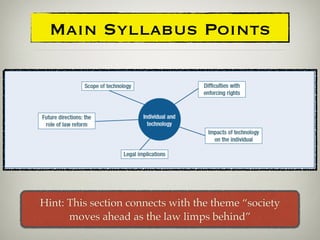
1. Technology often develops faster than laws can regulate it, creating privacy issues that laws must address, such as regarding Google Street View and CCTV.
2. The internet allows anonymity and global connectivity but challenges jurisdiction and law enforcement across borders. It also enables new forms of fraud, spam, and piracy.
3. Governments try to balance internet openness with protecting privacy, children, and intellectual property through domestic laws and international treaties, but perfect control is difficult given the internet's global nature.