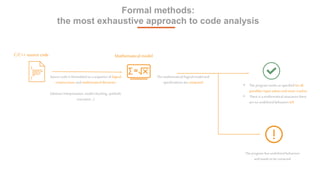
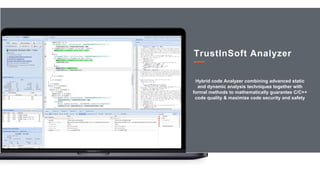
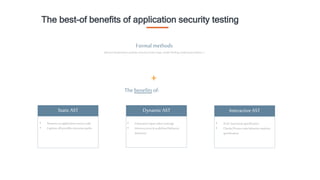
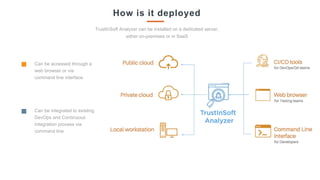
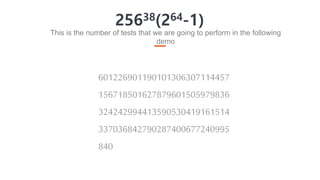
The document discusses TrustInSoft's advanced code analysis solution that utilizes formal methods to mathematically guarantee safety and security in C/C++ software. It highlights the solution's ability to detect undefined behaviors, optimize bug detection, and improve operational efficiency, with proven results in various industries such as aeronautics and consumer electronics. The deployment options for TrustInSoft Analyzer are also noted, including server installations and integration with existing development processes.