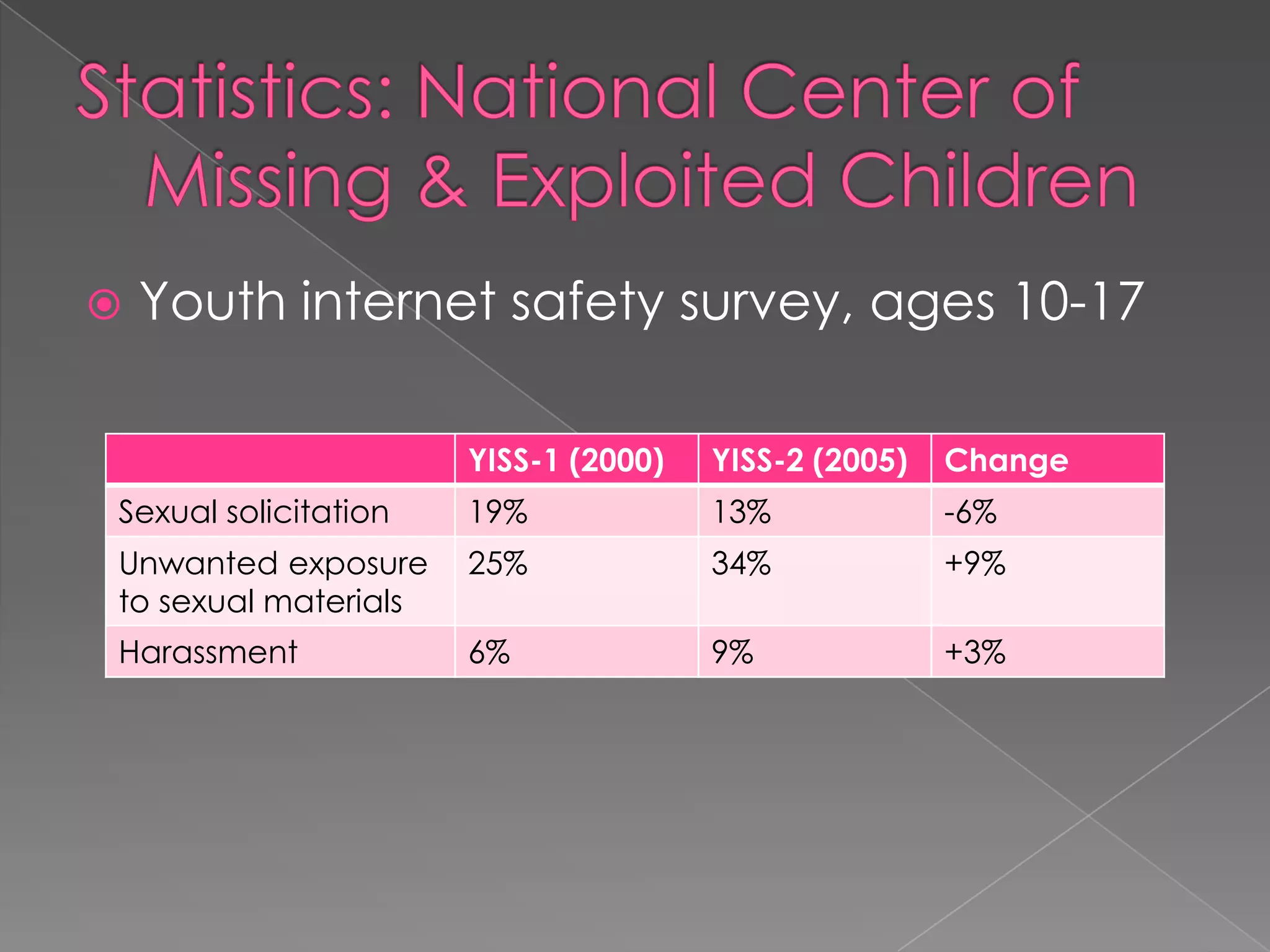
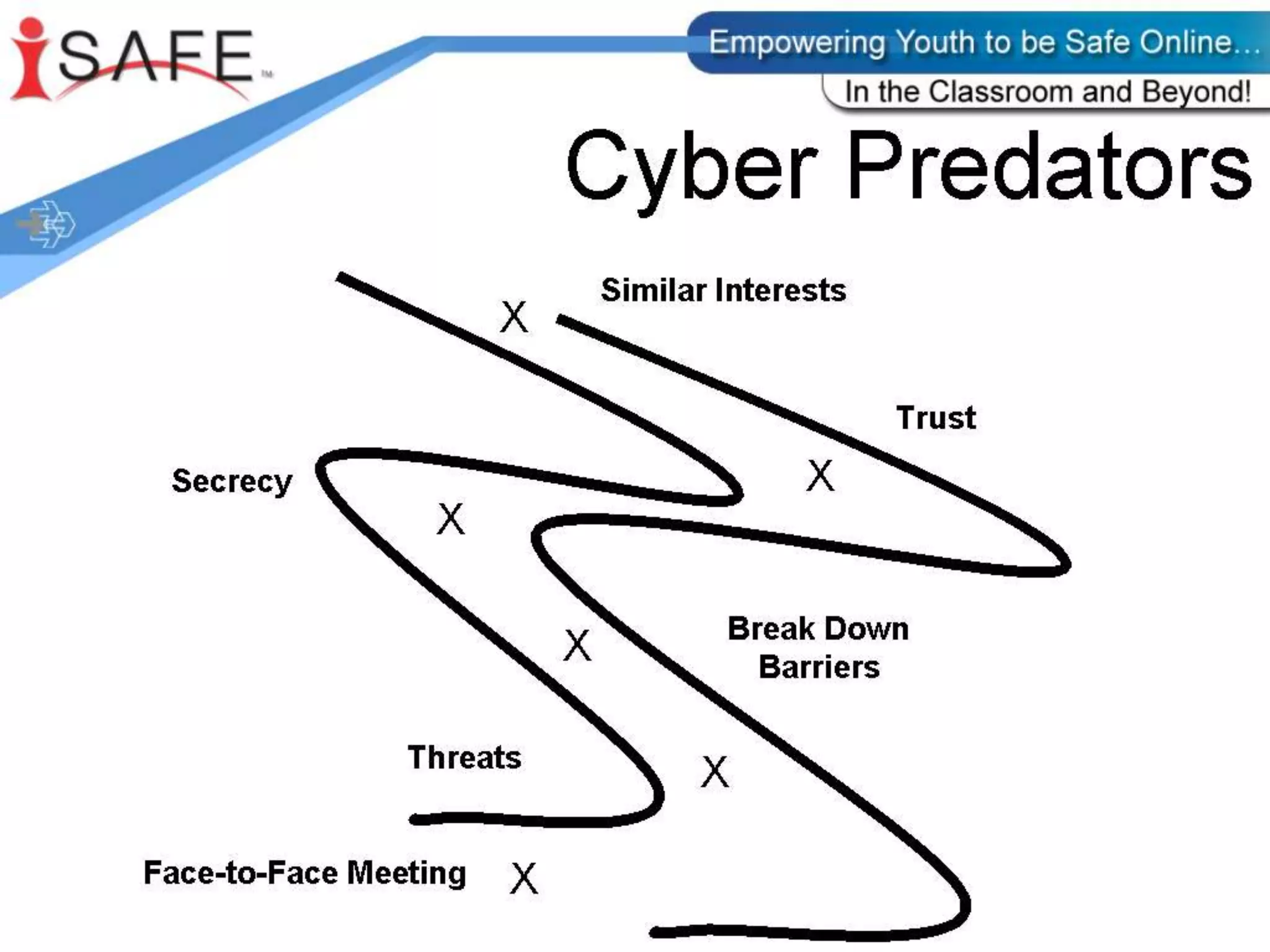
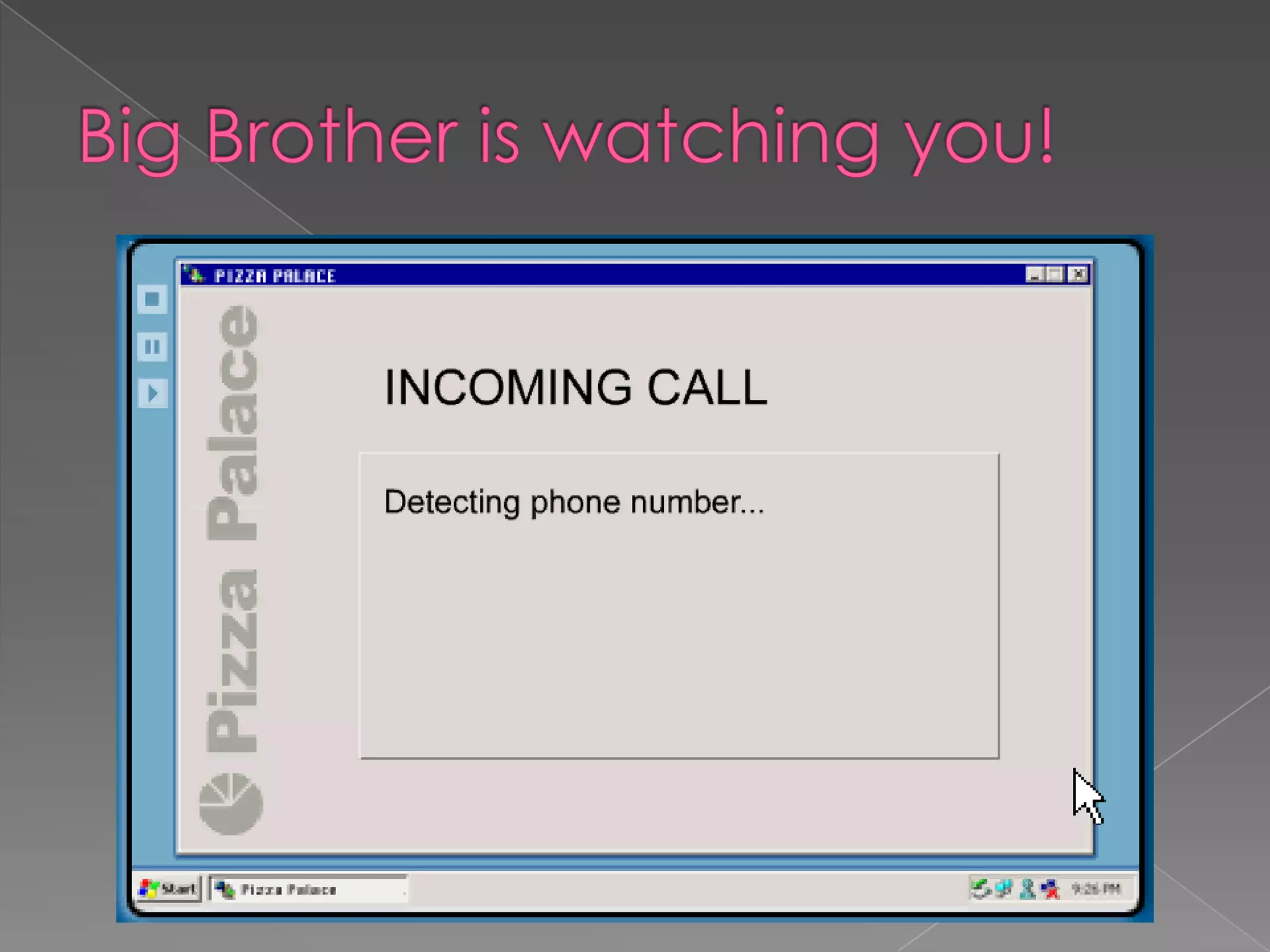
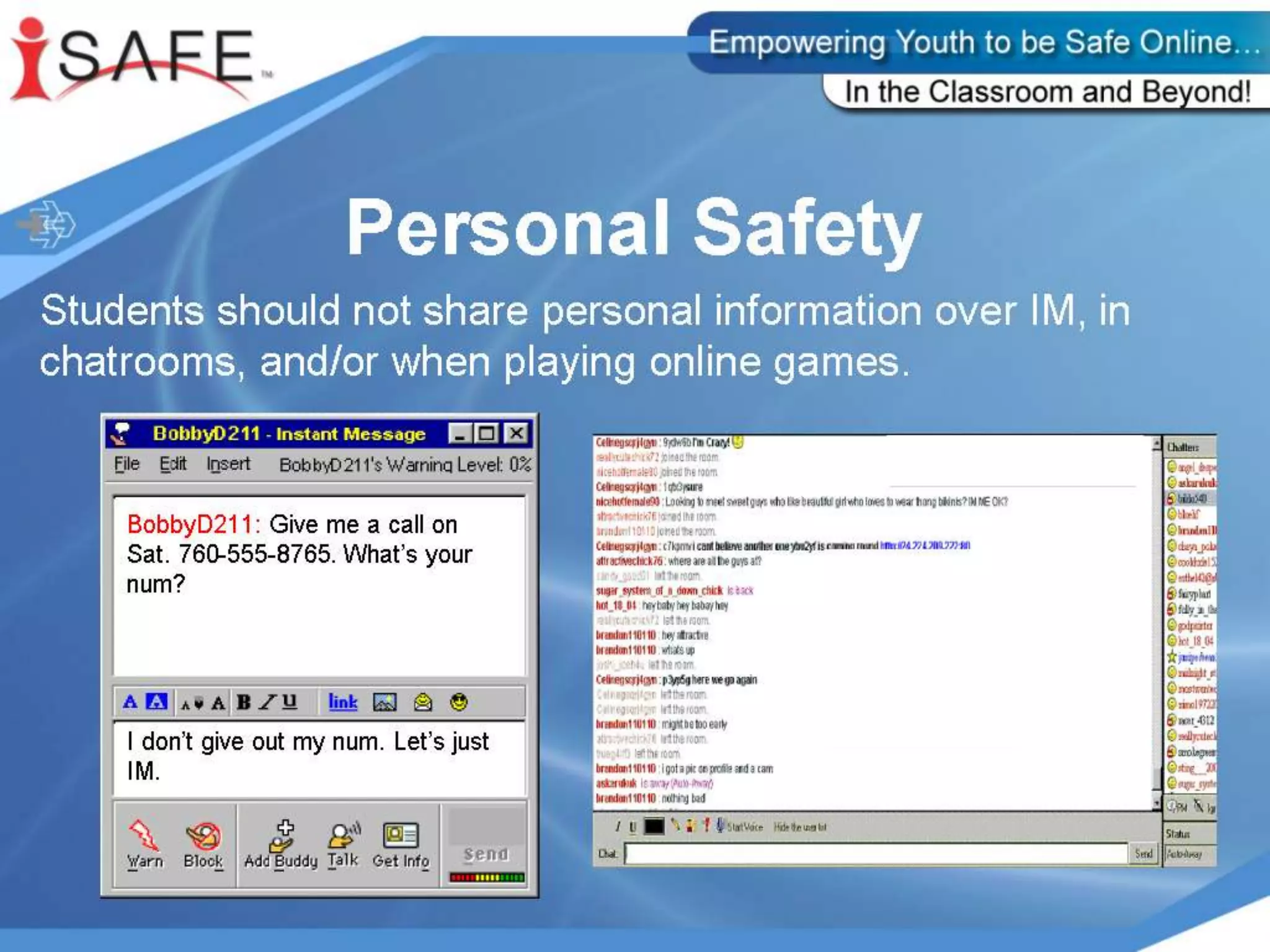
The i-Safe presentation for parents provided by Ms. Carrie Svihlik and Detective Keith Smith outlines various internet safety concerns, including internet predators, cyberbullying, and the implications of personal online profiles. It emphasizes the importance of educating both parents and students about safe online practices, including the use of privacy settings, recognizing cyberbullying, and understanding the risks associated with cell phone use and online gaming. The document also includes various resources for further guidance on internet safety for families.