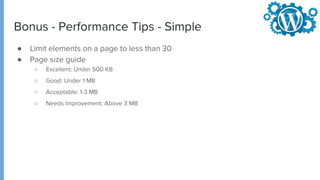
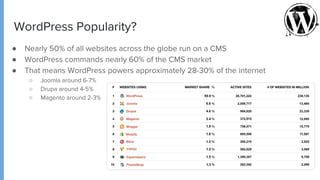
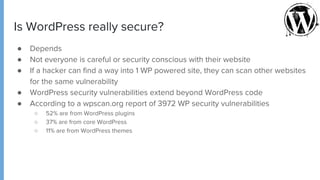
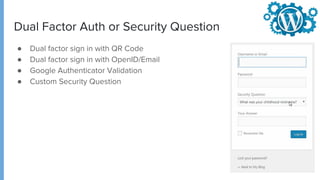
The document provides comprehensive guidance on securing WordPress websites, highlighting the prevalence of security vulnerabilities linked to plugins, themes, and core code. It addresses common issues such as brute force attacks, password protection, and configuration settings, offering practical solutions for enhancing security. The importance of ongoing maintenance, backup strategies, and immediate recovery measures in the event of a hack are also emphasized.














![Sample .htaccess rules
Protect from Script Injection
Options +FollowSymLinks
RewriteEngine On
RewriteCond %{QUERY_STRING} (<|%3C).*script.*(>|%3E) [NC,OR]
RewriteCond %{QUERY_STRING} GLOBALS(=|[|%[0-9A-Z]{0,2}) [OR]
RewriteCond %{QUERY_STRING} _REQUEST(=|[|%[0-9A-Z]{0,2})
RewriteRule ^(.*)$ index.php [F,L]
Password Protection with htaccess
AuthType Basic
AuthName "Password Protected Area" AuthUserFile /path/to file
Require valid-user](https://image.slidesharecdn.com/ctrlf52018wordpresssecurity-180626104949/85/ResellerClub-Ctrl-F5-WordPress-Security-session-25-320.jpg)