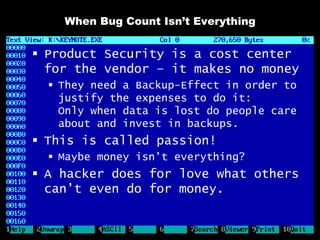
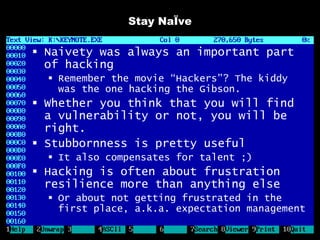
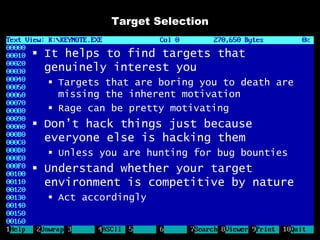
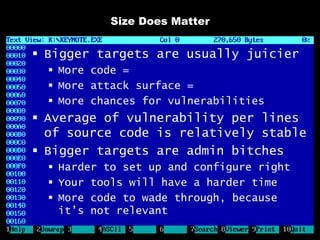
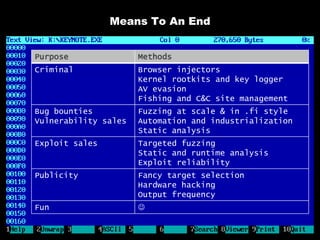
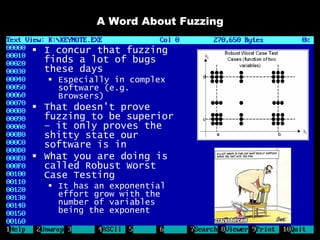
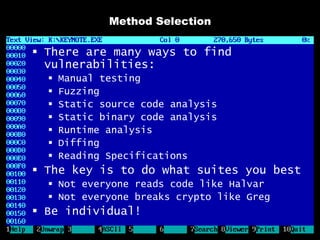
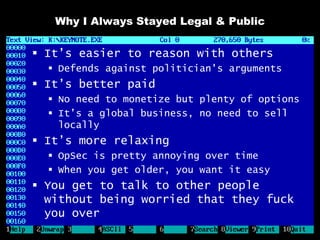
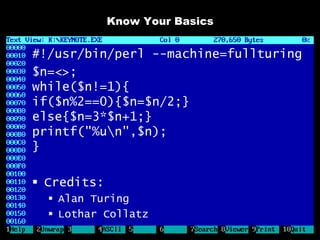
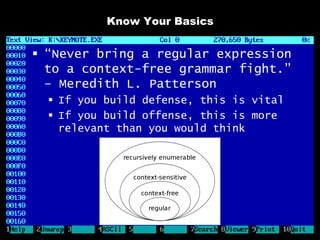
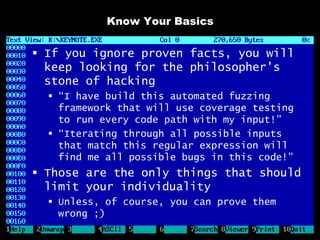
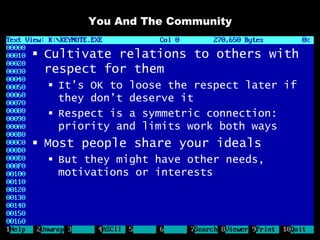
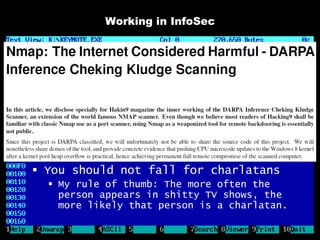
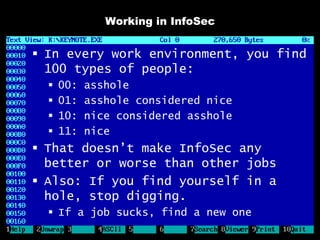
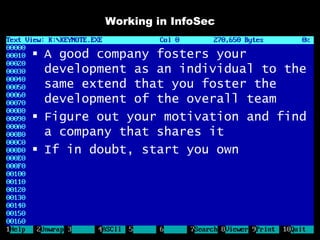
The document discusses reasons for hacking and target selection in hacking. It notes that reasons for hacking have changed over time from curiosity to career goals and public recognition. When selecting targets, it recommends choosing things that genuinely interest you rather than just following trends, and that bigger targets tend to have more code and vulnerabilities but are also more challenging. The purpose of hacking should guide the methods used, such as automation for bug bounties or reliability testing for exploit sales.




![Hacking in the 2000s
cd ~/some/open/source && grep –E –e
‘printfs*([^”]+[,)]’ *.c
7350 x2
Solaris sadmind
Cisco UDP echo
Worms!!1!
Heap Spraying
Fuzzing
Rise of the client-side attacks
Rise of the web application bugs](https://image.slidesharecdn.com/keynotefx-tryharder2beyourself-121127044944-phpapp02/85/Keynote-fx-try-harder-2-be-yourself-12-320.jpg)