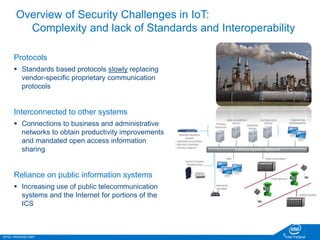
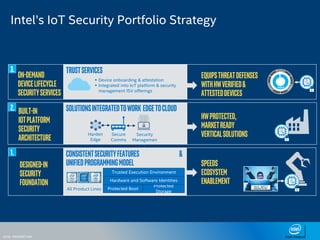
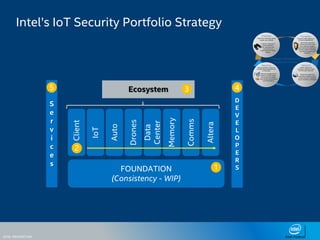
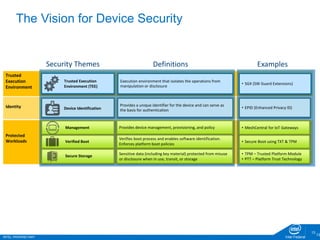
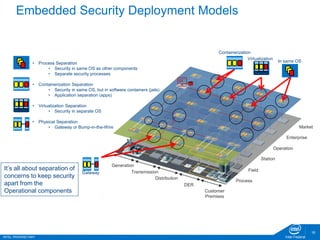
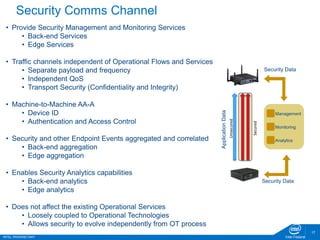
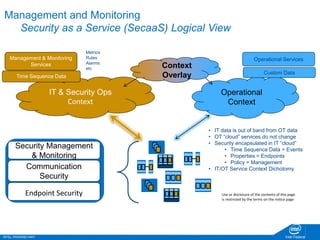
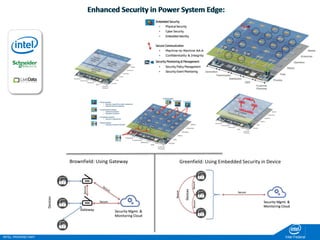
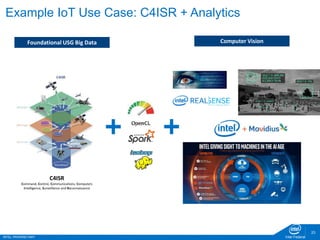
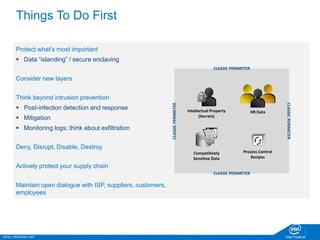
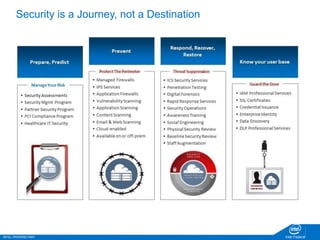
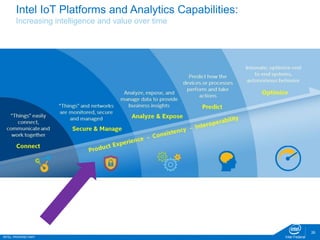
The document discusses the security challenges faced in the Internet of Things (IoT) and Industrial Control Systems (ICS), highlighting increased connectivity, complexity, and the rise of cyber threats. It outlines various attack scenarios, lessons learned, and the need for robust security measures, including device lifecycle security and the integration of security management across all devices. The ultimate goal is to ensure a secure and resilient IoT ecosystem through consistent security policies and advanced protection mechanisms.