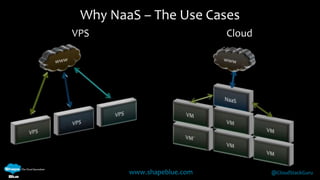
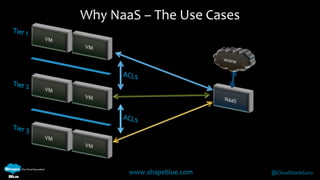
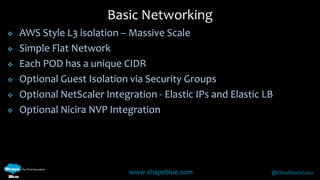
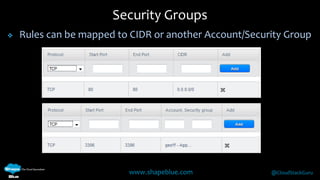
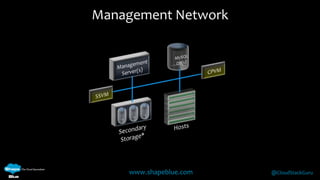
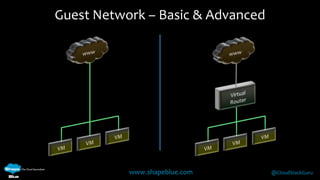
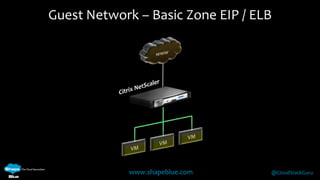
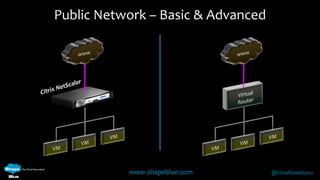
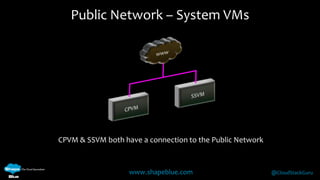
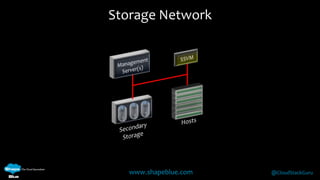
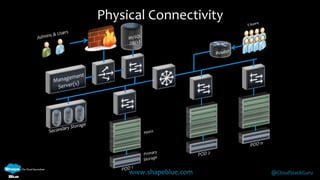
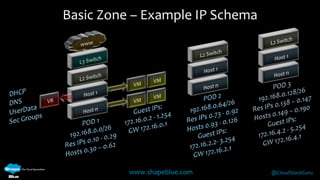
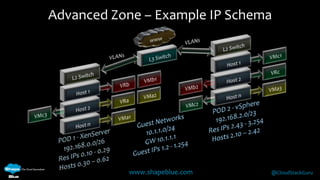
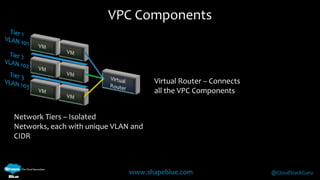
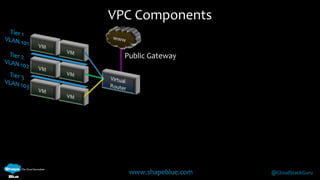
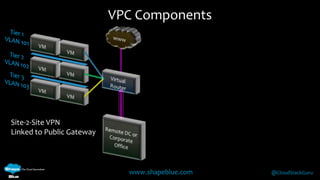
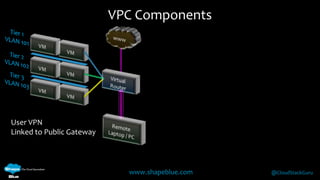
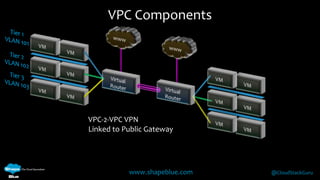
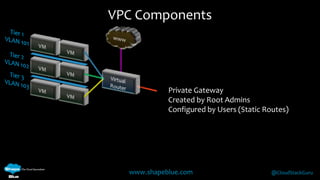
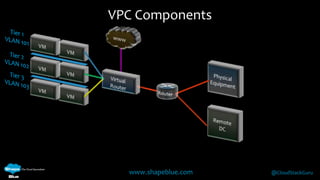
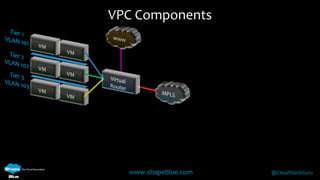
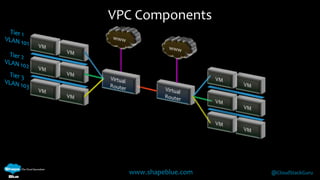
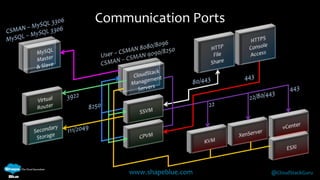
Geoff Higginbottom is a cloud architect and CTO of ShapeBlue who specializes in designing and building clouds based on Apache CloudStack. He has experience implementing CloudStack for various companies and is a committer for CloudStack. The document provides an overview of networking in CloudStack, including basic and advanced networking options, security groups, virtual private clouds, and the different network components and providers that can be used.