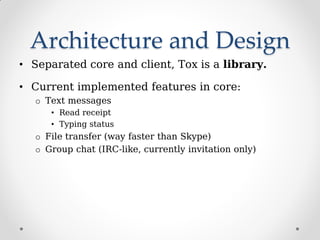
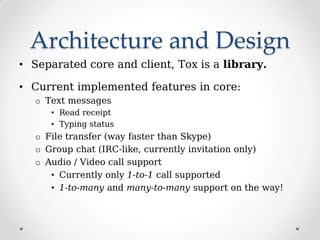
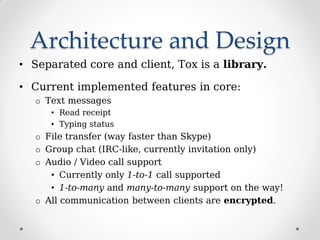
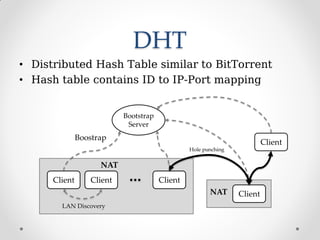
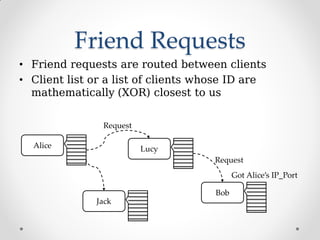
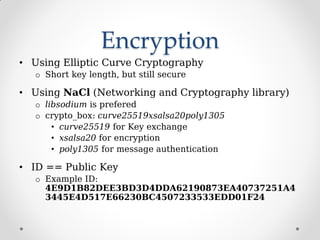
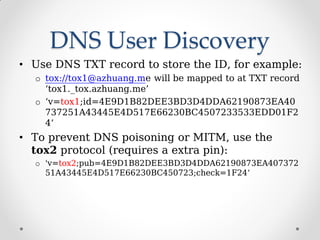
ProjectTox is a decentralized, end-to-end encrypted messaging network that aims to provide a free and secure alternative to Skype. It uses a distributed hash table and end-to-end encryption to allow communication without a centralized server. The core supports text, file transfers, group chat, and audio/video calls between two users. Several clients have been developed including Toxic for the command line and PyTox which provides full audio/video support through Python bindings. The developer demonstrated PyTox's new audio/video functionality and encouraged participants to join the project on GitHub or its wiki.