Embed presentation
Download to read offline

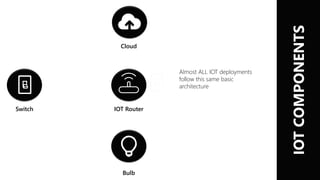
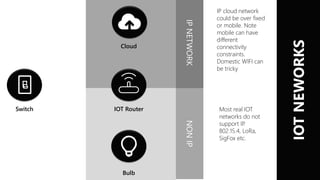
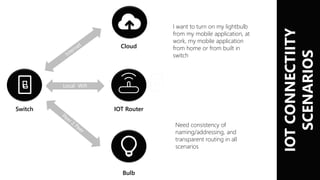





This document summarizes the key IoT security challenges discussed at an IoT security research day. It outlines the common IoT architecture of devices, routers, hubs and cloud connections. It notes that most real IoT networks do not use IP, instead using protocols like 802.15.4 and LoRa. The top 10 IoT security challenges discussed are encryption performance and footprint, encryption over networks, storage of secrets, tamper proofing devices, vulnerability of hubs, provenance of data, auditing access, permissioning, revocation and sharing. Background information provided includes a trusted execution environment, web application security models, peer reviews of IoT middleware security and a joint project between a company and Oxford University addressing







