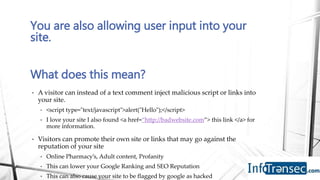
Robert Vidal is an information security professional who specializes in WordPress security. He outlines several recommendations for securing a WordPress site, including changing default usernames and passwords, removing WordPress version information, keeping software updated, using strong security plugins, limiting comments and user input, regularly backing up the site, and scanning for vulnerabilities, malware and unauthorized changes. Vidal emphasizes that there is no single solution and site owners must take an active, ongoing approach to security through multiple methods like plugins, backups and monitoring.