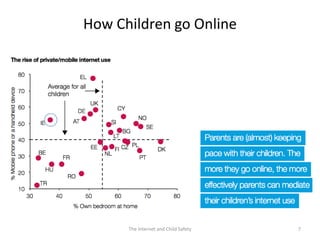
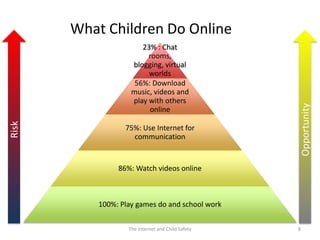
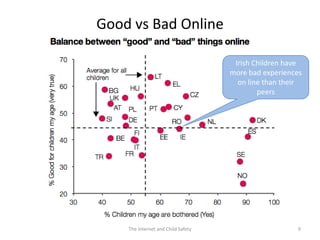
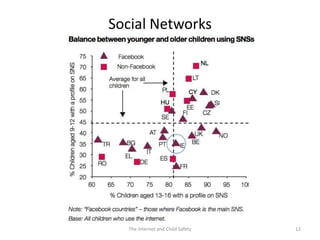
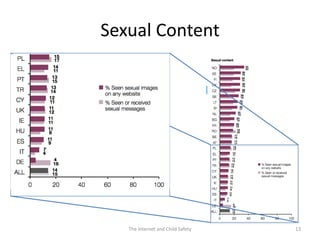
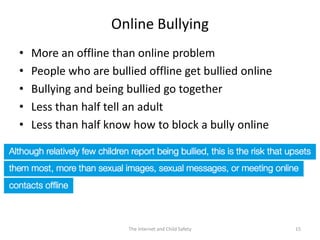
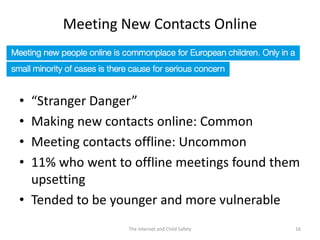
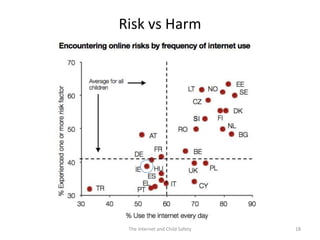
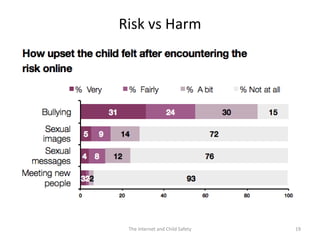
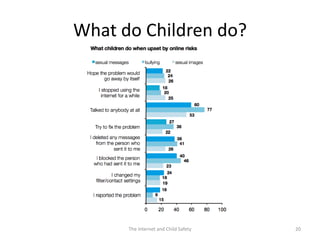
The document discusses risks and opportunities children face online. It summarizes research from a 2010 EU Kids Online survey of 25,000 children which found that internet use provides both opportunities and risks for children. While many fears about online risks exist, actual reported harm is often lower. Risky behavior tends to come from older, male, or more vulnerable children and increases with greater internet use and knowledge, though harm may decrease with age. The document provides strategies for parents to engage with children online to help manage risks.