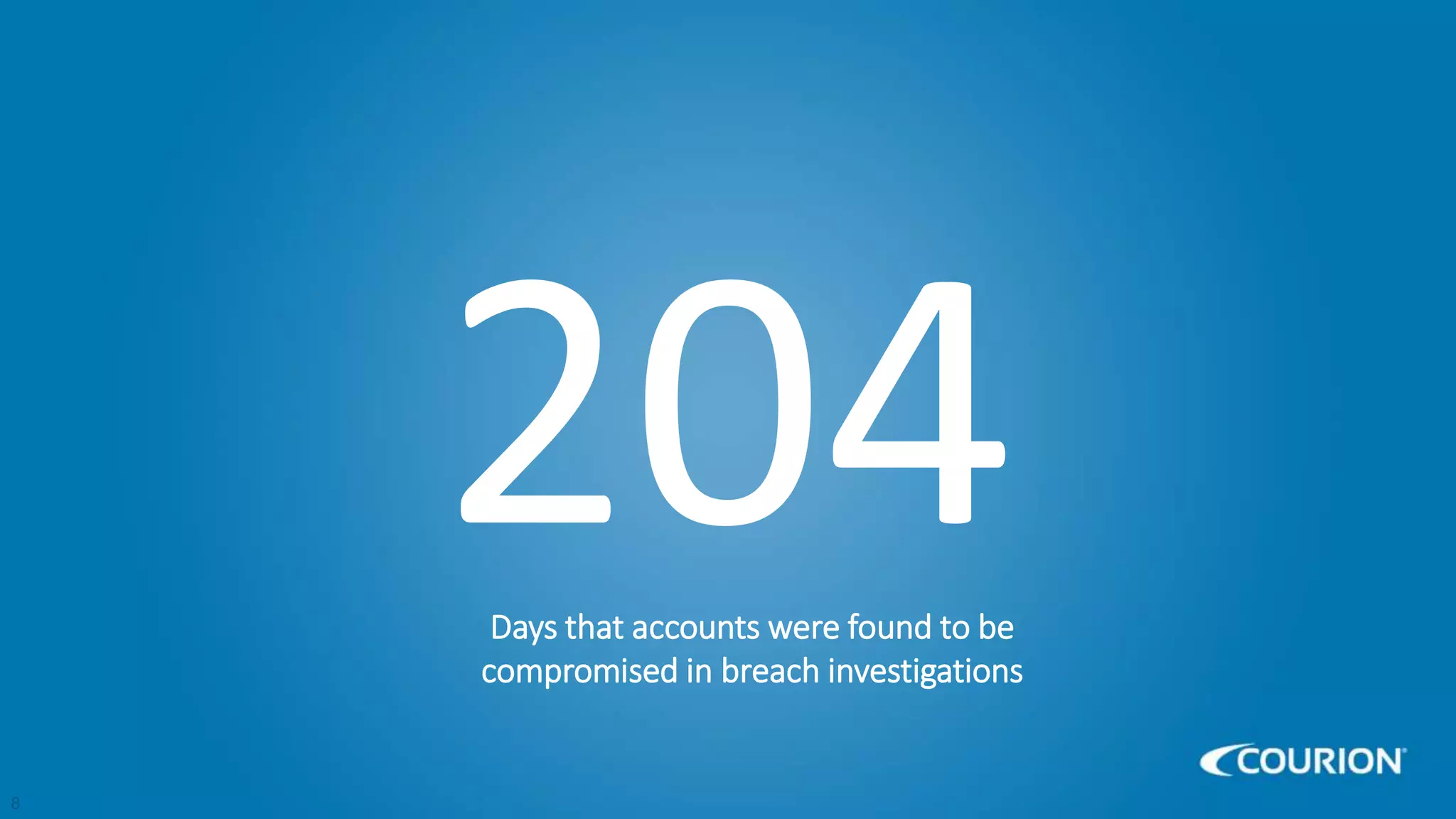
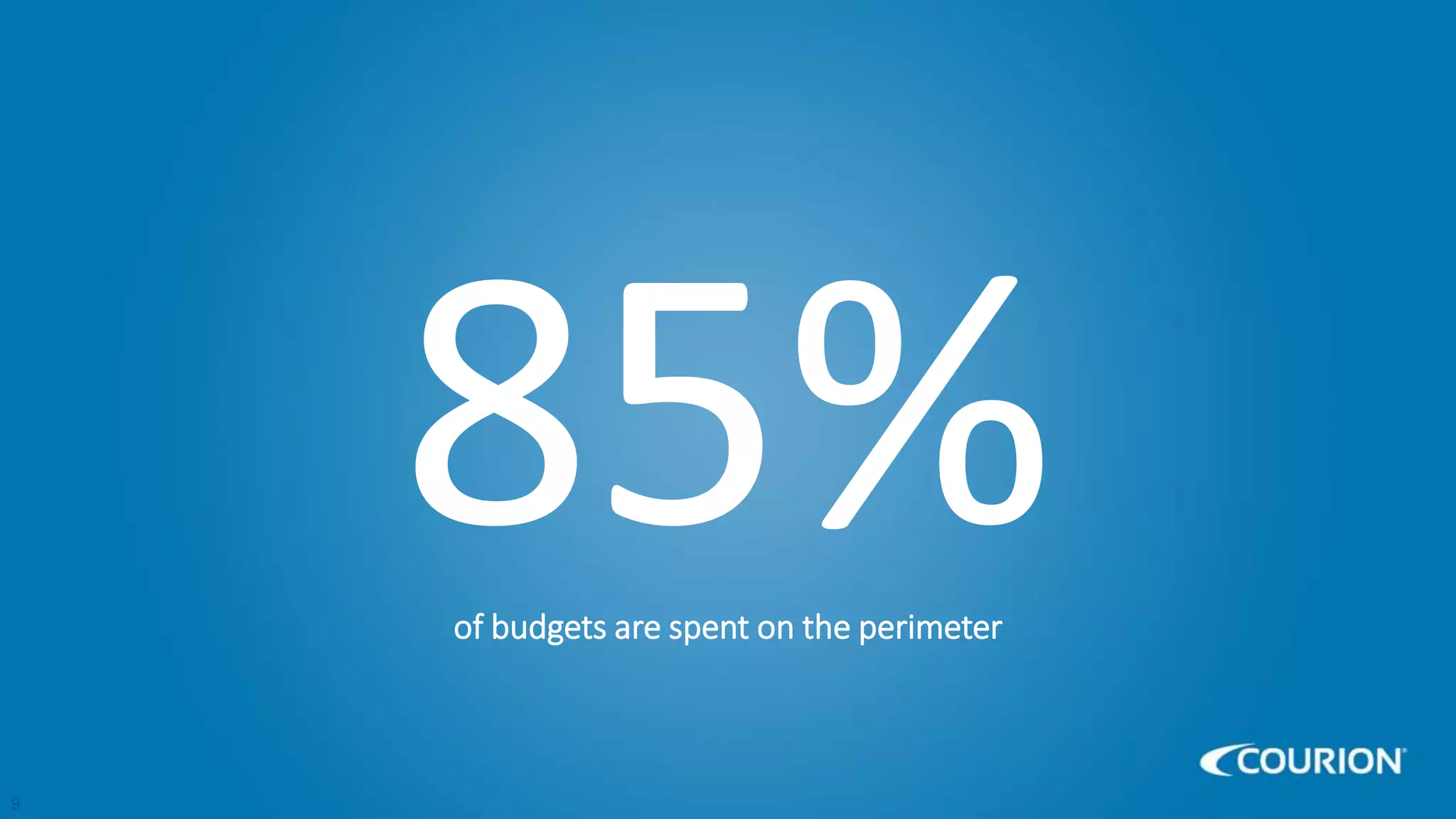
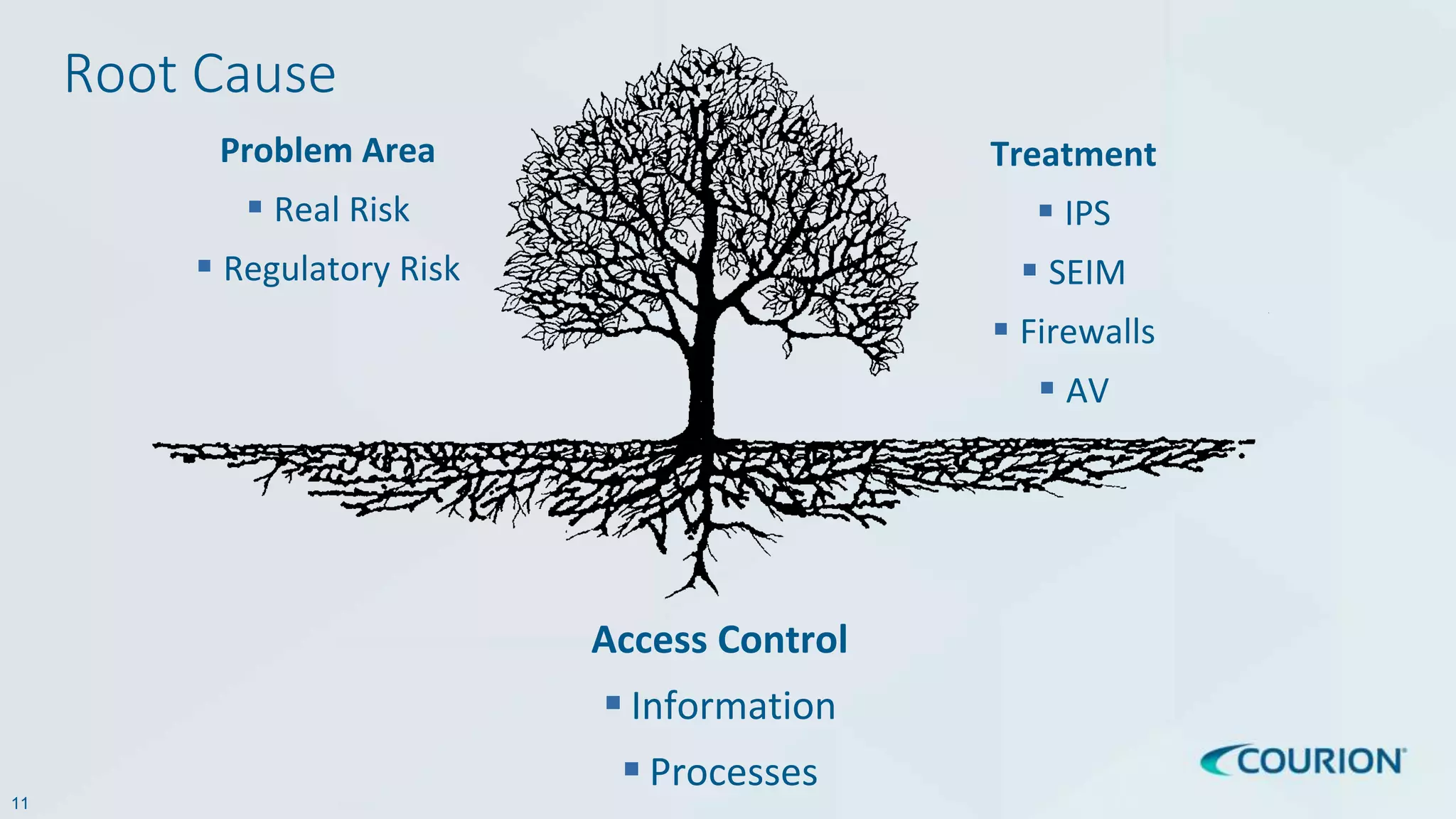
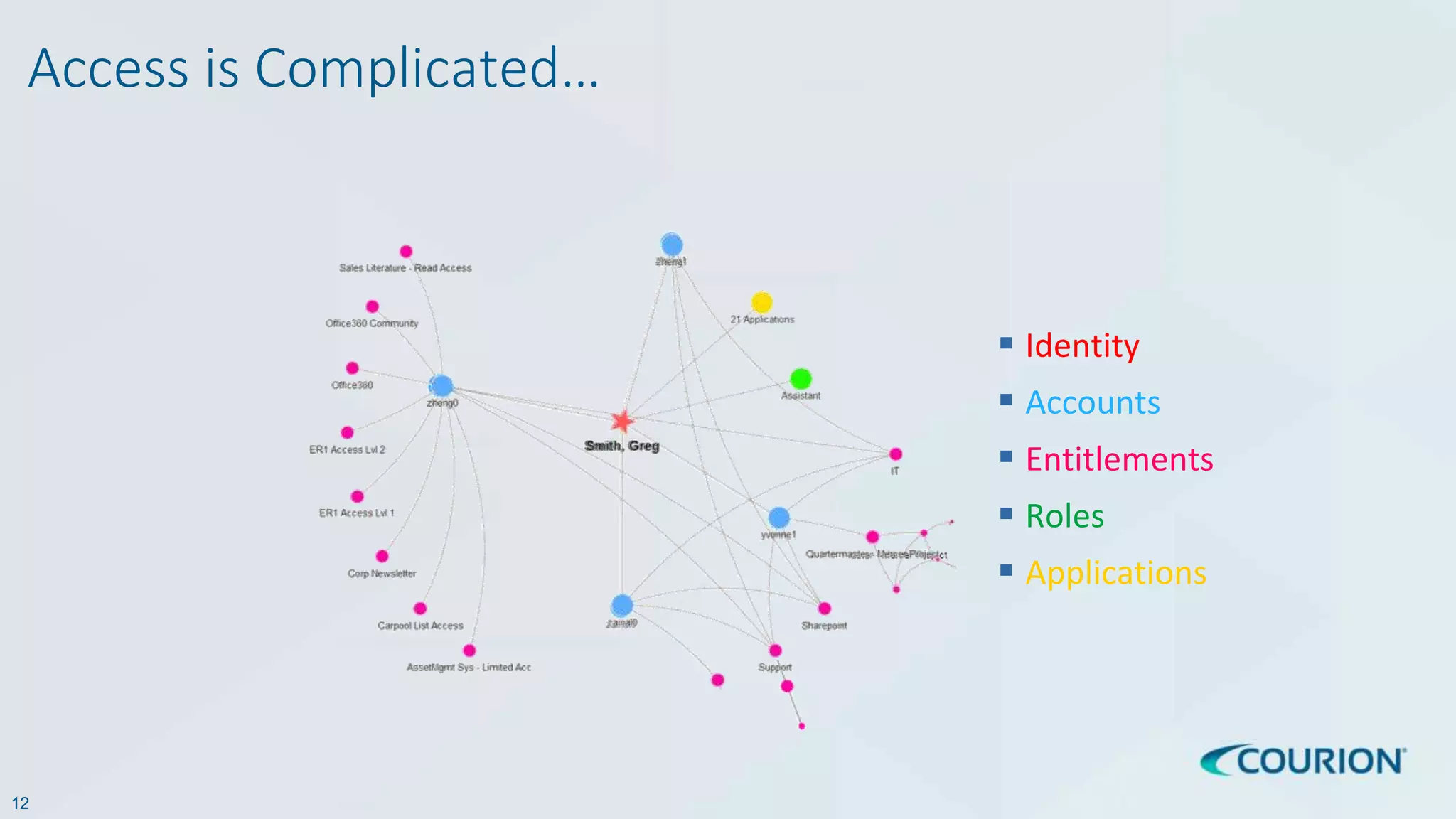
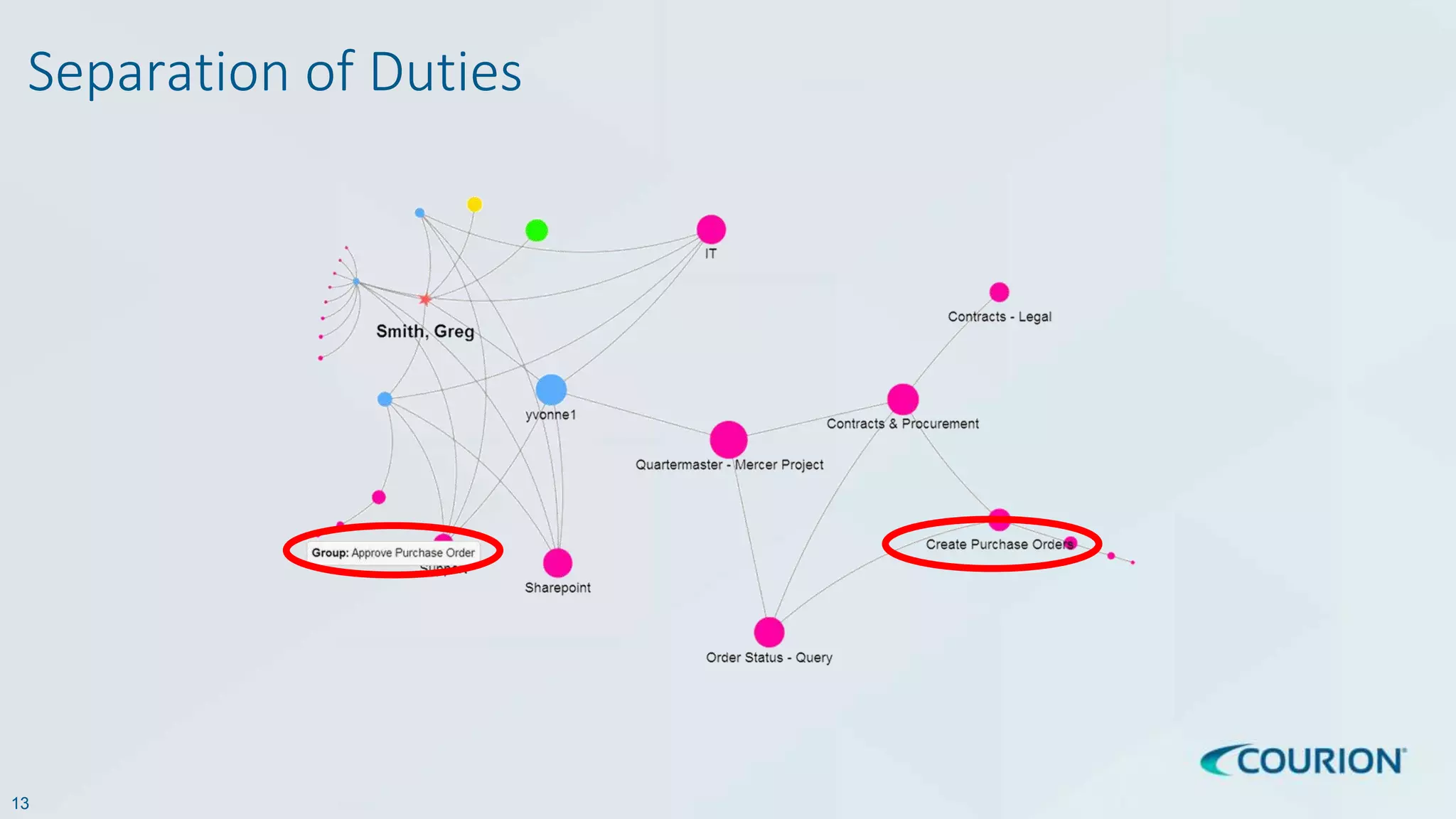
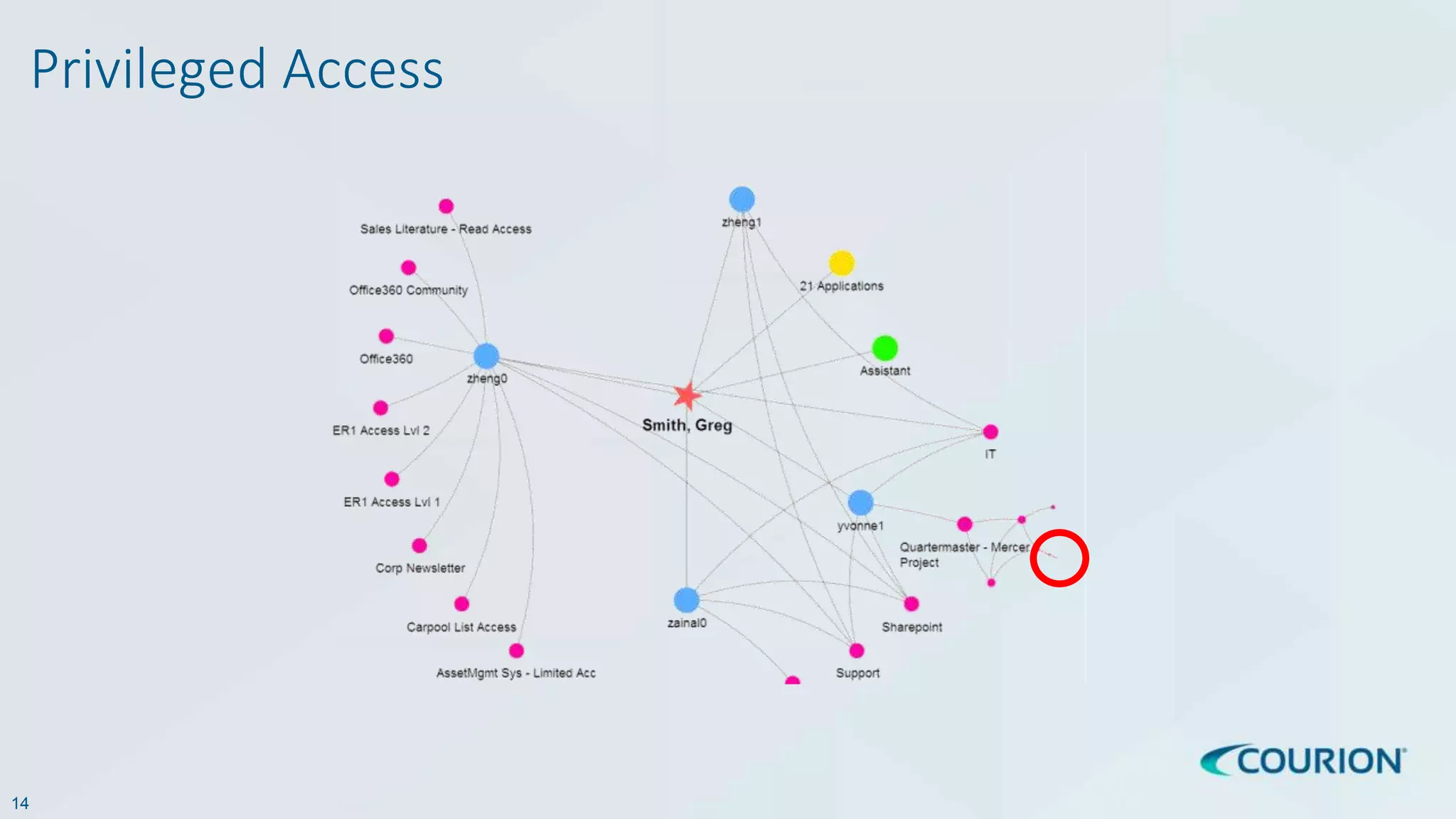
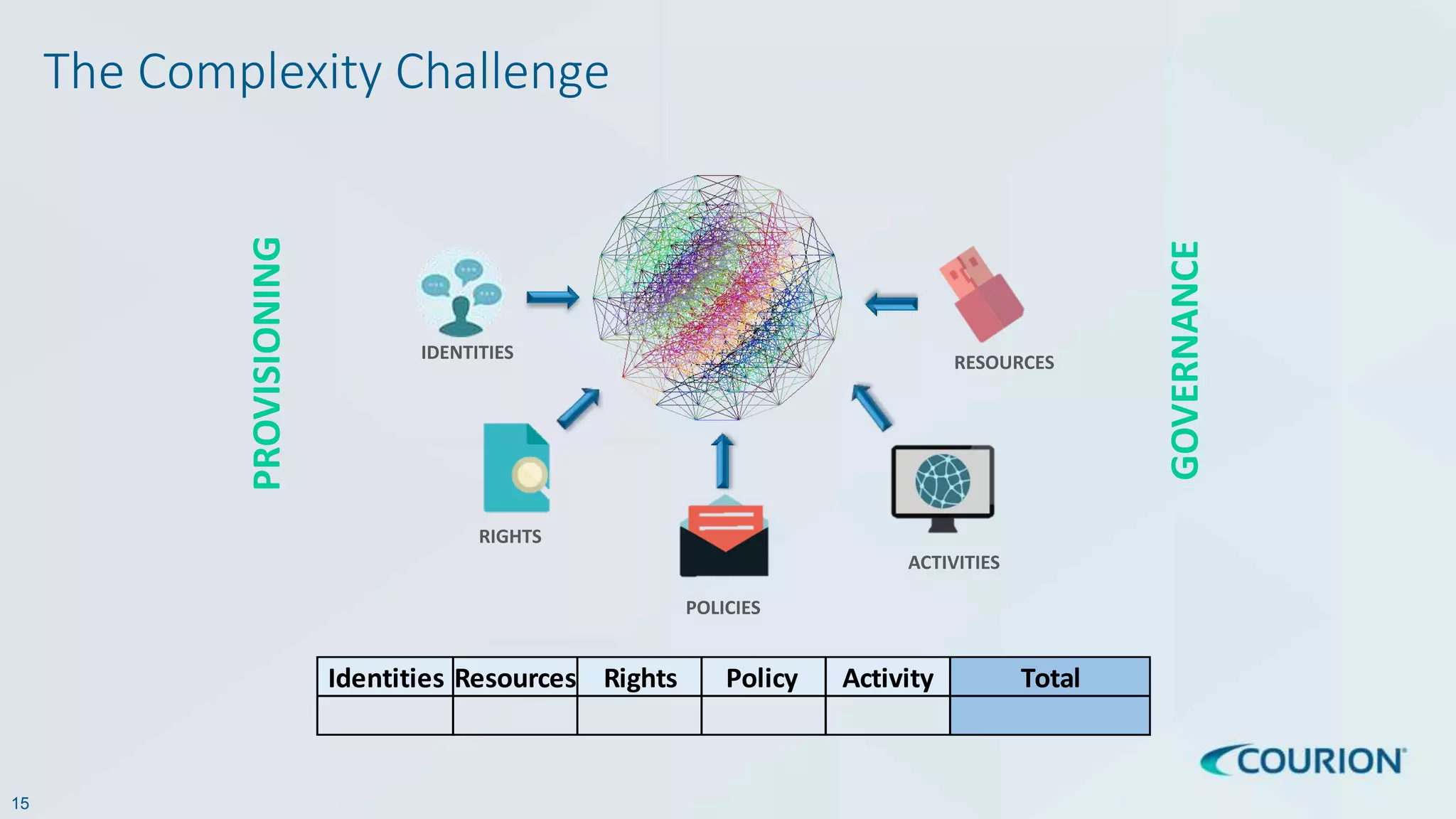
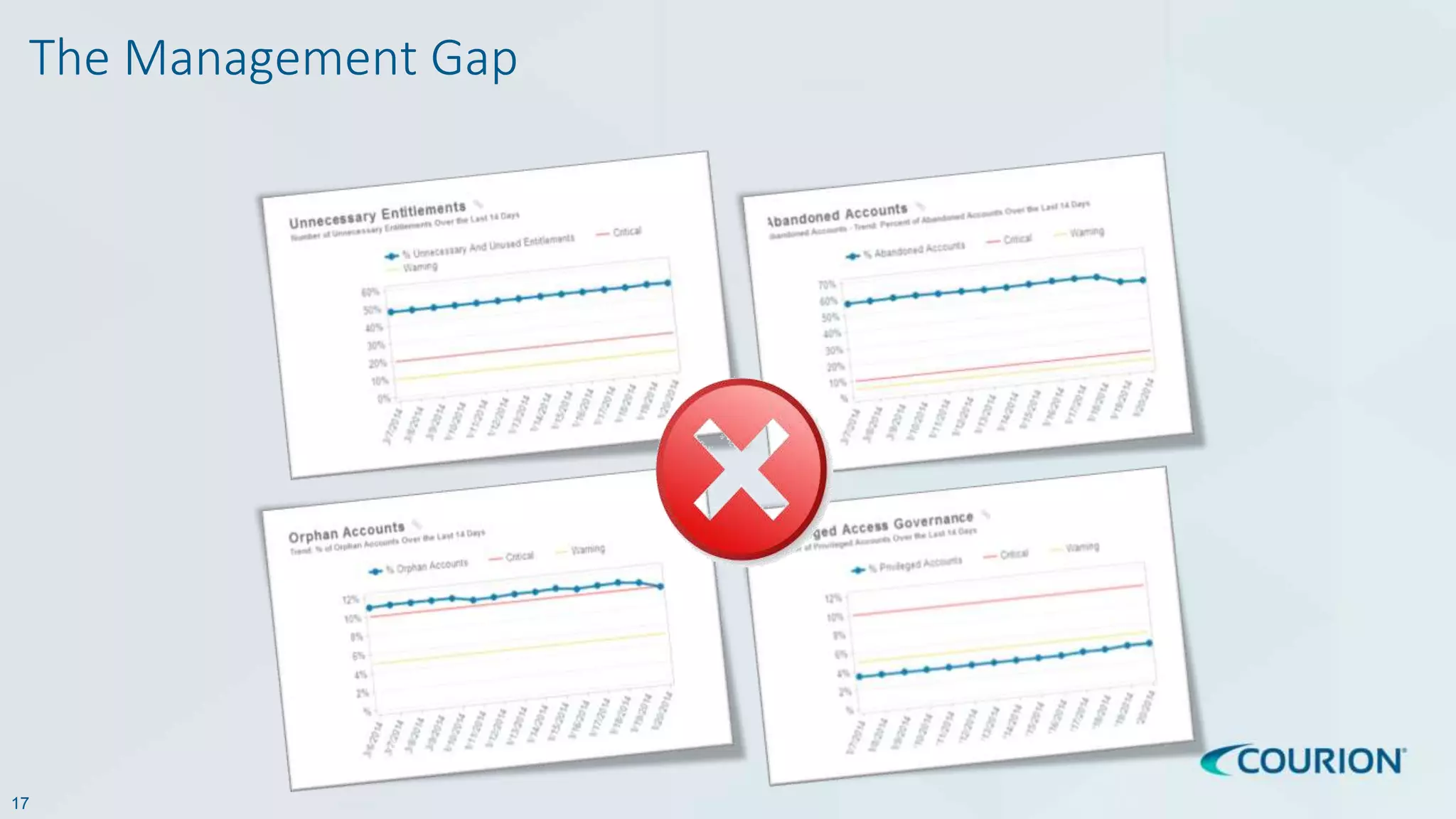
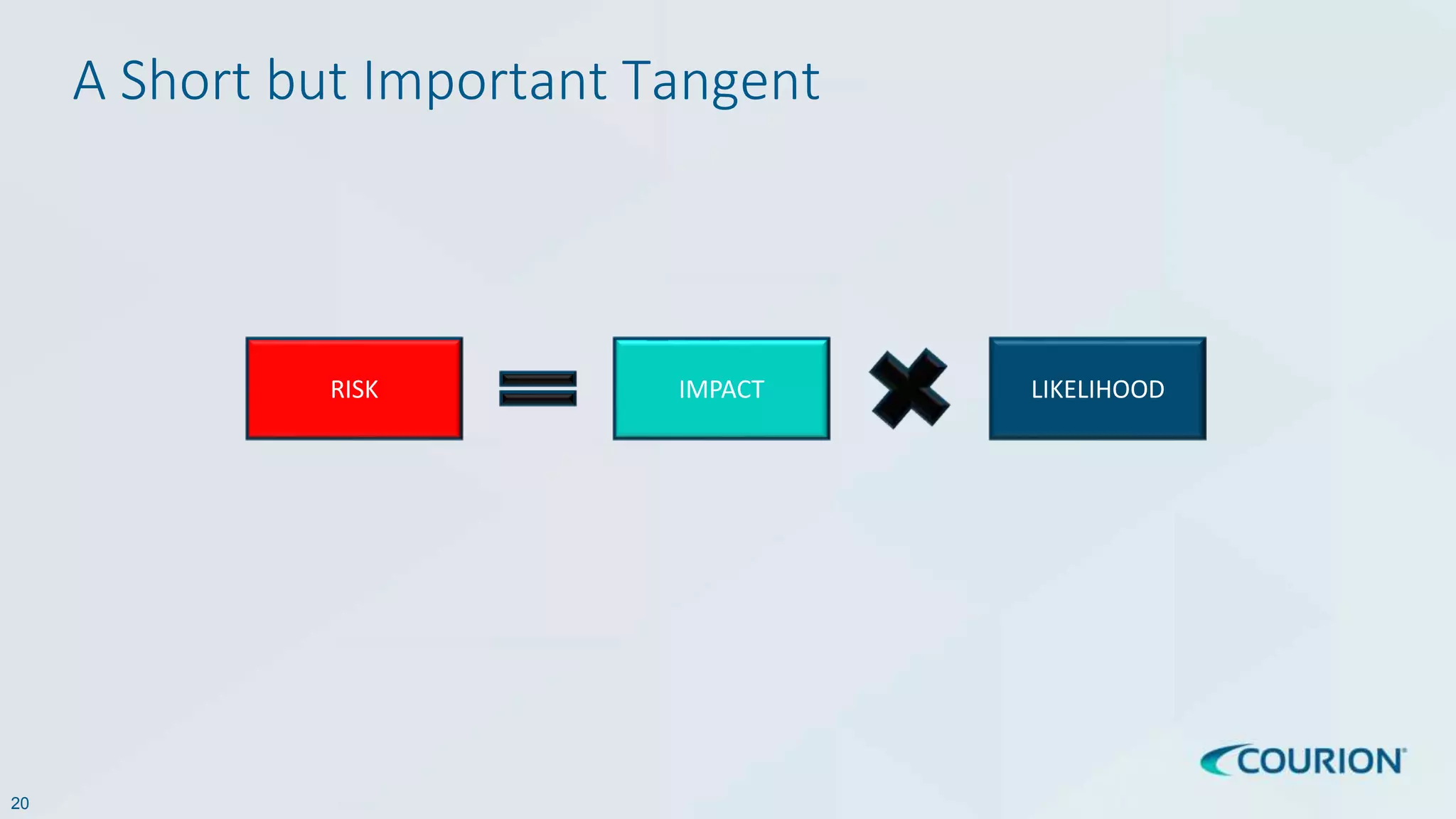
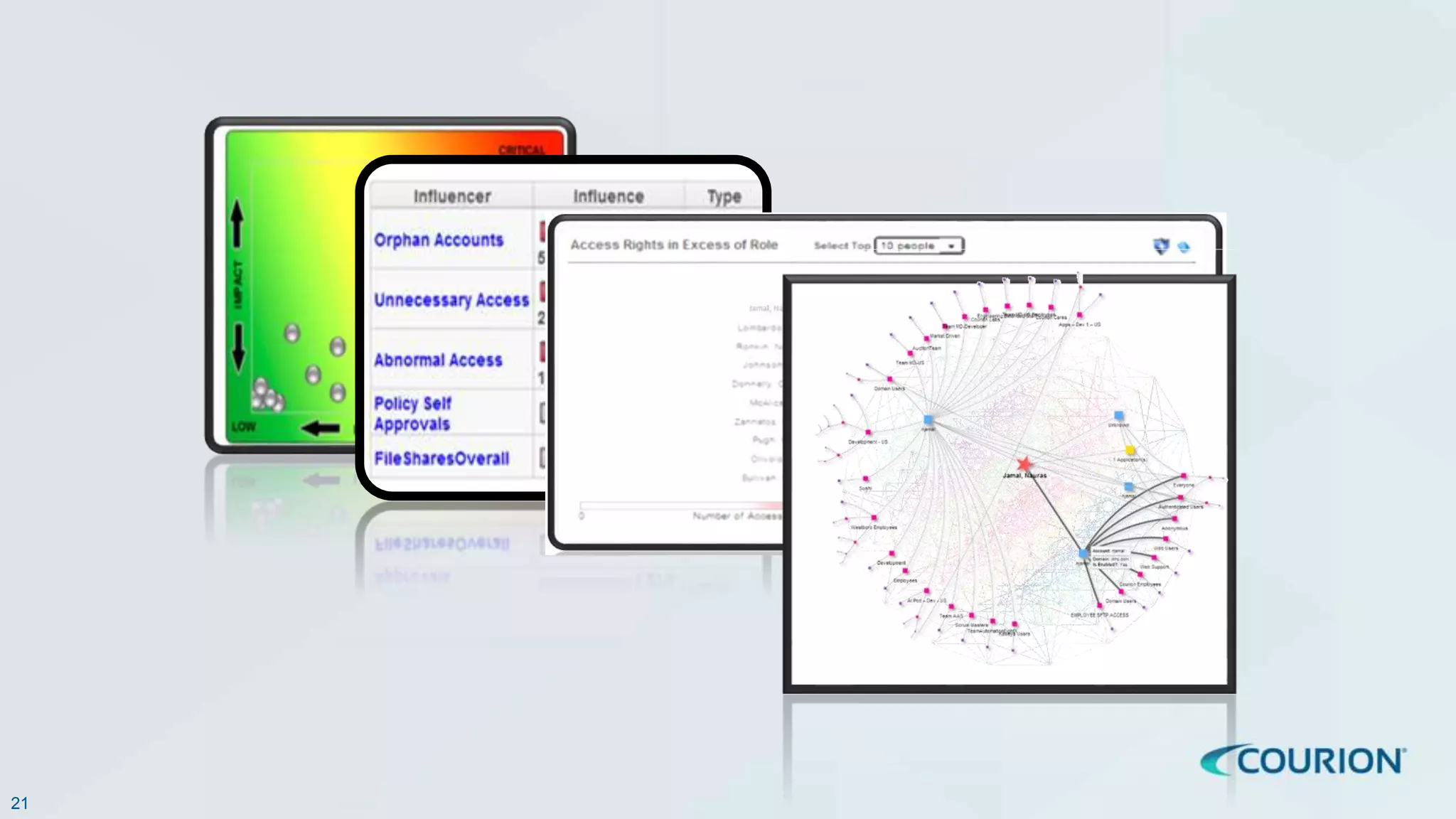
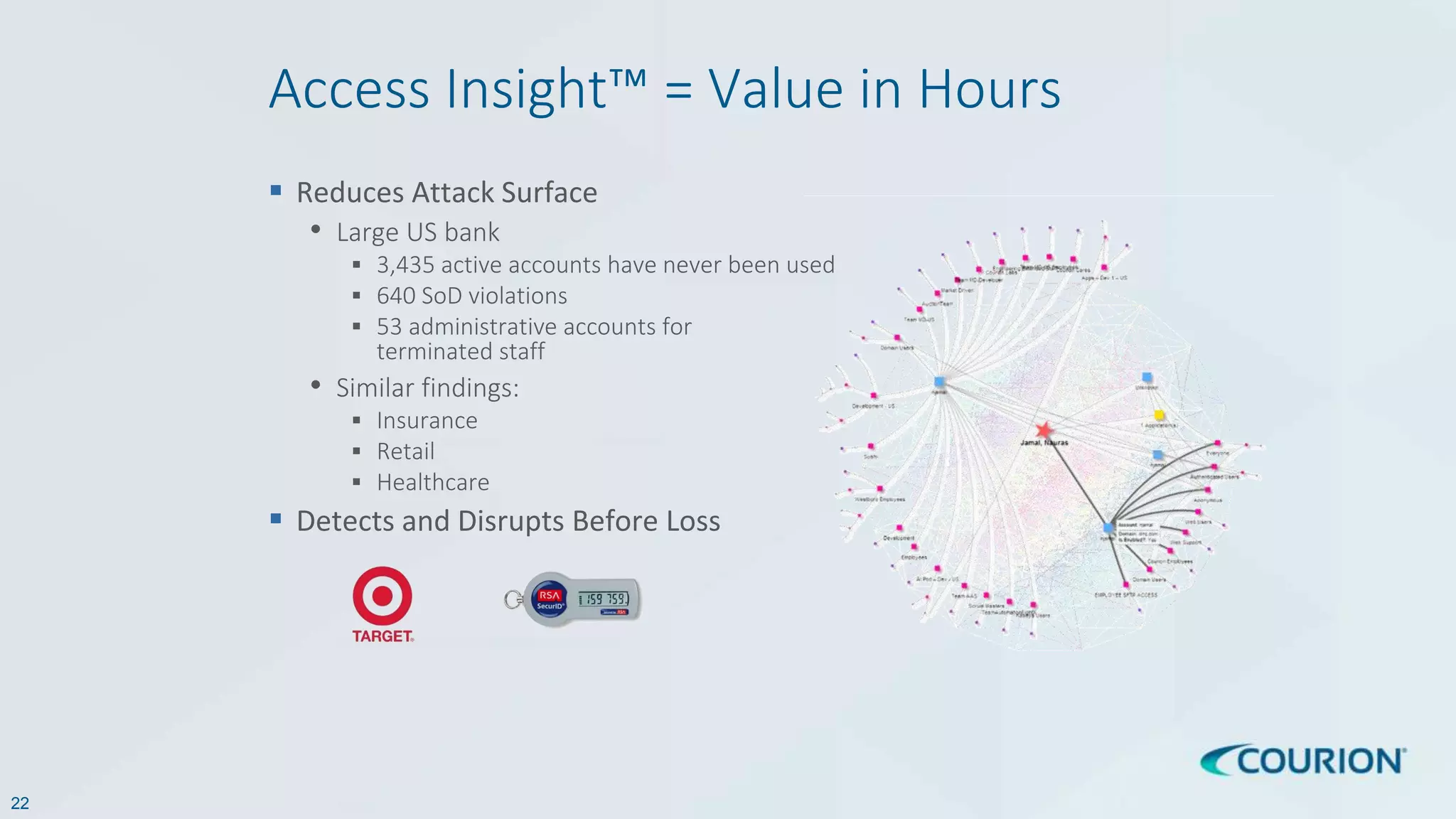
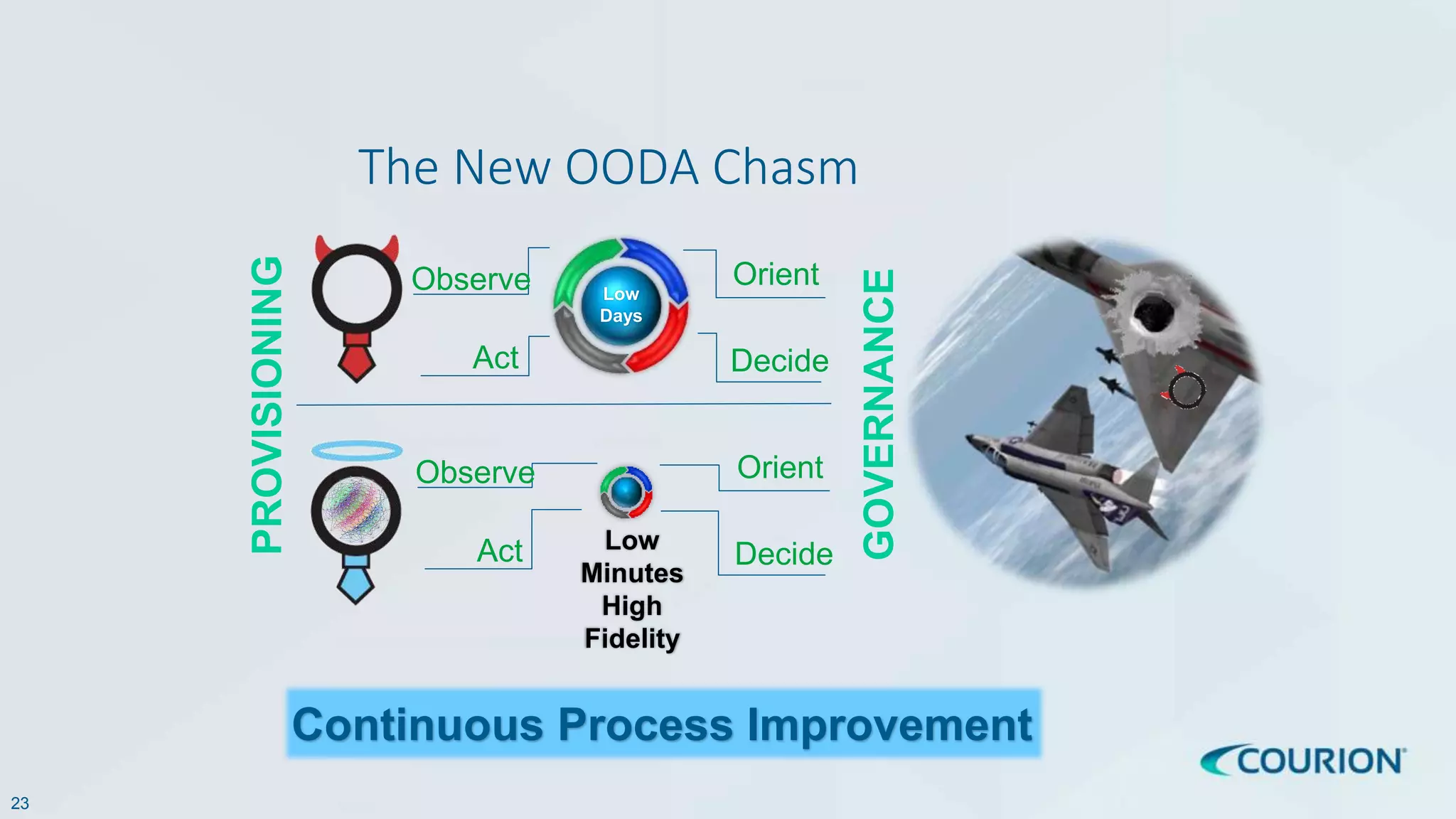
This document discusses intelligent identity and access governance. It notes that over 80% of breaches involve compromised accounts, and the average time accounts are compromised before detection is over 200 days. This leaves a need for access intelligence and analytics to more quickly detect and remediate access risks. The document introduces Access Insight, a tool from Courion that uses access analytics to identify issues like unused accounts, separation of duties violations, and accounts of terminated employees within hours of analyzing an organization's identity data. This helps reduce attack surfaces and detect and disrupt threats before losses occur.