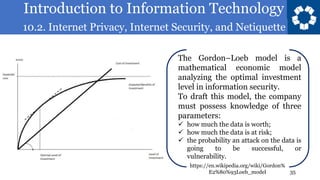
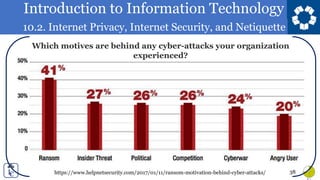
The document discusses various topics relating to internet privacy, security, and netiquette. It covers computer security and the importance of protecting systems from harm. Examples are given of different systems that are at risk of attacks, including financial systems, utilities, aviation, consumer devices, large corporations, and automobiles. Specific security issues and past attacks are described for each one.