- MPLS can be used to create virtual private networks (VPNs) that provide wide-area connectivity between sites of a large organization through dedicated label switched paths. This gives the appearance of a dedicated network while transmitting through a public or shared MPLS network.
- The integrated services model was developed by IETF to provide different levels of quality of service in the Internet. It uses resource reservation, packet classification, and scheduling to ensure applications receive their requested QoS.
- The Resource Reservation Protocol (RSVP) is used by the integrated services model to signal resource requirements and set up flows with a requested QoS across a network. RSVP uses soft state and receiver-initiated reservations.


![10.4.2 Controlled-Load Service
The controlled-load service is intended for adaptive applications that can tolerate
some delay but that are sensitive to traf®c overload conditions. These applica-
tions typically perform satisfactorily when the network is lightly loaded but
degrade signi®cantly when the network is heavily loaded. Thus the controlled-
load service was designed to provide approximately the same service as the best-
effort service in a lightly loaded network regardless of the actual network con-
dition. The above interpretation is deliberately imprecise for a reason. Unlike the
guaranteed service that speci®es a quantitative guarantee, the controlled-load
service is qualitative in the sense that no target values on delay or loss are
speci®ed. However, an application requesting a controlled-load service can
expect low queueing delay and low packet loss, which is a typical behavior of
a statistical multiplexer that is not congested. Because of these loose de®nitions
of delay and loss, the controlled-load service requires less implementation com-
plexity than the guaranteed service requires. For example, the controlled-load
service does not require the router to implement the weighted fair queueing
algorithm.
As in the guaranteed service, an application requesting a controlled-load
service has to provide the network with the token bucket speci®cation of its
¯ow. The network uses admission control and policing to ensure that enough
resources are available for the ¯ow. Flows that conform to the token bucket
speci®cation should be served with low delay and low loss. Flows that are non-
conforming should be treated as best-effort service.
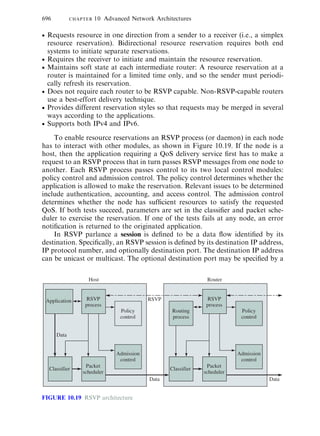
10.5 RSVP
The resource ReSerVation Protocol (RSVP) was designed as an IP signaling
protocol for the integrated services model. RSVP can be used by a host to
request a speci®c QoS resource for a particular ¯ow and by a router to provide
the requested QoS along the path(s) by setting up appropriate states.6
Because IP traditionally did not have any signaling protocol, the RSVP
designers had the liberty of constructing the protocol from scratch. RSVP has
the following features:
Performs resource reservations for unicast and multicast (multipoint-to-multi-
point) applications, adapting dynamically to changing group membership and
changing routes.
10.5 RSVP 695
6
RSVP can be extended for use in other situations. For example RSVP has been proposed to reserve
resources and install state related to forwarding in MPLS [RFC 2430].
| | | Textbook Table of Contentse-Text Main Menu
v
v](https://image.slidesharecdn.com/integratedservicesrsvp-200324103719/85/Integrated-services-and-RSVP-Protocol-3-320.jpg)





![INTEGRITY: This object carries cryptographic and authentication informa-
tion that is used to verify the contents of an RSVP message.
SCOPE: This object provides an explicit list of senders that are to receive
this message. The object may be used in Resv, ResvErr, or ResvTear
messages.
RESV_CONFIRM: This object carries the receiver IP address that is to
receive the conformation.
RSVP messages are built from a common header followed by a number of
objects. For example, the format of a Path message is given as follows:
Path message::=Common Header[INTEGRITY]
SESSIONRSVP_HOP
TIME_VALUES
[POLICY_DATA...]
[sender descriptor]
sender descriptor::=SENDER_TEMPLATESENDER_TSPEC[ADSPEC]
Another important example is the Resv message, which is given as follows:
Resv message::=Common Header[INTEGRITY]
SESSIONRSVP_HOP
TIME_VALUES
[RESV_CONFIRM][SCOPE]
[POLICY_DATA...]
STYLEflow descriptor list
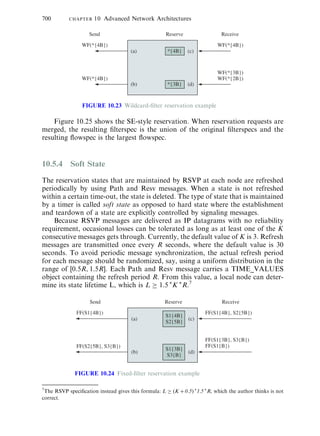
The ¯ow descriptor list depends on the reservation styles. For Wildcard
Filter (WF) style, the list is
flow descriptor list::=WF flow descriptor
WF flow descriptor::=FLOWSPEC
For Fixed FILTER (FF) style, the list is given by
flow descriptor list::=FLOWSPECFILTER_SPEC|
flow descriptor listFF flow descriptor
FF flow descriptor::=[FLOWSPEC]FILTER_SPEC
For Shared Explicit (SE) style, the ¯ow descriptor list is given by
flow descriptor::=SE flow descriptor
SE flow descriptor::=FLOWSPECfilter spec list
filter spec list::=FILTER_SPEC|
filter spec listFILTER_SPEC
10.6 DIFFERENTIATED SERVICES
The integrated services model was a ®rst step toward providing QoS in the
Internet. However, the integrated services model requires a router to keep a
10.6 Differentiated Services 703
| | | Textbook Table of Contentse-Text Main Menu
v
v](https://image.slidesharecdn.com/integratedservicesrsvp-200324103719/85/Integrated-services-and-RSVP-Protocol-11-320.jpg)