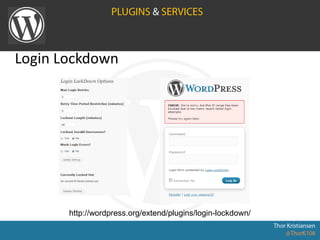
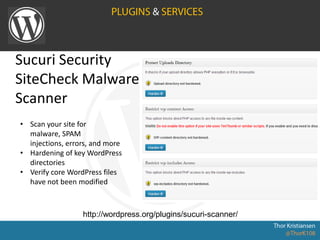
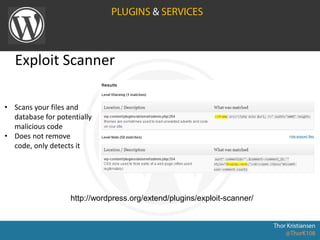
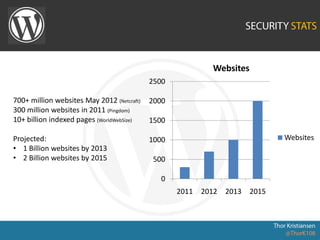
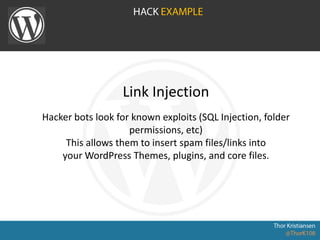
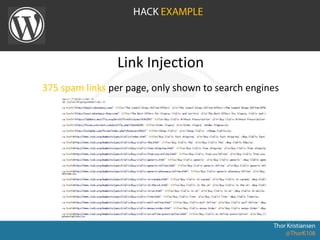
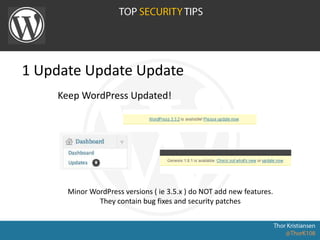
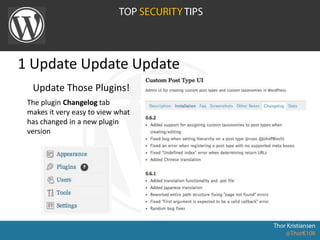
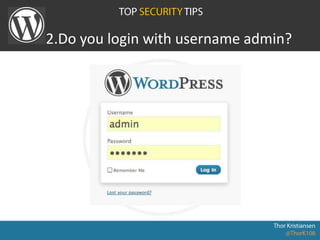
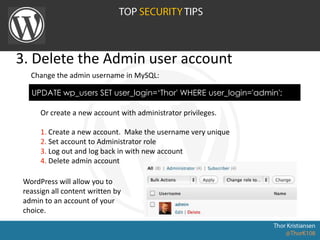
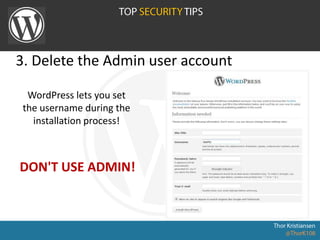
WordPress Security document outlines security stats, a hack example, and top security tips. It provides recommendations to keep WordPress updated, secure login credentials, lock down admin access, use trusted sources for themes and plugins, and utilize security plugins and services like Login Lockdown, Sucuri Scanner, and Exploit Scanner. The document emphasizes the importance of common sense practices like strong unique passwords, backups, and limiting administrator accounts.






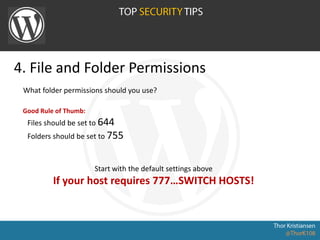
![4. File and Folder Permissions
find [your path here] -type d -exec chmod 755 {} ;
find [your path here] -type f -exec chmod 644 {} ;
Or via SSH with the following commands](https://image.slidesharecdn.com/wordpress-131001052801-phpapp02/85/WordPress-Security-WordPress-Meetup-Copenhagen-2013-22-320.jpg)