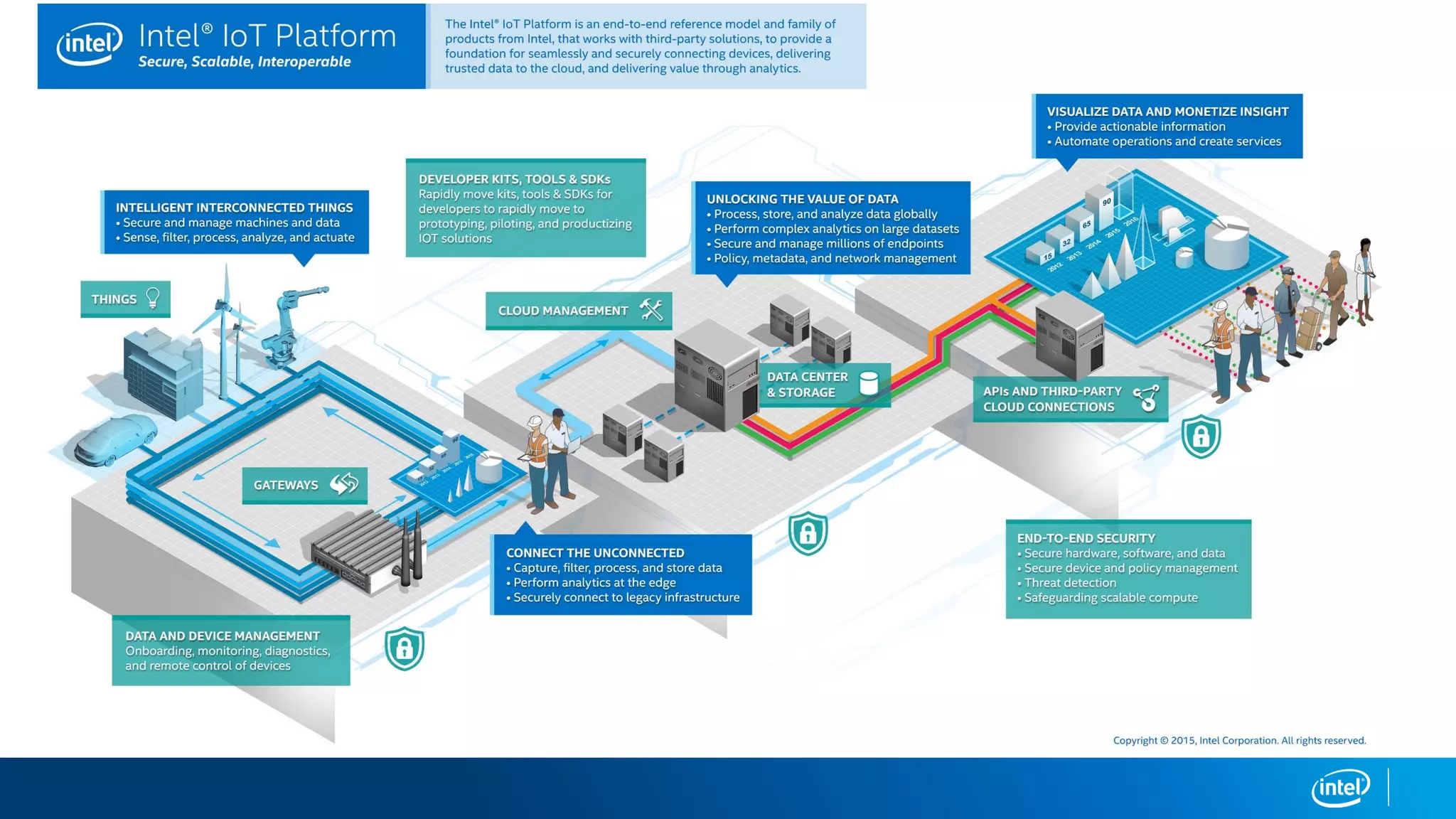
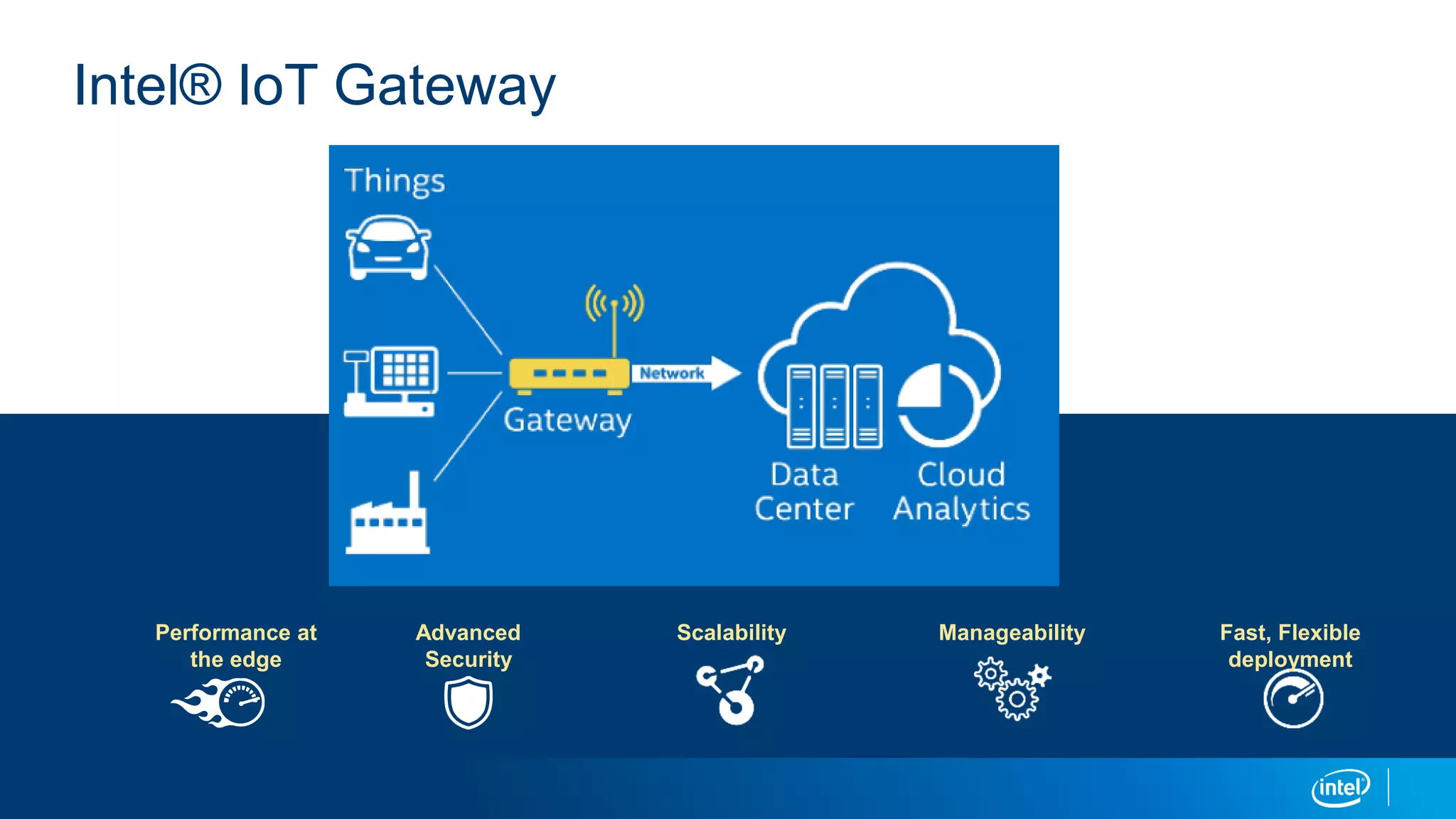
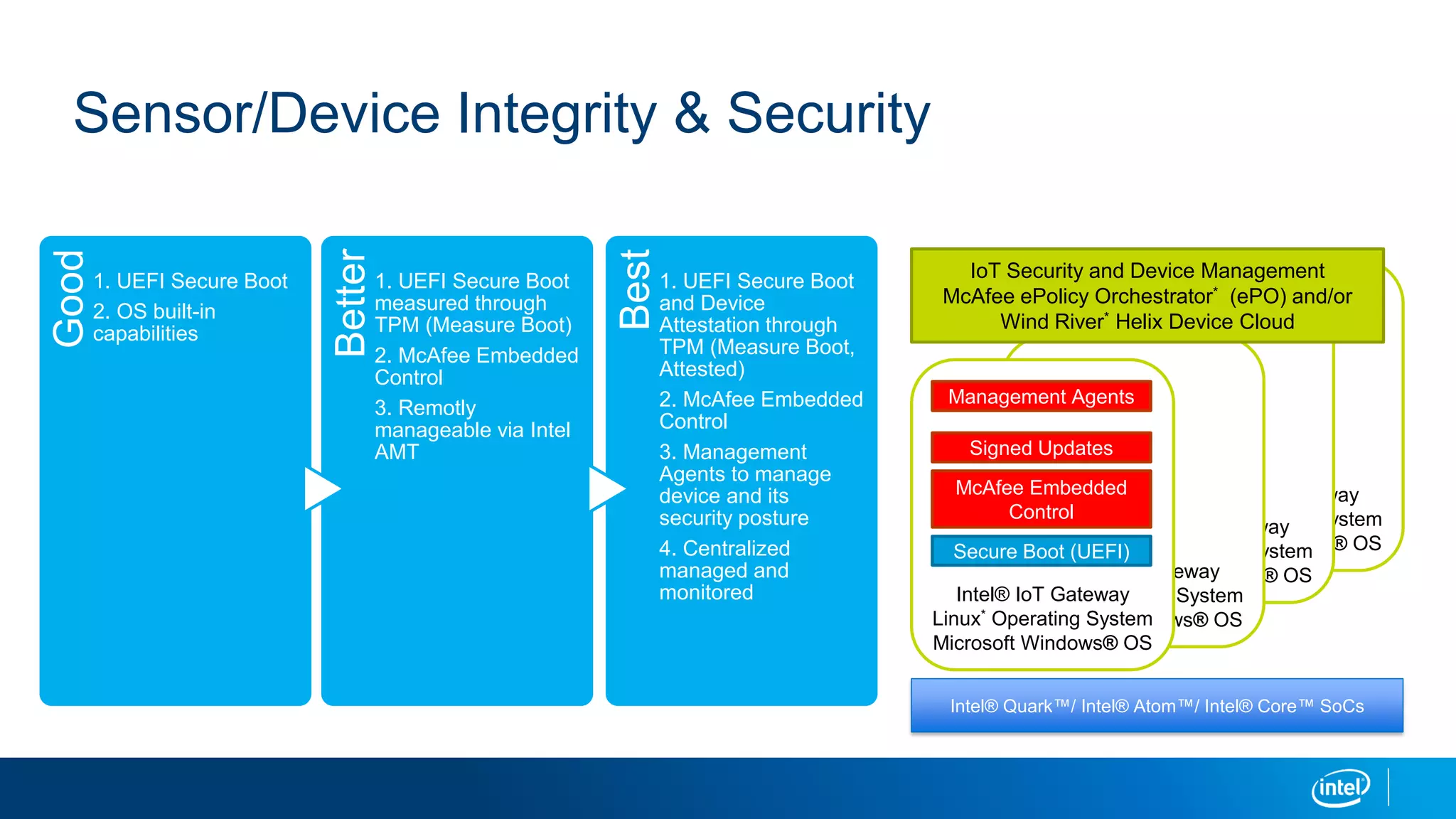
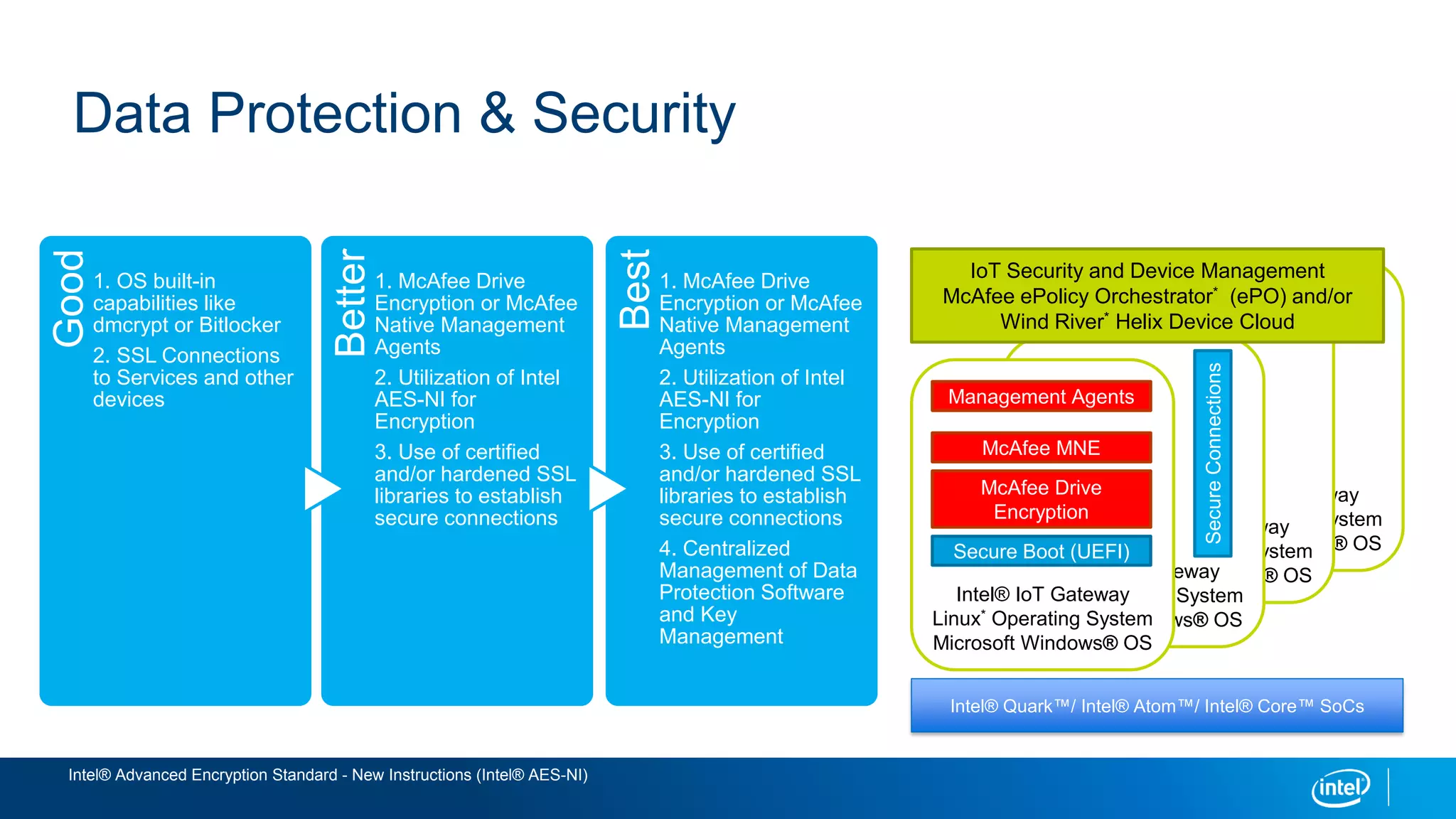
This document discusses security issues related to the Internet of Things (IoT). It notes that as the number of connected devices grows, so too will cyber attacks targeting IoT devices, as they often contain personal information and have existing vulnerabilities. Common IoT security threats mentioned include denial of service attacks, malware, data breaches, and weakening of security perimeters. The document advocates addressing IoT security across all levels from devices to cloud infrastructure. It presents Intel's IoT security portfolio as providing comprehensive protection from physical attacks and cyber threats, including features like secure boot, whitelisting, encryption, and centralized management of devices and data.