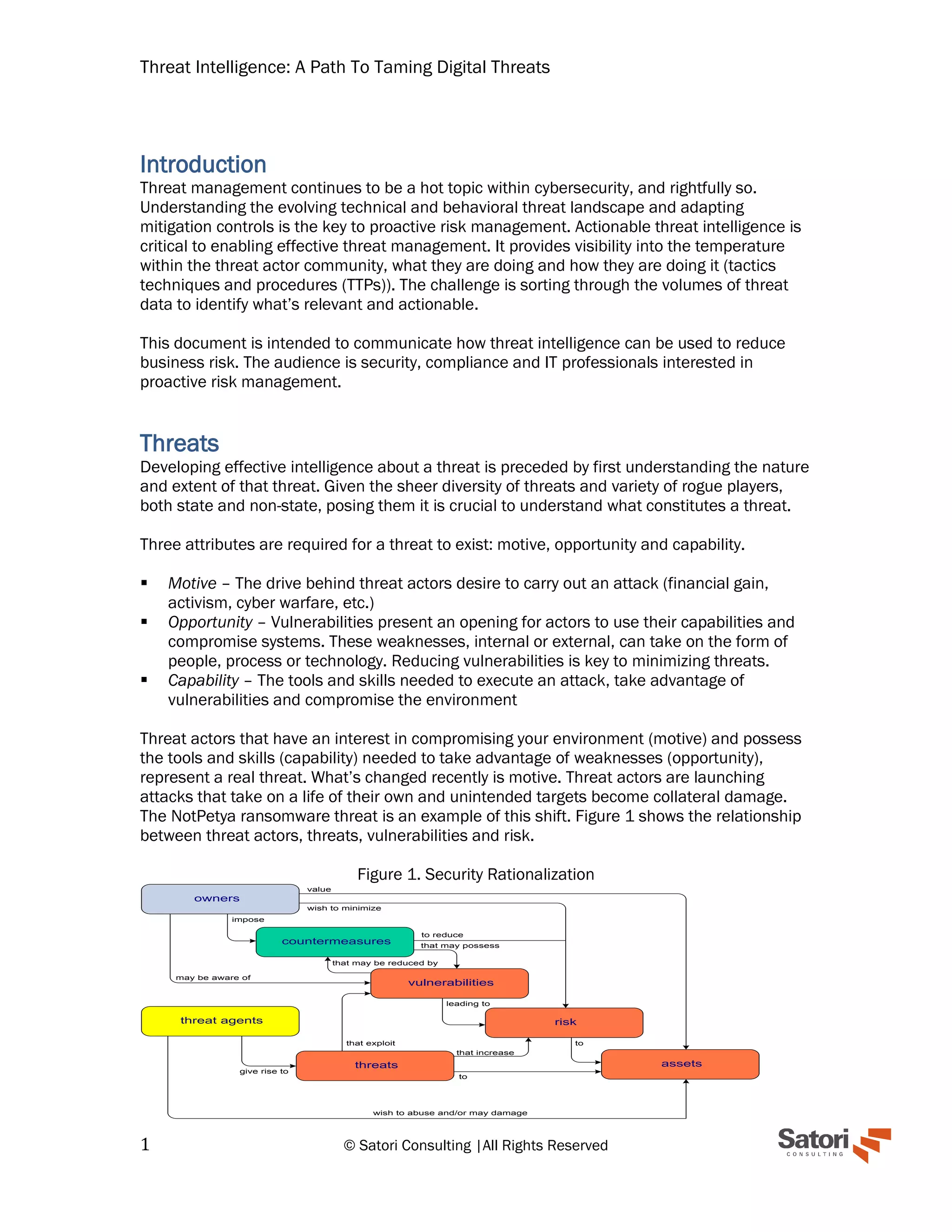
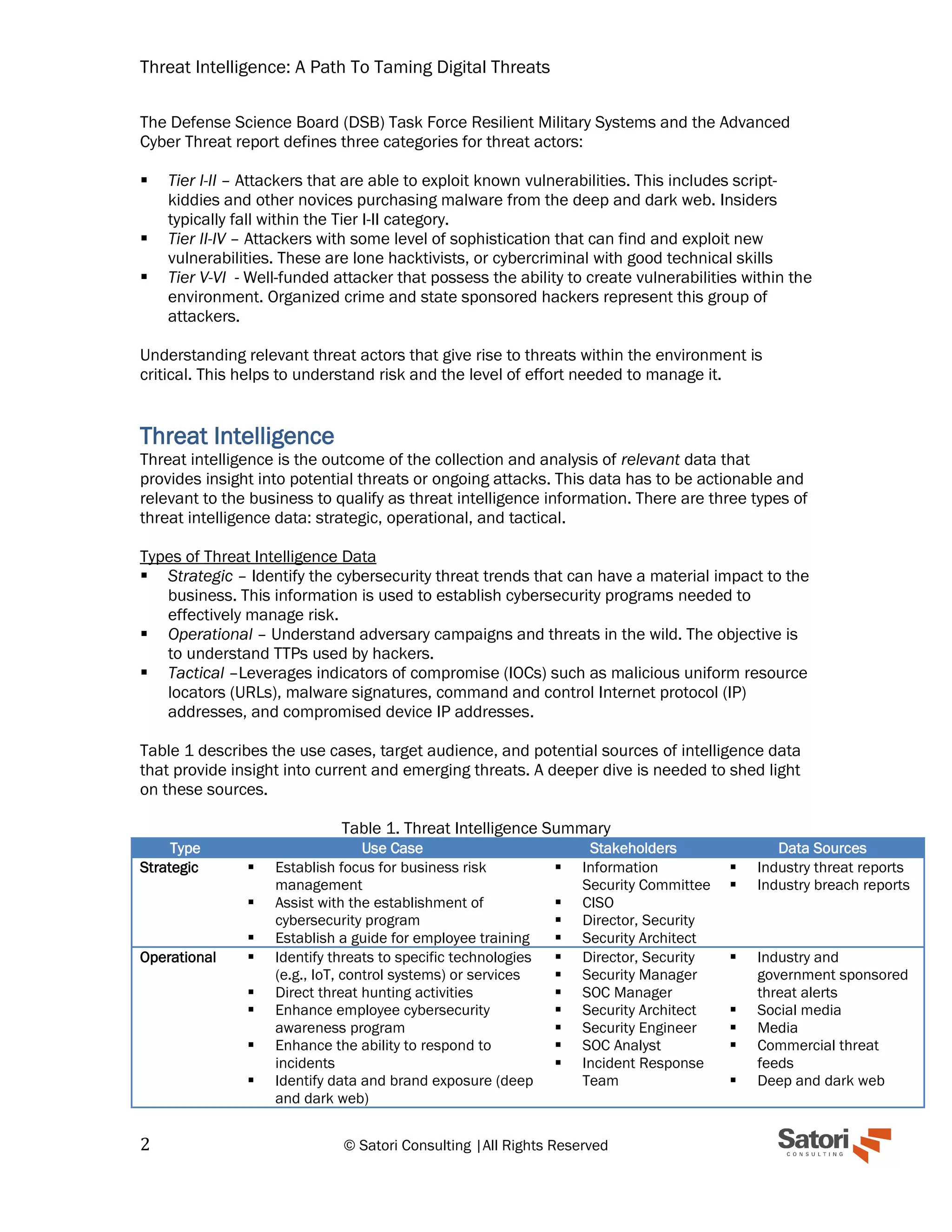
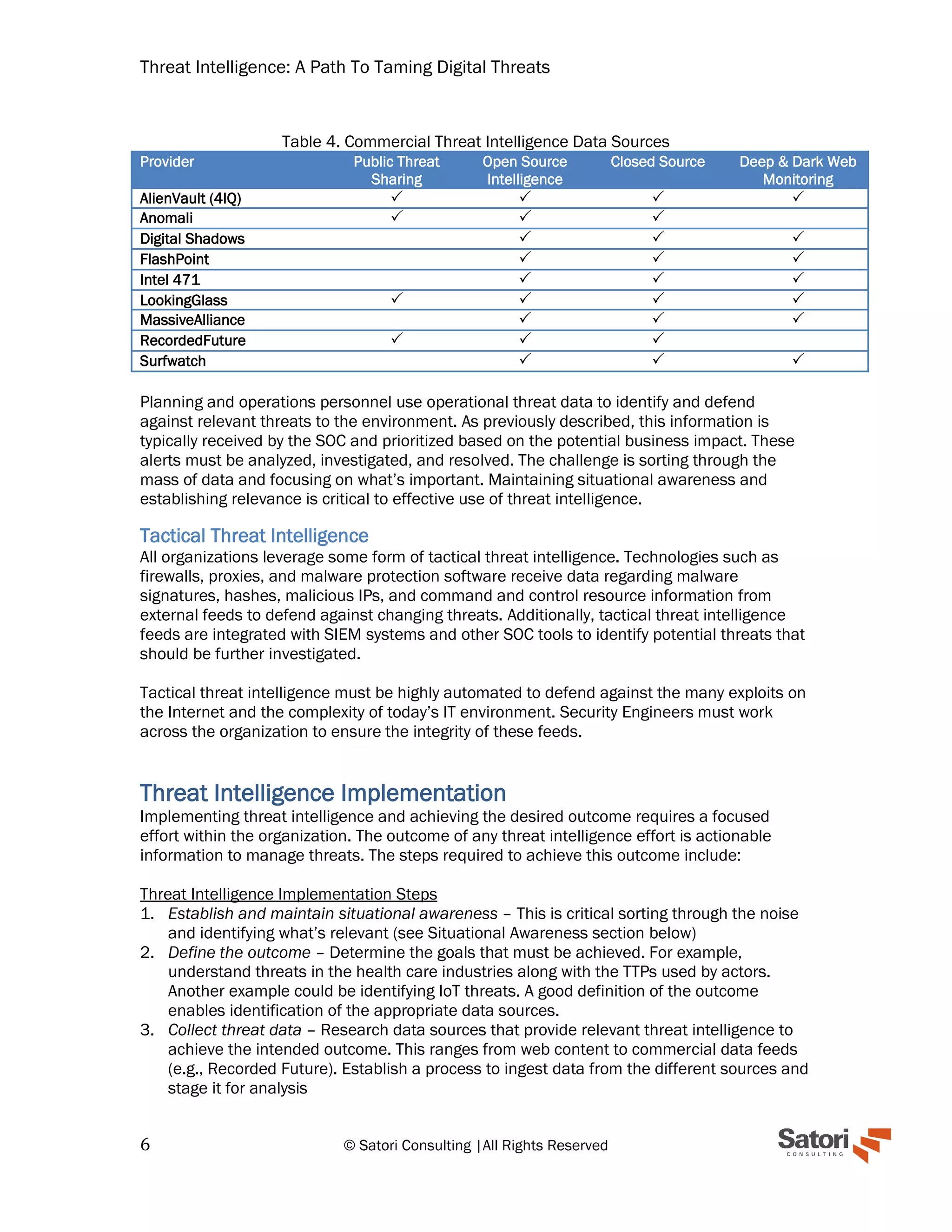
This document discusses the importance of threat intelligence in cybersecurity for effective risk management. It outlines the need for understanding threat actors, the types of threat intelligence (strategic, operational, and tactical), and the processes involved in collecting and analyzing relevant data to mitigate risks. The focus is on implementing actionable threat intelligence to not only defend against known threats but also to proactively adapt to emerging risks.