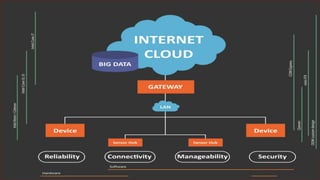
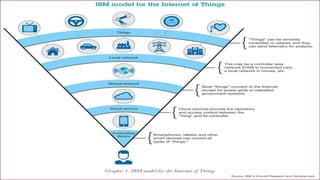
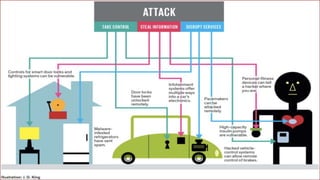
The document discusses security challenges with Internet of Things (IoT) devices and solutions to improve IoT security. It outlines that IoT systems connect various devices to networks, but many current devices have weaknesses like default passwords, vulnerabilities in protocols, and lack of updates. This can enable attacks like denial of service, data theft, and device compromise. The document recommends manufacturers implement security features like access control, authentication, encryption and that users isolate devices, change passwords, and keep software updated to safeguard IoT systems and the data they generate.