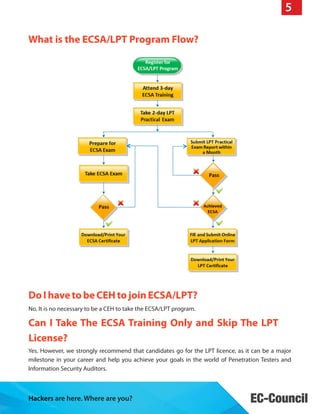
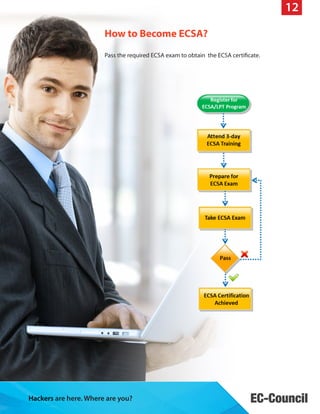
The document discusses the ECSA/LPT program which provides comprehensive training and validation for IT security professionals' penetration testing and security auditing capabilities. The program consists of the ECSA training and the LPT practical exam. ECSA is a 3-day hands-on training using simulated scenarios, while LPT is a 2-day exam to evaluate skills. Successful candidates receive two certificates. The program teaches standard methodologies and prepares students for real-world assessments and audits.