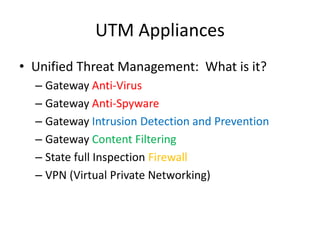
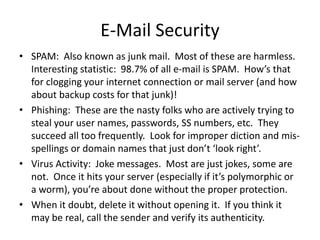
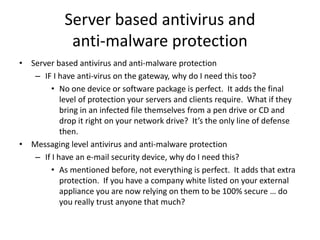
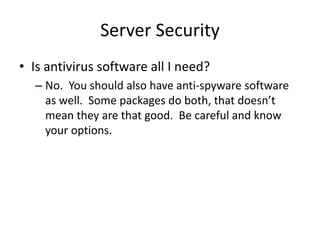
Jim Slick is the President and CEO of Slick Cyber Systems. He has over 30 years of experience in IT, including building data centers. His presentation covers various topics related to enterprise security, including gateway security, unified threat management appliances, email security, server security, desktop security, remote user security, disaster recovery and backup, social engineering, security policies, and outsourcing IT functions. He emphasizes the importance of having proper security measures, policies, and expertise in place to protect a business and its data.