1. Cyber law governs rules related to use of the internet and addresses legal issues like intellectual property, privacy, freedom of expression, and jurisdiction.
2. Cyber law encompasses laws around cyber crimes, digital signatures, intellectual property, data protection, and privacy. The Information Technology Act, 2000 was enacted in India to regulate e-commerce, cyber crimes, and other cyber activities.
3. Regulation of cyber space can occur through norms, law, architecture (technological design), or market forces. As online interactions increase, cyber law is important to balance individual privacy with organizations' interests while addressing new legal challenges of technology.

![2. Electronic and Digital Signatures
3. Intellectual Property
4. Data Protection and Privacy
Cybercrimes are unlawful acts where the computer is used either as a tool or a target or both. The enormous growth in electronic
commerce (e-commerce) and online share trading has led to a phenomenal spurt in incidents of cyber-crime. To prevent these crimes
and to maintain the fair usage of the internet cyber laws are designed.
Cyber law includes some of the major laws:
1. Copyright law
2. Software and source code Licenses
3. Trademark law
4. Semiconductor law
5. Patent law
Cyber law is important because it touches almost all aspects of transactions and activities concerning the Internet, the World Wide Web
and Cyberspace.
Data protection and privacy laws aim to achieve a fair balance between the privacy rights of the individual and the interests of data
controllers such as banks, hospitals, email service providers etc. These laws seek to address the challenges to privacy caused by
collecting, storing and transmitting data using new technologies.
In early times, there was no statute in India for governing Cyber Laws involving privacy issues, jurisdiction issues, intellectual property
rights issues and a number of other legal questions. With the tendency of misusing of technology, there arisen a need of strict statutory
laws to regulate the criminal activities in the cyber world and to protect the true sense of technology "INFORMATION TECHNOLOGY ACT,
2000" [ITA- 2000] was enacted by Parliament of India to protect the field of e-commerce, e-governance, e-banking as well as penalties
and punishments in the field of cyber-crimes. The above Act was further amended
in the form of IT Amendment Act, 2008 [ITAA-2008]
Need for Cyber Law
There are various reasons why it is extremely difficult for conventional law to cope with cyberspace. Some of these are discussed
below.
1. Cyberspace is an intangible dimension that is impossible to govern and regulate using conventional law.
2. Cyberspace has complete disrespect for jurisdictional boundaries. A person in India could break into a bank’s electronic vault hosted
on a computer in USA and transfer millions of Rupees to another bank in Switzerland, all within minutes. All he would need is a laptop
computer and a cell phone.
3. Cyberspace handles gigantic traffic volumes every second. Billions of emails are crisscrossing the globe even as we read this, millions
of websites are being accessed every minute and billions of dollars are electronically transferred around the world by banks every day.
4. Cyberspace is absolutely open to participation by all. A ten-year-old in Bhutan can have a live chat session with an eight-year-old in
Bali without any regard for the distance or the anonymity between them.
5. Cyberspace offers enormous potential for anonymity to its members. Readily available encryption software and stenographic tools
that seamlessly hide information within image and sound files ensure the confidentiality of information exchanged between cyber-
citizens.
6. Cyberspace offers never-seen-before economic efficiency. Billions of dollars’ worth of software can be traded over the Internet
without the need for any government licenses, shipping and handling charges and without paying any customs duty.
7. Electronic information has become the main object of cyber-crime. It is characterized by extreme mobility, which exceeds by far
the mobility of persons, goods or other services. International computer networks can transfer huge amounts of data around the
globe in a matter of seconds.
8. A software source code worth crores of rupees or a movie can be pirated across the globe within hours of their release.
9. Theft of corporeal information (e.g. books, papers, CD ROMs, floppy disks) is easily covered by traditional penal provisions.
However, the problem begins when electronic records are copied quickly, inconspicuously and often via telecommunication facilities.
Here the “original” information, so to say, remains in the “possession” of the “owner” and yet information gets stolen.
Regulation of cyber space
As electronic transactions over the Internet become important the question arises whether they will be controlled on the national and
international levels.](https://image.slidesharecdn.com/2-160617162652/85/Cyber-Law-Forensics-2-320.jpg)








![tax system is also equitable in its application. Not only does it treat taxpayers in similar economic circumstances9
similarly but
also it makes suitable distinctions in its treatment of those in different economic situations.) (It necessarily raises questions of
"similar economic circumstances", certainty in the tax laws is a fundamental principle in the establishment of ideal tax structure
because predictability of tax consequences is an essential component of other basic tax principles. Finally, taxation has always
been a mechanism for stabilization and regulation of the economy10
. Recognizing this fact, legislature has emphasized the
economic effects of the principle of taxation, with a particular focus on encouraging economic growth.)
Challenges Before Tax authorities
The general perceived wisdom to which tax authorities universally appear to subscribe, is that their major challenges regarding e-
commerce are:
(i) Identifying the tax payer, especially when an Internet user is involved.
(ii) Identifying audit risks and developing audit trials to ensure compliance.
(iii) Obtaining access to verifiable information and documents.
(iv) Obtaining access to encrypted data
(v) Developing a response to the advent of electronic money (e-cash) and ensuring efficient mechanism for collecting tax
especially from non-resident tax payers.
Points to remember in e taxation(Limitations):
There is a need for initial inter-government and multi-jurisdictional co-operation and agreement to synchronize
the taxation treatment.
Taxation authorities need to modernize their operation radically.
There is a need to monitor cross-border business activities on the Internet.
Authorities need to upgrade their technological knowledge.
Tax authorities need better data mining techniques database management took and an audit policy indeed towards thoroughly
examining the various models of e-business.
Tax treatment need to match electronic reality.
Privileges such an extended filing dates for tax returns could be granted to tax payers who conduct their dealings with the tax
authorities electronically.
Many tax authorities urgently need to co-ordinate better with other Government departments to obtain information on matters
such as customs duty clearances.
General legislations and domain registration requirements and investment attraction.
Tax policy makers need to strike a balance between providing incentives to promote the new e-business economy. Simplicity of
rules and case of compliance are obvious legislative and administrative goals yet these must be balanced by regulatory controls
preventing crime and tax fraud ensuring personal data protection.
E governance and Cyber-crime
E-governance or Electronic Governance is dealt with under Sections 4 to 10A of the IT Act, 2000. It provides for legal recognition of
electronic records and Electronic signature and also provides for legal recognition of contracts formed through electronic means.
Filing of any form, application or other documents, creation, retention or preservation of records, issue or grant of any license or permit
or receipt or payment in Government offices and its agencies may be done through the means of electronic form.
Through e-governance, government services will be made available to citizens in a convenient, efficient and transparent manner. The
three main target groups that can be distinguished in governance concepts are government, citizens and businesses/interest groups. In
e-governance there are no distinct boundaries.
[2]
Generally, four basic models are available – government-to-citizen (customer), government- to-employees, government-to-
government and government-to-business.
In cyber-crime, ICT devices are either the target or the means of the crime, or are incidental to it. Most cyber-crimes are not new
crimes. Often the only difference is that the evidences are in electronic form or that the tools used to commit the crimes are ICT
tools. Indeed, most of the crimes committed today involve some amount of evidence in the electronic form such as phone calls,
messages, emails, electronic files etc. Most cyber-crime cases are booked in India under the provisions of the Indian Penal Code (IPC)
and laws on economic offenses, and only very few under the Information Technology Act 2000. However, the Information Technology
Act 2000 has enabling provisions for admissibility of electronic evidences in the courts of law.
Unlike traditional crime, cyber-crime is not restricted by geographical boundaries. Indeed, often cyber criminals operate from other
countries.
Information warfare is now a recognized national threat. Indeed, “IT disaster” is among is the newest additions to the man-made
disasters. This brings out the need of strong international cooperation on real-time basis to tackle cyber-crimes. Many companies do
not report to authorities about attacks on their networks out of fear of adverse publicity and losing the confidence of the clients.](https://image.slidesharecdn.com/2-160617162652/85/Cyber-Law-Forensics-11-320.jpg)

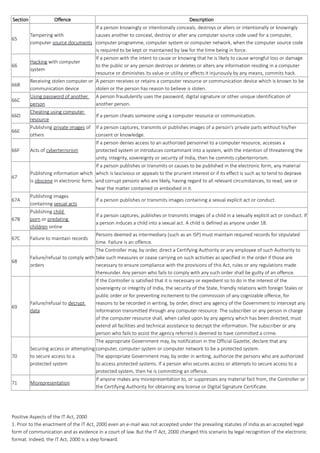
![2. From the perspective of the corporate sector, companies shall be able to carry out electronic commerce using the legal infrastructure
provided by the IT Act, 2000. Till the coming into effect of the Indian Cyber law, the growth of electronic commerce was impeded in our
country basically because there was no legal infrastructure to regulate commercial transactions online.
3. Corporate will now be able to use digital signatures to carry out their transactions online. These digital signatures have been given legal
validity and sanction under the IT Act, 2000.
4. In today’s scenario, information is stored by the companies on their respective computer system, apart from maintaining a backup.
Under the IT Act, 2000, it shall now be possible for corporate to have a statutory remedy if any one breaks into their computer systems or
networks and causes damages or copies data. The remedy provided by the IT Act, 2000 is in the form of monetary damages, by the way of
compensation, not exceeding Rs. 1, 00, 00,000.
5. IT Act, 2000 has defined various cyber-crimes which includes hacking and damage to the computer code. Prior to the coming into
effect of the Indian Cyber law, the corporate were helpless as there was no legal redress for such issues. But the IT Act, 2000 changes the
scene altogether.
The Grey Areas of the IT Act, 2000[4]:
1. The IT Act, 2000 is likely to cause a conflict of jurisdiction.
2. Electronic commerce is based on the system of domain names. The IT Act, 2000 does not even touch the issues relating to domain
names. Even domain names have not been defined and the rights and liabilities of domain name owners do not find any mention in the
law.
3. The IT Act, 2000 does not deal with any issues concerning the protection of Intellectual Property Rights I the context of the online
environment. Contentious yet very important issues concerning online copyrights, trademarks and patents have been left untouched by
the law, thereby leaving many loopholes.
4. As the cyber law is growing, so are the new forms and manifestations of cybercrimes. The offences defined in the IT Act, 2000 are by no
means exhaustive. However, the drafting of the relevant provisions of the IT Act, 2000 makes it appear as if the offences detailed therein
are the only cyber offences possible and existing. The IT Act, 2000 does not cove various kinds of cybercrimes and Internet related crimes.
These Include: -
a) Theft of Internet hours
b) Cyber theft
c) Cyber stalking
d) Cyber harassment
e) Cyber defamation
f) Cyber fraud
g) Misuse of credit card numbers
h) Chat room abuse
5. The IT Act, 2000 has not tackled several vital issues pertaining to e-commerce sphere like privacy and content regulation to name a few.
Privacy issues have not been touched at all.
6. Another grey area of the IT Act is that the same does not touch upon any anti- trust issues.
7. The most serious concern about the Indian Cyber law relates to its implementation. The IT Act, 2000 does not lay down parameters for
its implementation. Also, when internet penetration in India is extremely low and government and police officials, in general are not very
computer savvy, the new Indian cyber law raises more questions than it answers. It seems that the Parliament would be required to
amend the IT Act, 2000 to remove the grey areas mentioned above.](https://image.slidesharecdn.com/2-160617162652/85/Cyber-Law-Forensics-14-320.jpg)