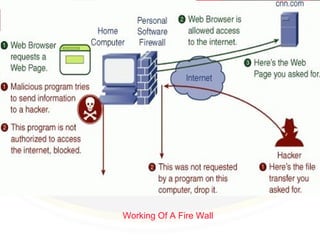
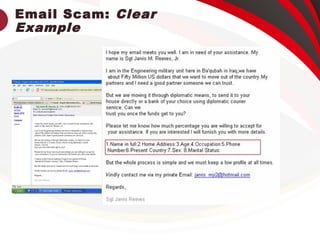
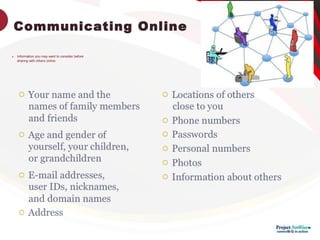
This document provides information on keeping computers safe from cyber threats. It defines key terms like firewalls, antivirus software, cookies, and passwords. It discusses how to safely use the internet, protect personal information, identify scams and phishing attempts, use strong passwords, and socialize online responsibly. It emphasizes the importance of being cautious with personal details, verifying website legitimacy, avoiding meeting strangers from online, and getting parent permission before providing information or payments.