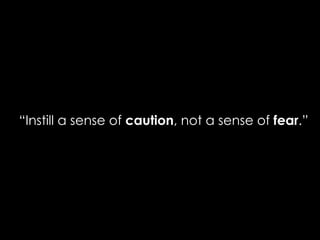
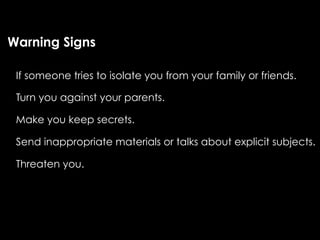
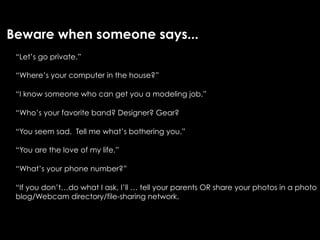
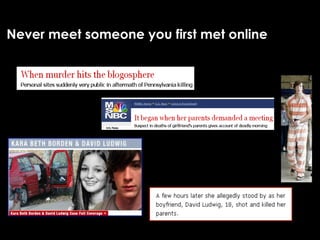
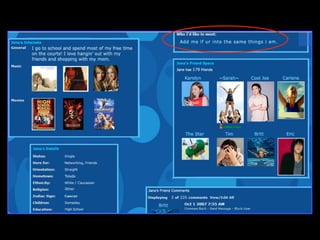
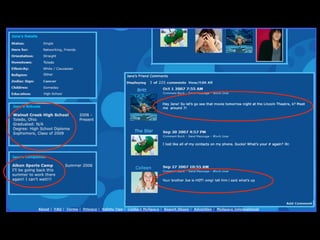
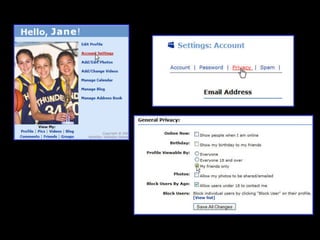
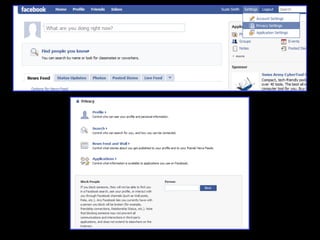
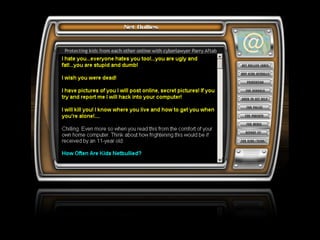
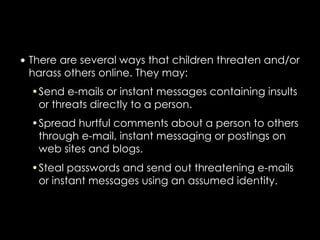
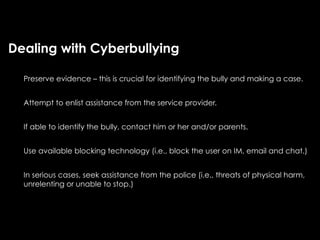
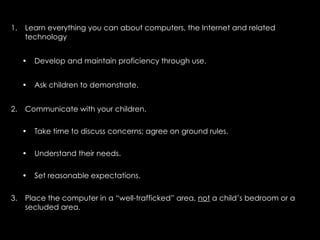
The document provides comprehensive guidelines on internet safety for teens, emphasizing the importance of caution while navigating online relationships and protecting personal information. It highlights the potential risks of cyberbullying, inappropriate content, and communication with strangers, including preventative measures and parental involvement in monitoring online activities. Additionally, it encourages responsible behavior by recognizing online predatory techniques and communicating effectively with trusted adults.