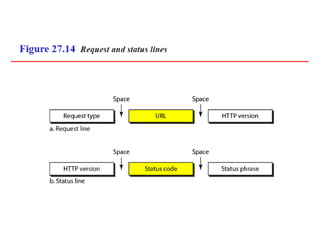
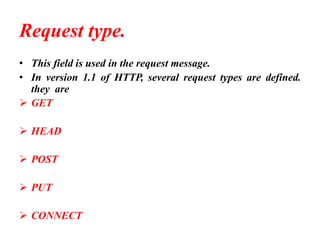
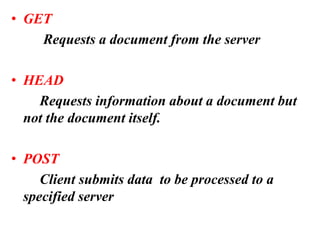
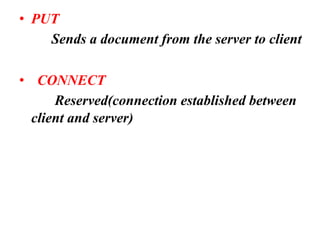
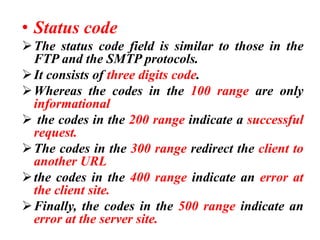
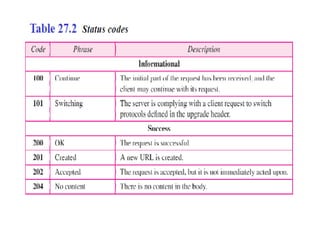
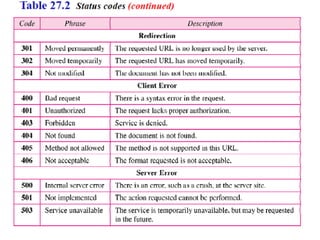
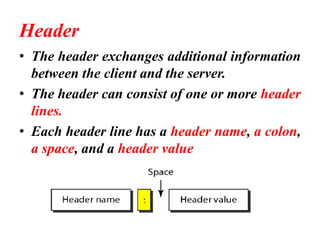
The document provides an overview of the Hypertext Transfer Protocol (HTTP), detailing its role in accessing data on the World Wide Web and its similarities with FTP and SMTP. It explains HTTP transactions, request and response messages, headers, status codes, and network security principles related to message confidentiality, integrity, authentication, and non-repudiation. Additionally, the document outlines the current version of HTTP, various request types, and headers used in both requests and responses.